Getting IPv6 SLAAC to work in my network
-
@bob-dig sorry, I misspoke, English is not my native language.
I meant to say hosts, ie. the devices connected to the LAN network.
-
@ionutit Then you must have configured that ULA yourself in RA? Again, pfSense is not handing out ULA on its own.
-
@bob-dig
Those are probably from some other actor inside my network. Maybe my Apple devices are doing that. I will look into that, but regardless, I have my RA priority set to High on pfsense, so if things there are working, it should take from my router not anyone else.
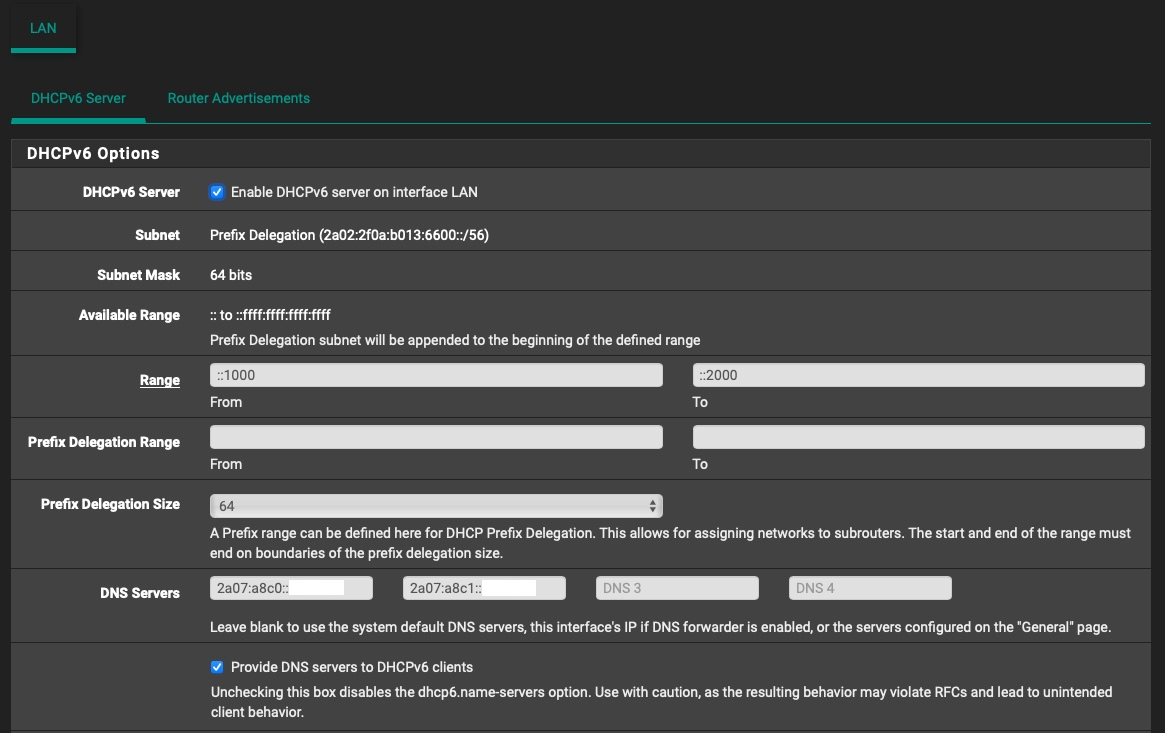
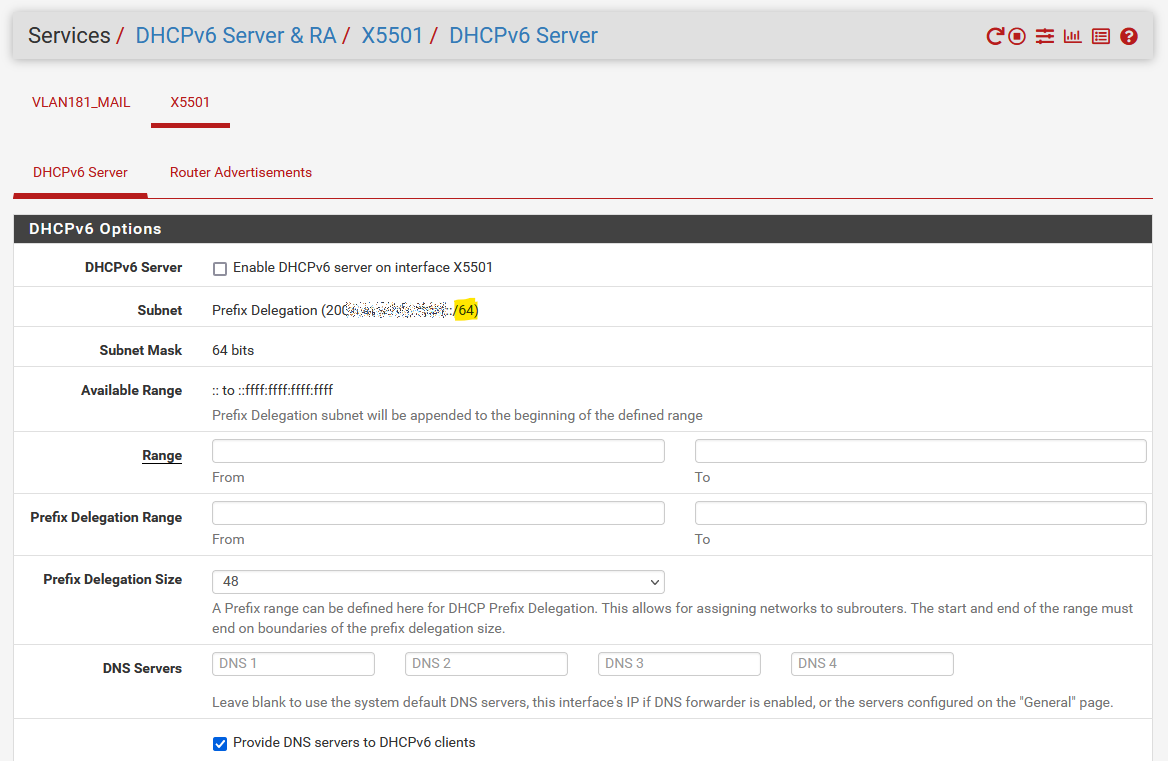
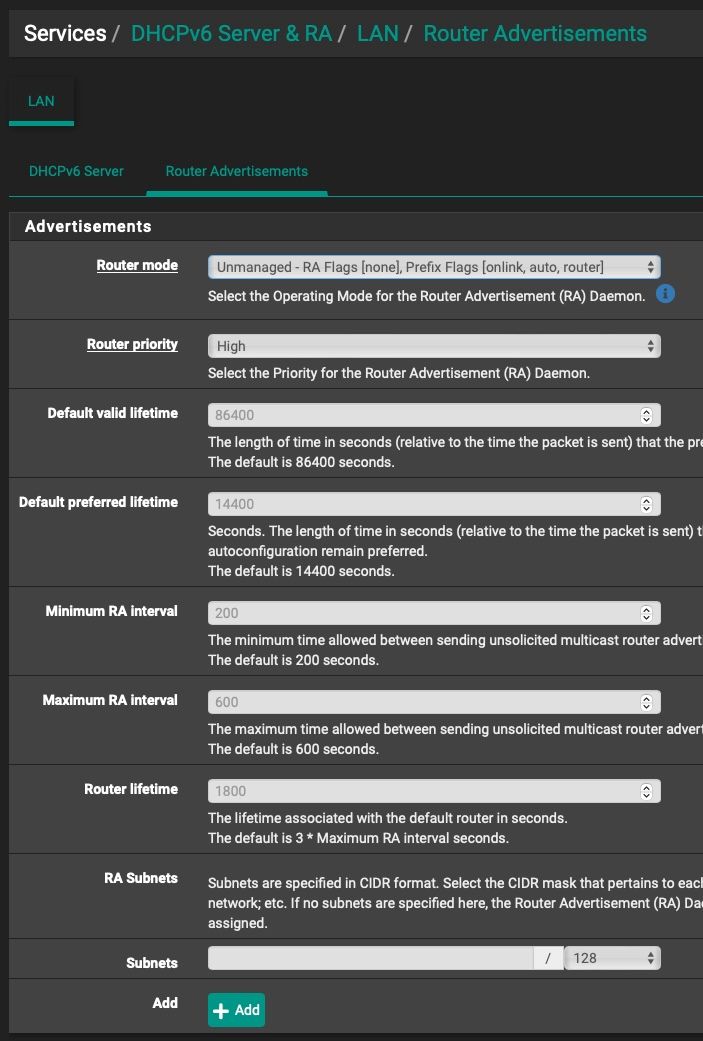
With DHCPv6 server turned off and RA set to Unmanaged, I don't get any GUA addresses from my ISPs Prefix Delegation, unless I manually set it in the RA Subnets field in pfsense config.
I also tried with RA set to Stateless DHCP and the results are the same.
Is the fact that my PD from my ISP at /56 an issue? Is there a way to fill in the /56 to a /64 so that I can serve a /64 to SLAAC (might be talking nonsense here, I've been learning about IPv6 for a few months now, even though I work in networking for 14 years, I only dealt with IPv4 so far).
-
@ionutit said in Getting IPv6 SLAAC to work in my network:
Is the fact that my PD from my ISP at /56 an issue?
No, every LAN-type-interface in pfSense need its own /64 and /56 contains many /64, so that is good.
Maybe you have something incorrectly configured in the beginning and it is better to start fresh.
-
@bob-dig
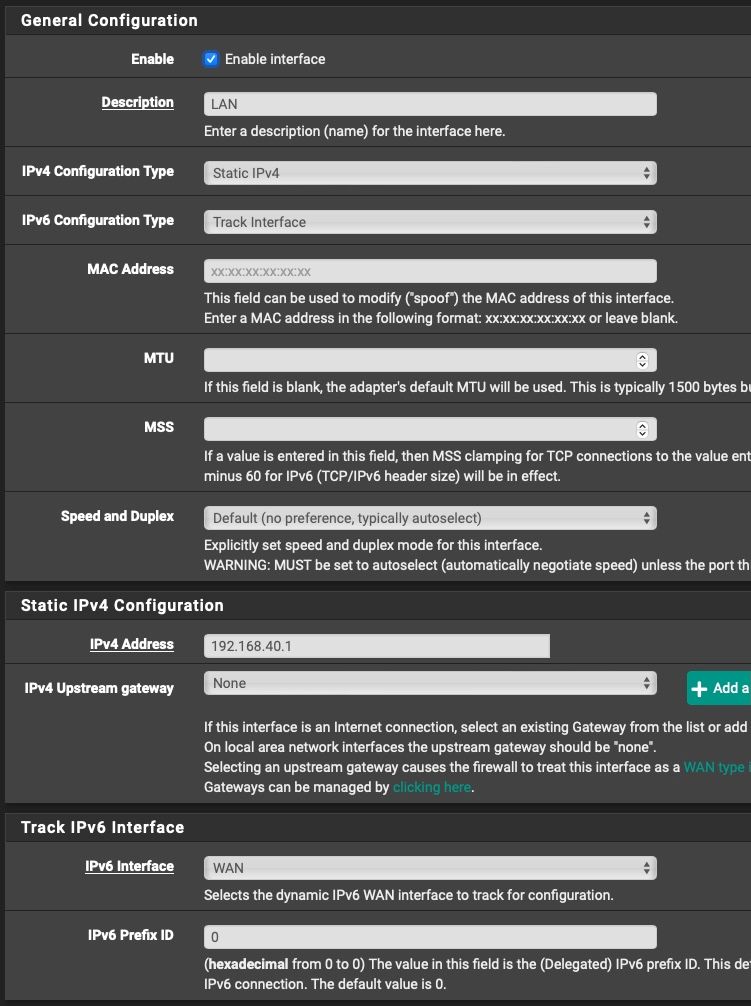
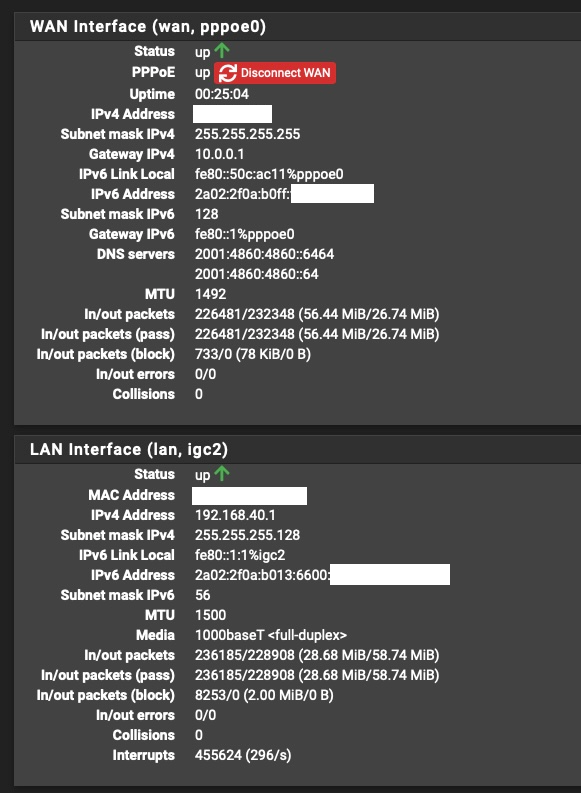
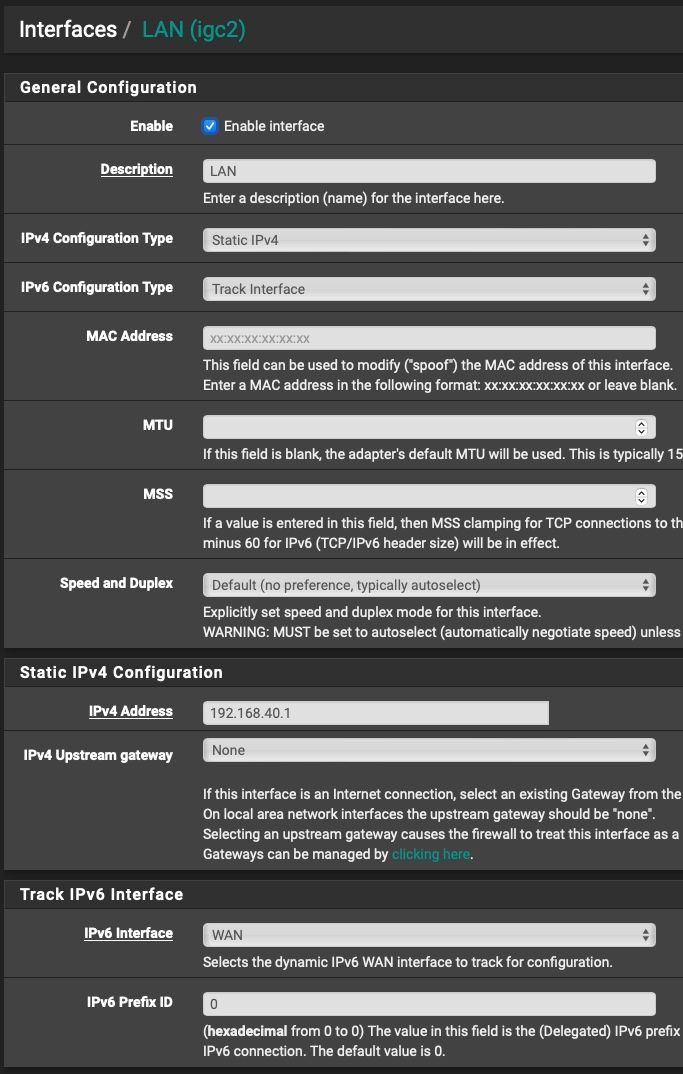
But the interface itself (LAN) gets a /56. The WAN gets a /128.
-
-
@bob-dig
I didn't do anything wrong, It gets a /56 automatically from the ISP through DHCPv6-PD.
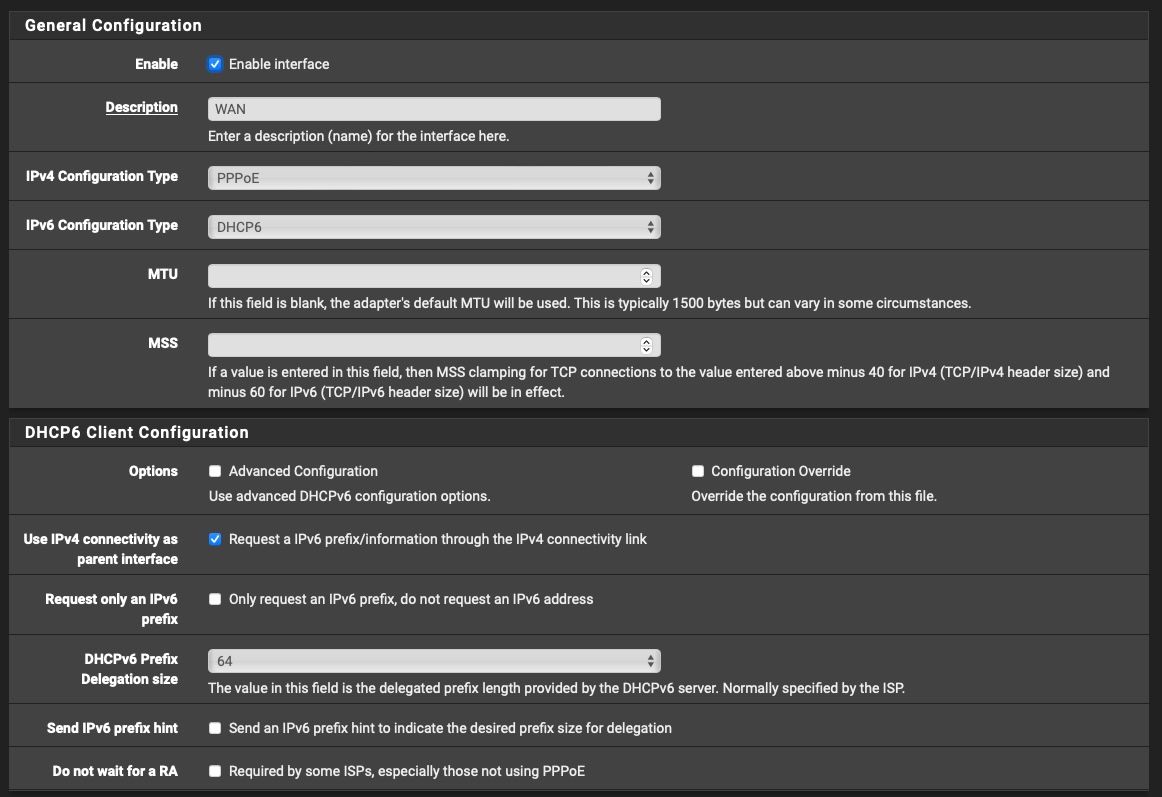
There's not many settings to mess up when configuring, as you can see in the screenshots I posted.
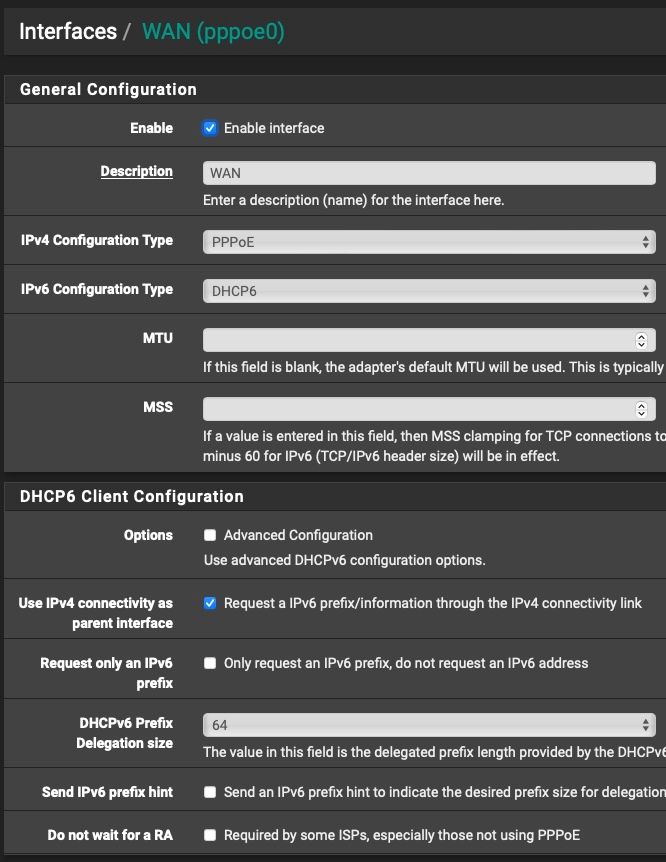
On the WAN interface I did:
On the LAN interface I did:
And in the RA page I did:
I haven't touched anything else...
And for some weird reason, even though I set my Prefix Delegation to /64, my ISP always gives me /56.
-
@ionutit said in Getting IPv6 SLAAC to work in my network:
I haven't touched anything else...
And non the less there is no way I can think of that pfSense is showing /56 on the Subnet in the DHCPv6 Options for your LAN if you use Track Interface.
Something is fundamentally wrong in your setup, maybe your running pppoe over your LAN? Really just start fresh is all I can advice you to do.
-
@bob-dig
I'm not running PPPoE over my LAN, that's just for WAN.
The only thing I think it's wrong is the fact that my ISP gives me a /56 even though I ask for a /64. And the Prefix Delegation is assigned to /56 even though I want /64.
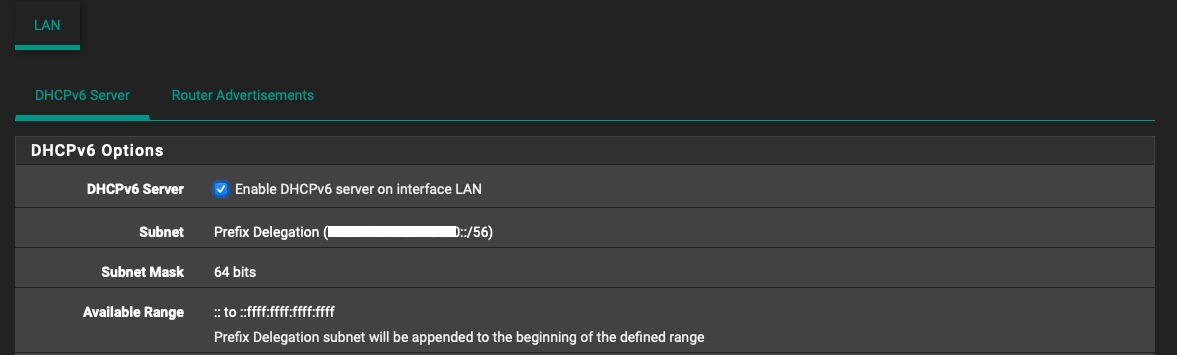
-
@bob-dig
OK so I finally made it work, but in a very weird way.
Seeing as when I set "64" in WAN settings "DHCPv6 Prefix Delegation size" gave me an actual /56 network for my LAN interface, I tried to set that to "56" (against the information that is handed out by my ISP), and sure enough, I instantly got a /64 network for my LAN interface and SLAAC magically started working.
Can't really explain why that worked, but I won't complain.
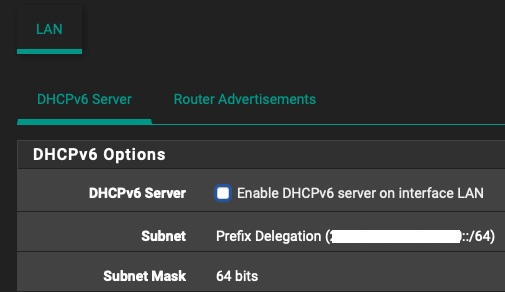
-
@ionutit said in Getting IPv6 SLAAC to work in my network:
Can't really explain why that worked, but I won't complain.
Interesting! Still won't explain the ULA on your LAN but at least you're making some progress.
-
@bob-dig
Yeah, I have no idea where those ULAs are coming from. It seems that not all my IPv6 enabled devices in my network get 2 IPs, one GUA and one ULA.
Is there a way to check RA packets and pinpoint the source?
At the end of the day this is not such a dealbreaker as obviously Internet traffic is passed through the GUA IP.
-
@ionutit said in Getting IPv6 SLAAC to work in my network:
And I also get a GUA IPv6 but with a /128 mask again with fe80::1 gateway.
On the LAN side, I get GUA IPv6 with a /56 subnet which is OK, even though I ask for a /64 (and the ISP itself is saying on it's info page that they give out /64 PD)A /128 GUA and link local gateway is entirely normal. Are you sure you get a /56 on the LAN?
but those PDs are dynamic, and if I disconnect for any reason I will get a new prefix delegation so that field needs to be manually updated.
Have you selected Do not allow PD/Address release on the WAN page?
-
@ionutit said in Getting IPv6 SLAAC to work in my network:
Is there a way to check RA packets and pinpoint the source?
Do a packet capture and check the MAC.
-
@jknott said in Getting IPv6 SLAAC to work in my network:
Are you sure you get a /56 on the LAN?
Yeah, for some strange and weird reason, when I set my Prefix Delegation size to 64 in WAN settings page, I always got a /56 assigned to my LAN (interface was set to tracking).
But as I mentioned in my last post, when I set the PD size to 56 (against what my ISP has informed me I should use) I immediately got a /64 assigned to my LAN and SLAAC started working.
Now I just need to find the source of these ULA addresses that my network gets, it's going to be a pain to find them, but fortunately it doesn't really impact my ability to go online though IPv6.
-
@ionutit said in Getting IPv6 SLAAC to work in my network:
But as I mentioned in my last post, when I set the PD size to 56 (against what my ISP has informed me I should use) I immediately got a /64 assigned to my LAN and SLAAC started working.
56 on the WAN is normal. That's what I have here. This way, you have up to 256 /64s to use.
As for the RAs, as I said, do a packet capture to see the MAC address, from which you can identify the device.
-
I'm trying to do that, but I might be doing it wrong.
So I'm running Wireshark on the ens0 (Ethernet port on my Mac Mini) and filtering for
icmpv6.type == 134
But all my outputs are showing fe80: link-local source and destination. I can't catch the fdcd: ULA anywhere.
Any pointers on how I should sniff for that?
-
@ionutit In the end, you can not filter "local" traffic in one subnet anyway, only something routed through the firewall can be filtered. So as long as this (apple-)device is only member of one subnet, it shouldn't matter. I hope you have more than one LAN because otherwise the firewall isn't doing much for you.
-
@bob-dig
Yeah, at the end of the day I don’t really mind having this ULA network as it’s not routed outside.
Only thing that bugged me is that hosts use this ULA range for mDNS updates. I had to create a firewall rule to allow “any” to “ff02::fb” on UDP 5353.
-
I think you'll find capture filters work better than display filters. Capture filters affect what's captured and display filters affect what packets of the capture are displayed. Of course, you can use both for more flexibility. However, I mostly use capture filters. So, you'd filter on ICMP6, which should capture all ICMP6 packets. Once you have some of those, you can use display filters. However, just capturing ICMP6 and quickly scanning the captured packets should reveal the RAs.