PFSENSE WIFI CALLING
-
@msa1878 Can you please show your IPSec and firewall setup?
-
@msa1878 I've never had this issue, but I've seen posts online that suggest going to System -> Advanced -> Firewall & NAT and switching the "Firewall Optimization Options" from Normal to Conservative has resolved this issue for others.
Other posts have suggested that manually changing the "UDP Multiple" timeout setting from 60 to 900 may achieve the same result. Also located in System -> Advanced -> Firewall & NAT under the "State Timeouts" section.
-
I use Wifi calling with pfSense and no problems here. Also, it's not plain IPSec. It's encapsulated in UDP, to get through NAT.
Here is some info that may help:
What are the firewall required ports for wifi-calling? -
You might need "static port" depending on your carrier as well..
-
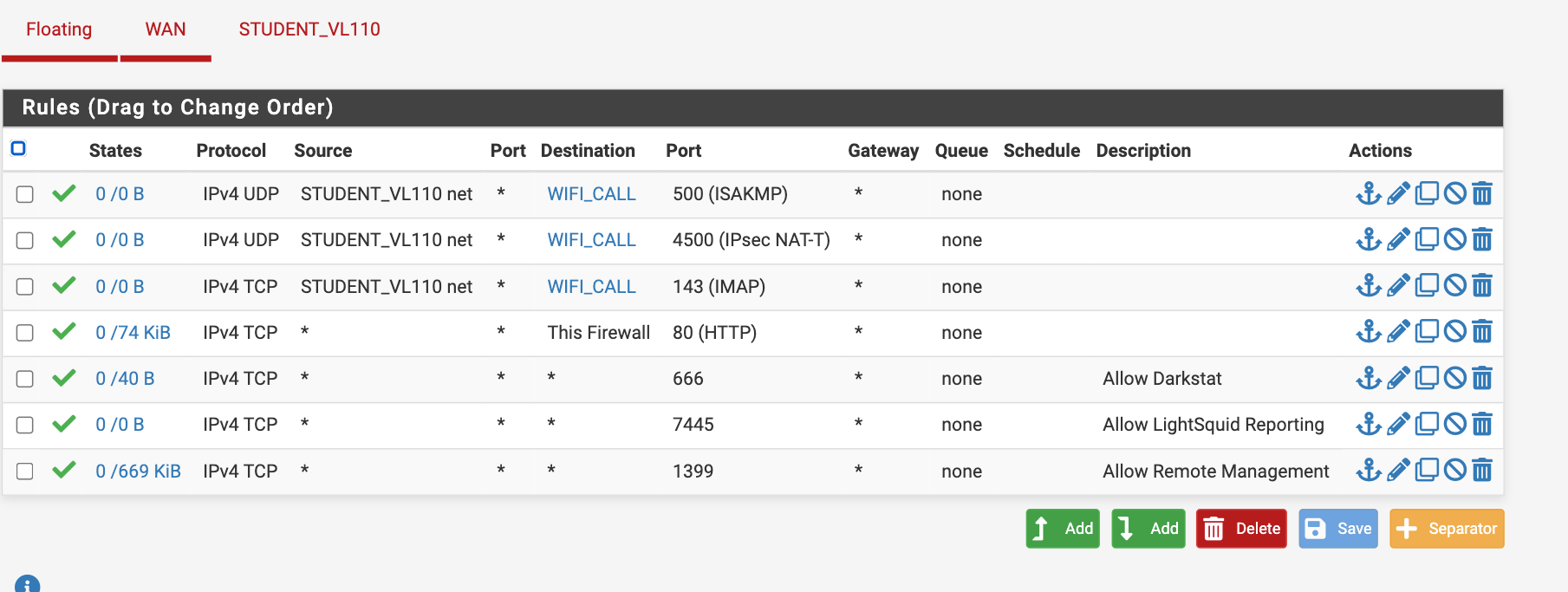
Because its reaching out over UDP:4500 , maybe firewall rules are blocking it?
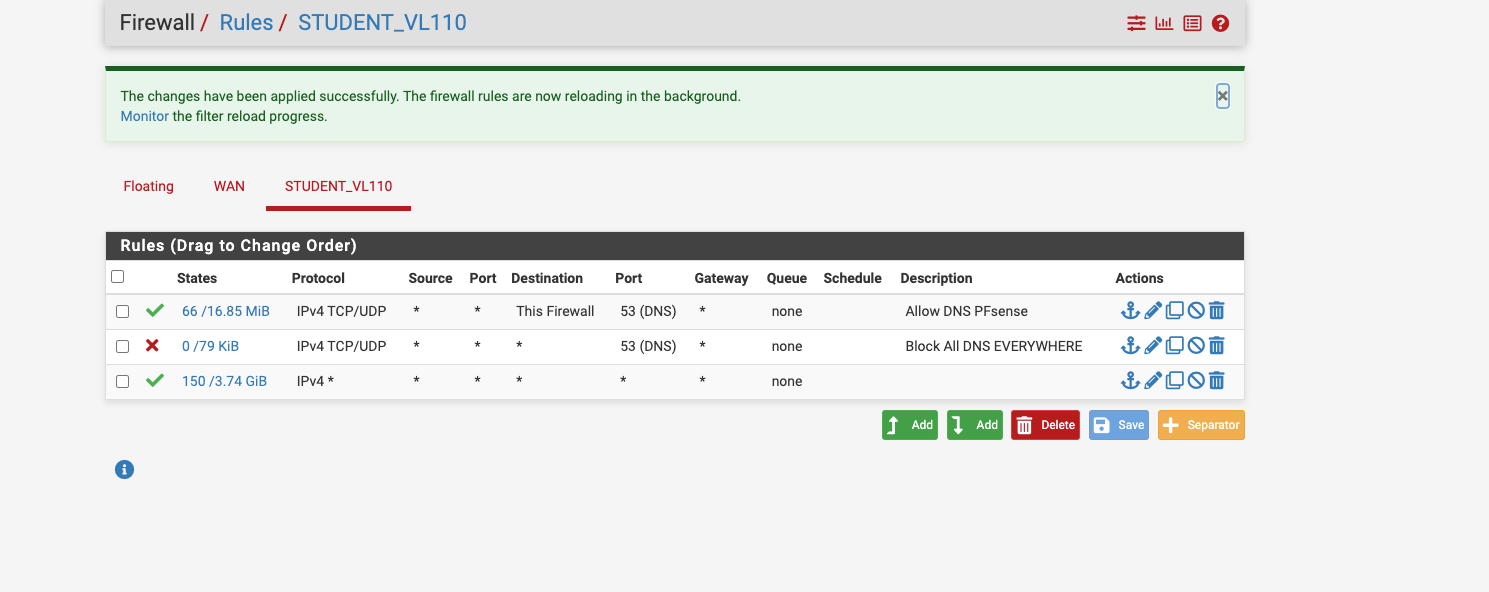
For example, my IoT vlan which my phone sits in has the following session. The rules for this vlan is pretty much any/any to the internet.
-
I remember when I had Sprint, I had to open a few ports for cell phone wifi calling... UDP ports 500, 4500, and 5061. I don't have an any-any rule so had to specify those. Check with your carrier, hopefully they can provide info on what they need open. I had to set 'Firewall Optimization' to conservative for Cisco Jabber 'soft-phone' calling and opened a handful of ports for that too, that I got from Cisco. Then work switched to Zoom phone, had to open a few more ports for that... So yea check with the carrier or soft-phone provider if there are high number ports that need to be open.
And to clarify, yes outbound ports... As I mentioned I have no any-any rule, and assumed same with the OP as he wouldn't need to open anything if he did... -
@marvosa making this change is what worked for me.
-
Just to be clear you should never need to open inbound ports for this. If you are blocking outbound traffic you may need to open ports there.
-
Thank you for any advanced help with this matter. as you can see I have tried every thing
TIm
-
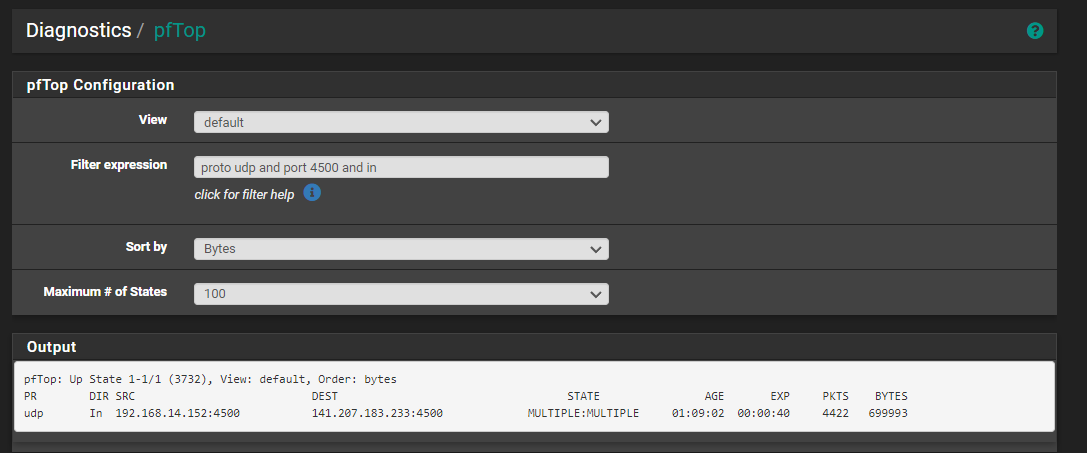
@msa1878 take one phone. Create an any/any rule for that one phone in your rules. Then see if WiFi calling works. See what states it creates using pftop.
-
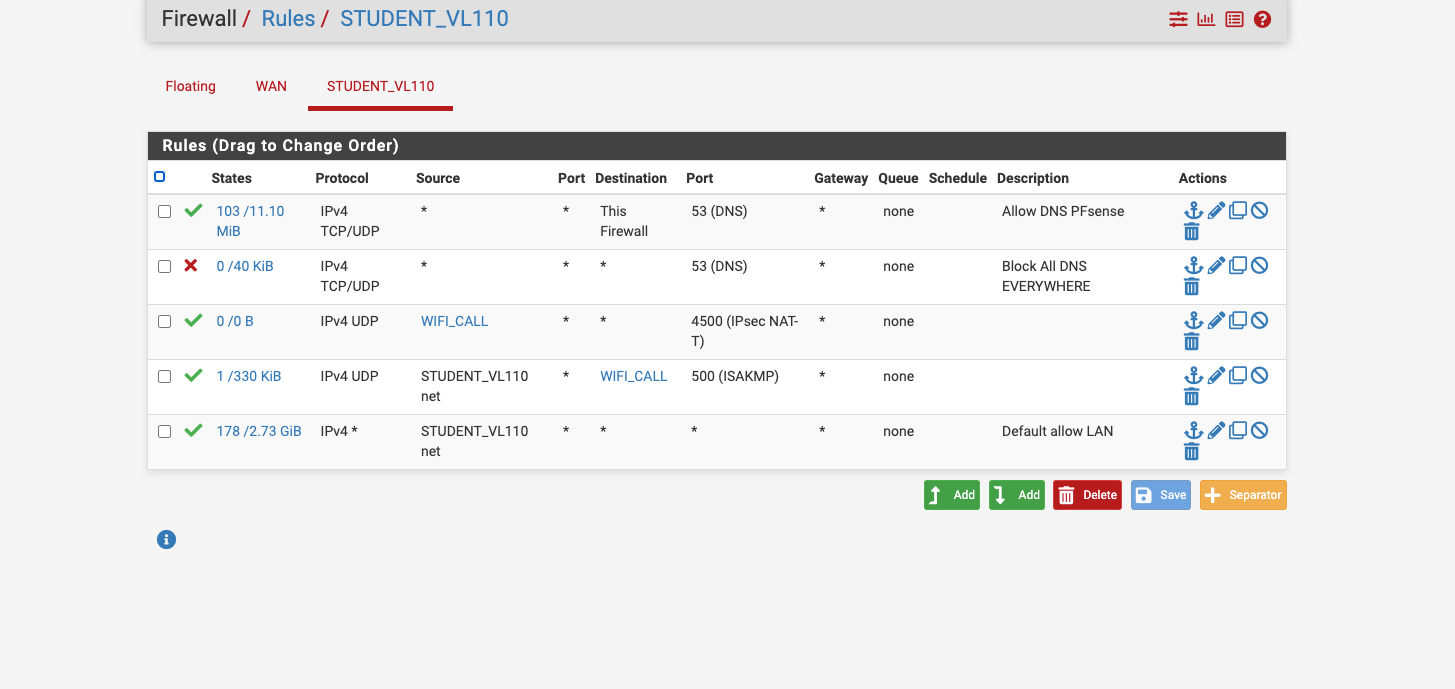
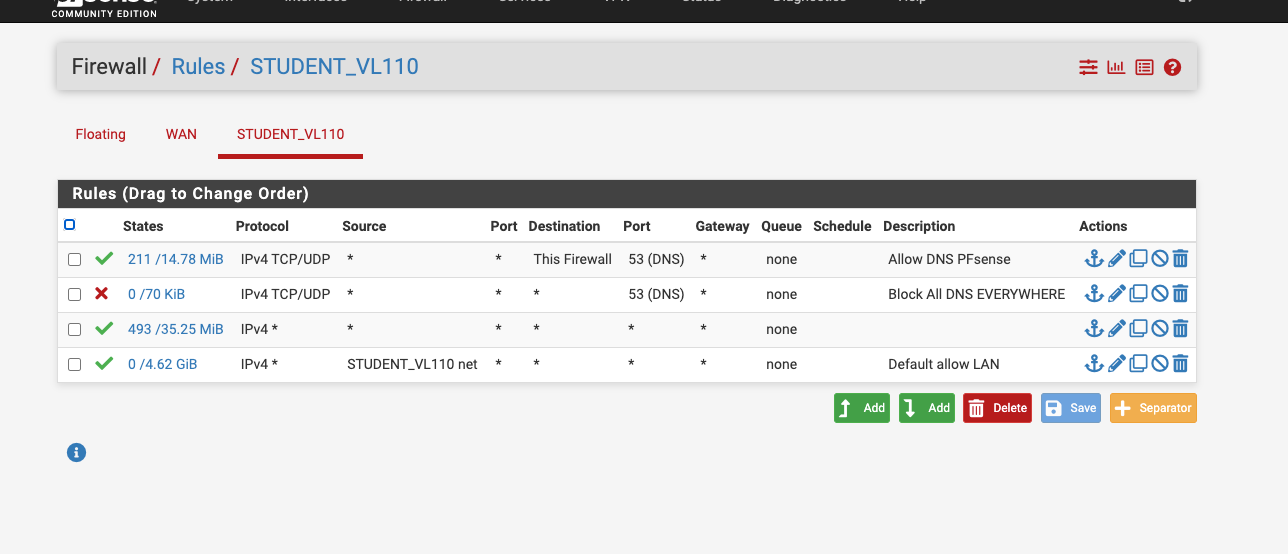
Would this rule reside on the lan rule or wan or floating? this is what I added per your suggestion.
Tim
-
@msa1878 I’m not understanding your rules. You have two rules that permit any/any. Just seeing that, WiFi calling should work.
-
-
@msa1878 I just wanted you to put in a new rule with the source IP being the phone you want to test BUT is WiFi calling working?
-
System -> Advance -> Firewall & NAT -> change Firewall Optimization Options to Conservative.
This is what worked for me. I have Verizon wireless. Before I made this change it would be hit or miss. After the change everything is working as expected.
-
@mikeisfly interesting. I didn’t have to make any changes. I have VZW
-
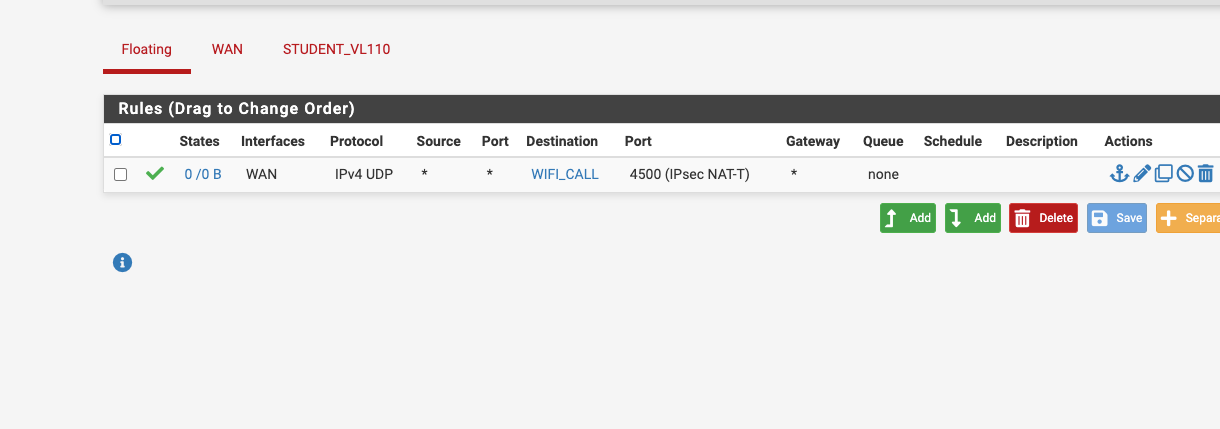
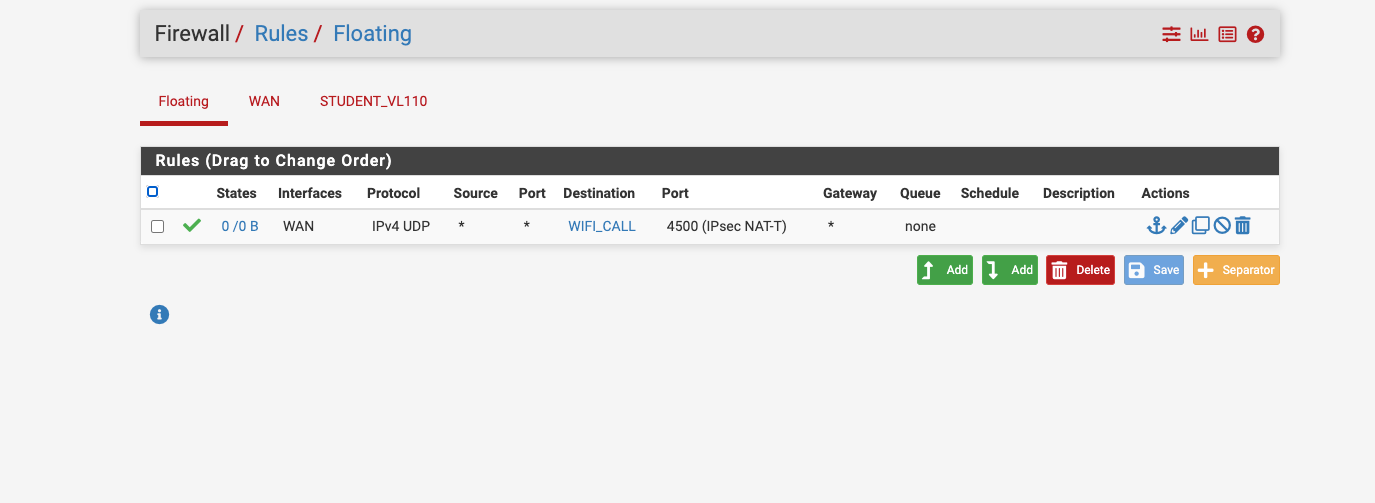
You should not have any rules allowing that IPSec traffic inbound. So not on WAN or as Floating rules applied to WAN. All the IPSec connections for that are opened outbound.
The wifi calling might be trying to use some hardcoded DNS which would be blocked by your rules.
-
Haven't checked ...the day got away from me... I will let you know later.
Thank you for your support in this
-
I had a chance to look at this fully... my cellphone is 10.110.9.99 and I look at the pftop session and the cellphone doesn't even reach out to port 4500 or doesn't trigger a UDP port 4500 session
I did make a rule directly allowing 10.110.8.99 cellphone to use port 4500.
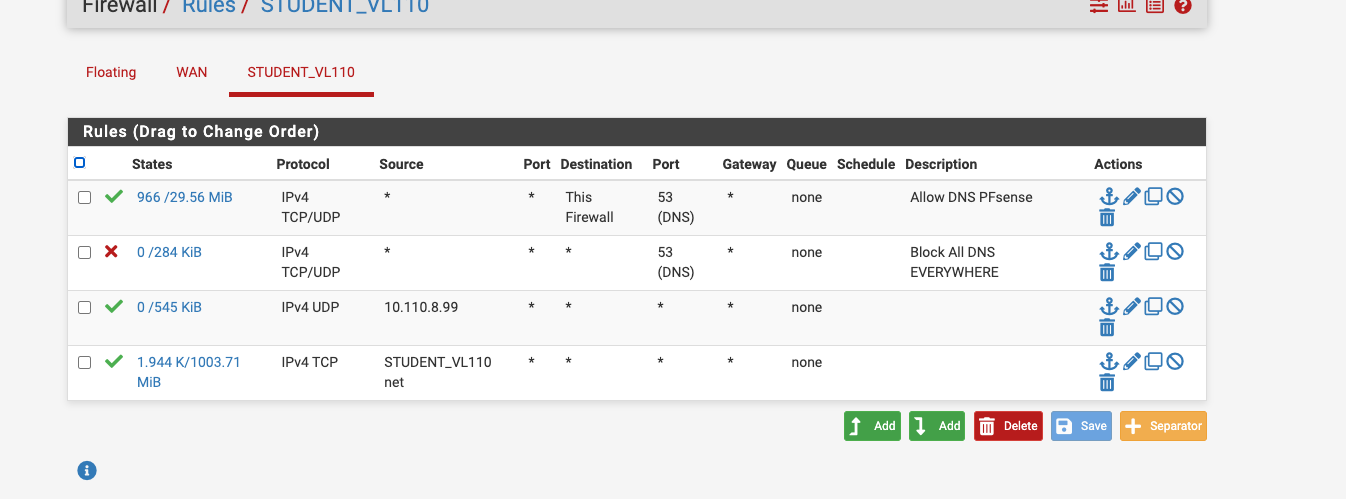
Any suggestions?
-
@msa1878 said in PFSENSE WIFI CALLING:
Any suggestions?
Run packet capture, filtering on the IP or MAC address, to see what's happening.