Simple firewall rules are not working?
-
I'm simply trying to block outbound traffic, and allow certain traffic using the floating rules.
I've also tried this with the WAN interface directly, and not floating but still, I get no ICMP for a ping to 8.8.8.8, no we browsing to any HTTPS website and nslookup lookups are shown as blocked.
Any ideas?
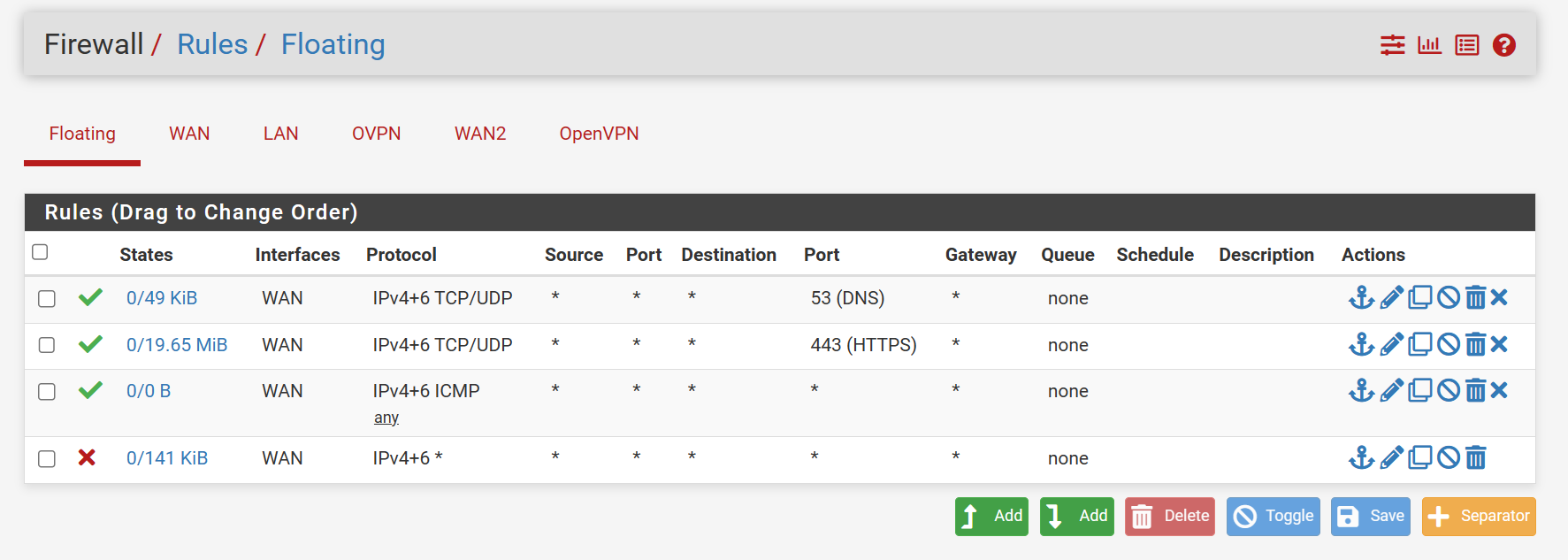
-
@deanfourie Im not following what you are trying to do here and the WAN rules you posted dont seem fully fleshed out.
What do your outbound rules look like?
Your inbound rules you are allowing port 443 which i assume you have pfsense GUI listening in on and based on the amount of bytes sent/received in your screen shot it shows to be working. -
@deanfourie said in Simple firewall rules are not working?:
tried this with the WAN interface directly
WAN rules would be used to allow traffic from the Internet. Allowing source * to 443 on WAN would allow the Internet/WAN to log in to pfSense.
I suggest not using floating rules until you get things working, since floating rules can behave what might seem a bit odd at times, with quick vs not-quick. https://docs.netgate.com/pfsense/en/latest/firewall/floating-rules.html
Blocking outbound from LAN to Internet would be via rules on the LAN interface.
-
@SteveITS I would prefer to block on the WAN interface, and add required rules to allow specific traffic.
Why would a simple block any proto, any port, any host, ipv4+ipv6 on WAN interface not stop internet traffic of any protocol.
This should work...
-
@deanfourie By default there are no rules on WAN so all inbound traffic on WAN is blocked.
You started out talking about outbound traffic but then only refer to WAN which would be inbound traffic...firewall rules apply when a packet arrives on an interface. So if you want to block a packet from LAN to Internet, normally the rule is put on LAN.
Floating rules can have a direction but as noted they're more complex. https://docs.netgate.com/pfsense/en/latest/firewall/floating-rules.html#direction And allowing inbound :443 on WAN allows the world to try to log in to your router.
-
@deanfourie said in Simple firewall rules are not working?:
@SteveITS I would prefer to block on the WAN interface, and add required rules to allow specific traffic.
Why would a simple block any proto, any port, any host, ipv4+ipv6 on WAN interface not stop internet traffic of any protocol.
This should work...
Because putting block rules on the WAN will only block devices on the WAN.
Rules only work on an interface for the devices attached to that interface.
So if you want to block outbound traffic from your LAN devices, you put the rule on the LAN interface. -
Ok thanks, I have it working on the LAN interface now.
My only reasoning around wanting to block on the WAN interface was for devices that may not actually sit on my subnet.
Say ghost devices sitting on a completely different subnet.
Say I have a LAN subnet of 192.168.10.0/24 and there are some unknown and untrusted devices on 192.168.20.0/24, this traffic will now not be blocked by the rules defined for the LAN interface.Sure, i understand that any traffic destined for the internet needs to leave via the 192.168.10.0 network. But you know.......
The setup is for security and also a bit of learning. I have never really done anything regarding blocking outbound, so figured might as well give it a go.
Not sure if this is a waste of time as I'm sure any malicious traffic these days would probably just be sent over HTTPS.
Out of curiosity, anyone doing SSL inspection / stripping? How are you sure your HTTPS traffic is clean? I'm considering dedicating some hardware to do this.
Thanks
-
@deanfourie said in Simple firewall rules are not working?:
Say I have a LAN subnet of 192.168.10.0/24 and there are some unknown and untrusted devices on 192.168.20.0/24,
How would those leave pfsense? If this network is not setup in pfsense, pfsense is not going to route it or nat it.. and by default the rules on lan are limited to the lan network anyway.
So say some 192.168.20.x IP somehow was setup to talk to your pfsense IP on 192.168.10 as it gateway.. Pfsense wouldn't allow it because that is not part of "lan net" your 192.168.10.0/24 network - even if you had a rule setup that allowed all and didn't limit to lan net, pfsense wouldn't nat it to your pfsense wan IP.. Because 192.168.20 wouldn't be in the outbound nat rules.
So unless you have specifically setup to route and nat a network, some "unknown" IP isn't going to be able to do anything with pfsense.
-
@deanfourie other subnets would typically have their own interface, and rules can be copied there.
Re SSL/TLS inspection, it requires a proxy and certificate all the devices trust. We run it on our clients’ PCs via Bitdefender’s corporate/cloud a/v. The one down side is you can’t see the site’s real cert in your browser.
-
@johnpoz Yea true!
Everything needs to leave via the LAN gateway and then be natted.
Theres not other way around that right...?
-
@deanfourie said in Simple firewall rules are not working?:
Theres not other way around that right...?
Around what? By default the lan rules would be limited to IPs in the actual lan net say 192.168.10.0/24, so even if you had someone setup 192.168.11.x/23 on their device so that they could talk to 192.168.10.x, pfsense would not allow the traffic, nor nat it to whatever your wan IP is so unlikely they could talk to anything past pfsense.