Very Basic IPv6 security question.
-
@RobbieTT said in Very Basic IPv6 security question.:
No, you are mistaken. When configured as stated the DHCPv6 leases look like:
2axx:xxx:xxxx:1::16be
With the ':1::' above being this particular LAN network prefix and the remaining 4 digits identifying the host.
You also get the full GUA, privacy addresses et al.
You know : I know I'm doing something wrong, and I'm trying to understand what I'm doing wrong for long time now.
So, Let try again :
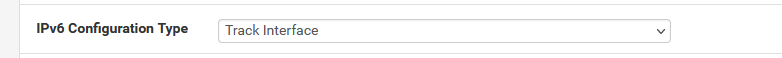
with :
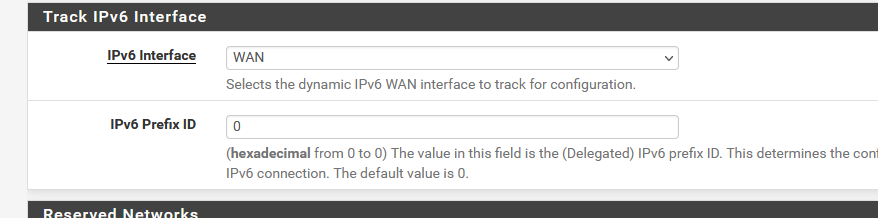
( My ISP router announces in it's own GUI that it has a /56 available, but pfSense (dhcp6c) doesnt show a "256" - it shows 0 to 0 ? So I chose zero ... )
dhcp6c manages to obtain the prefix "2a01:cb19:907:a6dc" - and only this prefix.
Anyway, I set my LAN V6 to tracking (the WAN interface), re assign the DHCP server v6 to :
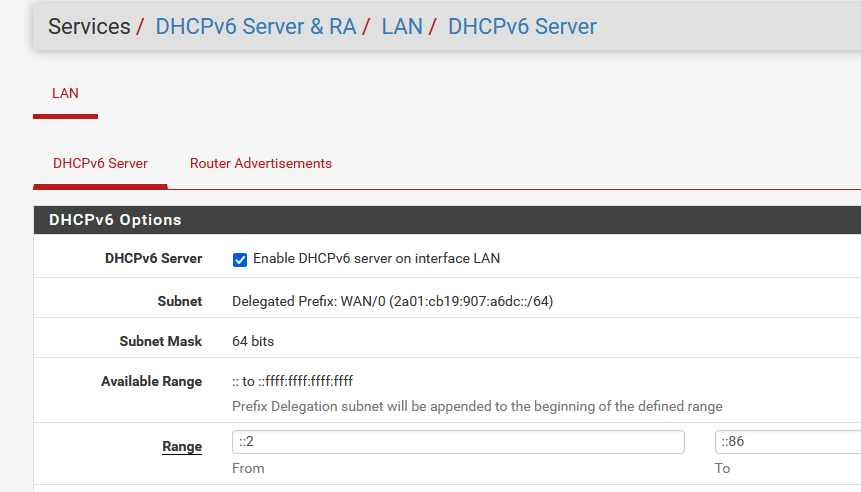
and reboot.
When done reboot : the GUI shows :
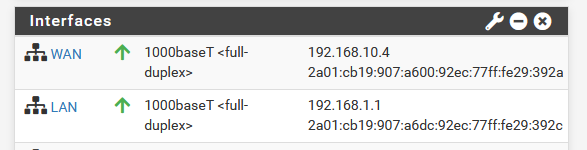
That's not a nice xxxxxxxx::1 as you mentioned.
How do I force a ::1 force LAN pfSense ? What did I forget ?Now : my PC :
I "ipconfig /renew" :
Carte Ethernet Ethernet :
Suffixe DNS propre à la connexion. . . : bhf.net Description. . . . . . . . . . . . . . : Intel(R) Ethernet Connection (11) I219-LM Adresse physique . . . . . . . . . . . : A4-BB-6D-BA-16-A1 DHCP activé. . . . . . . . . . . . . . : Oui Configuration automatique activée. . . : Oui Adresse IPv6. . . . . . . . . . . . . .: 2a01:cb19:907:a6dc::c7(préféré) <======= champagne !! Adresse IPv6 de liaison locale. . . . .: fe80::daa9:bcf8:99cd:717e%11(préféré) Adresse IPv4. . . . . . . . . . . . . .: 192.168.1.6(préféré) Masque de sous-réseau. . . . . . . . . : 255.255.255.0 Bail obtenu. . . . . . . . . . . . . . : vendredi 21 juillet 2023 13:04:59 Bail expirant. . . . . . . . . . . . . : samedi 22 juillet 2023 13:11:59 Passerelle par défaut. . . . . . . . . : fe80::92ec:77ff:fe29:392c%11 192.168.1.1 Serveur DHCP . . . . . . . . . . . . . : 192.168.1.1 IAID DHCPv6 . . . . . . . . . . . : 346340205 DUID de client DHCPv6. . . . . . . . : 00-01-00-01-26-59-DF-8D-A4-BB-6D-BA-16-A1 Serveurs DNS. . . . . . . . . . . . . : 192.168.1.1 NetBIOS sur Tcpip. . . . . . . . . . . : Activé Liste de recherche de suffixes DNS propres à la connexion : bhf.netSo, ok, thanks you for re forcing me to use tracking mode.
How can I get my short (simple) LAN IPv6 back, the one ending with a ::1 instead of this very long :
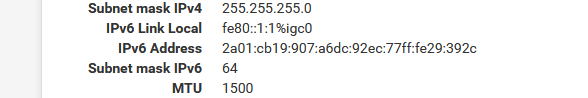
is there a way ?
-
My guess is that as you only have 1 subnet / LAN defined, so no need for a choice of prefix ID (I have 3 local networks defined).
Any leases showing here:
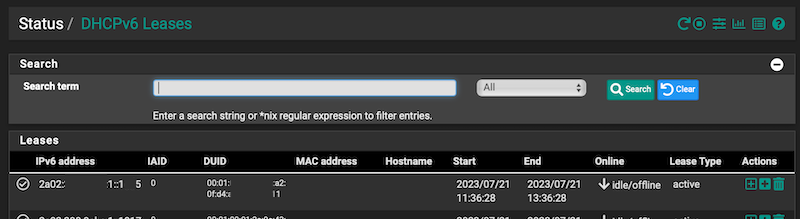
An example client shows the following addresses:
en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500 options=6463<RXCSUM,TXCSUM,TSO4,TSO6,CHANNEL_IO,PARTIAL_CSUM,ZEROINVERT_CSUM> ether f8:4d:xx:xx:26:88 inet6 fe80::xx:80c4:xxxx:7eef%en0 prefixlen 64 secured scopeid 0xf inet6 2a02:xxxx:xxxx:1:1808:6752:xxxx:a287 prefixlen 64 autoconf secured inet6 2a02:xxxx:xxxx:1:7c15:c736:xxxx:7732 prefixlen 64 deprecated autoconf temporary inet 10.0.1.10 netmask 0xffffff00 broadcast 10.0.1.255 inet6 2a02:xxxx:xxxx:1::1b06 prefixlen 64 dynamic inet6 fd83:xxxx:239c:4fb4:8cd:5e06:xxxx:def8 prefixlen 64 autoconf secured inet6 fd8d:xxxx:3a57:4f07:142f:f915:xxxx:4cef prefixlen 64 deprecated autoconf secured inet6 2a02:xxxx:xxxx:1:b5b2:5b0a:xxxx:6e82 prefixlen 64 deprecated autoconf temporary inet6 2a02:xxxx:xxxx:1:f186:b1b0:xxxx:3a5b prefixlen 64 autoconf temporary nd6 options=201<PERFORMNUD,DAD> media: autoselect status: activeYou would probably benefit from your own thread as we are distracting from this one. Apologies to @guardian.
 ️
️ -
@guardian said in Very Basic IPv6 security question.:
Have I configured pfSense IPv6 Correctly? I am attempting to configure a VLAN6 which I am connecting over a trunk to an SG300 switch, and ultimately to an access port on GE2. The IPv4 is working fine, I get an IP assignment, and a DHCP server, but the IPv6 isn't working. I have a linux laptop connected to GE2 with DHCP configuration for both IPv4/v6. I have no IPv6 connectivity - a ping6 to 2607:f8b0:400b:804::2003 from the laptop results in Destination unreachable: Beyond scope of source address, but is successful if executed from the pfSense WebGUI.
The laptop has an fe80::/64, and the Default Route has an fe80:: address as well. There are no other entries, and if I attempt to run ping6 against the Defaut route, I get invalid argument. For some reason ping6 does not liek fe80 addresses--even when I fully expanded :: with the appropriate number of 0000 to make 8 complete hextets
I need to determine if the problem is with pfSense, the SG300, or the laptop, so any guidance would be much appreciated.
You have to configure the VLAN on every device that uses it or it passes through. For example, my guest WiFi is on VLAN3. I configured VLAN3 on the same interface as my main LAN, on the access point for the 2nd SSID and also both ports on my switch that it had to pass through.
Link local addresses are often used for routing. On Rogers, your default route will be a link local address and you will also have a global address on your WAN interface, but it's not used for routing.
BTW, I see you have a prefix delegation size of 64. That will get you only a single /64 prefix. You want to use 56, which will get you 256 /64s.
Also, why are you using DHCPv6 on your LAN? Unless you have a specific need for it, I'd recommend you stick with SLAAC. Also, thanks to some genius at Google, Android devices don't support DHCPv6.
I'd recommend you start simple and then work out what else you want, after you get pfSense working. For example, configure your VLAN after the main LAN is working.
-
@Gertjan said in Very Basic IPv6 security question.:
Because I know that I will receive "2a01:cb19:xO7:a6dc" as a prefix, I "hard coded" it.
Is that address from Rogers? If not, you shouldn't be using it. My addresses from Rogers start with 2607.
-
@Gertjan said in Very Basic IPv6 security question.:
Again : I know, treating the prefix as a static value is plain wrong / can bite you back in the future (== break your IPv6 networking).
This is one area where Rogers is really good. I've had the same prefix for a few years. Even my IPv4 address is virtually static and my IPv4 host name changes only when I change hardware.
-
@JKnott said in Very Basic IPv6 security question.:
Also, why are you using DHCPv6 on your LAN? Unless you have a specific need for it, I'd recommend you stick with SLAAC. Also, thanks to some genius at Google, Android devices don't support DHCPv6.
Just so we are all on the same page with the applicable pfSense options:
-
Managed
The firewall will send out RA packets and addresses will only be assigned to clients using DHCPv6. -
Assisted
The firewall will send out RA packets and addresses can be assigned to clients by DHCPv6 or SLAAC. -
Stateless DHCP
The firewall will send out RA packets and addresses can be assigned to clients by SLAAC while providing additional information such as DNS and NTP from DHCPv6.
Coming from different router environment I originally selected "Stateless DHCP," given that I used SLAAC previously on a different OS. A Netgate developer suggested "Assisted" instead and it solved a brace of annoying issues and is friendly enough for 'droid clients too.
 ️
️ -
-
@RobbieTT said in Very Basic IPv6 security question.:
Coming from different router environment I originally selected "Stateless DHCP," given that I used SLAAC previously on a different OS. A Netgate developer suggested "Assisted" instead and it solved a brace of annoying issues and is friendly enough for 'droid clients too.
I use unmanaged. Between SLAAC and RDNSS, you generally have all you need.
As has been mentioned, start simple and go from there, as you get things working.
-
@JKnott said in Very Basic IPv6 security question.:
As has been mentioned, start simple and go from there, as you get things working.
Cannot argue with that.

 ️
️ -
@JKnott said in Very Basic IPv6 security question.:
Because I know that I will receive "2a01:cb19:xO7:a6dc" as a prefix, I "hard coded" it.Is that address from Rogers?
No. I'm living in the original, old world, not the recent one ;)
To be exact : 2a01:cb19:907:a6dc
ISP Orange, France.@RobbieTT said in Very Basic IPv6 security question.:
Just so we are all on the same page
Managed, for myself.
I'm doing my best to give Android devices a hard time on my networks.
I'm joking of course, I don't have any Android devices so I'm not in the need of the SLAAC thing.
( or am I saying the same thing differently ? ) -
@Gertjan said in Very Basic IPv6 security question.:
No. I'm living in the original, old world, not the recent one ;)
To be exact : 2a01:cb19:907:a6dc
ISP Orange, France.Sorry, I was getting posters mixed up. I thought I was replying to @guardian, who is on Rogers.
-
@RobbieTT said in Very Basic IPv6 security question.:
You are not configured for it to work just yet. For the Interfaces / WAN I would start by checking the boxes below and you will also have to determine what the prefix delegation size is from your ISP. A nice fat /48 is typical (as I have on the example below), with some ISPs trimming this down to a /56 (as it is still massive). Hopefully you don't just have a /64 but I understand that there are some ISPs that are that dumb/restrictive (particularly in the US it seems).
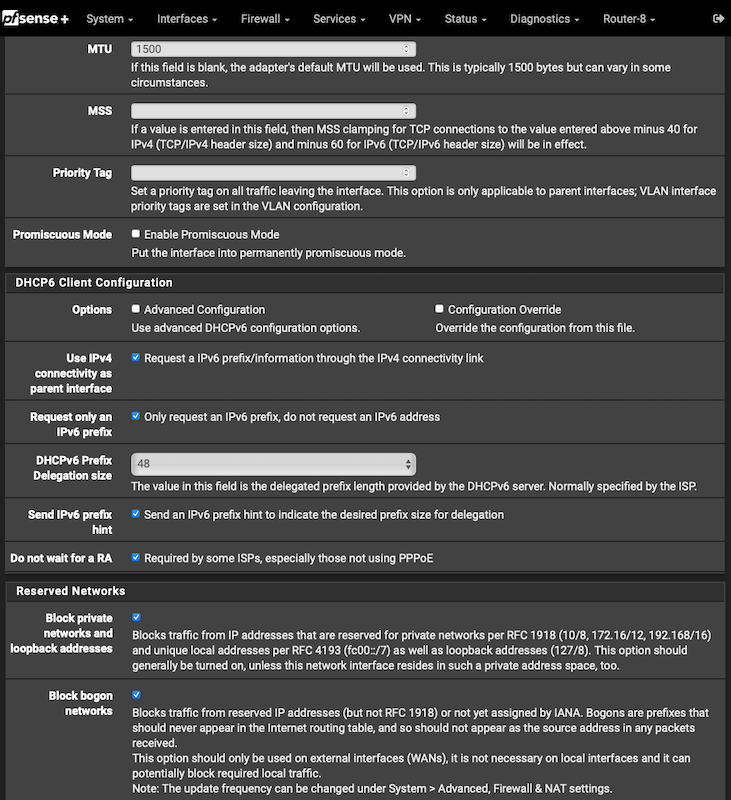
More to do after that on your LAN(s)/VLANs, DHCPv6 Server and Router Advertisements but the above is as good as any starting point. That and reading the section in the pfSense manual.
 ️
️@RobbieTT - Thanks very much - when I made these changes I now have IPv6 Connectivity being passed through to the VLAN, and hence the laptop. For some reason the connection monitor isn't working - it was working before, but then everything else wasn't working, so it didn't matter. Is there a way to fix it? FYI I can ping this address successfully from the Diagnostics menu and also from the shell, so I'm wondering if the process got hung somehow (how do I restart it?).
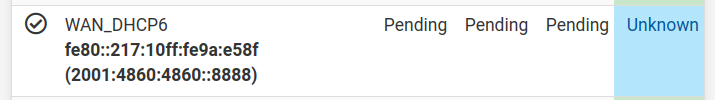
For the benefit of anyone who comes after me, (for Rogers Canada in July 2023) the deligation is "only" 56, and here is how I am set up now on the WAN:
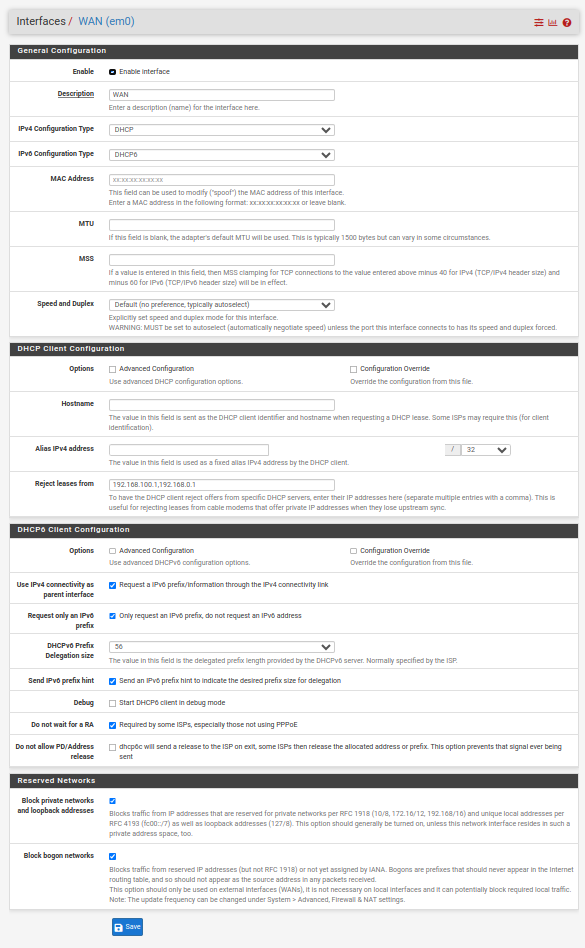
-
@guardian said in Very Basic IPv6 security question.:
For some reason the connection monitor isn't working - it was working before, but then everything else wasn't working, so it didn't matter. Is there a way to fix it?
What address are you using? It has to be a global address, not link local.
-
If it is the first hop to the ISP's node then link local (fe80) would be fine or even expected. Beyond that it would need a global target to ping against.
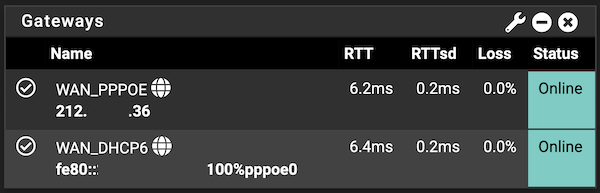
-
In my experience, it didn't work with the link local address. I did a traceroute to Google and used the first global address that turned up.
-
I just tried again, using the default route fe80::217:10ff:fe9. While it is accepted, the dashboard shows packet loss.
-
@JKnott
Understood - just clarifying that a global address is not always needed for a gateway to node hop.
 ️
️ -
@RobbieTT said in Very Basic IPv6 security question.:
global address is not always needed for a gateway to node hop.
very true.. But what would be needed to be able to ping something you monitoring that has gua. Is a gua to send the answer back too.
Also possible the link local address might not even answer ping, etc.
-
@johnpoz said in Very Basic IPv6 security question.:
Also possible the link local address might not even answer ping, etc.
That appears to be the case here.
-
@johnpoz said in Very Basic IPv6 security question.:
very true.. But what would be needed to be able to ping something you monitoring that has gua. Is a gua to send the answer back too.
Also possible the link local address might not even answer ping, etc.
Clearly it should respond to ICMP6 (it is an IPv6 requirement) but ISPs...
In my example above I didn't set anything manually as the link-local for the gateway comes via the RA and pfSense adopts it:
Jul 20 18:43:40 rtsold 67156 Received RA specifying route fe80::xxx:xxxx:xxxx:x100 for interface wan(pppoe0)I'm a bit of a purist, keeping the gateway monitor limited to the gateway, rather than the wider internet. One of my servers runs a GUA ping graph via PingPlotter 24/7, to monitor the broader upstream connectivity.
 ️
️ -
@RobbieTT said in Very Basic IPv6 security question.:
Clearly it should respond to ICMP6
ICMP sure - but not the "ping" echo request of ICMP.. that is not actually "required" for IPv6 to function... But I believe the rfc says to allow them.. And pfsense does..
# IPv6 ICMP is not auxiliary, it is required for operation # See man icmp6(4) # 1 unreach Destination unreachable # 2 toobig Packet too big # 128 echoreq Echo service request # 129 echorep Echo service reply # 133 routersol Router solicitation # 134 routeradv Router advertisement # 135 neighbrsol Neighbor solicitation # 136 neighbradv Neighbor advertisement pass quick inet6 proto ipv6-icmp from any to any icmp6-type {1,2,135,136} ridentifier 1000000107 keep state # Allow only bare essential icmpv6 packets (NS, NA, and RA, echoreq, echorep) pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type {129,133,134,135,136} ridentifier 1000000108 keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type {129,133,134,135,136} ridentifier 1000000109 keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type {128,133,134,135,136} ridentifier 1000000110 keep state pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type {128,133,134,135,136} ridentifier 1000000111 keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type {128,133,134,135,136} ridentifier 1000000112 keep state pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type {128,133,134,135,136} ridentifier 1000000113 keep statehttps://www.rfc-editor.org/rfc/rfc4890#section-4.3.1
4.3.1. Traffic That Must Not Be Dropped Error messages that are essential to the establishment and maintenance of communications: o Destination Unreachable (Type 1) - All codes o Packet Too Big (Type 2) o Time Exceeded (Type 3) - Code 0 only o Parameter Problem (Type 4) - Codes 1 and 2 only Appendix A.4 suggests some more specific checks that could be performed on Parameter Problem messages if a firewall has the necessary packet inspection capabilities. Connectivity checking messages: o Echo Request (Type 128) o Echo Response (Type 129) For Teredo tunneling [RFC4380] to IPv6 nodes on the site to be possible, it is essential that the connectivity checking messages are allowed through the firewall. It has been common practice in IPv4 networks to drop Echo Request messages in firewalls to minimize the risk of scanning attacks on the protected network. As discussed in Section 3.2, the risks from port scanning in an IPv6 network are much less severe, and it is not necessary to filter IPv6 Echo Request messages.But as you stated - not all ISPs follow the RFCs ;) and they could have some rate limiting on it, etc.
If you read this part of the RFC
A.5. ICMPv6 Echo Request and Echo Response Echo Request (Type 128) uses unicast addresses as source addresses, but may be sent to any legal IPv6 address, including multicast and anycast addresses [RFC4443]. Echo Requests travel end-to-end. Similarly, Echo Responses (Type 129) travel end-to-end and would have a unicast address as destination and either a unicast or anycast address as source. They are mainly used in combination for monitoring and debugging connectivity. Their only role in establishing communication is that they are required when verifying connectivity through Teredo tunnels [RFC4380]: Teredo tunneling to IPv6 nodes on the site will not be possible if these messages are blocked. It is not thought that there is a significant risk from scanning attacks on a well-designed IPv6 network (see Section 3.2), and so connectivity checks should be allowed by default.So ok you won't be able to do teredo if you block them.. But that is pretty much dead..
But I read
It is not thought that there is a significant risk from scanning attacks on a well-designed IPv6 network (see Section 3.2), and so connectivity checks should be allowed by default.
But does that mean its required to allow - I don't think so, other than teredo..