Captive portal not working by openvpn as server mod for users
-
Hello
I set up an openvpn server and client users can connect From WAN to pfsense and access the LAN subnet.
I used FreeRadius to define the user, in FreeRadius there is a section called "Traffic and Bandwidth" where options are specified to define amount of traffic and speed, but it seems that they do not work and users use unlimited amount of traffic and maximum speed I think these options are only compatible with Captive Portal and do not work individually.
The problem is that captive portal cannot be used for openvpn users.
I couldn't find a way to limit users to a specific internet traffic qouta.In CP, there is no Openvpn option as an interface, and CP cannot be activated on it
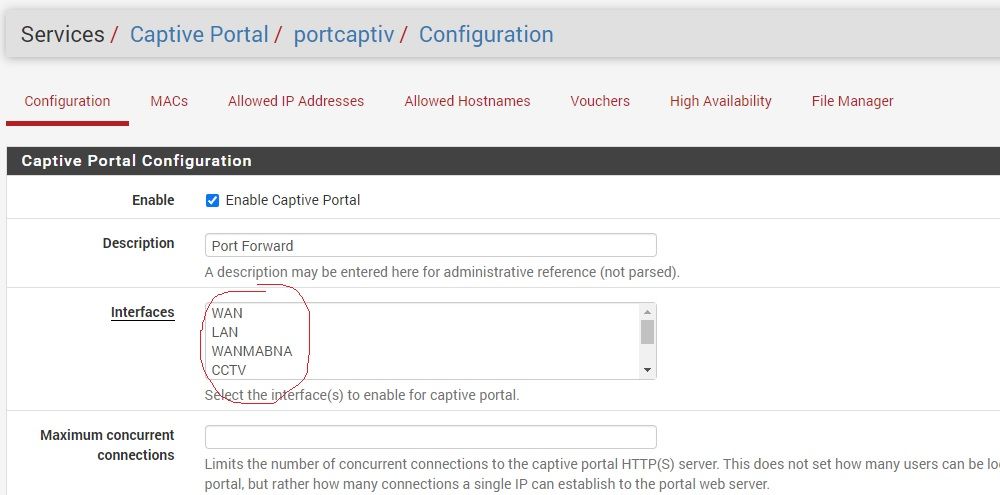
It seems that activating the interface for Openvpn is only possible for the Openvpn as client mod, and it is not possible in Openvpn Server mode, and all the rules are done by the "openvpn" tab in the FW part, and it is not possible to introduce the "openvpn" tab to the CP in the mode of an interface.
Is there a solution?
-
@reza3sw said in Captive portal not working by openvpn as server mod for users:
Is there a solution?
I've been looking several days for a comprehensible answer.
I have to default to : "just don't do that".
It's like fish on dry land : it has been tried many times, it still doesn't work out.
-
@Gertjan said in Captive portal not working by openvpn as server mod for users:
I have to default to : "just don't do that".
It's like fish on dry land : it has been tried many times, it still doesn't work out.
Hello and thank you for your reply.
I found a solution for this issue, if Openvpn is used in server mode and on TAP Layer 2, you can assign an interface to it and perform the desired activities on that interface in CP and it works correctly. .But there is a big problem that makes this method obsolete, the problem is that you can't use Openvpn in TAP Layer2 mode on Android, IOS.
I think we should ignore this issue in Pfsense and look for another solution.
I hope they fix this problem in Pfsense in the future.
-
@reza3sw said in Captive portal not working by openvpn as server mod for users:
I hope they fix this problem in Pfsense in the future.
OpenVPN usage and captive portal usage have a thing in common :
Accepting "non trusted" users so they can authenticate , and then use a trusted resource.OpenVPN (server) is typically used so you can expose inside, protected resources to visitors who are coming in over the WAN, so they can access local resorces.
The captive portal is sued for 'inside' users, so they can access world's most famous resource : an Internet access.
Having ''LAN' local users access a local OpenVPN server ? ( ?? ! )
Btw : it's quite common that captive portal users first authenticate against the captive portal.
Then they activate their OpenVPN client, and use the protected Internet access to do their thing.Now, I'm just a pfSense user like you, so, what do I know ?
But you could be the first that wants to use a captive portal on an interface with a OpenVPN attached to it .... (something like that).
Let me say it like this : something needs to be 'fixed', maybe. But not pfSense ^^ -
What you said is correct and CP is only for local network or LAN.
I think you misunderstood my point, OpenVPN users connect to pfsense through WAN and their access to LAN is opened. Users are not local
But in Pfsense, there is no way to limit amount of traffic for Openvpn users, and the parts in Freeradius do not work without CP.Openvpn is used by default in Layer 3 or TUN mode. But as far as I understand, CP imposes restrictions on the local network in Layer 2 mode.
When you start Openvpn Server in TAP Layer2 mode, you can assign an Interface to this Openvpn and put it in Bridge mode with LAN Interface.From now on Openvpn users can get their address from DHCP on LAN and be part of LAN network, maybe this is a trick to cheat CP, Openvpn, but as I said you can't use it in TAP mode on Android, IOS and there is this limitation, so this solution only works on Windows and Linux.
And I am still looking for a solution to solve this problem, because my users are different (Windows, Android, IOS, ..)
-
@reza3sw said in Captive portal not working by openvpn as server mod for users:
My users connect via WAN from outside as Openvpn.
And then you 'redirect' the OpenVPN into the portal - from the wrong interface side ?
Or : redirect to an OPTx style interface, and connect that interface to another OPTx interface which has the portal activated ?
My advise : don't even call Houston. This question will auto vanish ...When I ask worlds biggest search engine about OpenVPN (server) I find a lot about OpenVPN users and bandwidth limiting.
Close to nothing about quota (data usage) management. Because OpenVPN was never meant to do such a thing. ?.
The portal, I get it, can do quota management like : user X can consume XX Mbytes per day. This works because the portal authenticates the user upon portal login, and continues to do a "connection audit" every 300 seconds or so, and amongst others, the connection is metered, so it is easier (simply : possible) to do a daily/weekly/whatever quota test.
This works pretty well, I've used it a couple of time just for the fun. -
@Gertjan
What I mean is that the users are outside the work environment and through the Internet and Openvpn they can connect to the WAN interface through Public IP and access the LAN network where files and other things exist in the work environment.Everything works fine, I just wanted to be able to limit bandwidth and amount traffic for users and I noticed that Freeradius can't limit without CP enabled and the problems I mentioned above occur when CP is enabled on the Openvpn interface. has it.
How do you limit amount of traffic for users who have been authenticate through Freeradius? I enter traffic and bandwidth daily in FreeRadius, but it doesn't work. This part only works when CP is active on the desired interface and users log in through CP that interface.
When the user is authenticated through CP and Freeradius, everything works, but when only Freeradius is used to authenticate users, the bandwidth limit options do not work, and the user has no limit.
I want to implement the following scenario, but I am having trouble.
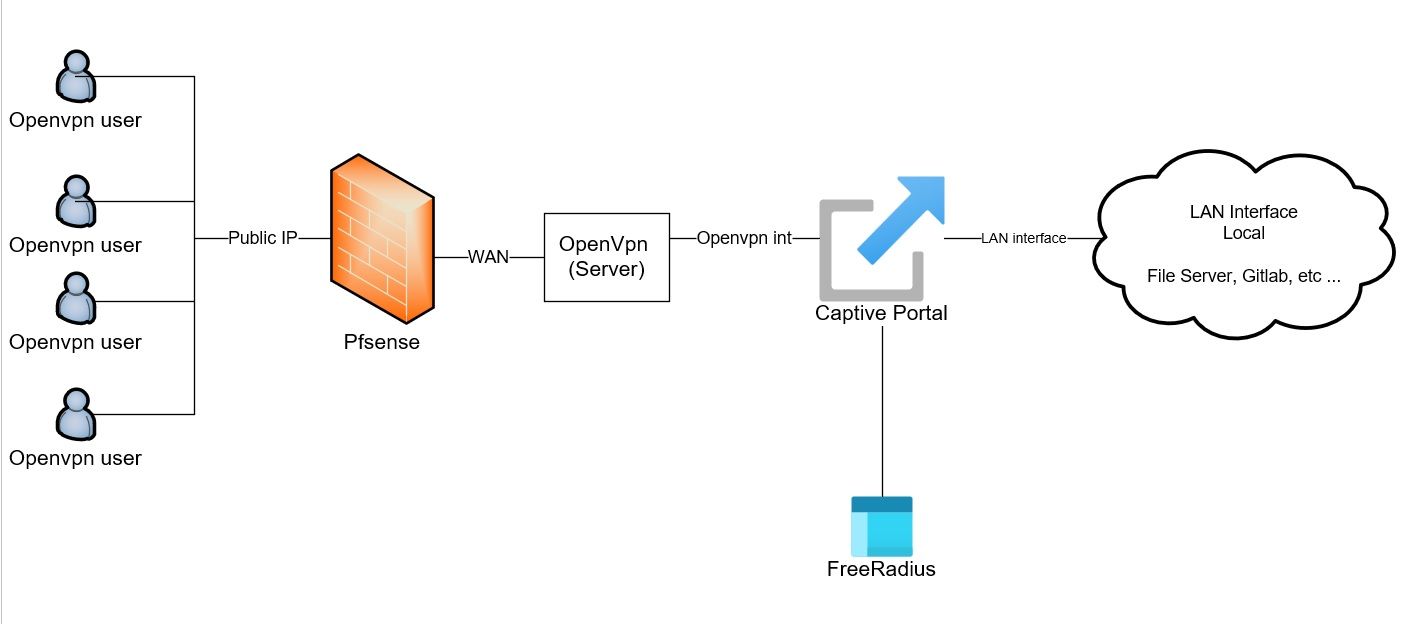
Openvpn Client from internet >WAN public IP > Pfsense > Openvpnserver> Captive Portal> Authenticate with freeradius > Access to My LAN
Everything is correct and users can connect and access the LAN network, but it is not possible to apply a limit to the traffic of users in Freeradius, there is an option to apply a limit in Freeradius, but it does not work on its own, and it must be used in addition to CP from This option is used. For this reason, I have to activate CP for Openvpn next to freeradius so that I can use the restriction option in freeradius, but it is not possible to activate CP on the Openvpn interface, I am now looking for a solution to apply the restriction to users, a requirement to use I don't have CP and any solution that can apply restrictions is good, but pfsense can apply restrictions to users only through CP and radius, but this method does not work for openvpn users.
I also followed this solution, but this solution didn't work either
https://forum.netgate.com/topic/141034/rate-limit-on-radius-reply-attributes-for-pppoe-connections-not-working