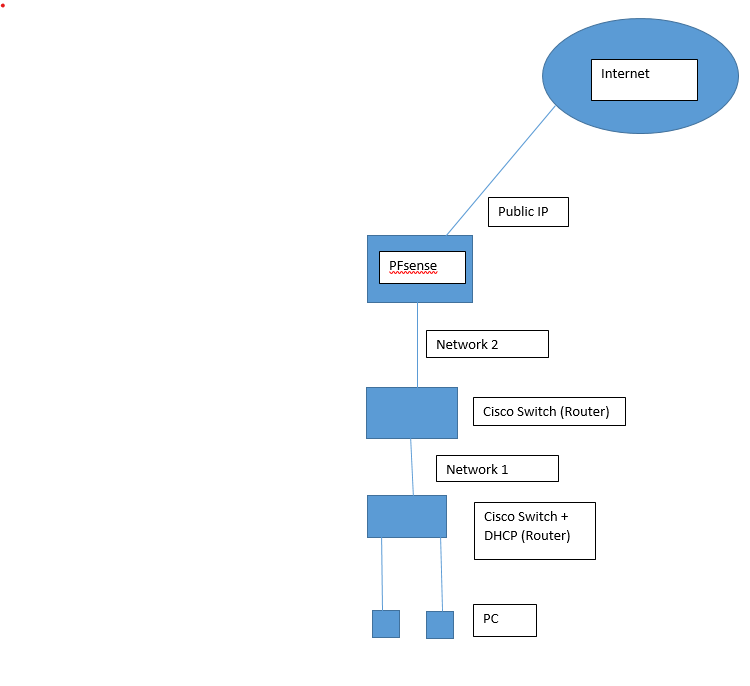
captive portal in complicated network
-
Behind the captive portal interface : use only 'dumb' switches.
If routers are used, then the MAC adresses of visiting clients are hidden, the captive portal can't "see" them anymore, it will only see the router's often called "WAN" interface MAC addresses.
That's can work, yes, is pretty broken, and tedious to manage.Select :
-
@emad4
Thank you GertganYou mean it is possible to apply captive portal on this network but it is not easy
-
If yo have Youtube somewhere : go here : Youtube Netgate
There are two (3 ?) special Captive portal where everything you want to know, and far more, is explained from a to z by the guy who created it.
The videos are old, but still pretty valid.
See them all. You'll have the answer. And also the answered to the question you haven't found yet. -
I will see but I uploaded the diagram and need how to activate captive portal in this scenario
Thank you again -
Well, first I need to know what this is :
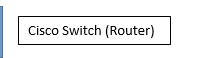
is it a switch (and don't care if it can do coffee, answering phone calls and do routing) ?
Is it a router ?Same thing here :
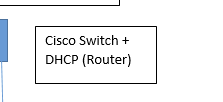
Same questions.
And why running a DHCP in the captive portal and not using the build in DHCP server that pfSense ?
Doing things the centralized way is a big plus.Anyway, you'll understand that you have to check this one :
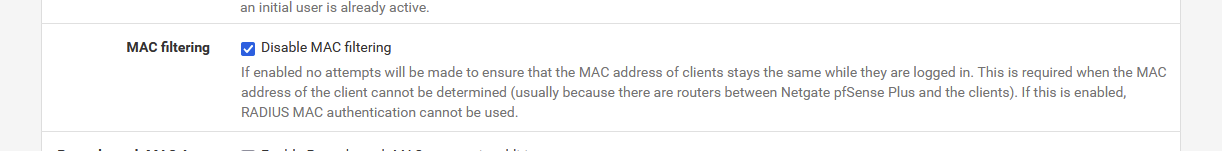
which means, from then on, the captive portal can only distinguish portal users by their IP addresses.
The MAC addresses you'll see are the MAC addresses of your routers ( ! )
So using the MAC addresses == useless. -
Yes , the Cisco Switch (Router) is a layer 3 switch which works as a router and has an ip address , same thing for (Cisco Switch + DHCP Router) is a layer 3 device which works as a router and dhcp is enabled on it , so it is distributing ip addresses to other computers. Moreover, I only made a subnet for the total network because I have more than 20 subnets and my plan is to use another pfsense server (one for captive which already exists and the other for radius server) but I experienced this problem which is, there are two switches configured as routers and have IPs addresses between pfsense and the clients.
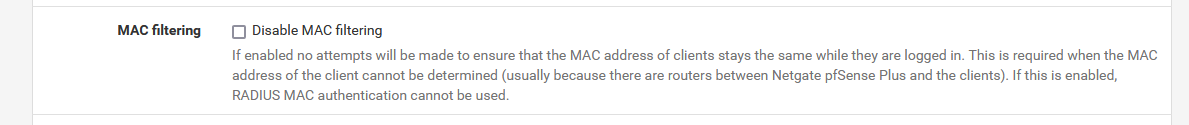
Concerning the MAC Filtering , I understood the concept you mentioned but where can I find it exactly ?
-
Captive portal networks are classic network, with a DHCP server (not needed if all clients use static IP settings) and DNS access (very important).
On a network, everything is based upon initiative of the client device.
A client has to ask a IP/lease, if it uses DHCP.
A client has to ask 'what is the IP of "apple.com" if it want to connect to apple.com.
etc.
pfSense serves requests if these are directed to it, or passes the traffic 'else where'.To understand how a captive portal could work : see here : https://en.wikipedia.org/wiki/Captive_portal
pfSense uses the 'http' method.
pfSense needs to be able to identity the device. The two most important available things are : the IP of the device, and the MAC of the device.
You use routers : pfSense does not obtain the MAC of the device - it obtains the MAC of the downstream router (the routers upstream port).Why don't you try this out yourself ??
Connect an Access Point to a LAN port of a "router".
Connect the router with the uostream port to the pfSense Captive LAN port.Connect your phone to the SSID of the access point.
Note the Wifi MAC of your phone.
The captive portal login page should popup.
Login.
On the pfSEnse side, look at the connected user list. Compare the MAC with your phone MAC.
It's different.
Check who's MAC it is ... (hit : look at the MAC address of the upstream LAN port of your router ^^ )You are also using a downstream DHCP server, so things will get worse.
Connect another phone to the AP.
There is a big chance that this second device doesn't need to login at all.You just managed to "totally break" your captive portal.
To have a workable situation :
No downstream DHCP servers.
No downstream routers.Do what all the others do : a captive portal is dedicated network port on pfSense, one big, or several, switches, or switch like devices (CPE, wifi bridges, whatever), a boat load off access points.
And that's it.
Your setup can work. With side effect as mentioned above, and maybe others, I can't tell, as I have never tried something like that. -
Thank you Gertjan for yr reply
my question was where I can find the option of disabling mac filtering in pfsense (in which list)
I did configure before captive portal in a simple network where the PFsense server was performing as DHCP server for clients and captive portal and it was working successfully but as I mentioned earlier , the current scenario is completely different as the PFsesne (captive portal) is far from the clients and there are some routers between them.
Again, thank you for explanation
-
@emad4 said in captive portal in complicated network:
my question was where I can find the option of disabling mac filtering in pfsense (in which list)
That is : Mac filtering for the captive portal.
On the main captive portal configuration page :
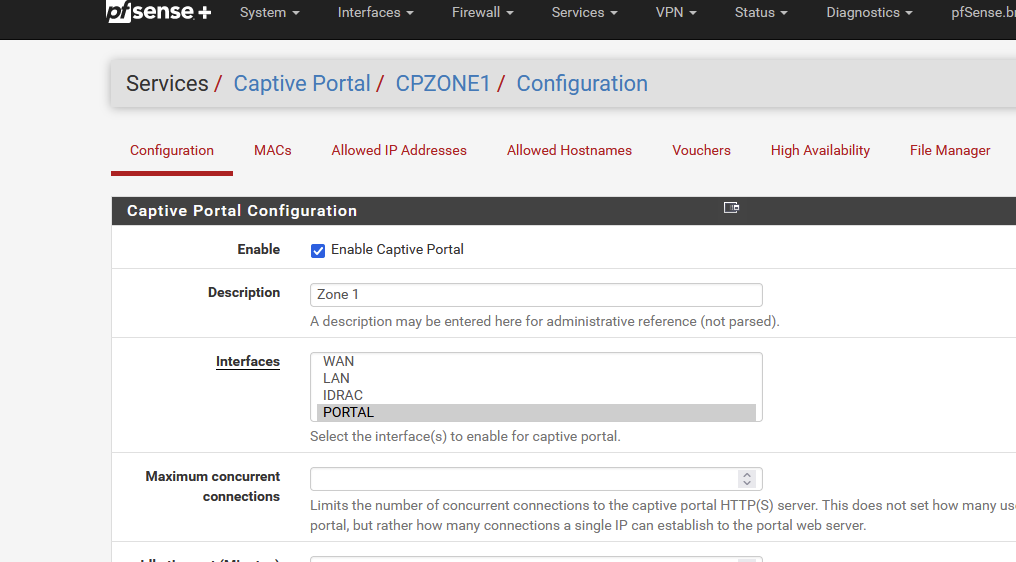
My zone is called "CPZONE1", yours has another name.
Scroll this page downwards. You'll find it.
-
@Gertjan
Okay , Thank you for help