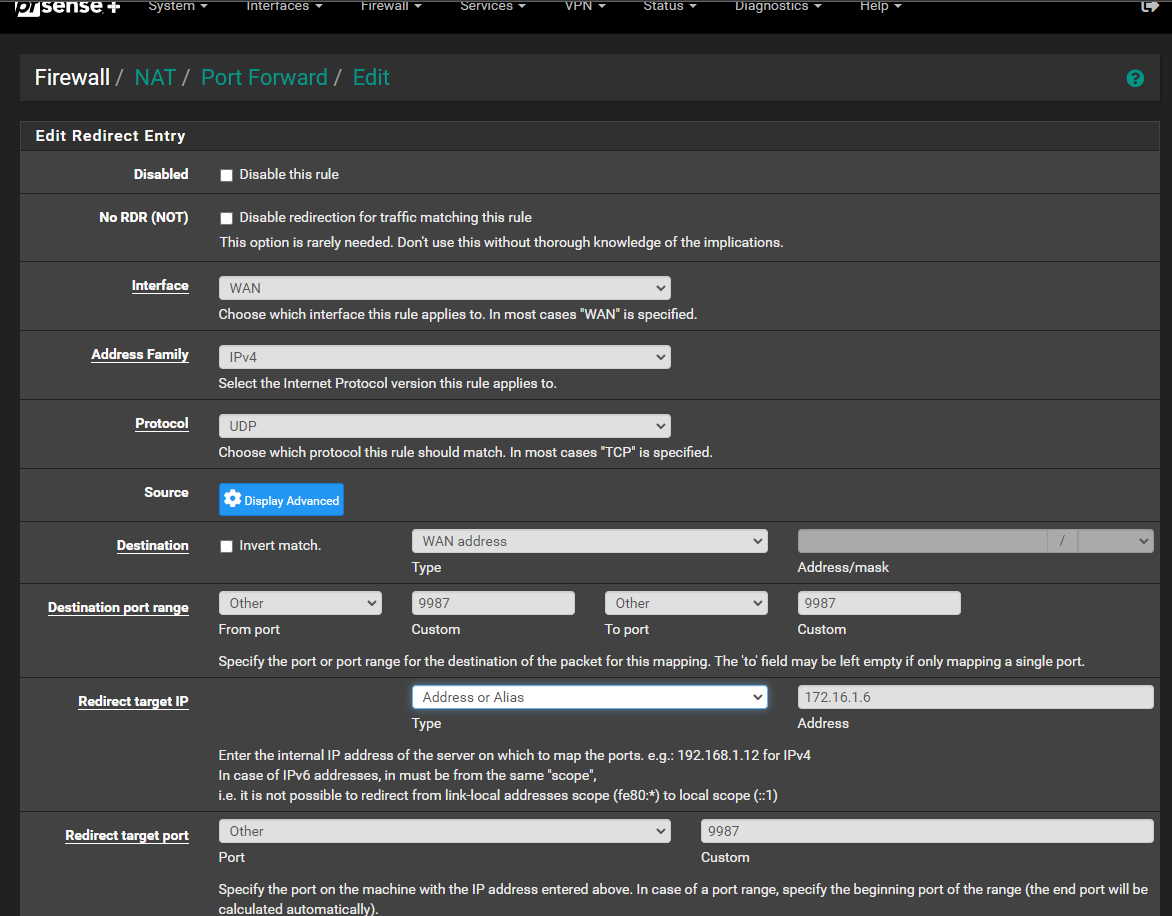
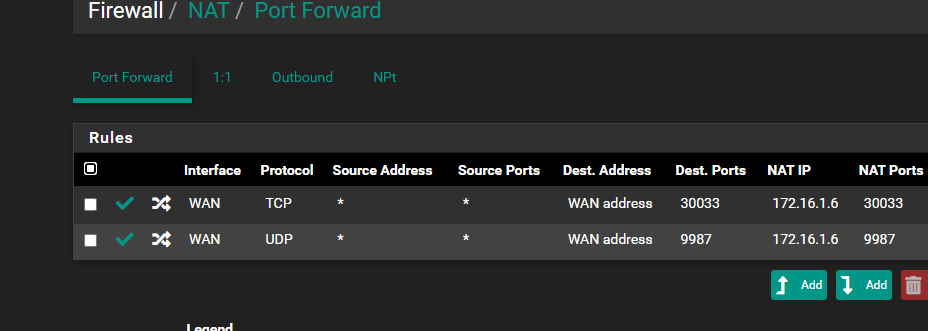
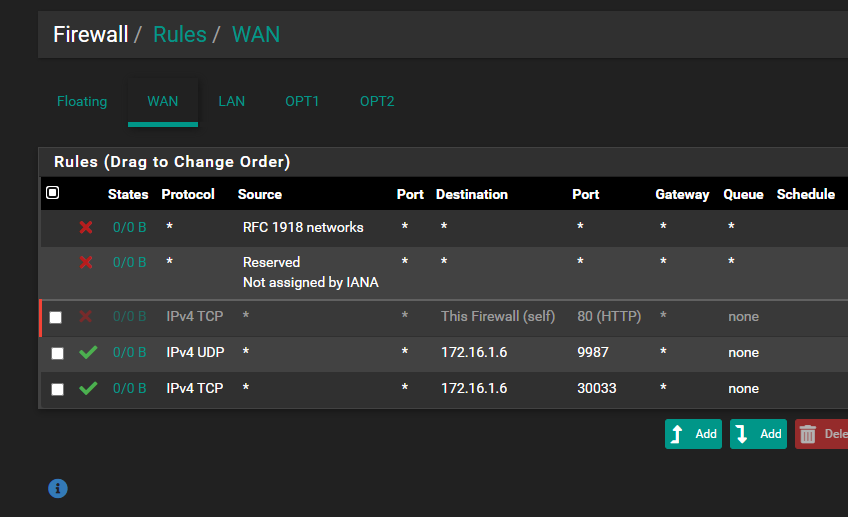
Port Forward does not work..
-
@johnpoz said in Port Forward does not work..:
@viragomann said in Port Forward does not work..:
The port checker might only be able to do TCP checks.
Yeah can you see me can only do TCP.. you would have to use something that can send udp..
Here is one..
https://www.ipvoid.com/udp-port-scan/
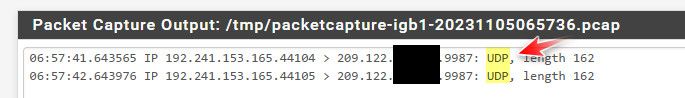
But if when testing and tcp gets there via packet capture - its a good sign that udp is open as well. But yeah its never bad idea to actually validate
My bad for not noticing 9987 was setup for udp..
In the packet capture log, only 30033 appears with the public ip, 9987 appears open on the last tool provided by you but does not appear in the log, I don't understand why it doesn't work
-
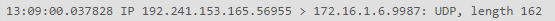
It seems that it finally appears, but I still can't connect to the teamspeak server using the public ip
-
@root1ng
Sniffing the traffic is the way to investigate this and to nail down the issue.
Run a capture on the WAN. If you can see the expected packets there, run a capture on the LAN side.However, it's required to know, which packets this service requires to work before.
-
@root1ng where did you sniff that - on the lan side interface of pfsense I have to assume because its already been forwarded to the 172.16 address. So pfsense did its thing.
Why your 172.16 doesn't answer could be lot of things, its not actually listening on that port, it has a firewall running not allowing it. Your sending to the wrong IP completely.
That device is not using pfsense as its gateway. But if your seeing traffic sent on from pfsense to the IP you want, and the port then its not pfsense issue.. Look to your device, or something else downstream in your network that could prevent that device from seeing the traffic.
Users all the time forget about host firewalls.. The only job pfsense has in this is sending it on to where you say to send it on too, if that device doesn't answer that is not a pfsense problem..
-
@viragomann said in Port Forward does not work..:
Sniffing the traffic is the way to investigate this and to nail down the issue.
Run a capture on the WAN. If you can see the expected packets there, run a capture on the LAN side.However, it's required to know, which packets this service requires to work before.
I came back with the log for WAN and LAN, I see that it responds to both, is it ok?
WAN:
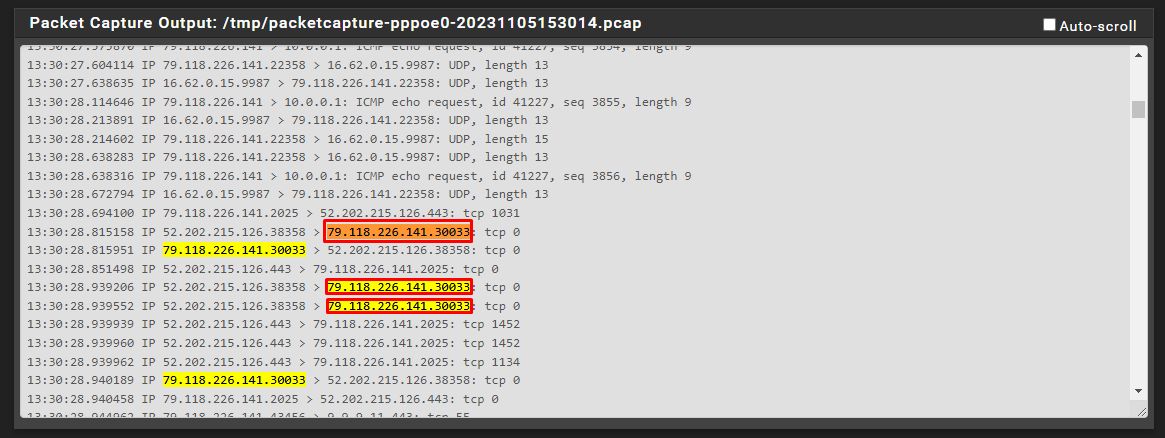
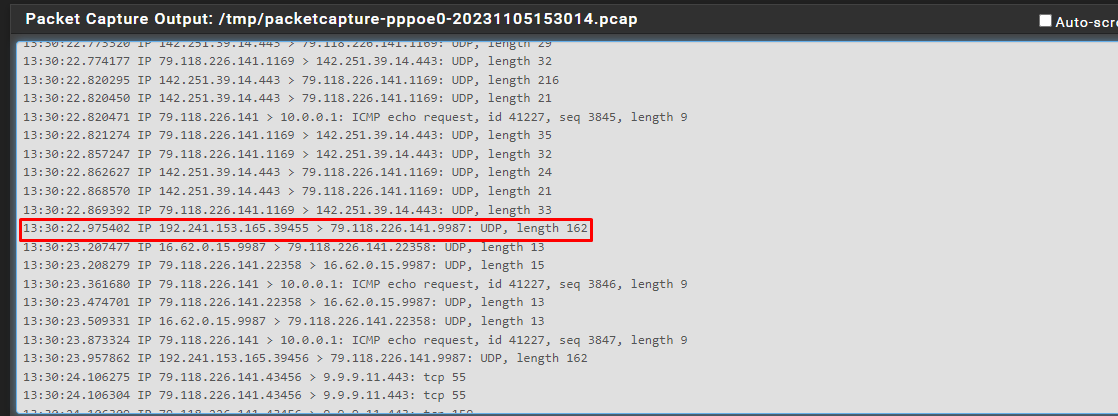
LAN:
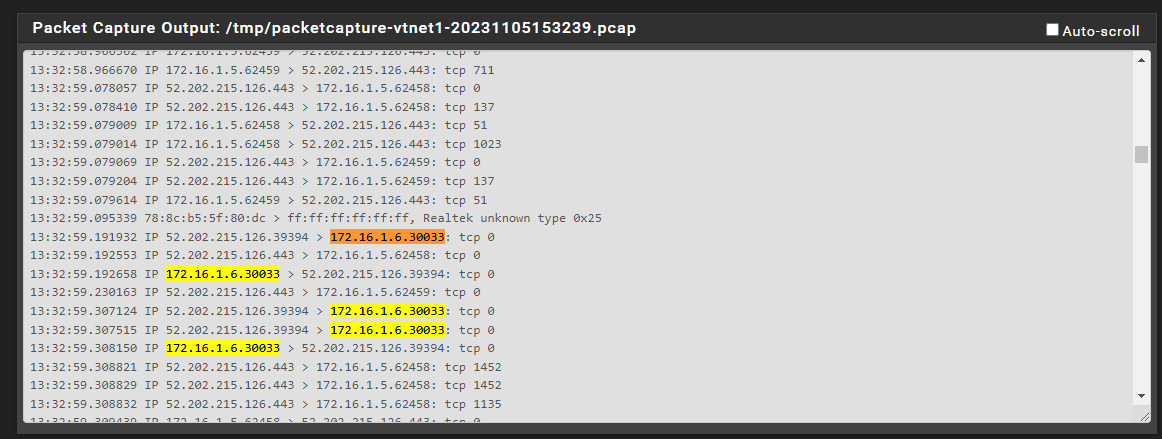
-
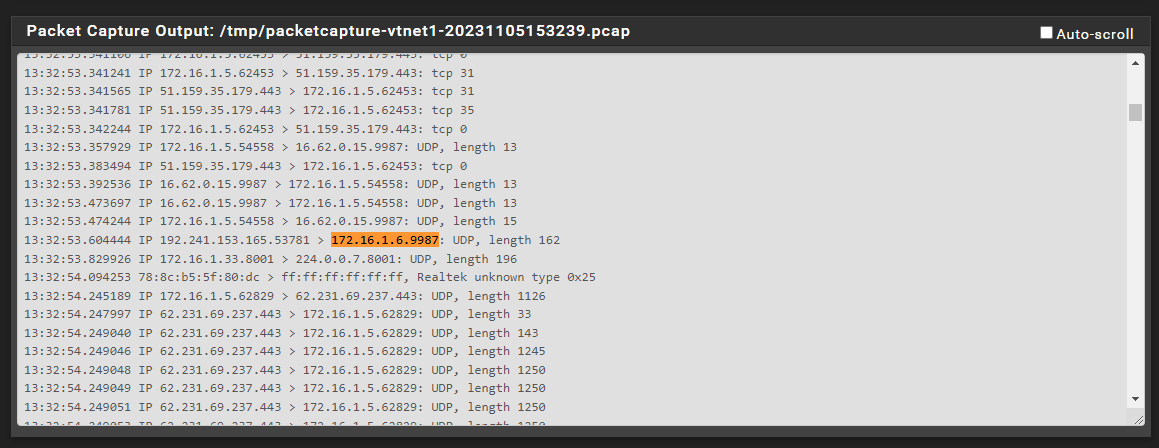
@root1ng where do you see 172.16.1.6 respond with traffic to its 9987 port?
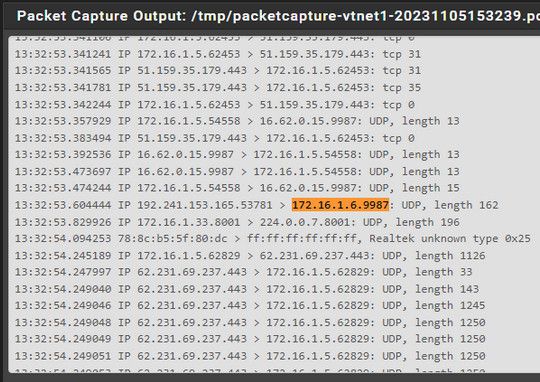
I don't see a response to 192.241.153.165 port 53781 in what you posted.
-
@johnpoz said in Port Forward does not work..:
@root1ng where do you see 172.16.1.6 respond with traffic to its 9987 port?
I don't see a response to 192.241.153.165 port 53781 in what you posted.
Yes, you are right, I checked once more and there is nothing from me to that ip, only from him to me.. I don't know what else to do, do you think you could help me by sharing or teamviewer?
-
@root1ng if you see traffic sent to that IP.. Check on that device that actually listening. Netstat -an will show you ports being listened on.
for example
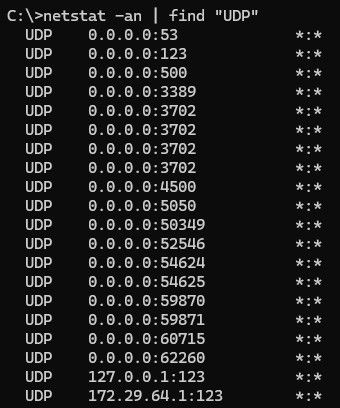
Some udp ports my windows box is listening on.. Do you see that 9987 listed?
do a packet capture on the device, wireshark is free and 2 seconds to install, etc..
-
@johnpoz said in Port Forward does not work..:
@root1ng if you see traffic sent to that IP.. Check on that device that actually listening. Netstat -an will show you ports being listened on.
for example

Some udp ports my windows box is listening on.. Do you see that 9987 listed?
do a packet capture on the device, wireshark is free and 2 seconds to install, etc..
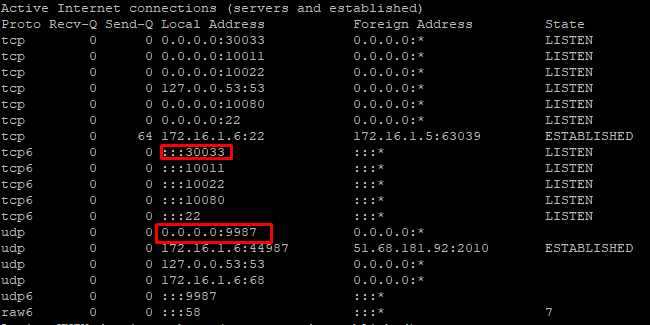
The server is on linux (ubuntu), not on windows, I still ran the same command, I attach a picture below.
-
@root1ng so that is good its listening - so firewall is running, its not answering for some other reason, its sending return traffic elsewhere?
So fire up wireshark or tcpdump and validate the traffic is getting there..
Pfsense did its thing, clearly it sent the traffic.. It has no control to if it gets an answer or not.. Which from your packet captures it did not.
edit: Oh wait - why does it not show Listen as state?
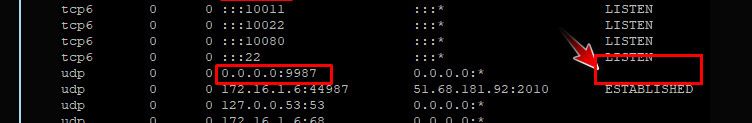
edit2: my bad - its UDP ;) having a brain fart this morning that we dealing with UDP ;) sorry..
Since you see pfsense sending it on, you need to sniff on the device itself - is it seeing it? If so does it answer to something other than pfsense? might have to validate what mac address is sending to if you see a response to that IP your checking from.
Does it not see it at all - its getting lost between pfsense and your device.. Or its application just didn't answer, or some firewall on the device not letting the application see the traffic.
-
@johnpoz said in Port Forward does not work..:
@root1ng so that is good its listening - so firewall is running, its not answering for some other reason, its sending return traffic elsewhere?
So fire up wireshark or tcpdump and validate the traffic is getting there..
Pfsense did its thing, clearly it sent the traffic.. It has no control to if it gets an answer or not.. Which from your packet captures it did not.
edit: Oh wait - why does it not show Listen as state?

edit2: my bad - its UDP ;) having a brain fart this morning that we dealing with UDP ;) sorry..
I don't know why he doesn't listen, I don't have a firewall on neither on the virtual machine nor on Proxmox, I don't know what else to do... the situation is too complicated...
-
@root1ng see my edit, sorry about that - udp with netstat wouldn't show "listen" state.. like tcp does.. but you can see its listening.
-
@johnpoz said in Port Forward does not work..:
@root1ng see my edit, sorry about that - udp with netstat wouldn't show "listen" state.. like tcp does.. but you can see its listening.
I don't really have anything to check on the device, everything is default, firewall off, the firewall for that virtual machine is off from Proxmox, I don't know what else to check and how..
-
@root1ng on the VM install tcpdump.. sniff with that, depending on the distro you installed might be already installed.
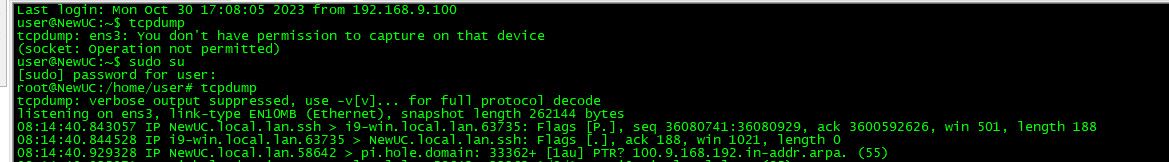
You can set filters on it so only looking for your udp 9987 port.
-
@johnpoz said in Port Forward does not work..:
@root1ng on the VM install tcpdump.. sniff with that, depending on the distro you installed might be already installed.

You can set filters on it so only looking for your udp 9987 port.
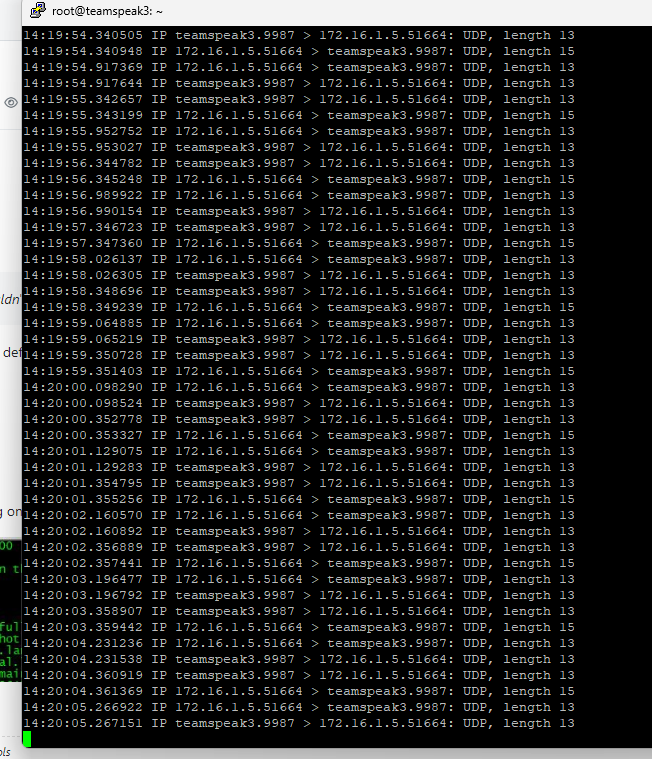
That's about all it shows, nothing more, it's just me connected from a local PC (172.16.1.5)
-
@root1ng In Proxmox you have a Firewall Option for every VM and every vNIC. Have you checked both?
-
@Bob-Dig said in Port Forward does not work..:
@root1ng In Proxmox you have a Firewall Option for every VM and every vNIC. Have you checked both?
Hey,
VM Firewall:
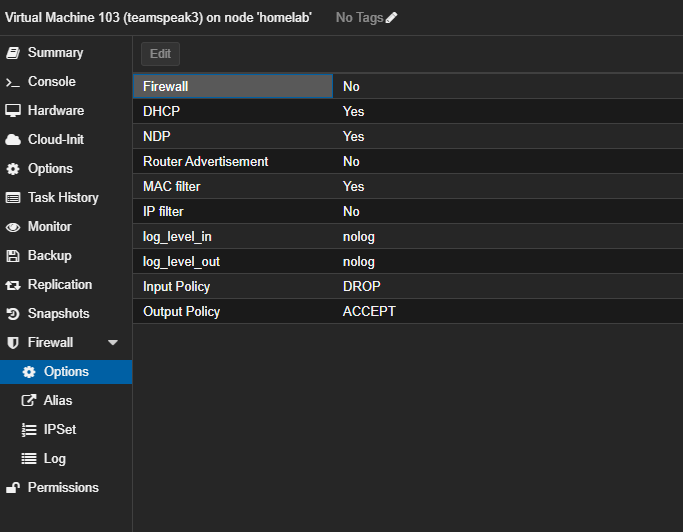
NIC Firewall:
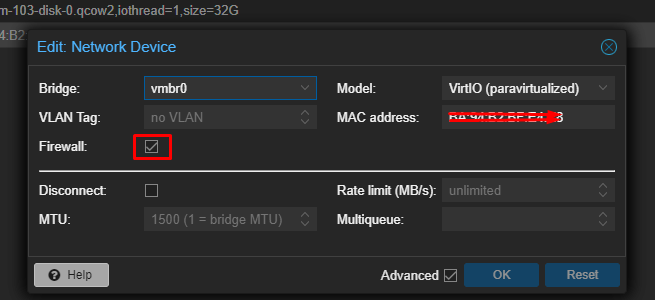
What I want to add is that, even with Firewall ON or OFF on the NIC, I still can't connect, I tried all the possible options, but without result.
The firewall is not active on all virtual machines, including the main node. -
@root1ng Disable this checkbox on all the VM NICs, on your pfSense and your Linux Server.
I am running TS on a Linux VM (Debian) behind a pfSense VM on Proxmox too, it is running fine for me, just checked.

-
@Bob-Dig said in Port Forward does not work..:
@root1ng Disable this checkbox on all the VM NICs, on your pfSense and your Linux Server.
I am running TS on a Linux VM (Debian) behind a pfSense VM on Proxmox too, it is running fine for me, just checked.

Deactivated but without result..
edit: And I gave a restart to be sure of both
-
@root1ng Maybe the host firewall, what Linux are you using exactly?
Maybe a routing problem, you could show us your proxmox network.In the beginning you had no hits at all on your rules. Have you fixed something or is your testing flawed otherwise? Send me your IP, I will check if I can connect.
Also show your rules on that VMs LAN.