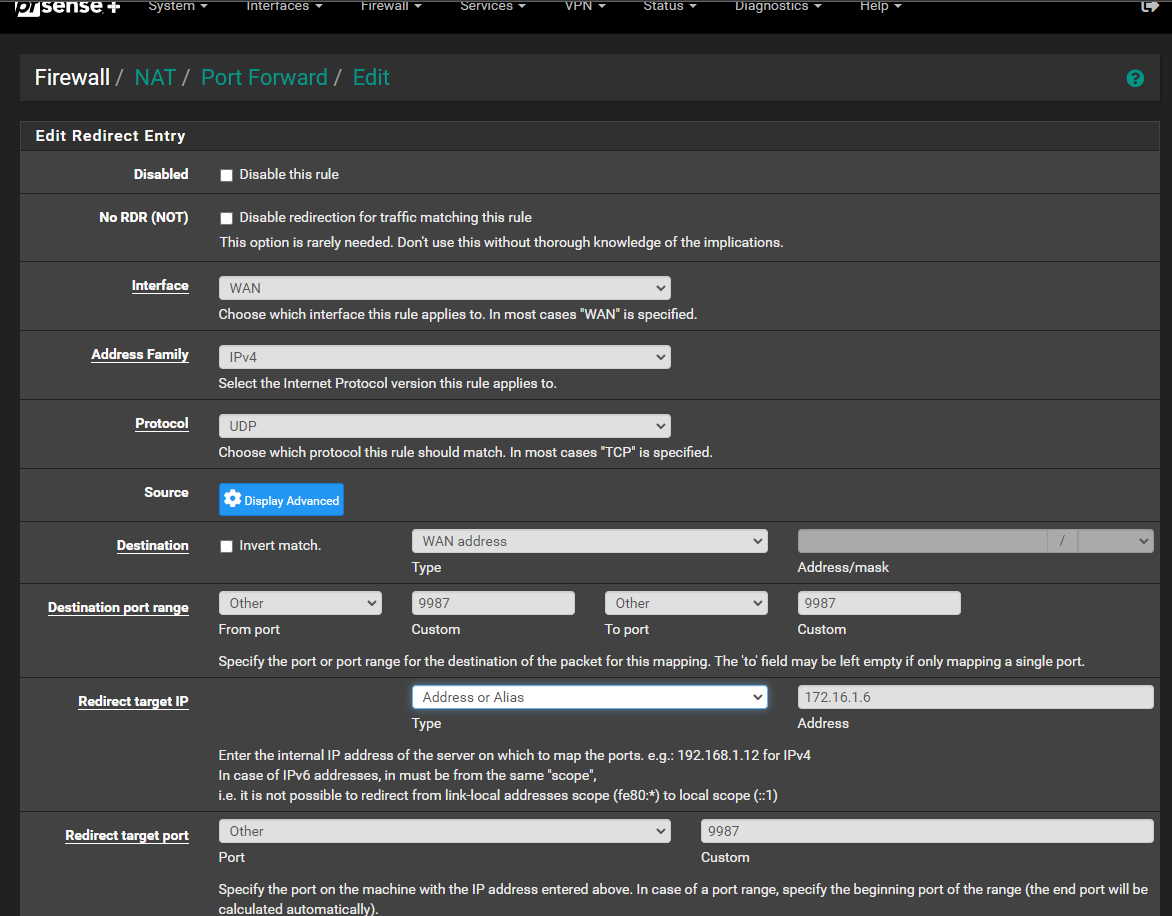
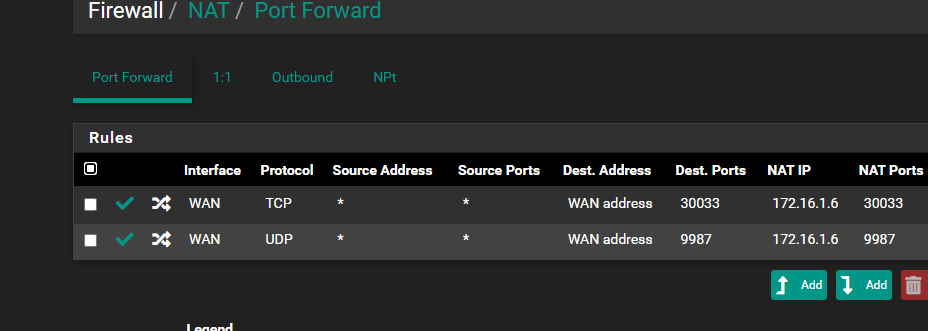
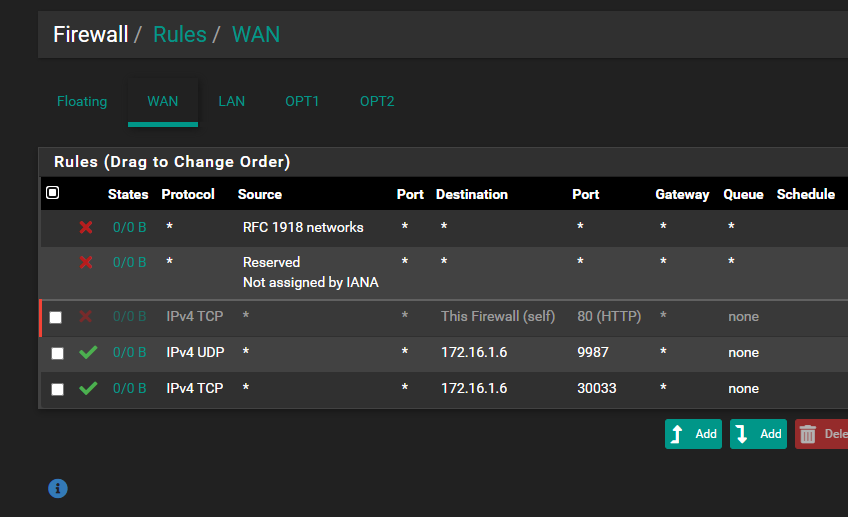
Port Forward does not work..
-
@root1ng if your not seeing the test from the outside on your .6 box, but your seeing it from your local .5 box.. When clearly pfsense sent the traffic on.. then you have something filtering it..
Even if the firewall on the vm was filtering it from the application, the sniff should still show it.
Pfsense has no job other to send the traffic to the IP you say to send it too - it has no control after it puts the traffic on the wire.. Clearly its putting it on the wire from your sniff. If your not seeing it at the end device. Is its sending it to the correct mac, have to assume so since you say that other 33 port is working.
Even had some firewall blocking it on pfsense on outbound direction, on your lan - the sniff you show on the lan side interface showing it was sent wouldn't show that if you had say a floating rule blocking it in the outbound connection..
You have something preventing the 9987 from getting to your VM, if you sniff and see pfsense put it on the wire, but your VM never sees it. Even if the vm wasn't listening or had a firewall blocking it.. The sniff should show that that traffic got there. So maybe you have something in your VM host preventing from sending it on to the VM, or sending it to the wrong vm.. Or something else filtering traffic from getting there - acl on a switch? Something in wifi if that is in use..
But if pfsense put it on the wire, pfsense job is done.. There is nothing else for pfsense to do..
-
@johnpoz Yeah, I could even connect to it, only OP can't do it to the public IP.
-
@Bob-Dig I know longer have my proxmox box to play with, so I can not test anything with proxmox.. But from what he shows pfsense put the traffic on the wire - if the destination is not getting it, that nothing to do with pfsense.
I would sniff on proxmox host to validate the traffic gets to it.. Then you for sure would know that its proxmox where the problem is.
edit: I even validated if you have a floating rule outbound to block it, would pfsense sniff maybe show going out the wire, even though it really wasn't
And when I block it with an outbound floating rule on the lan, the sniff never shows it going anywhere.. So it can't even be something like that.. Because he shows a sniff on pfsense sending on the traffic
-
@johnpoz said in Port Forward does not work..:
@Bob-Dig I know longer have my proxmox box to play with, so I can not test anything with proxmox.. But from what he shows pfsense put the traffic on the wire - if the destination is not getting it, that nothing to do with pfsense.
I would sniff on proxmox host to validate the traffic gets to it.. Then you for sure would know that its proxmox where the problem is.
edit: I even validated if you have a floating rule outbound to block it, would pfsense sniff maybe show going out the wire, even though it really wasn't
And when I block it with an outbound floating rule on the lan, the sniff never shows it going anywhere.. So it can't even be something like that.. Because he shows a sniff on pfsense sending on the traffic
Yes, it seems that from outside the network I can connect with the public IP, from inside the network (WiFi or Cable) I can't connect at all with the public address..
I don't understand what I have to check with Proxmox, because everything is default and I have nothing to change. -
@root1ng said in Port Forward does not work..:
from inside the network (WiFi or Cable) I can't connect at all with the public address.
your trying this from inside?? For that to work you would need to setup nat reflection.
-
@johnpoz said in Port Forward does not work..:
your trying this from inside?? For that to work you would need to setup nat reflection.
Yes, from the inside, no, I don't have NAT Reflection active.
Do I activate it globally or for each individual rule? -
@root1ng you can do it either way.. But with something like this you could have a problem.. But if your hitting the wan IP from the inside and not seeing traffic being sent on - that would be due to no nat reflection setup.
You might have to do a full proxy setup - not really a fan of nat reflection, its an abomination if you ask me ;)
But problem is even if you reflect if the source IP is local to where your sending it, and that something answers directly back.. The client might say hey wait a minute - I sent this traffic to mac abc (its gateway) why is mac xyz answering me.. You can see this very easy with dns and redirection.. There are plenty of posts around here going over that specific scenario..
But that really has nothing to do with plex doing the job of the port forward, but if you want plex to send the traffic to 1.6 when you hit your public IP from the lan side, that would need a nat reflection to be setup.
-
@johnpoz said in Port Forward does not work..:
@root1ng you can do it either way.. But with something like this you could have a problem.. But if your hitting the wan IP from the inside and not seeing traffic being sent on - that would be due to no nat reflection setup.
Ok, and do I enable nat reflection in Firewall - NAT - Port Forward for each rule added for the teamspeak server, or do I enable it globally from System > Advanced > Nat Reflection for Port Forward?
I think it's the same thing, but it's better to ask than to do another stupid thing :))
-
@root1ng I made some edits about nat reflection on my previous post, but you can set it up when you do the forward.
-
@johnpoz said in Port Forward does not work..:
But problem is even if you reflect if the source IP is local to where your sending it, and that something answers directly back.. The client might say hey wait a minute - I sent this traffic to mac abc (its gateway) why is mac xyz answering me.. You can see this very easy with dns and redirection.. There are plenty of posts around here going over that specific scenario..
But that really has nothing to do with plex doing the job of the port forward, but if you want plex to send the traffic to 1.6 when you hit your public IP from the lan side, that would need a nat reflection to be setup.
Ok and how do I do these settings? What should be set exactly? I don't understand, Pure NAT or NAT + Proxy or are there more advanced settings that need to be done?
-
@johnpoz said in Port Forward does not work..:
@root1ng you can do it either way.. But with something like this you could have a problem.. But if your hitting the wan IP from the inside and not seeing traffic being sent on - that would be due to no nat reflection setup.
You might have to do a full proxy setup - not really a fan of nat reflection, its an abomination if you ask me ;)
But problem is even if you reflect if the source IP is local to where your sending it, and that something answers directly back.. The client might say hey wait a minute - I sent this traffic to mac abc (its gateway) why is mac xyz answering me.. You can see this very easy with dns and redirection.. There are plenty of posts around here going over that specific scenario..
But that really has nothing to do with plex doing the job of the port forward, but if you want plex to send the traffic to 1.6 when you hit your public IP from the lan side, that would need a nat reflection to be setup.
I think I solved it and I hope I did the right thing, I changed the global settings, I'm attaching a picture below, is it okay?
By the way, this is how I can connect with the public IP from LAN/WiFi.
Without those two checked boxes I can't connect. (1:1 and outbound)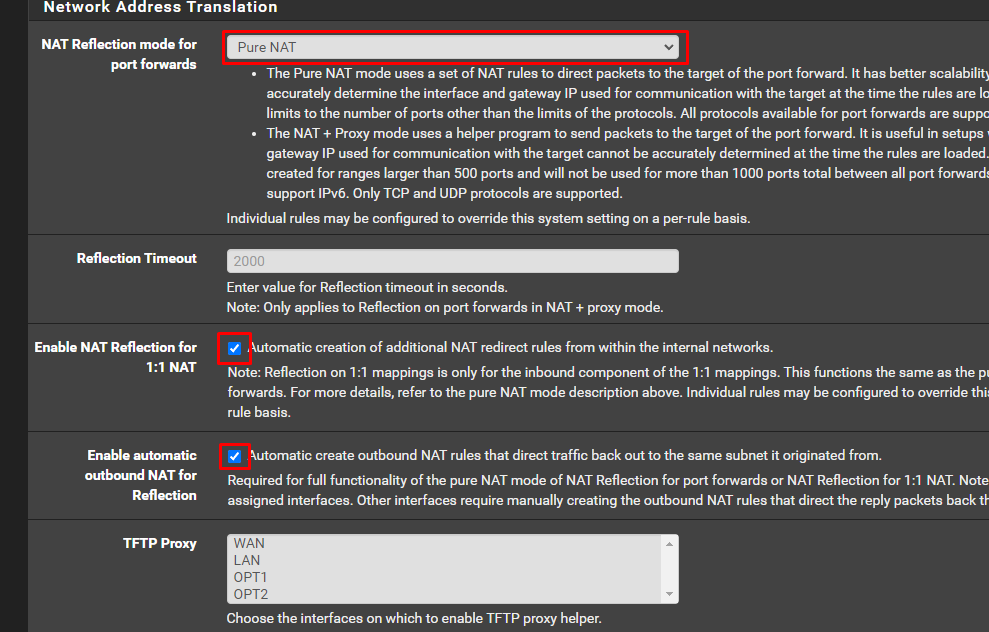
-
@root1ng said in Port Forward does not work..:
@johnpoz said in Port Forward does not work..:
@root1ng you can do it either way.. But with something like this you could have a problem.. But if your hitting the wan IP from the inside and not seeing traffic being sent on - that would be due to no nat reflection setup.
You might have to do a full proxy setup - not really a fan of nat reflection, its an abomination if you ask me ;)
But problem is even if you reflect if the source IP is local to where your sending it, and that something answers directly back.. The client might say hey wait a minute - I sent this traffic to mac abc (its gateway) why is mac xyz answering me.. You can see this very easy with dns and redirection.. There are plenty of posts around here going over that specific scenario..
But that really has nothing to do with plex doing the job of the port forward, but if you want plex to send the traffic to 1.6 when you hit your public IP from the lan side, that would need a nat reflection to be setup.
I think I solved it and I hope I did the right thing, I changed the global settings, I'm attaching a picture below, is it okay?
By the way, this is how I can connect with the public IP from LAN/WiFi.
Without those two checked boxes I can't connect. (1:1 and outbound)
edit:
But that's not good, I connect and my IP changes to 172.16.1.1 which is actually the pfSense gateway.
Connecting with the public ip or dns I am assigned 172.16.1.1, if I connect with 172.16.1.6 I am assigned 172.16.1.5, I did something wrong.. -
@root1ng said in Port Forward does not work..:
But that's not good, I connect and my IP changes to 172.16.1.1 which is actually the pfSense gateway.
Yeah, this is what NAT reflection does and what it has to do if it is enabled to avoid asymmetric traffic.
if I connect with 172.16.1.6 I am assigned 172.16.1.5, I did something wrong.
This connection doesn't pass pfSense, so it can do nothing on it, and it's also not necessary.
-
@viragomann said in Port Forward does not work..:
@root1ng said in Port Forward does not work..:
But that's not good, I connect and my IP changes to 172.16.1.1 which is actually the pfSense gateway.
Yeah, this is what NAT reflection does and what it has to do if it is enabled to avoid asymmetric traffic.
if I connect with 172.16.1.6 I am assigned 172.16.1.5, I did something wrong.
This connection doesn't pass pfSense, so it can do nothing on it, and it's also not necessary.
And what do you recommend? Should I leave Reflection off and connect with my local IP and the rest with the public one?
-
@root1ng
I recommend nothing regarding this. I didn't follow the whole thread and hence I don't know, why @johnpoz recommend to enable it.
Does this make incoming teamspeak connections succeed?NAT reflection basically needed if you really need to access the public IP from inside the network and if you cannot use the FQDN with DNS host overrides for whatever reason.
I don't expect that there is any change on incoming forwarded connections.The generated hidden outbound NAT rules should only be applied on traffic from another local subnet.
-
@viragomann said in Port Forward does not work..:
Does this make incoming teamspeak connections succeed?
Anyone outside my network can connect with the public IP, only I can't, but I don't mind connecting with the local one. I will stay like this for a while, it seems safer to me.
-
@viragomann said in Port Forward does not work..:
why @johnpoz recommend to enable it.
Because he stated its not working when hitting his public IP from inside his network - which of course it wouldn't unless you were doing nat reflection.
I personally think the function shouldn't even be available - its an abomination to all things networking ;) But if that is what he wants to do - it would never working hitting the public IP from the inside without nat reflection
-
@johnpoz said in Port Forward does not work..:
Because he stated its not working when hitting his public IP from inside his network - which of course it wouldn't unless you were doing nat reflection.
I'd expect, that you would rather recommend to use a public FQDN with DNS host overrides to achieve this.
But yes, if this is not an option for what ever reason, we don't know, NAT reflection is the only way to achieve this. -
@viragomann I would much rather suggest use a fqdn yes.. But his problem was based on ip and not seeing it.. Which he never would without nat reflection.
I was just troubleshooting his problem - not suggesting how he should setup his network.
But completely agree with you - in my multiple statements that nat reflection is an abomination ;) you should hit the local IP be that with IP or with a fqdn that resolves to your local IP when your local vs the public.
-
@johnpoz said in Port Forward does not work..:
But completely agree with you - in my multiple statements that nat reflection is an abomination
That's the way I know you.

As I mentioned, I didn't read all posts and I missed the reason for doing NAT reflection.