NAT Reflection on a multiwan system - need help debugging my problem getting it to work.
-
I have a box running pfsense 2.7.0 with 4, fixed ip, wan connections. This works fine.
I have 1 installation of a mailinabox server that will only be accessed publically by 1 of the 4 wan ip addresses on interface X. The nat rules are configured to pass traffic to interface X to the mailinabox server for ports 80, 443, 25, 587, 143, 993 which are the ports necessary for supporting smtp, imap and webmail. This works fine.
The problem is that mailinabox assumes that it only has a public ip and is not NAT mapped to a private ip. This means that the status checks only use the public ip assigned to the mailinabox installation to test/check the system.
The obvious solution is to enable the NAT reflection to allow these checks to succeed. Unfortunately, I am unable to get it to work and am looking for any advice or help on how to debug this problem correctly.
The firewall has the following configuration under / System / Advanced / Firewall & Nat / Network Address Translation /
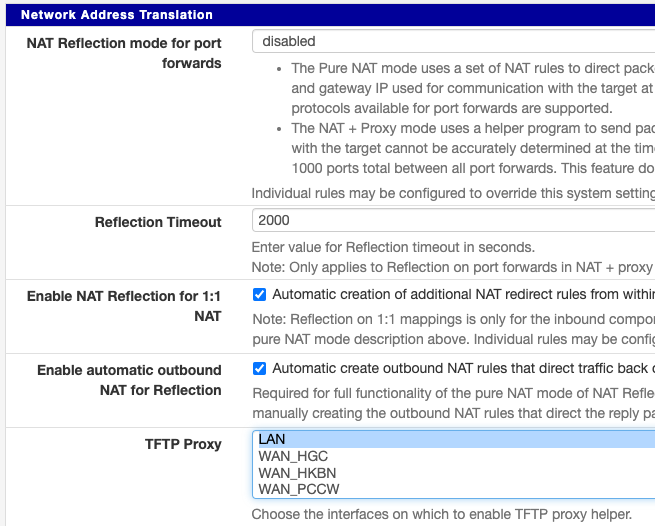
Yes, I am aware that the default setting of "NAT Reflection mode for port forwards" is disabled. This is on purpose. I have done that so I can enable the "NAT Reflection mode for port forwards" on an individual rule basis, like so:
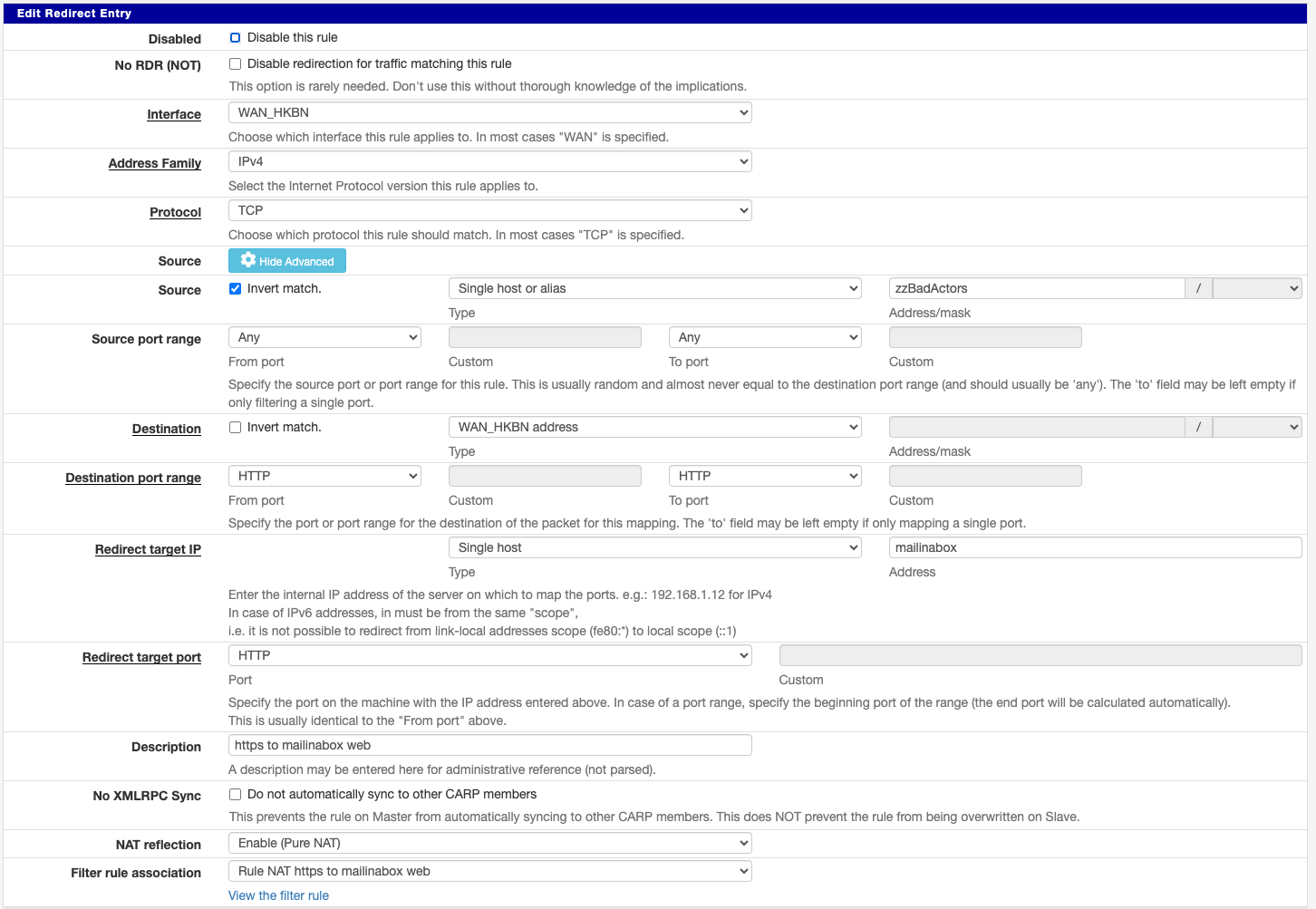
When I examine the /tmp/rules.debug file, I can find the following for this mapping (where em0 is the LAN and the other 3 are the ipsec, openvpn and wireguard vpns respectively)
# Reflection redirect rdr on { em0 enc0 openvpn WireGuard } inet proto tcp from ! $zzBadActors to <PublicIP> port 80 -> $mailinabox nat on em0 proto tcp from 10.10.1.0/24 to $mailinabox port 80 -> 10.10.1.1 port 1024:65535However, when I am on the LAN, I am unable to access the mailinabox via it's public IP.
If I set the default to be pure nat for everything, then it I get more reflection rules in the firewall, but it still doesn't work.
My / Firewall / NAT / Outbound / rules are set to "Automatic outbound NAT rule generation"
My questions are:
- is there any way to debug why the traffic from the local lan to the public ip of the port forwarded ports is not going through?
- does that reflection firewall rule look correct for my situation?
- the default route for the LAN traffic is a gateway group composed of the 4 lan connections. Could this be causing a problem, preventing the nat reflection from working?
- could I use the / Diagnostics / Packet Capture / somehow to find out what is or is not happening?
Finally, split DNS will not solve this problem as the mailinabox system checks specifically test the public ip.
Any advice or suggestions would be greatly appreciated.
Thank you.
-
@pdwalkerhk said in NAT Reflection on a multiwan system - need help debugging my problem getting it to work.:
is there any way to debug why the traffic from the local lan to the public ip of the port forwarded ports is not going through?
Sniff the traffic with the packet capture tool on the LAN.
does that reflection firewall rule look correct for my situation?
I would expect it to work.
the default route for the LAN traffic is a gateway group composed of the 4 lan connections. Could this be causing a problem, preventing the nat reflection from working?
You may mean an interface group. This is not a problem, however, ensure that a rule on LAN allows the traffic from LAN IP to LAN destination IP.
The rule must not be a policy routing rule (gateway (group) stated)!could I use the / Diagnostics / Packet Capture / somehow to find out what is or is not happening?
Yes. You should see packets from the source IP to the public going to pfSense and packets leaving with source = LAN IP and local destination IP.