Help with rules to block UniFi Cloudkey Gen2+
-
Thanks, I'll keep digging into this "problem"

-
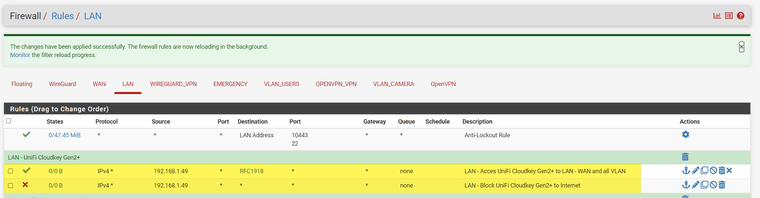
According to your explanations (THANK YOU!) I've created these rules, I think I'm "right"... do you think it's actually OK?
EDIT :
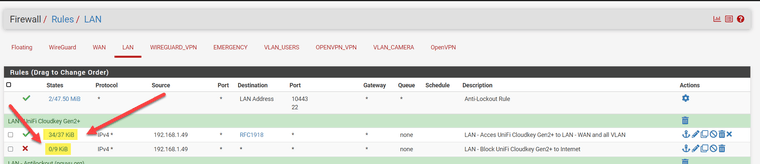
In any case, I have "activity" on these rules
-
@SwissSteph yeah those rules would allow that 1.49 IP to go to any rfc1918 address (or whatever networks you have in that alias) and anywhere else would be blocked. Ie the internet..
-
YES YES YES!!!
Thank you so much for your help and patience

Now all I have to do is try to block entry into my UniFi Cloudkey Gen2+ from the outside, then it would be perfect. Because I could give or not this access ONLY when I want.
But I don't really understand how it works and how to block the Unify site from reaching my Cloudkey.
Now I can still do it...
If anyone has the "magic rule", I'd love to hear from you.
-
@SwissSteph said in Help with rules to block UniFi Cloudkey Gen2+:
how to block the Unify site from reaching my Cloudkey.
unfi is not "reaching" your cloudkey, your cloudkey is creating a connection to them. Unless you setup a port forward on pfsense, or something with a reverse proxy there is no way for unifi to create an unsolicited inbound traffic to talk to your cloudkey..
If you block its access to the internet, at some point their site will show your cloudkey offline.. Might take a bit before they reflect they are no longer talking to your clouldkey.. Make sure you kill any states as well once you created the block rule.
-
I agree.
Thanks for these clarifications, I'll keep an eye on it and if there's still a connection, then I'm the one who authorized it directly in my "Cloudkey". This is possible because I'm not sure I've done everything "right" as soon as it's installed, so I'm going "step by step".
"Unless you setup a port forward on pfsense, or something with a reverse proxy there is no way for unifi to create an unsolicited inbound traffic to talk to your cloudkey"
I don't have a "reverse proxy" or "port specific redirection for unify" ... but I'll keep an eye on it.
Thanks again!
-
@johnpoz
A little feedback ... these two rules work perfectly. Thanks again for your help and happy new year! -
My new feedback, is that by not changing anything to the two rules explained in this topic, in 2024 and using the same applications (only the version is changed) on my phone it is impossible for me to connect as it worked perfectly with OpenVPN ... now nothing works anymore.
Of course, if I remove the two blocking rules above, it works again (probably Unify's "cloud").
In short, the blocking that was perfect in 2023, blocks so well that in 2024 and the changes made by Unify I can no longer connect remotely with my phone (while not at home) and with my OpenVPN on my Pfsense.
As I don't want to let Unify "see all my configurations", do you have a solution?
- keep the rules above that block the "Unify sew".
- find a solution so that Unify Android applications work as before (in 2023).
I find it very hard to understand why everything is blocked when I'm not at home using my Android phone + OpenVPN.
This same phone, on my WiFi at home, works very well with the applications installed on my phone.
If I test (still at home) with OpenVPN -> it no longer works ... so logically with the same OpenVPN from elsewhere it doesn't work.Help!
-
@SwissSteph said in Help with rules to block UniFi Cloudkey Gen2+:
As I don't want to let Unify "see all my configurations", do you have a solution?
Huh? Just disable the Cloudkey from connecting to Unifis Cloud for their remote admin stuff. That's a controller option. Done. Ubiquiti doesn't "read" your configuration. That's nonsense. Also blocking the cloud key from the internet won't show you any updates of your devices and the cloudkey itself, so it's a bit of strange move when you want the stuff to work and get updates but at the same time disabling it's ability to download updates from the official servers?
I simply disabled the remote connection stuff and don't have the option to connect to my cloudkey even when I log into their online portal thingy as it just doesn't connect there. That's more then enough for me.
As for your problem with your OpenVPN - those two things are simply not connected to each other. As we can't predict what rules and stuff you configured, there's no way we could see why your Android via OVPN wouldn't work anymore.
Cheers
-
Thank you for your message and your advice.
"Protect" doesn't work anymore, and this without any configuration change on my Pfsense, it's actually a new version of the "Protect" application that broke this.
On the Ubiquiti forum, there are other messages from members who have exactly the same problem. And no help from official Ubiquiti support.
I'm talking about my configuration where my Pfsense blocks all connections from my "Cloudkey" to the outside and where I used to connect to it without any problem with my OpenVPN and the "Protect" application, now it's impossible (including while on my WiFi)
Yes, updates are no longer offered. If I want them, I disable my two rules on my Pfsense and they come. The latest update https://community.ui.com/releases/UniFi-Switch-6-6-61/8f96bd97-d43b-4387-9b5e-6273f5db54bf seems to break a lot of things, and I'm glad I didn't put this new version on my appliances (anyway I don't leave the updates in "automatic mode" for security reasons ... which not everyone does, as several have had problems waking up).