Remote access openvpn server can't access peer to peer openvpn servers
-
Hi everyone!
Firstly, I want to say that I'm complete noob with pfsense, so maybe my problem is easy to solve, but I cannot understand what to do for a few days.
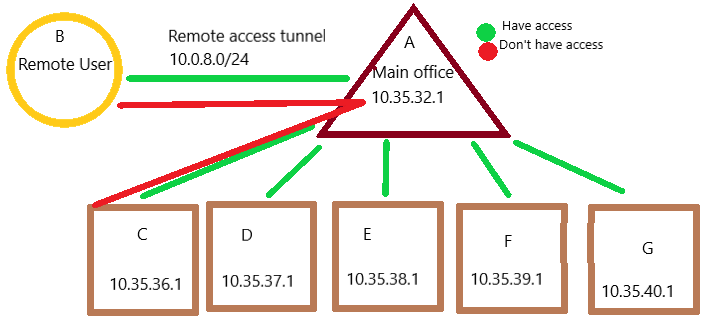
I have this problem: I need to connect 5 remote offices and remote user to the main office. I need to be able to manage any server using my phone.
I've already created 2 openvpn servers. First server connects main server and remote user using "Remote Access ( SSL/TLS + User Auth )" mode. Tunnel network: 10.0.8.0/24. Second server connects five remote servers to the main one using "Peer to Peer ( SSL/TLS )" mode. All of them are running pfsense. Their IPs:
10.35.32.1 - main server
10.35.36.1
10.35.37.1
10.35.38.1
10.35.39.1
10.35.40.1I have already connected these servers with one another using ipsec, but I need to use openvpn.
-
@Shuldyk-Andrii said in Remote access openvpn server can't access peer to peer openvpn servers:
Second server connects five remote servers to the main one using "Peer to Peer ( SSL/TLS )" mode.
Which tunnel network?
Did you configure CSO for each? Is so, can you show them, please?
Their IPs:
10.35.32.1 - main server
10.35.36.1
10.35.37.1
10.35.38.1
10.35.39.1
10.35.40.1Are these the virtual VPN IPs or local ones?
Can you show all VPN server and client settings, please?
-
@viragomann
Thank you!Which tunnel network?
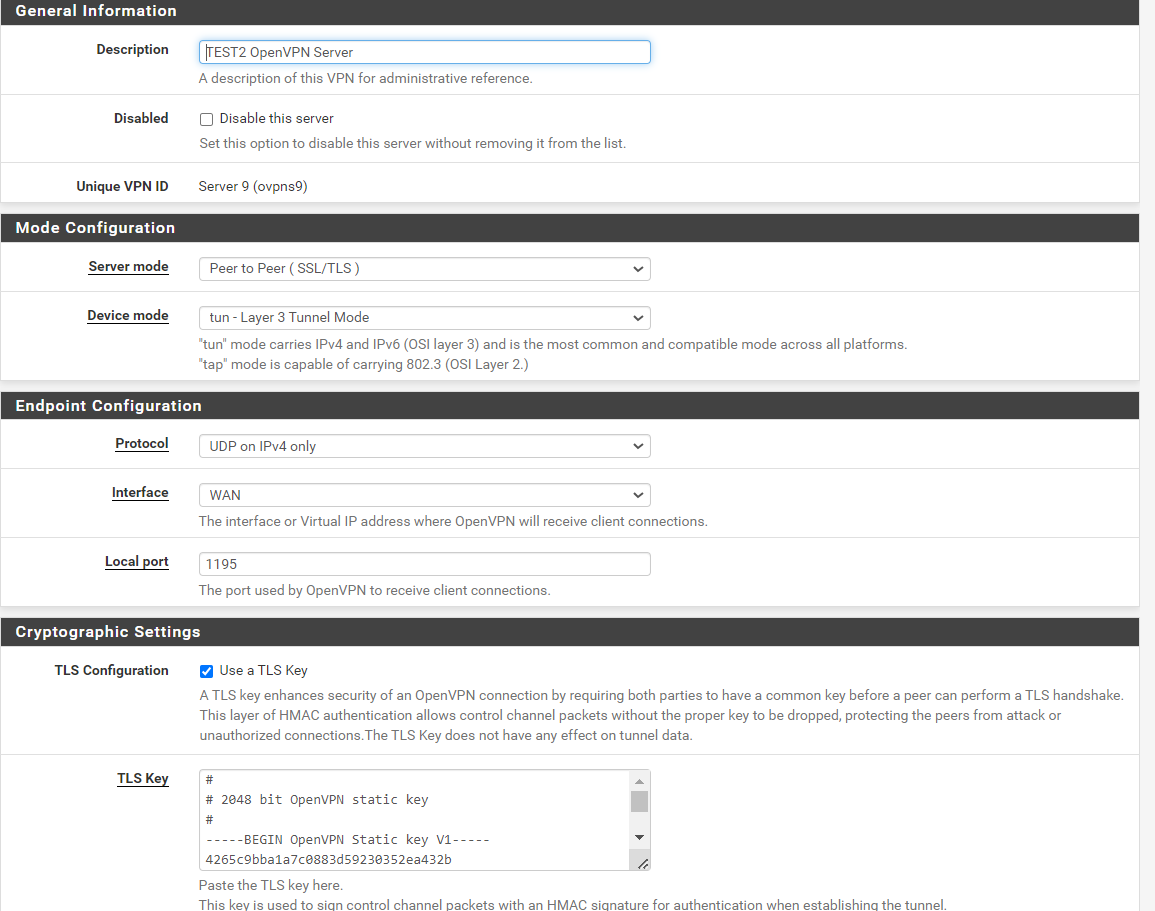
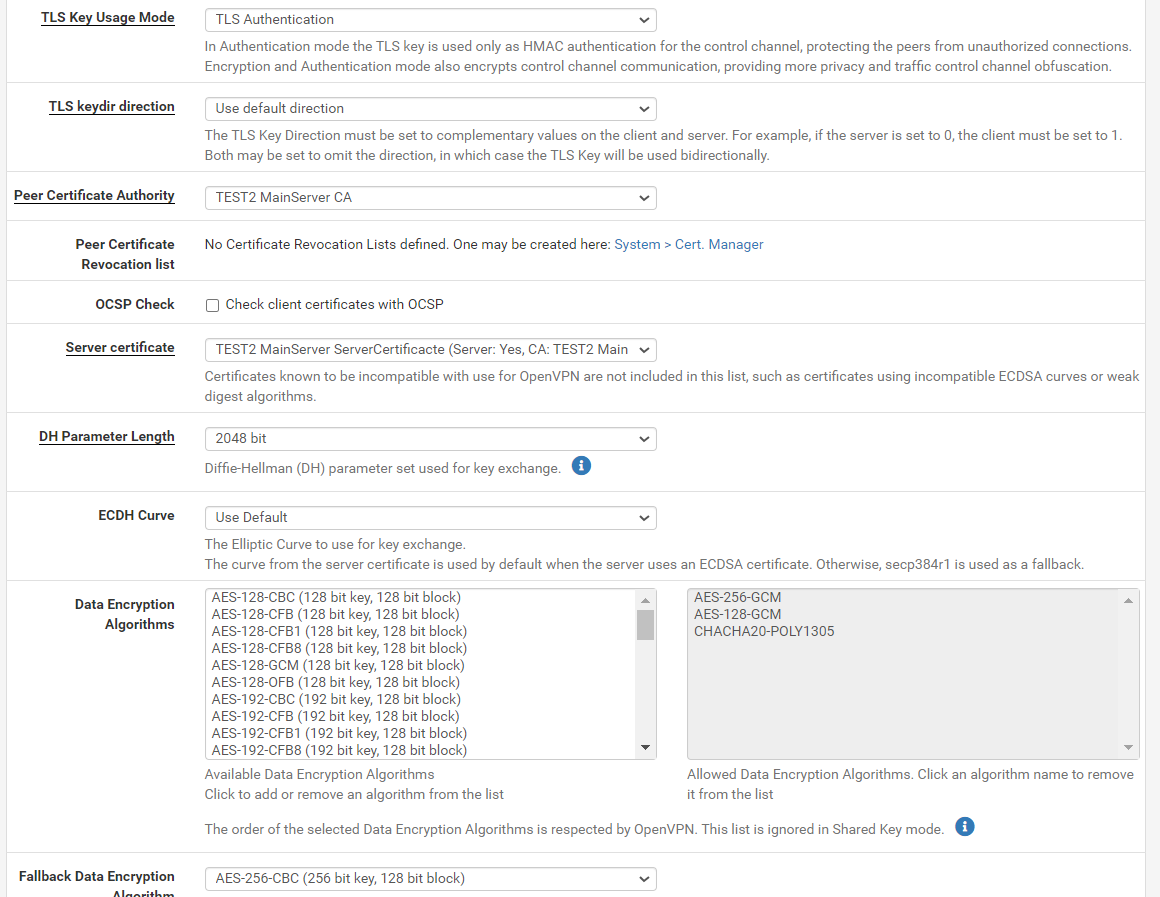
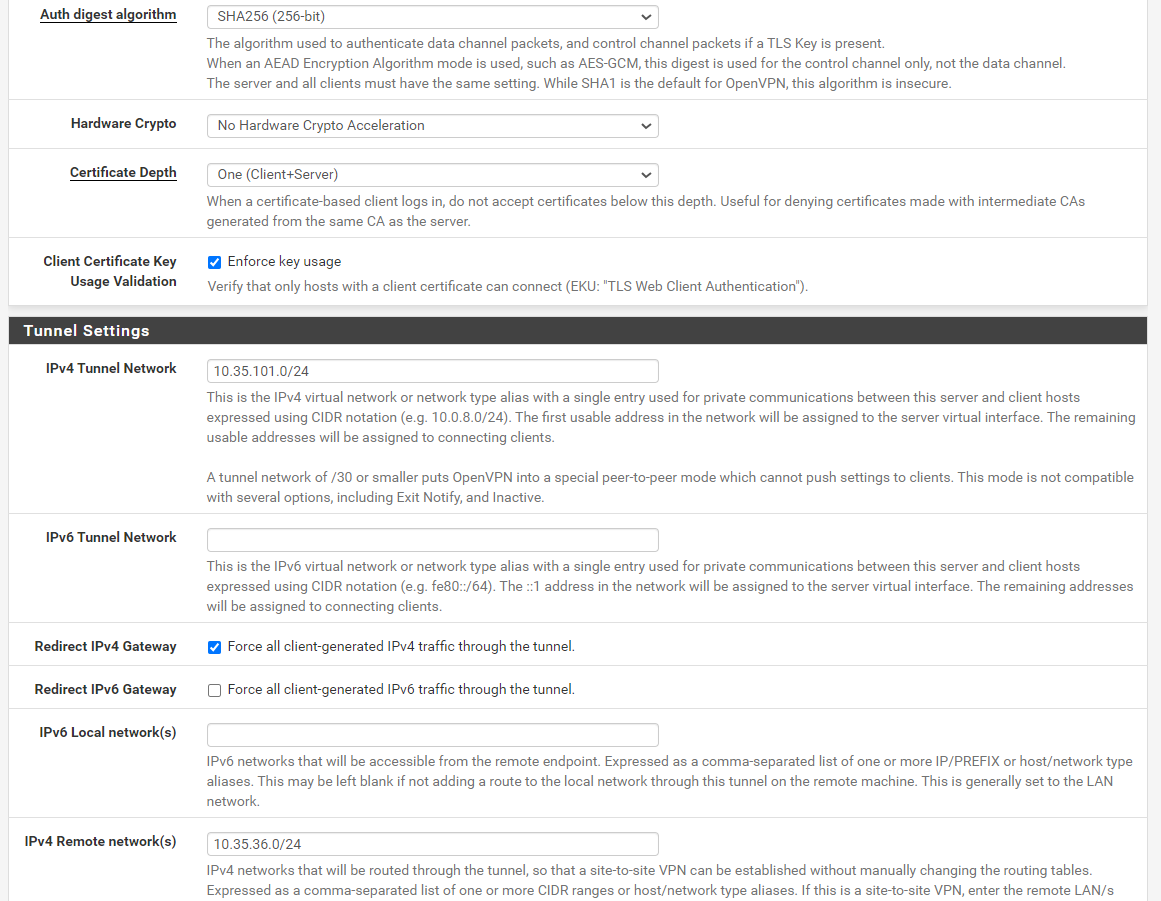
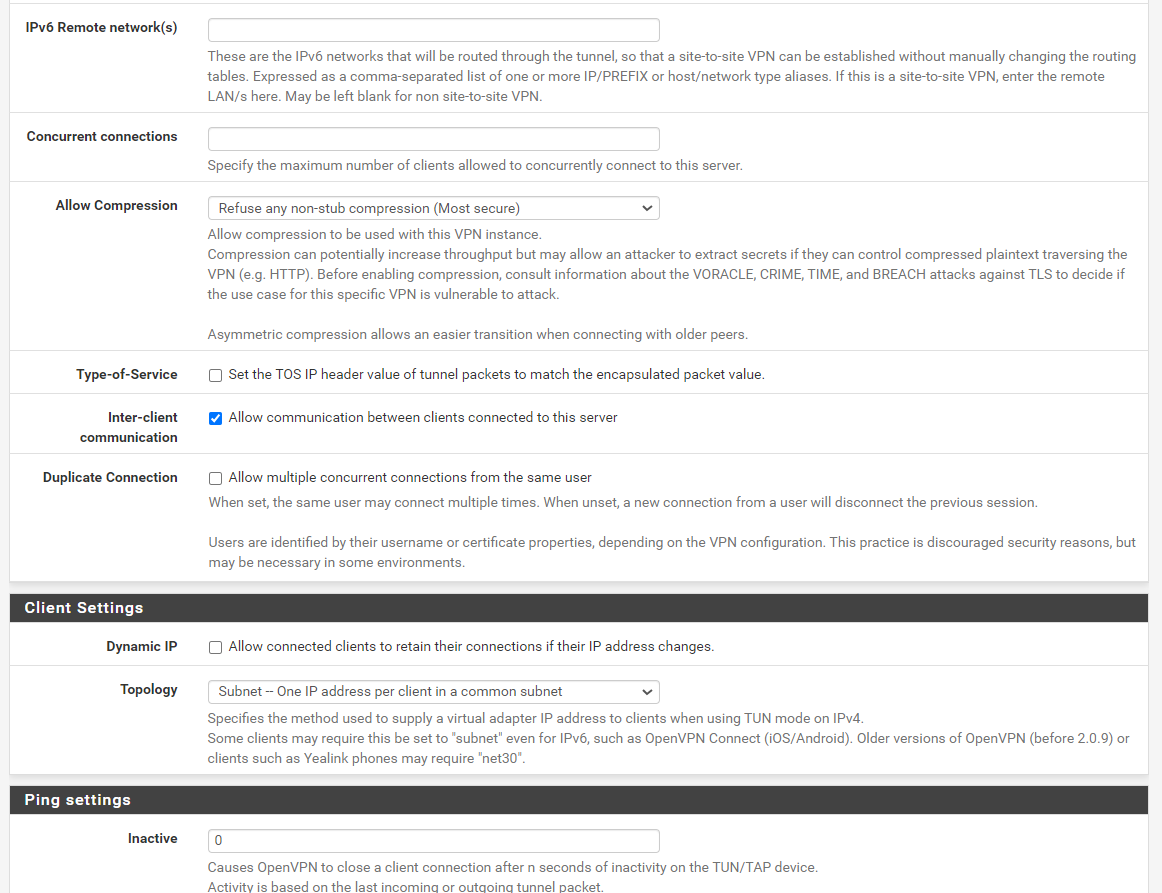
The peer to peer tunnel network is 10.35.101.0/24.
Did you configure CSO for each? Is so, can you show them, please?
Yes, I have configured cso for all of 5 remote servers. Here is one of them(everyone is configured in the same way):
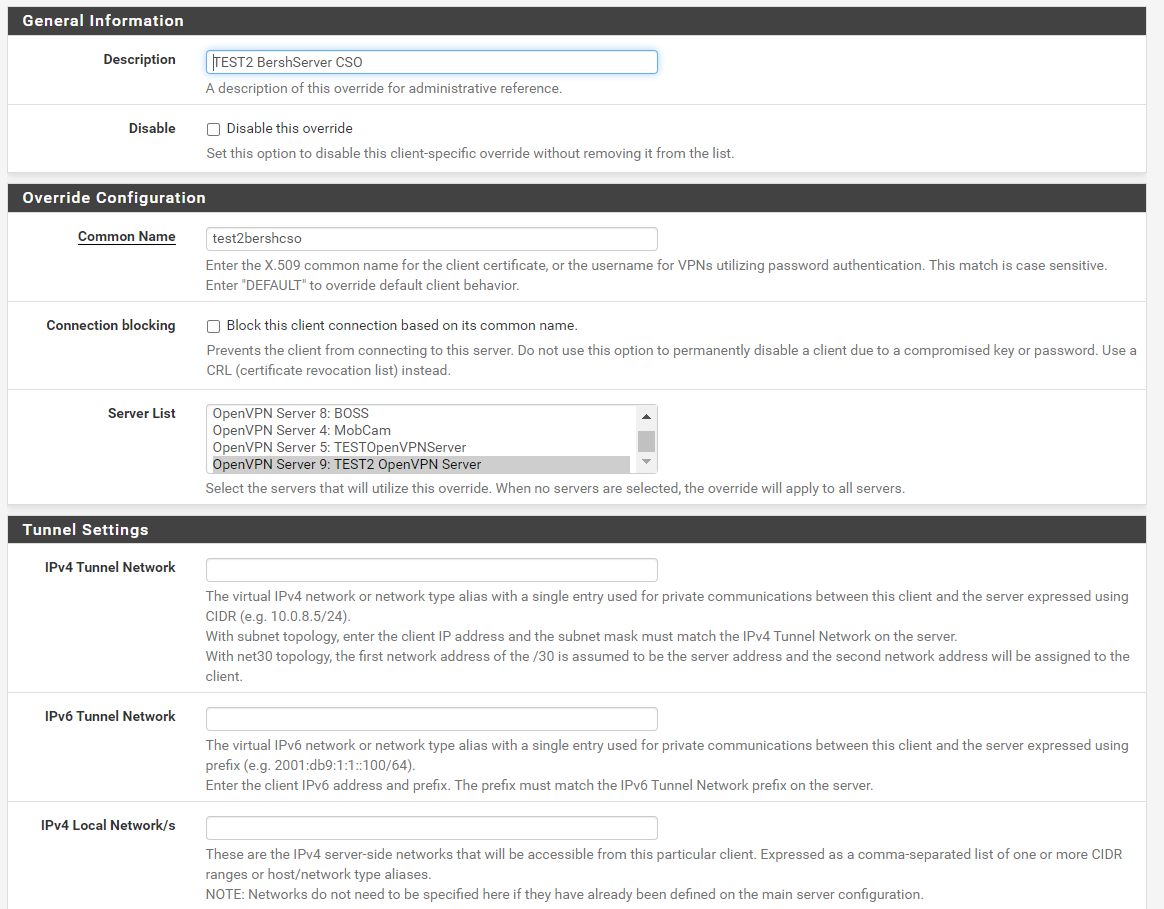
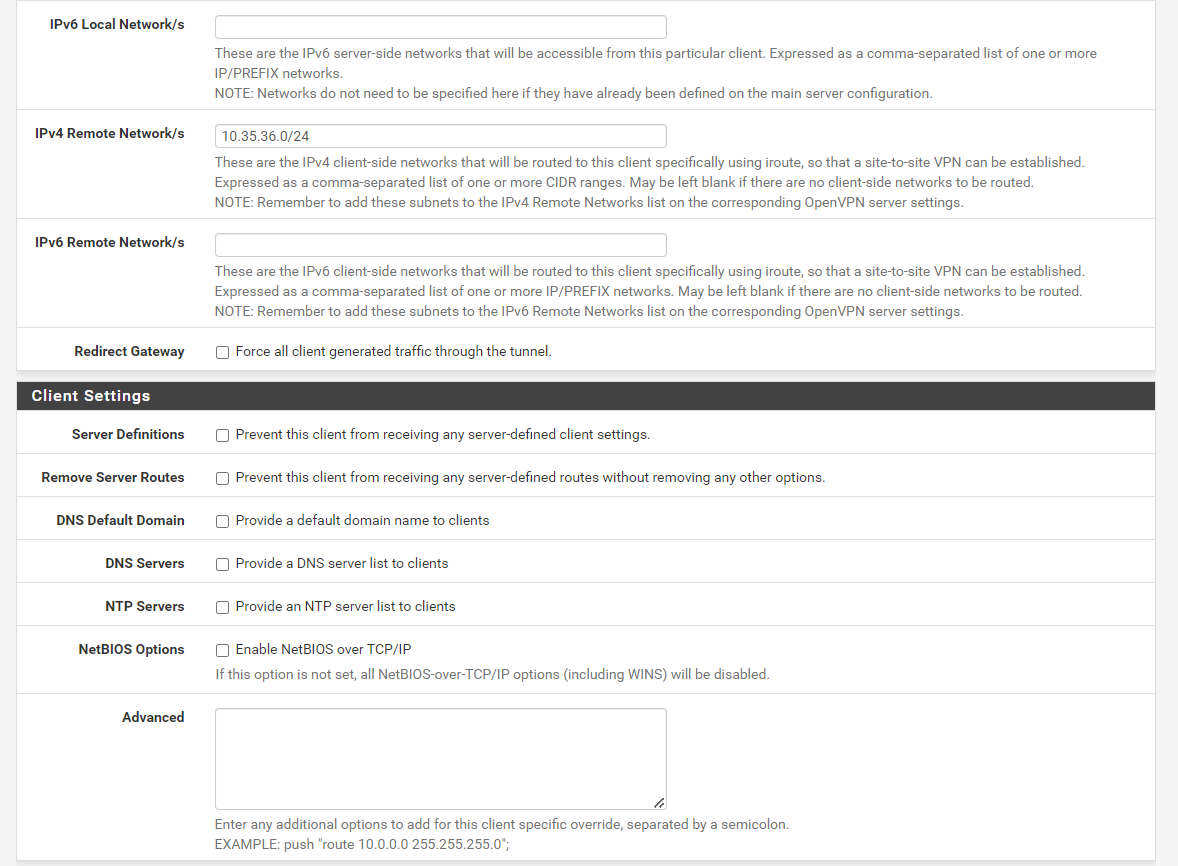
Are these the virtual VPN IPs or local ones?
They are local ones
Can you show all VPN server and client settings, please?
Of course, here is remote access server settings:
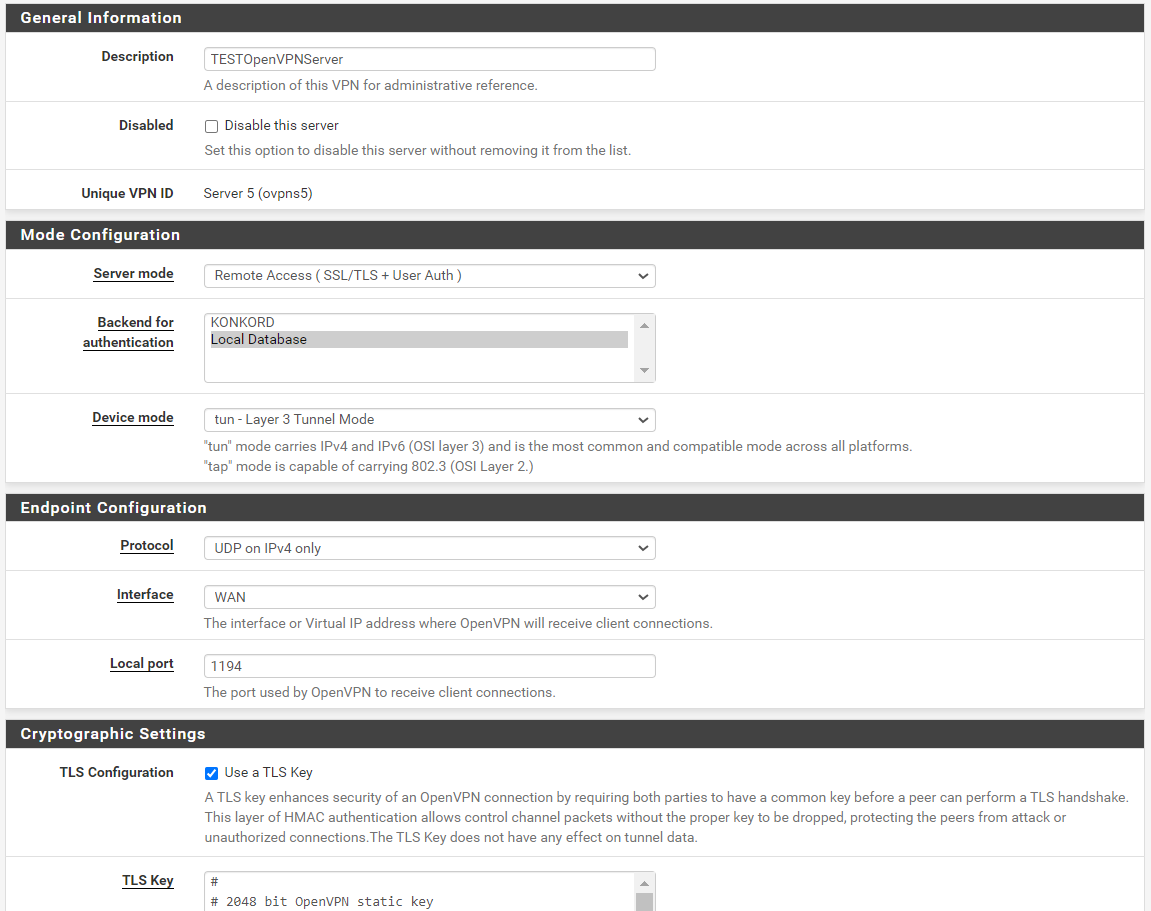
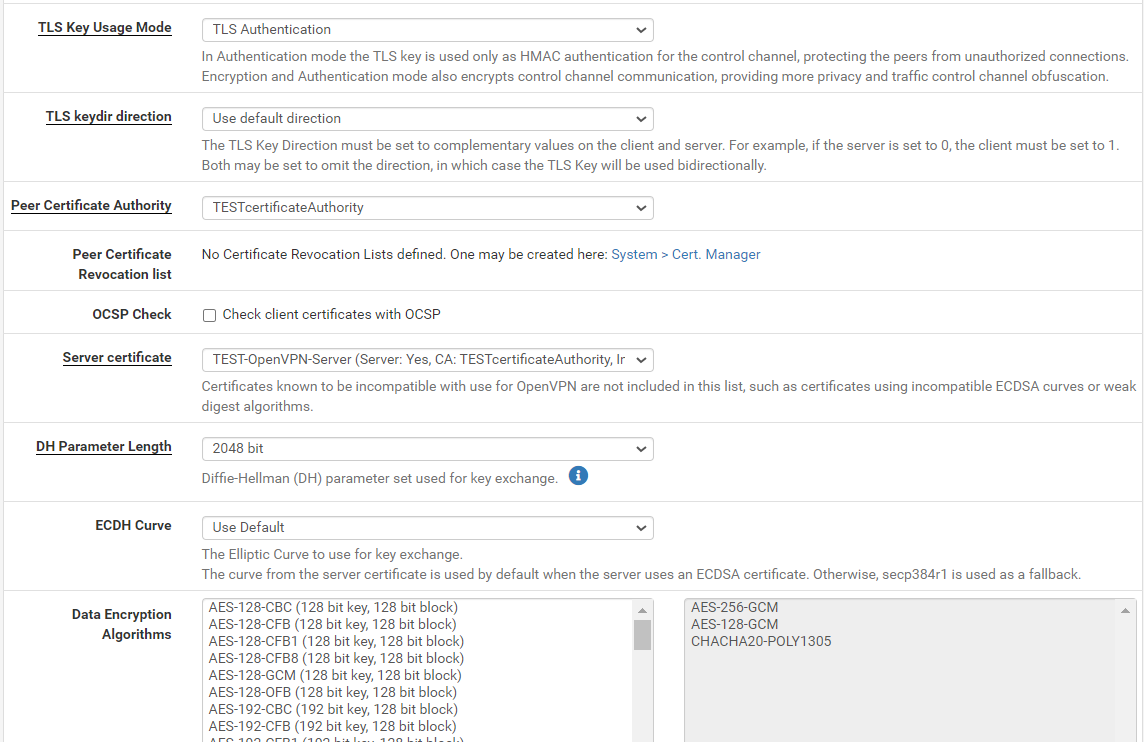
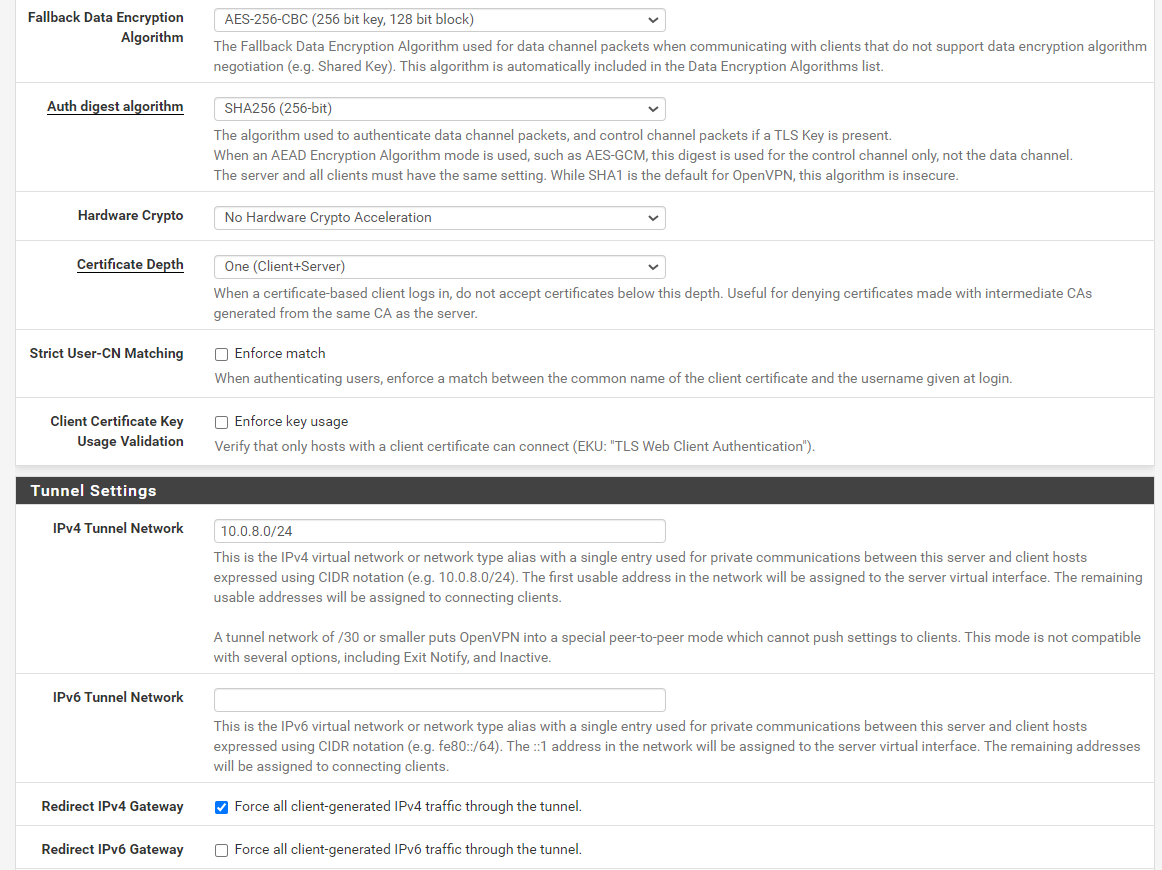
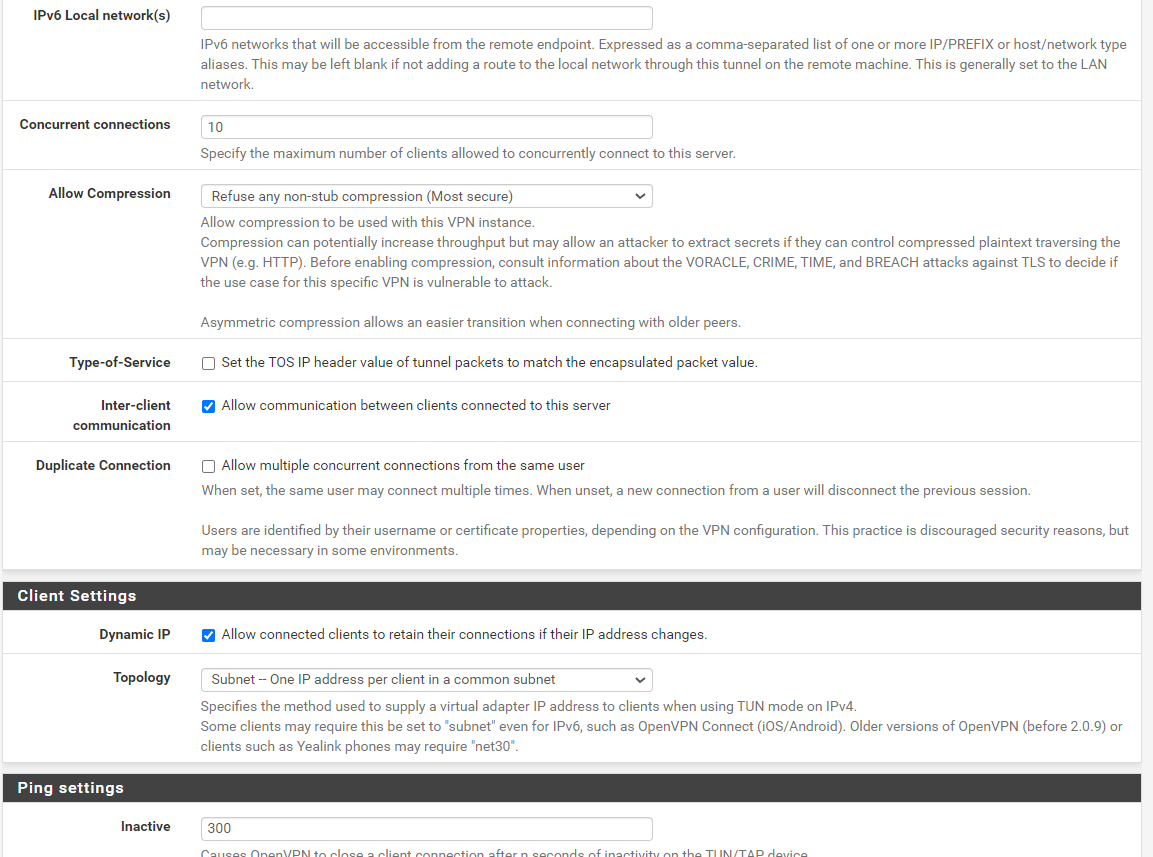
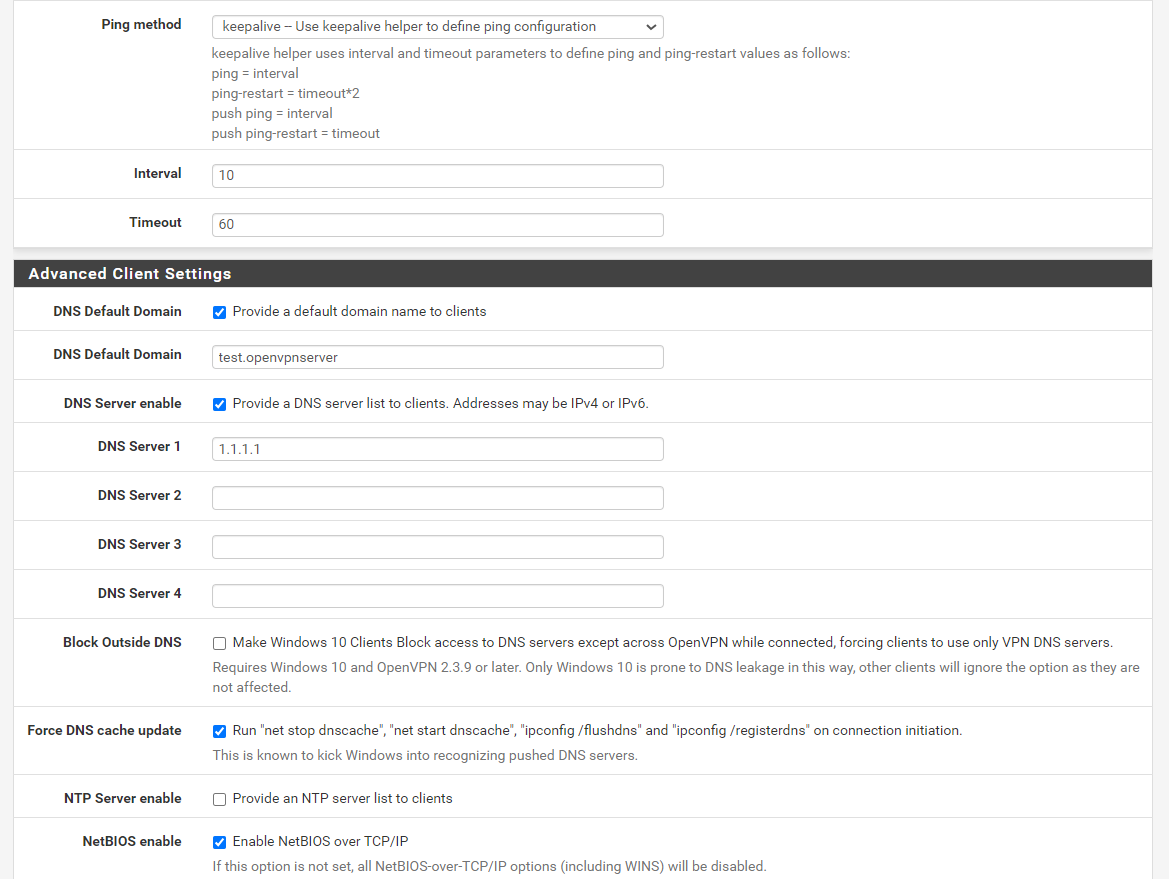
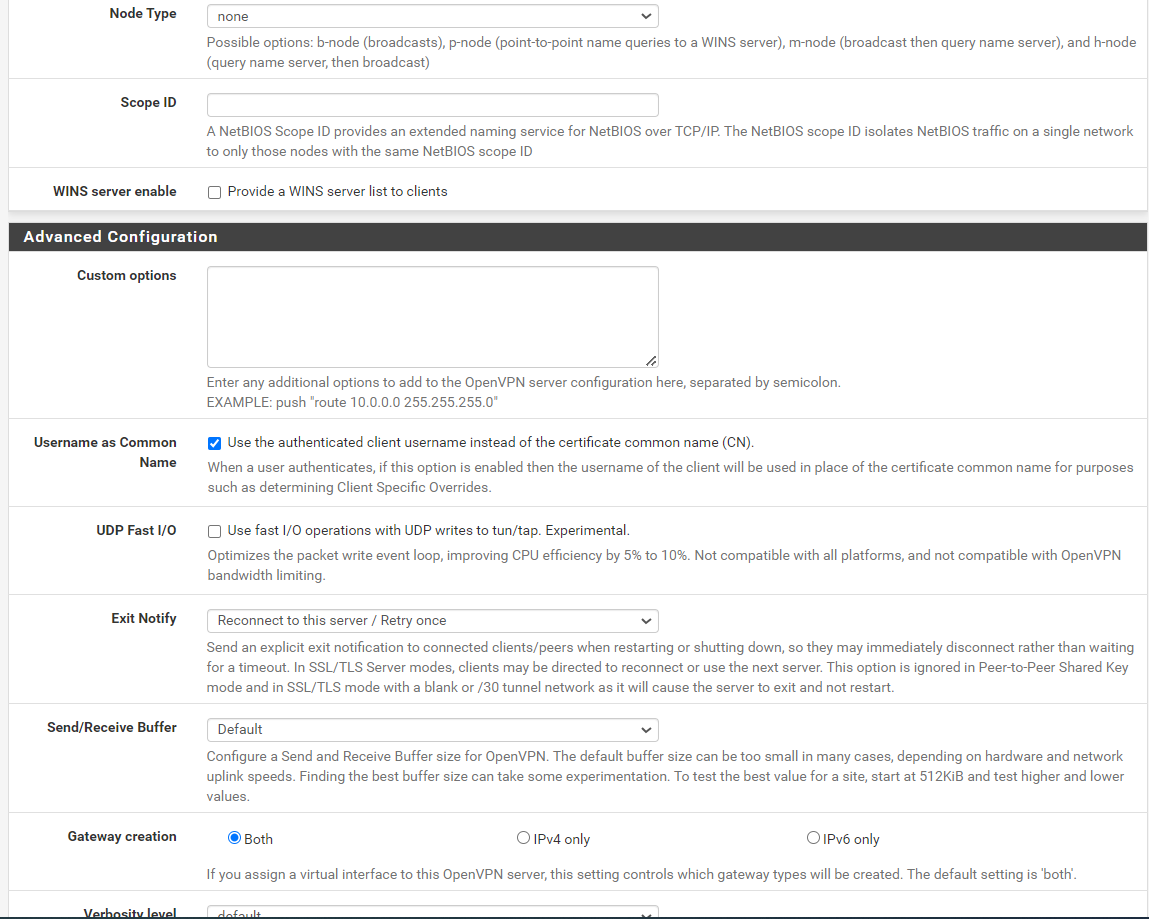
And the peer to peer one:
-
@Shuldyk-Andrii
Should work so far. But on the 10.35.36.1 you have also enter the remote networks for proper routing.
If you only want it to communicate with the main office and the access server clients put this into the "Remote networks" box:10.35.32.0/24,10.0.8.0/24If you also want to reach the other branches you need to add their local networks as well.
If it still doesn't work, check the routing tables of the remote access client and the pfSense C.
-
@viragomann said in Remote access openvpn server can't access peer to peer openvpn servers:
10.35.32.0/24,10.0.8.0/24
Unfortunately, it didn't help.
If it still doesn't work, check the routing tables of the remote access client and the pfSense C.
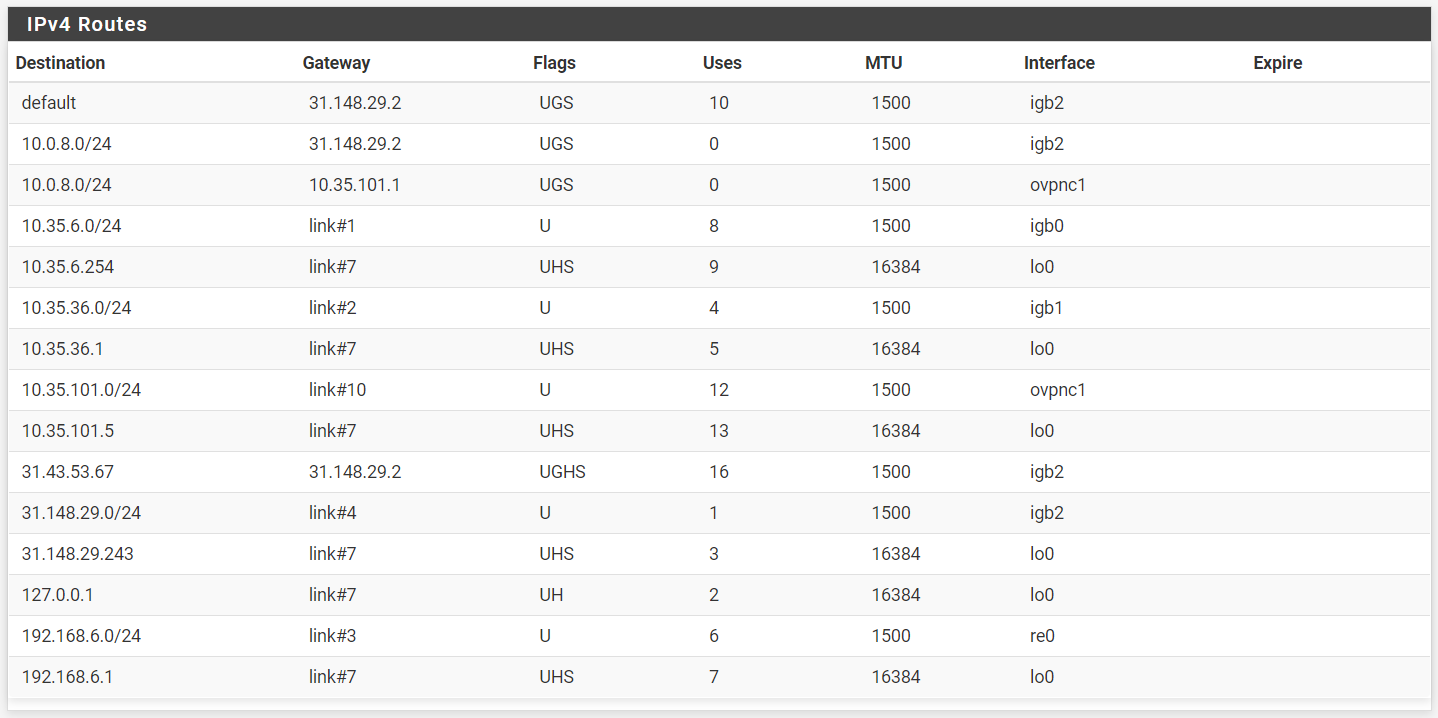
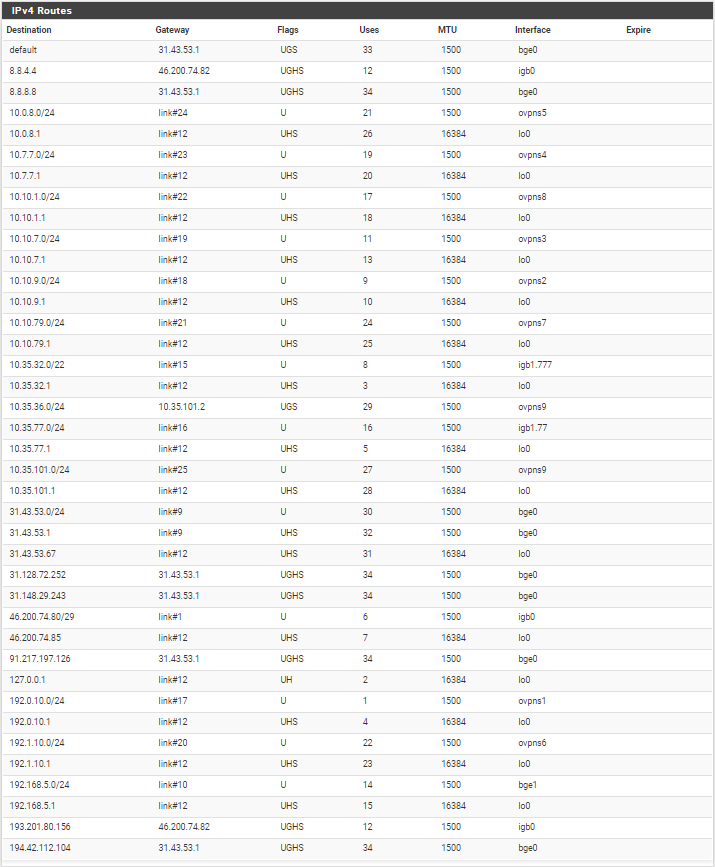
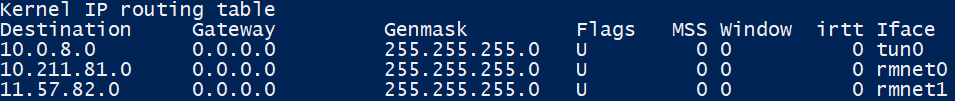
I've already checked routing tables and think it's okay, here how it looks in C:


-
@viragomann
I am actually trying to use this code now in the remote access server:push "route 10.35.36.0 255.255.255.0"route add -net 10.35.36.0/24 gw 10.35.101.6 push "route 10.35.37.0 255.255.255.0"route add -net 10.35.37.0/24 gw 10.35.101.7 push "route 10.35.38.0 255.255.255.0"route add -net 10.35.38.0/24 gw 10.35.101.8 push "route 10.35.39.0 255.255.255.0"route add -net 10.35.39.0/24 gw 10.35.101.9 push "route 10.35.40.0 255.255.255.0"route add -net 10.35.40.0/24 gw 10.35.101.10But I have next error:
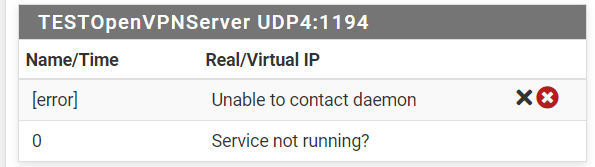
My chief system administrator said he had already solved this problem a few years ago, but he doesn't remember exactly how. The only thing he remembers that he has used something like this code.
Maybe you can know what can be done to this?
-
@Shuldyk-Andrii
The routes of all involved devices can impact the routing. So C, main and access client.
And the point of interest is not a single route only, but the whole IPv4 routing table. There may be other routes interfere with the needed ones.I am actually trying to use this code now in the remote access server:
push "route 10.35.36.0 255.255.255.0"route add -net 10.35.36.0/24 gw 10.35.101.6
push "route 10.35.37.0 255.255.255.0"route add -net 10.35.37.0/24 gw 10.35.101.7These command have wrong syntax and you should not use them anyway. Instead the pfSense GZU provide the "Local Networks" and "Remote Networks" boxes to set the routing.
-
-
@Shuldyk-Andrii
So at C there is a static route in place, pointing the access server tunnel pool 10.0.8.0/24 to the default gateway for whatever reason. Obviously this route have precedence over the OpenVPN route.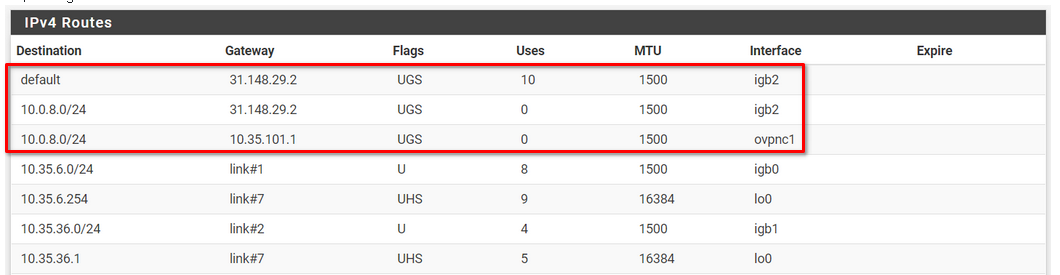
I don't think, that this route is really needed, since the default gateway has a public IP address and might not route private subnets anyway.
-
@viragomann
Okay, it works when I connect using remote server's virtual vpn ip(e.g. 10.35.101.5), but it doesn't work using local one(e.g. 10.35.36.1). Can it be made in the way I could use local IPs? Or I should just give them static virtual IPs? -
@Shuldyk-Andrii
Ah ya, also your client doesn't have proper routes.Did you enter the local networks of C - G into the "Local Networks" box of the access server settings?
You can combine all your subnets by entering 10.35.32.0/20. So the server will push the route for 10.35.32.0 - 10.35.47.255, which include local network of A as well.