Can't perform WireGuard handshake when connected to WAN using PPoE?
-
Hi, everyone!
I'm new to pfsense, in theory I got my router bridged this past weekend. I have to call my ISP to do this procedure as I'm locked out of the router and they gave me PPPoE credentials to have internet access, this may be important later.
Anyways, everything has been working fine up until I wanted to create a WireGuard VPN tunnel to my network. I've followed official documentation, read and followed multiple tutorials (this one did the job for a colleague of mine), but it doesn't look like I ever get traffic when targeting my public IP, even when creating a WAN rule that allows all traffic and doing something like ssh to my public IP from WAN I never see it on Firewall logs with logging on the rule enabled. Just random connections from ports 80, 443.
Usual WG issues are regarding either MTU settings (which I set to 1420 as suggested by WG devs), or wrong CIDRs (/32 on my peer config and /24 on my actual peer configs) by the research I've been doing. However, since I can connect to the VPN when I'm on mobile data, the handshake times out. It only works when I'm on my network. I've tried hitting both my PPPoE IP address and my public IP, and it never seems to work if I'm on WAN.
So, this leads me to ask a bundle of questions, what am I actually missing here? Why rules even as drastic as allowing everything doesn't seem to be effective?
All tutorials and resources I've found on WireGuard actually have WAN using DHCP instead of PPPoE like me. Would that mean that I need to somehow route/forward traffic from WAN => Public IP Adress => PPPoE IP address => LAN? Is that even possible? Can my ISP actually "bridge" my device but still block incoming traffic or not allow me to do port forwarding?
For example, when running
nmapon port 51820 and my public IP return filtered even when I have created a rule that accepts from any source?Sorry if don't post this in WireGuard's specific category despite the title, I feel like it belongs more on Routing/Firewalling/NAT as it looks like my issue is with traffic not actually being handled, ports not being open, etc. Although I'm open to move it where its actually more fitting.
I'd appreciate some help and explanation on how different could a WAN through PPPoE setup would differ from a DHCP one regarding rules and NATting.
Thanks in advance!
-
@hegelmismo You seem to have problems with incoming connections. Nothing pfSense can do there for you.
You can create a rule on your WAN and see, if it gets any hits in the states column. You don't need a running service to see that. -
Hi @Bob-Dig!
Thanks for your reply! Just to get it absolutely clear, does this mean that something is blocking incoming traffic even before it gets to pfsense?

Because, as stated, I created a WAN rule that should have allowed all incoming traffic of any type from any source, and even enabling logging on that rule I saw IPs hitting my Public IP/WAN address/PPPoe IP, my friend tried to SSH directly into my router and couldn't do it either. I ran a ShieldsUP! test on some ports that I specifically opened and always come back as stealth.
I ask this yet again because I called my ISP asking this exact same thing, and they told me that their router is actually bridged now and just acting as a modem translating fiber, but nmapping and trying to connect from WAN using my public IP doesn't result in anything.
Is there anything on my end or something else would be worth checking out?
Thank you!
-
@hegelmismo Is the PPPoE-interface assigned in >Interfaces>Interface Assignments? Maybe your WAN-interface is not the PPPoE-interface right now. You might have to correct that and/or change the default gateway in >System>Routing>Gateways.
-
@Bob-Dig thanks for your feedback again!
Yeah, I think they are assigned properly, unless I'm missing something here and PPPoE actually requires a different assignment.
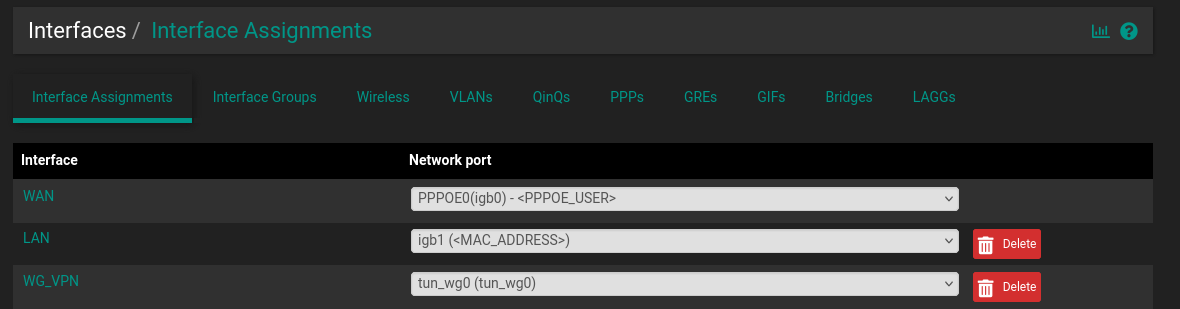
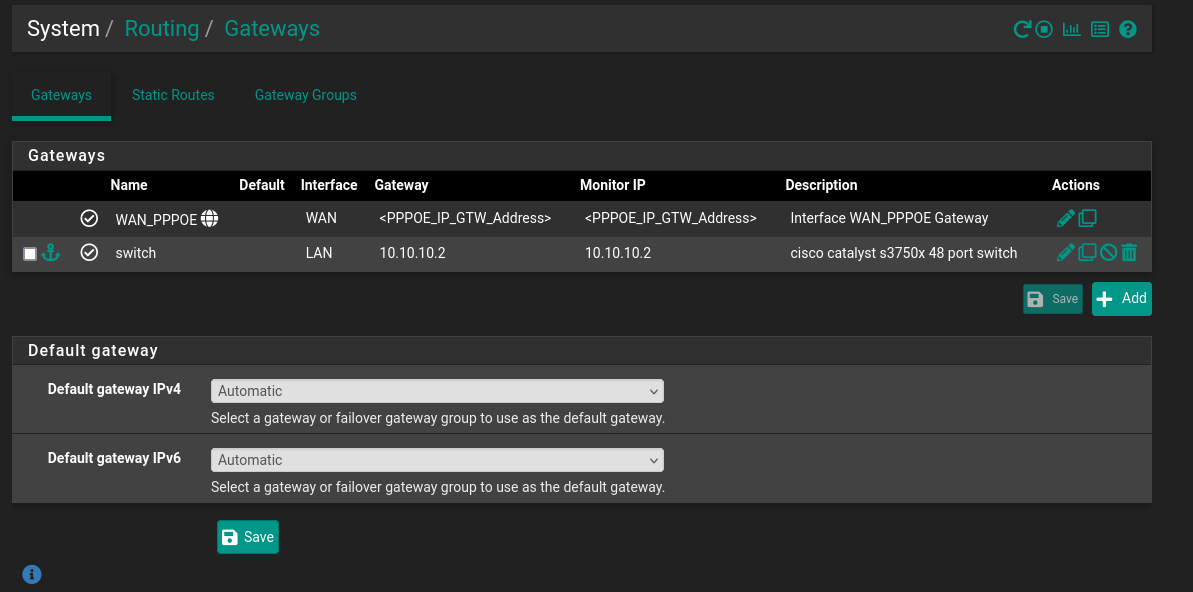
Thank you!