LDAP Auth Servers - AD bind problem with
-
hi there,
was trying to use OpenVPN with AD authentication.AD servers:
- PDC is a Windows Server 2022 Core VM
- RODC is a Synology RS822+ (synced with PDC)
Authentication should preferably run over RODC, because the PDC will often be switched off.
pfsense webinterface
(2.7.2)
i created in System/User Manager/Authentication for both an entryadressed by ip; port 389; standard TCPDiagnostics/Authentication works fine with PDC
php-fpm 3898 /diag_authentication.php: LDAP Debug: Logged in successfully as testuser via LDAP server PDC with DN = CN=Test User,OU=users,OU=department,DC=ad,DC=domain,DC=com. php-fpm 3898 /diag_authentication.php: LDAP Debug: Now searching in server PDC, container OU=users,OU=department,DC=ad,DC=domain,DC=com with filter (samaccountname=testuser). php-fpm 3898 /diag_authentication.php: LDAP Debug: Now Searching for testuser in directory. php-fpm 3898 /diag_authentication.php: LDAP Debug: LDAP connection error flag: false ...but gives an Error with RODC
php-fpm 3170 /diag_authentication.php: ERROR! Could not bind to LDAP server RODC. Please check the bind credentials. php-fpm 3170 /diag_authentication.php: LDAP Debug: LDAP connection error flag: false ...since the log didnt helped, i tested further with..
ldp
(program on an other server, not in the domain)
trying to connect to PDC, everything works fine.
(i tested two methods: "simple bind" and "bind with login information")ld = ldap_open("x.x.x.214", 389); Established connection to x.x.x.214. Retrieving base DSA information... Getting 1 entries: Dn: (RootDSE) configurationNamingContext: CN=Configuration,DC=ad,DC=domain,DC=com; currentTime: 11.07.2024 13:48:36 Mitteleuropäische Somm; defaultNamingContext: DC=ad,DC=domain,DC=com; dnsHostName: testPDC.ad.domain.com; domainControllerFunctionality: 7 = ( WIN2016 ); domainFunctionality: 4 = ( WIN2008R2 ); dsServiceName: CN=NTDS Settings,CN=testPDC,CN=Servers,CN=city,CN=Sites,CN=Configuration,DC=ad,DC=domain,DC=com; forestFunctionality: 4 = ( WIN2008R2 ); highestCommittedUSN: 223178; isGlobalCatalogReady: TRUE; isSynchronized: TRUE; ldapServiceName: ad.domain.com:testpdc$@ad.domain.com; namingContexts (5): DC=ad,DC=domain,DC=com; CN=Configuration,DC=ad,DC=domain,DC=com; CN=Schema,CN=Configuration,DC=ad,DC=domain,DC=com; DC=DomainDnsZones,DC=ad,DC=domain,DC=com; DC=ForestDnsZones,DC=ad,DC=domain,DC=com; rootDomainNamingContext: DC=ad,DC=domain,DC=com; schemaNamingContext: CN=Schema,CN=Configuration,DC=ad,DC=domain,DC=com; serverName: CN=TESTPDC,CN=Servers,CN=city,CN=Sites,CN=Configuration,DC=ad,DC=domain,DC=com; subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=ad,DC=domain,DC=com; supportedCapabilities (6): 1.2.840.113556.1.4.800 = ( ACTIVE_DIRECTORY ); ... supportedControl (40): 1.2.840.113556.1.4.319 = ( PAGED_RESULT ); ... supportedLDAPPolicies (20): MaxPoolThreads; MaxPercentDirSyncRequests; MaxDatagramRecv; MaxReceiveBuffer; InitRecvTimeout; MaxConnections; MaxConnIdleTime; MaxPageSize; MaxBatchReturnMessages; MaxQueryDuration; MaxDirSyncDuration; MaxTempTableSize; MaxResultSetSize; MinResultSets; MaxResultSetsPerConn; MaxNotificationPerConn; MaxValRange; MaxValRangeTransitive; ThreadMemoryLimit; SystemMemoryLimitPercent; supportedLDAPVersion (2): 3; 2; supportedSASLMechanisms (4): GSSAPI; GSS-SPNEGO; EXTERNAL; DIGEST-MD5; -- simple bind ---------- res = ldap_simple_bind_s(ld, 'testuser@ad.domain.com', <unavailable>); // v.3 Authenticated as: 'ad\testuser'. -- with login information --- 0 = ldap_set_option(ld, LDAP_OPT_ENCRYPT, 1) res = ldap_bind_s(ld, NULL, &NtAuthIdentity, NEGOTIATE (1158)); // v.3 {NtAuthIdentity: User='testuser@ad.domain.com'; Pwd=<unavailable>; domain = ''} Authenticated as: 'ad\testuser'.trying to connect to RODC, the simple bind throws an error
ld = ldap_open("x.x.x.215", 389); Established connection to x.x.x.215. Retrieving base DSA information... Getting 1 entries: Dn: (RootDSE) configurationNamingContext: CN=Configuration,DC=ad,DC=domain,DC=com; currentTime: 11.07.2024 10:10:07 Mitteleuropäische Somm; defaultNamingContext: DC=ad,DC=domain,DC=com; dnsHostName: testRODC.ad.domain.com; domainControllerFunctionality: 4 = ( WIN2008R2 ); domainFunctionality: 4 = ( WIN2008R2 ); dsServiceName: CN=NTDS Settings,CN=testRODC,CN=Servers,CN=city,CN=Sites,CN=Configuration,DC=ad,DC=domain,DC=com; forestFunctionality: 4 = ( WIN2008R2 ); highestCommittedUSN: 5906; isGlobalCatalogReady: TRUE; isSynchronized: TRUE; ldapServiceName: ad.domain.com:testRODC$@ad.domain.com; namingContexts (5): CN=Schema,CN=Configuration,DC=ad,DC=domain,DC=com; CN=Configuration,DC=ad,DC=domain,DC=com; DC=ad,DC=domain,DC=com; DC=DomainDnsZones,DC=ad,DC=domain,DC=com; DC=ForestDnsZones,DC=ad,DC=domain,DC=com; rootDomainNamingContext: DC=ad,DC=domain,DC=com; schemaNamingContext: CN=Schema,CN=Configuration,DC=ad,DC=domain,DC=com; serverName: CN=testRODC,CN=Servers,CN=city,CN=Sites,CN=Configuration,DC=ad,DC=domain,DC=com; subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=ad,DC=domain,DC=com; supportedCapabilities (5): 1.2.840.113556.1.4.800 = ( ACTIVE_DIRECTORY ); ... supportedControl (22): 1.2.840.113556.1.4.1413 = ( PERMISSIVE_MODIFY ); ... supportedLDAPVersion (2): 2; 3; supportedSASLMechanisms (3): GSS-SPNEGO; GSSAPI; NTLM; vendorName: Samba Team (https://www.samba.org); -- simple bind ---------- res = ldap_simple_bind_s(ld, 'testuser@ad.domain.com', <unavailable>); // v.3 Error <8>: ldap_simple_bind_s() failed: Strong Auth Required Server error: BindSimple: Transport encryption required. Error 0xB An attempt was made to load a program with an incorrect format. -- with login information --- 0 = ldap_set_option(ld, LDAP_OPT_ENCRYPT, 0) res = ldap_bind_s(ld, NULL, &NtAuthIdentity, NEGOTIATE (1158)); // v.3 {NtAuthIdentity: User='testuser@ad.domain.com'; Pwd=<unavailable>; domain = ''} Authenticated as: 'testuser@ad.domain.com'.i went on pfsense to CLI and tried also
ldapsearch
( ldapsearch 2.6.6 (Dec 8 2023 16:50:08) )
here i get the same errorldapsearch -v -H "ldap://x.x.x.215:389" -b "OU=users,OU=department,DC=ad,DC=example,DC=com" -s one -D "testuser@ad.domain.com" -w "xxxx" ldap_initialize( ldap://x.x.x.215:389/??base ) ldap_bind: Strong(er) authentication required (8) additional info: BindSimple: Transport encryption required.but with the option -Z it works
ldapsearch -v -H "ldap://x.x.x.215:389" -b "OU=users,OU=department,DC=ad,DC=example,DC=com" -s one -D "testuser@ad.domain.com" -w "xxxx" -Z ldap_initialize( ldap://x.x.x.215:389/??base ) filter: (objectclass=*) requesting: All userApplication attributes # extended LDIF # # LDAPv3 # base <OU=users,OU=department,DC=ad,DC=example,DC=com> with scope oneLevel # filter: (objectclass=*) # requesting: ALL # ...output for PDC stayed here successful for unencrypted too.
but with the option -Z i get an error, but still getting results, maybe by switching back to unencrypted communication:ldap_initialize( ldap://x.x.x.214:389/??base ) ldap_start_tls: Server is unavailable (52) additional info: 00000000: LdapErr: DSID-0C09135B, comment: Error initializing SSL/TLS, data 0, v4f7c filter: (objectclass=*) requesting: All userApplication attributes # extended LDIF # # LDAPv3 # base <OU=users,OU=department,DC=ad,DC=example,DC=com> with scope oneLevel # filter: (objectclass=*) # requesting: ALL #so is this meaning, i have to activate transport encryption to get it to work for RODC?
sadly any of this ways dont tell what transport encryption is used. (from further testing with LDP, i know only "negotiate" worked)back to
pfsense webinterface
i changed authentication server RODC setting to SSL/TLS
didnt work.
(out of despair tried many stupid combination of settings) neither STARTTLS nor port 636 worked.i dont know what i should set so that pfsense ldap auth behaves the same as ldapsearch and can access RODC.
i am grateful for any help.
thank you -
@apn Once you change from LDAP to LDAPs, you need to restart php and GUI:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/authentication.html
-
hi, thnx for the quick reply.
was there too, netgate docs was my first stop, looking for answers.
this didnt help.will check tomorrow if synology cli gives more log details, gui is really sparse.
i'm just wondering, why ldapsearch and lpd are working. it seems like pfsense is using only the simple auth method. while the other two can also use SASL, which can connect to both DC's, even though without encryption as they meet minimum requirements with SASL.
LDAP bind requests provide the ability to use either simple or SASL authentication. In simple authentication, the account to authenticate is identified by the DN of the entry for that account, and the proof identity comes in the form of a password. The password is transmitted without any form of obfuscation, so it is strongly recommended that simple authentication be used only over an encrypted connection (e.g., one that has been secured by SSL/TLS, or with the StartTLS extended operation). An anonymous simple bind can be performed by providing empty strings as the bind DN and password (technically, the LDAPv3 specification states that only the password must be empty, but this has been responsible for many security problems with LDAP clients in the past, and many servers require that if an empty password is provided then an empty DN must also be given).
SASL authentication uses the Simple Authentication and Security Layer, as defined in RFC 4422. SASL is an extensible framework that makes it possible to plug almost any kind of authentication into LDAP (or any of the other protocols that use SASL). SASL authentication is performed with a SASL mechanism name and an encoded set of credentials. Some SASL mechanisms may require the client and server to exchange information multiple times (via multiple bind requests and responses) in order to complete the authentication process.
is there any way to activate SASL auth in pfsense?
-
This post is deleted! -
thank you, that seems the only way, since pfsense isnt supporting SASL.
tried yesterday also with Apache Directory Studio
connection is accepted with StartTLS (no SASL), which doesnt work in pfsense .
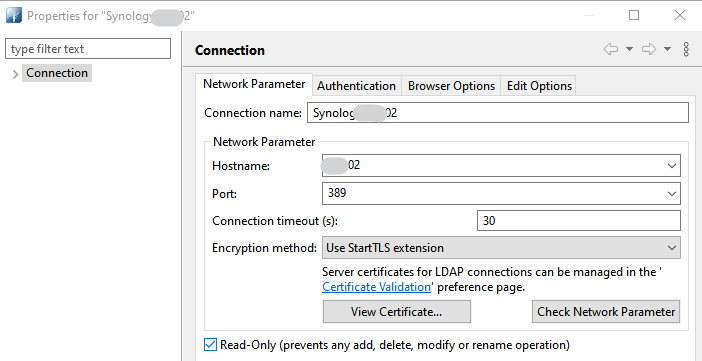
and
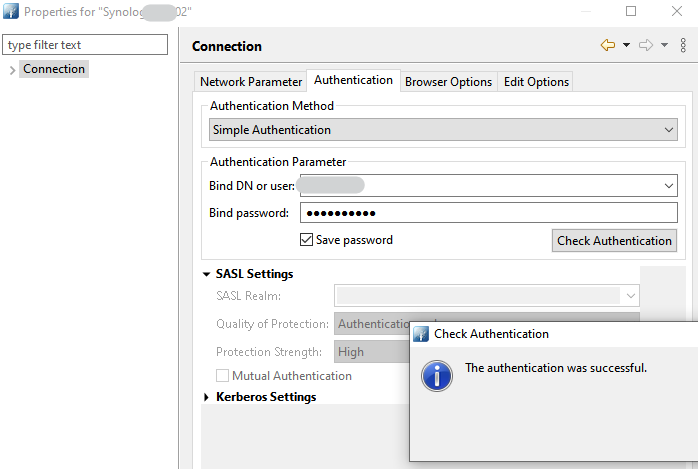
this is getting me really confused.anyway
i will try to export the CA and do it your way,
(was unsuccessful today, to find out how/where to extract it from the synology. the only thing i got was the certificate, no CA )
)
thank your for your help, i will report back how it went (in about two weeks, have to pause this project).