Openvpn tap cannot access LAN
-
I created an OpenVPN server with tap, but it can only ping the gateway (pfSense) and not any local devices. The local devices can neither ping the OpenVPN tap clients.
It does work in TUN, but I need the broadcast domain.
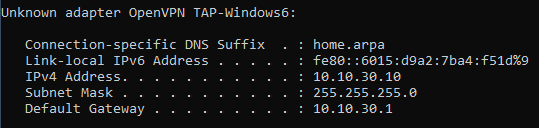
The VPN clients do get an IP from pfSense, but no matter what I change they can't access any LAN hosts (I don't really understand what would I need these settings for if the bridge is doing all the "heavy lifting"?).
I made a floating firewall rule to allow everything, but the VPN clients still can't access/ping the LAN hosts.
-
@darker said in Openvpn tap cannot access LAN:
I made a floating firewall rule to allow everything
On the VPN interface?
-
@viragomann on the "any" interface
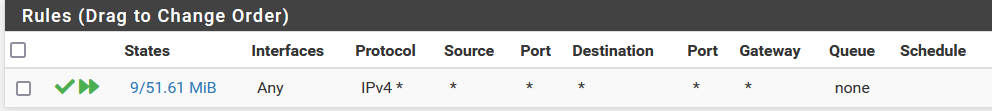
I also added a rule to allow everything on the tap, OpenVPN and LAN interface, and they still can't ping each other.
This is very confusing to me since it can perfectly load the pfSense web configurator.
It's like the bridge between LAN and the tap interface is not working. Maybe allowing everything to everywhere is a mistake and the packets are going where they shouldn't, and it somehow only works VPN client <-> pfSense?
-
@darker
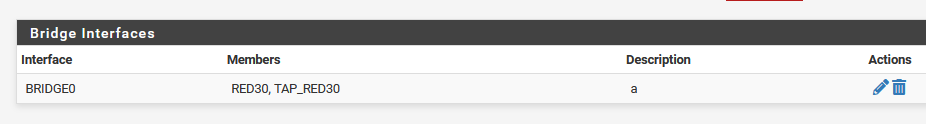
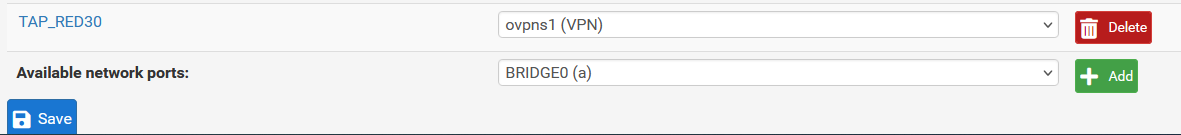
How did you configure the bridge?
Did you enable it and assign an IP? -
@viragomann I did not set the bridge up.
Thinking about how bridges work, it should have the .1 IP not .12. What about the LAN interface?
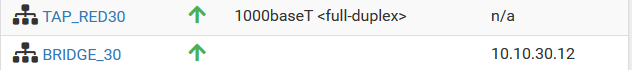
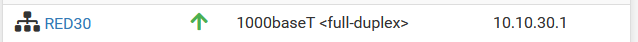
I tried to fix it, but it's still not working
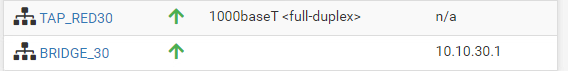
I moved the DHCP server to the bridge interface, but no host is getting addresses now.
-
@darker
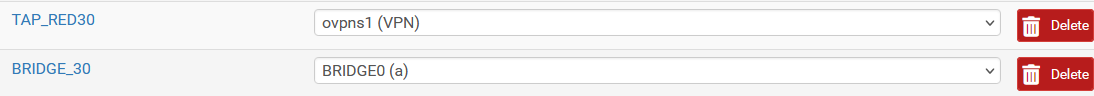
Basically when bridging an interface to LAN, you should take over all the network settings to the bridge interface.To avoid loosing access to the pfSense web GUI, enable the bridge interface and give it a free IP in the LAN subnet, which you connect to with your browser then.
Disable DHCP on LAN and then set the LAN IP setting to none.
Now you can change the bridge IP to the former LAN IP, set the correct mask and configure the DHCP on the bridge after. -
Apparently ESXi vSwitch was blocking the bridge interface on the LAN and only the VPN clients were getting IPs I disabled all the security features on the vSwitch and LAN, and it's all working now.
Thank you, @viragomann