Firewall rules for Guests network on IPv6?
-
"Configuring a Secure Wireless Hotspot" (in pfSense Documentation) is a great article that explains nicely how to firewall guest network from the rest of the LAN(s) but it does concentrate purely on IPv4 world.
What if my LAN is IPv4 / IPv6 (all capable clients have both IPv4 and IPv6 addresses)?
What will be proper firewall rules than to separate Guest network from rest of "private" VLANs?
Obviously blocking RFC1918 networks would not do, if clients will try to communicate over IPv6. There is something like RFC1918 in IPv6 world (I mean RFC4193 Unique Local IPv6 Unicast Addresses using FC00::/7 as as prefix), but this will not help me either, because I don't use these Unique Local IPv6 Unicast Addresses in my subnets.
Clients on my LAN subnets when configured with IPv6, they get "public" globally routable IPv6 addresses from prefixes I've got from my ISP including client devices on Guest network and that's perfectly fine and I like it that way, but in that case:
Do I have to block IPv6 traffic from Guest VLAN to each of my "private" IPv6 network with dedicated rule? Or create Alias for that and list all "private" IPv6 networks there? Because I don't think I can find any general destination target to allow outbound traffic to public internet only. I understand as no IPv6 addresses are actually "private", it's not easy for firewall to distinguish between my local IPv6 subnets and outer destinations on public internet.
Although I have an ideas how to work around this I'm still searching for your opinions, suggestions, advices, what would be considered as best praxes here?
Thank you very much for any suggestions, and have a great day everyone.
-
@manoli
You want a simple solution - don't give your guests an IPv6 address ;)What possible resource would they need to get to via IPv6 while on your guest network? Shoot a vast majority of the planet ISPs still don't even provide IPv6 to their clients.
If you were using Hurricane electric to give your network IPv6, its easy because you could just block access to your /48 network you get from them.
The problem with an alias currently is I don't think there is a way to create a nested alias with the local networks alias like lan subnets, or opt subnets, etc.
So if you were getting a dynamic IPv6 prefix from your ISP, this could change. So if you're in that boat, and you insist on making your life harder by giving guests IPv6.. Then you could prob want to create specific rules that call out your lan subnets, optx subnets, opty subnets, etc.
-
don't give your guests an IPv6 address
Could be as easy as :
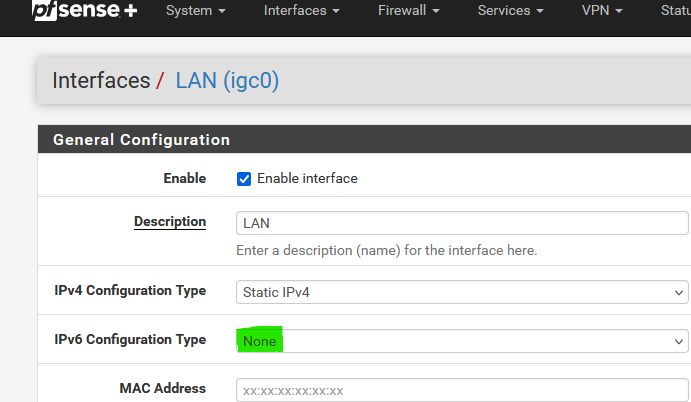
And use only IPv4 rules on your LAN/OPTx firewall.
The default (hidden) IPv6 "block all" rule will take care of the rest.@johnpoz said in Firewall rules for Guests network on IPv6?:
Shoot a vast majority of the planet ISPs still don't even provide IPv6 to their clients.
Hey, Houston ^^ we have (sorry,; native language, but the pictures are nice and you'll understand them ) less problems here : https://lafibre.info/ipv6/ipv6-barometre-2024/
France : 95 % adoption rate and counting .... (Google disagrees here).
Some of the 'way to cheap' ISPs are still ... well, making no progress - not wondering why.
Btw : Normally, I am the pessimist when it comes down to IPv6 , but it's true, everywhere where I test these days, it just 'works'. And as promised : totally transparent.The real issue is : even if the pfSense WAN gets an IPv6 address, that's not the entire story. pfSense also needs a prefix so IPv6 can be used on a pfSense LAN, And another prefix if another LAN exists, and so on. And that, handing over prefixes to pfSense, that totally 'su*****' - is a mess.
@manoli said in Firewall rules for Guests network on IPv6?:
What if my LAN is IPv4 / IPv6 (all capable clients have both IPv4 and IPv6 addresses)?
Bottom line :
Your Internet traffic comes into you house using electric signals over two copper wires (ADSL, cable) or light / laser pulses (fiber) : You don't care.
Packets are 1492 or 1500 bytes : You don't care.
Packets have the IPv6 bit set, or IPv4 bits set : You, my advise, shouldn't care.
That said, IPv6 has its own pros and cons. And because you use pfSense, you've shown you like the little details. Don't worry, you'll have them all
edit : wait, what : Denmark : IPv6 adoption : 13 % .... but DNSSEC adaption 95 % ?!
They prefer a secured DNS ... wonder why that is -
@johnpoz said in Firewall rules for Guests network on IPv6?:
If you were using Hurricane electric to give your network IPv6, its easy because you could just block access to your /48 network you get from them.
Actually this is pretty good and easy idea which for some reason I didn't think about.
I'm not talking about HE IPv6 tunnel to my network, but I'm lucky enough to have static /48 prefix from my ISP, so I can do exactly what you're saying because you are right, these are my "private" IPv6 addresses which I wanna block, thank you!!!
...and regarding IPv6 for Guests network, yes, I still wanna give them IPv6 address, because I believe IPv6 connectivity is crucial for everyone these days.
There might be services on internet IPv6 only, sometimes it's the way to reach "natively" networks behind cgNATs, and after-all I think nearly all client devices (I can't say for Windows and Android devices, have no experience there, but I think do the same), all clients basically prefer IPv6 connectivity if they can (if it is available), unfortunately still this is being so much ignored (also by many ISPs, which is a bit of shame, and would be always my no-go for ISP who does not provide IPv6 with reasonable prefix size).
-
@manoli said in Firewall rules for Guests network on IPv6?:
these are my "private" IPv6 addresses which I wanna block, thank you!!!
Your one and only IPv4 WAN, while it is attributed to you as the main ISP subscriber, falls under the same (legal) responsibility.
The ISP (and local government) doesn't care that you've lent your ISP Internet connections to some friends @home, using your Wifi and one of your RFC1918, and finally, their connection is going out over your WAN = using your IPv4.For a totally non trusted network (a network with connected people that can potentially create problems), I advise :
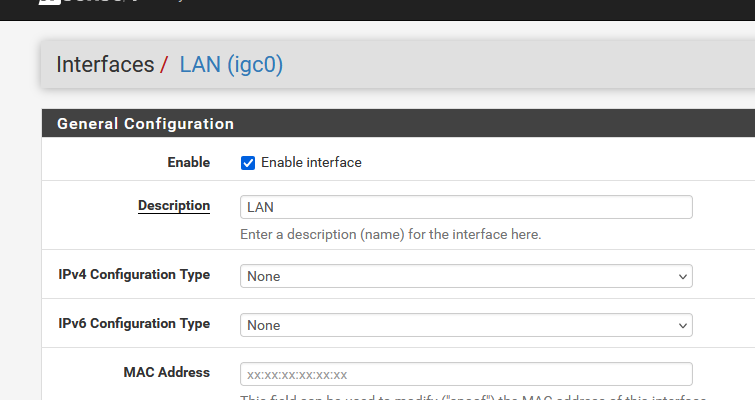
( sorry
 )
)Typically, you should do the same thing with an IPv6 as what you would do with an IPv4.
If needed, they know how to find you. Always.A way more serious solution is :
Route your non trusted network out over a VPN. You live in Hong Kong ? Route it out over VPN to some VPN POP in Washington DC (US) (or the other way around).
You'll be save now, no issues, guaranteed. No black US helicopters in China.Most VPNs are IPv4 anyway.
-
@Gertjan said in Firewall rules for Guests network on IPv6?:
The default (hidden) IPv6 "block all" rule will take care of the rest.
I believe this rule is not default any more. System / Advanced / Networking - Allow IPv6 was always checked by default (for me, since couple years ago).
@Gertjan said in Firewall rules for Guests network on IPv6?:
And that, handing over prefixes to pfSense, that totally 'su*****' - is a mess.
Using IPv6 subnets from ISP delegated prefix or delegating sub-prefixes further down the line works actually super well with pfSense! (there are other companies having huge problems there (like Ubiquity), they should think about them self.)
Bottom line:
My internet comes using optic fiber, my MTU on WAN has to be set 1492 due to PPPoE and also have to set MSS 1432 (40 bytes for IPv6 + 20 for TCP, this should normally happen automatically but my ISPs router for some reason doesn't send that properly), but I can live with that and with these settings IPv6 connectivity works great....and for many services out on the internet i get lower latency over IPv6 than over IPv4 ;-)
-
@Gertjan said in Firewall rules for Guests network on IPv6?:
or a totally non trusted network (a network with connected people that can potentially create problems), I advise :
Yeah, this one was nice...

I understand your concerns about Untrusted networks, but...
...my Guests network is not public at all, client devices still have to provide correct password to authenticate, Guest network is just place where device end up if it is not authenticated any further (either with certificate or dedicated username password, at least).
@Gertjan said in Firewall rules for Guests network on IPv6?:
A way more serious solution
I'm just wondering why would I want to route my Guests network via VPN? You mean not to compromise my IP addresses if there is a rough device connected to Guests network, I might be possibly banned if that device tries something bad out there? That probably makes sense.
And just to clarify I live in Czechia, so no Hong Kong, China, etc. and the only public VPN I use from time to time is Cloudflare (for simplicity), and I do not trust any VPN provider either free or paid, I don't care (only my own VPNs which I have setup here and there, on VPS where I'm the only one in control of that host providing VPN concentrator for me), ah, yeh Tailscale is also an exception I can accept. ;-)
-
@manoli said in Firewall rules for Guests network on IPv6?:
Allow IPv6 was always checked by default (for me, since couple years ago).
That has zero to do with the default deny that is on every interface just so you know..
-
@manoli said in Firewall rules for Guests network on IPv6?:
there are other companies having huge problems there
Nice to year that some ISP had read the RFC. Still quiet rare these days.
@manoli said in Firewall rules for Guests network on IPv6?:
optic fiber, my MTU on WAN has to be set 1492 due to PPPoE and also have to set MSS 1432
Oh ... fiber over pppoe. Oops.
Normally, when you have fiber, the ISP can deliver multiple hundreds of Mbits/sec or even several Gbit/sec. If that traffic has to go over a mono thread/process that handles the pppoe traffic (pppoe isn't multi core on FreeBSD/pfSense) thne that's a limiting factor.
Clamping down IPv6 like that isn't ideal.@manoli said in Firewall rules for Guests network on IPv6?:
...my Guests network is not public at all, client devices still have to provide correct password to authenticate, Guest network is just place where device end up if it is not authenticated any further (either with certificate or dedicated username password, at least).
I mentioned a the usage of a VPN to 'anywere' as it can be used to protect your own WAN IPv4 and IPv6, the ones your are accountable for. If you trust the devices used, no need for the VPN hassle.
-
Here are my rules for guest WiFi:
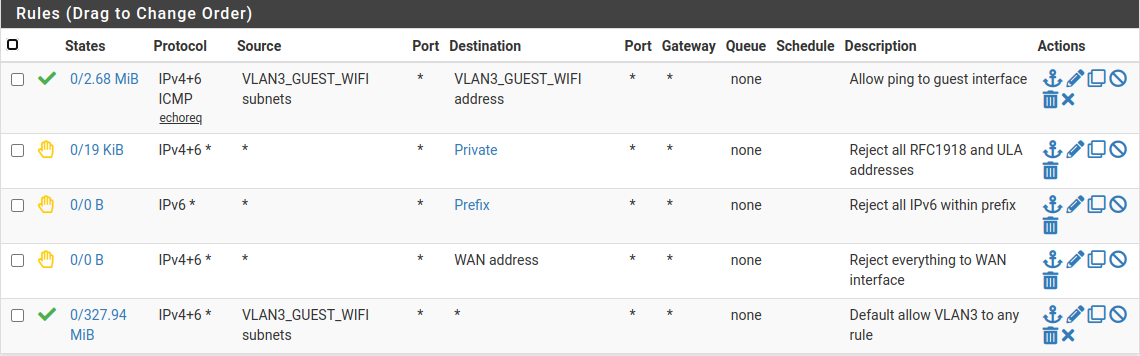
They only allow pinging the VLAN interface and accessing the Internet.
Private is an alias for all RFC1918 and ULA addresses.
Prefix is an alias for my /56 prefix from my ISP. -
@johnpoz said in Firewall rules for Guests network on IPv6?:
You want a simple solution - don't give your guests an IPv6 address ;)
For a simple solution, look at my post of my guest WiFi rules.