Unable to Establish Wireguard Connection Over Cell Network
-
Hi I'm trying to setup a simple remote access client VPN using Wireguard. At the moment, I'm struggling to get my mobile iOS device to establish a connection with my home network via a Wireguard tunnel when it's using a cell network.
Setup details:
LAN Interface @ 172.25.1.1
Netgate SG 1100 is behind ISP modem connected via WAN portWG_TEST Interface on tun_wg1 network port:
Enabled
Static IPv4
MTU / MSS 1420
IPv4 Address @ 172.26.2.1/24Firewall > NAT > Outbound:
Hybrid Outbound NAT
WAN Interface
IPv4
Source Network: 172.26.2.0/24
Translation: WAN AddressFirewall Rules > WAN:
Protocol: IPv4 UDP
Source: *, Port: *
Destination: WAN Address, Port: 51821Firewall Rules > Wireguard:
Protocol: IPv4
Source: *, Port: *
Destination: *, Port: *Firewall Rules > Wireguard:
Protocol: IPv4
Source: *, Port: *
Destination: *, Port: *Firewall Rules > WG_TEST:
Protocol: IPv4
Source: *, Port: *
Destination: *, Port: *VPN Wireguard Tunnels:
tun_wg1
Address / Assignment: WG_TEST
Listen port: 52821Peers:
iPhone Test
Endpoint: 172.26.2.2:52821
Allowed IPs: 0.0.0.0/0iOS App:
[Interface]
pubKey = MY_PUB_KEY (i've confirmed it matches config in pfSense)
Addresses = 172.26.2.2/24
DNS Servers: 9.9.9.9[Peer]
pubKey = MY_PUB_KEY (i've confirmed it matches config in pfSense)
Endpoint = MY_IP:51821
AllowedIPs = 0.0.0.0/0I'm almost certain the issue is due to my iOS Wireguard App's configuration or some limitation of the iOS Wireguard App I'm unaware of
Any help would be greatly appreciated! Thank you
-
@emnul maybe I might be doing it a different way than you are but this is how I have WireGuard working for my iOS and Windows Laptop when I'm on the go:
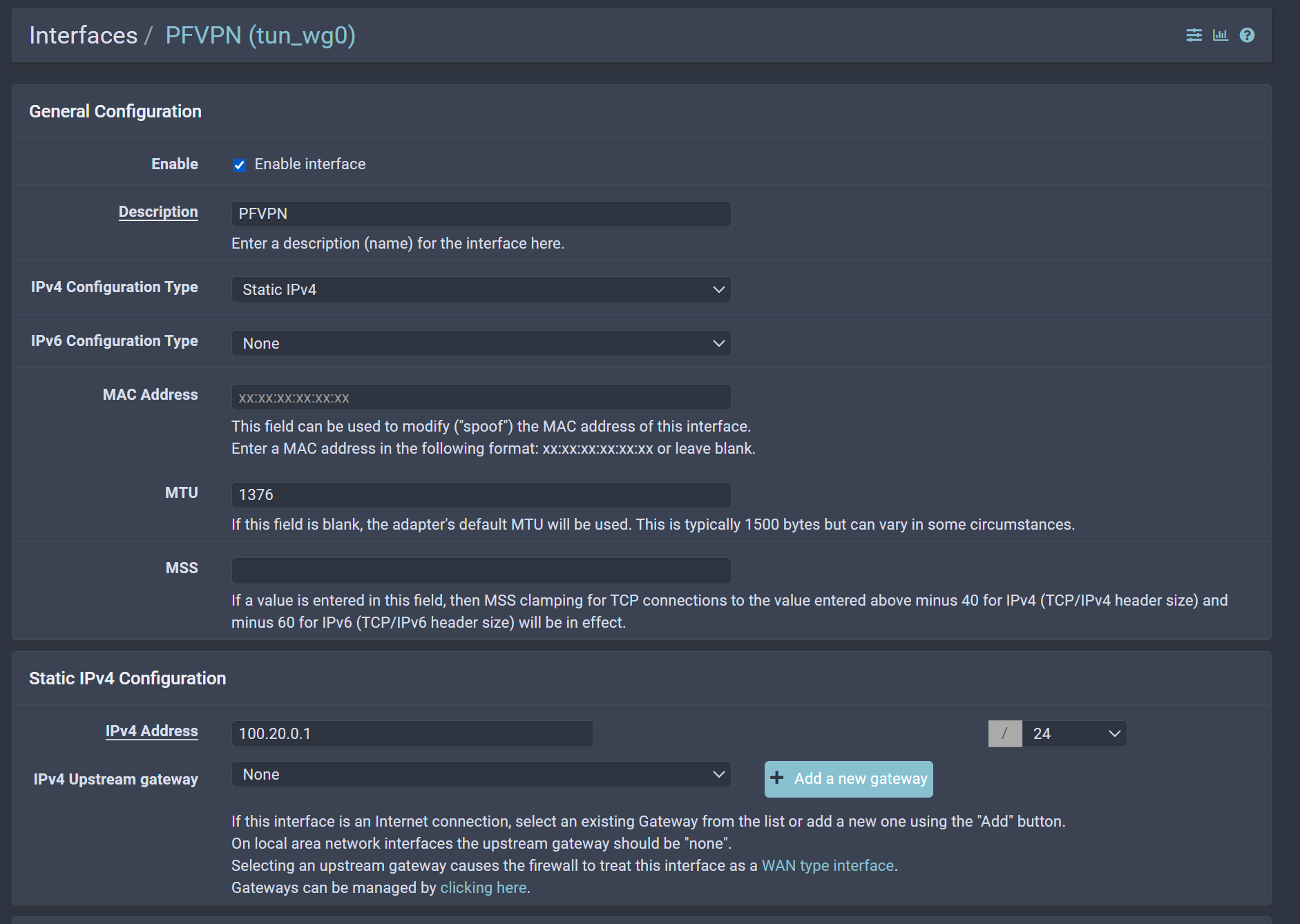
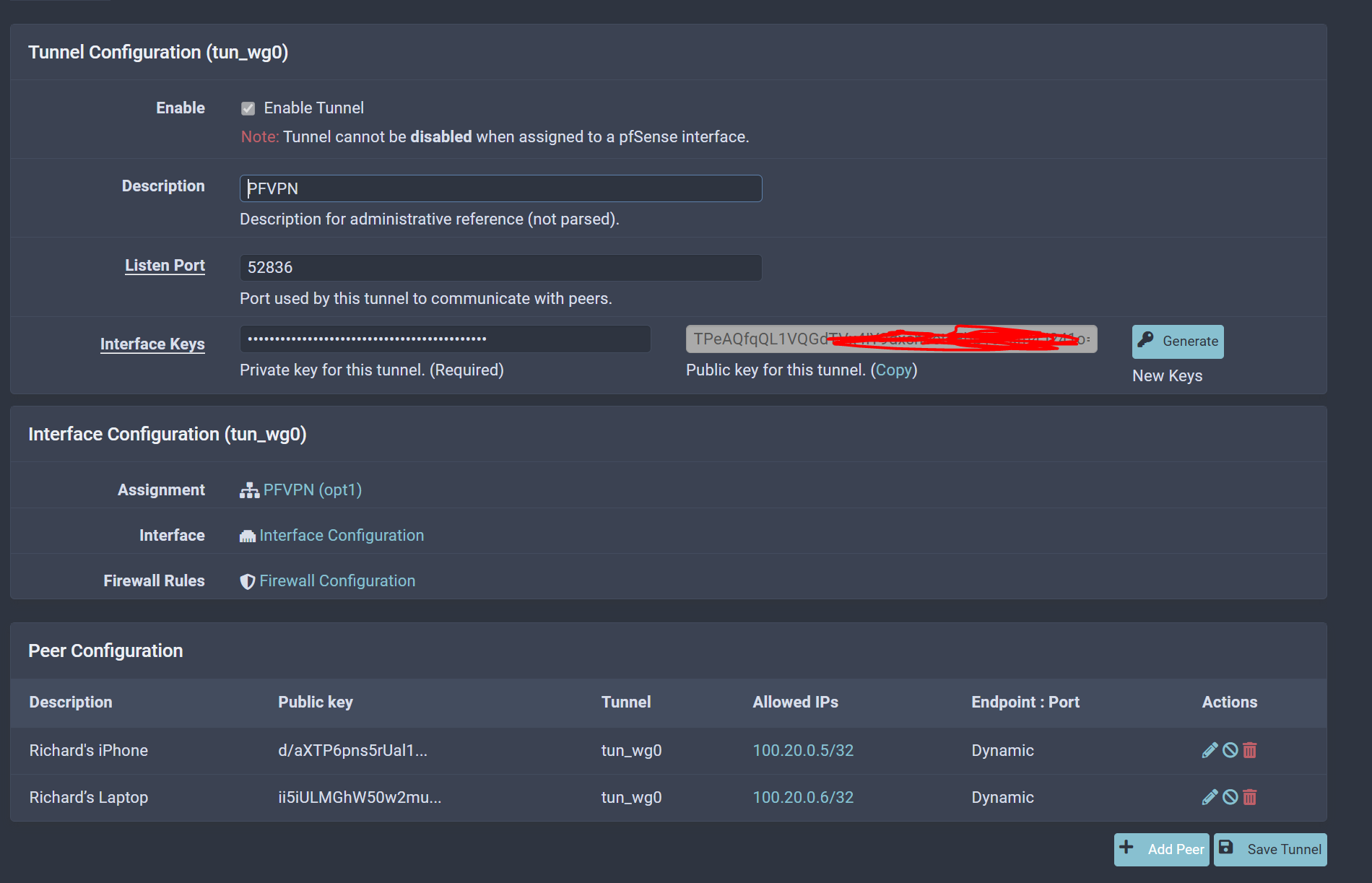
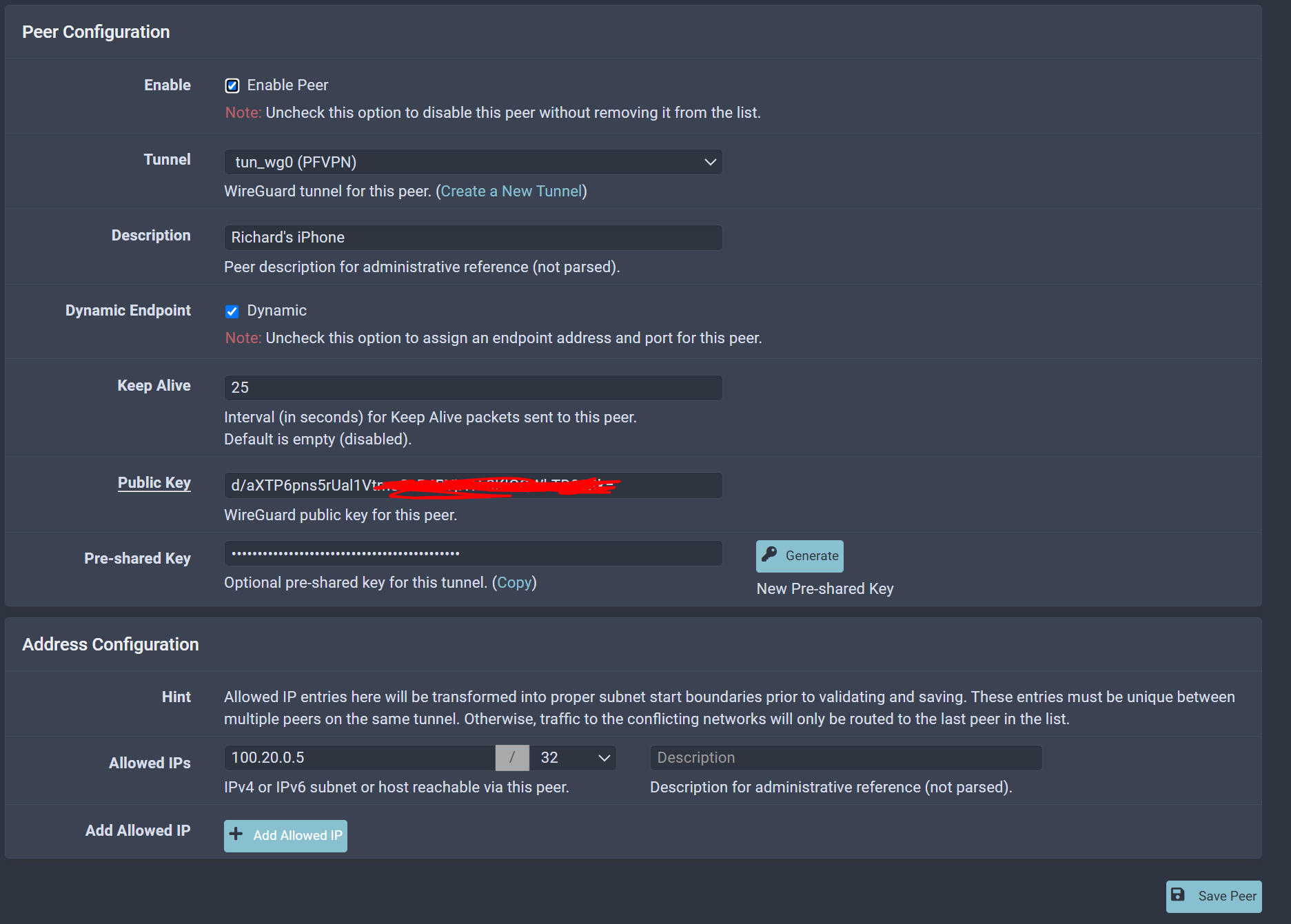
Firewall Rules:
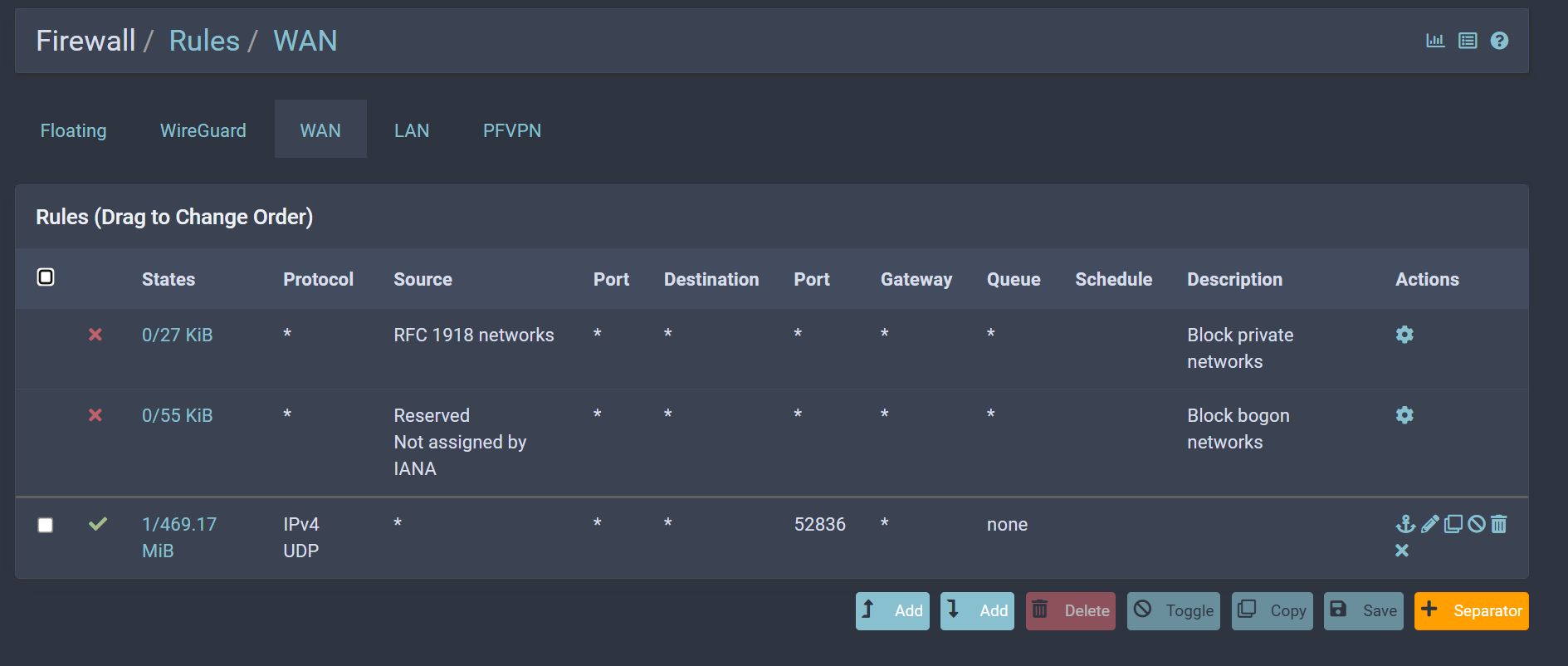
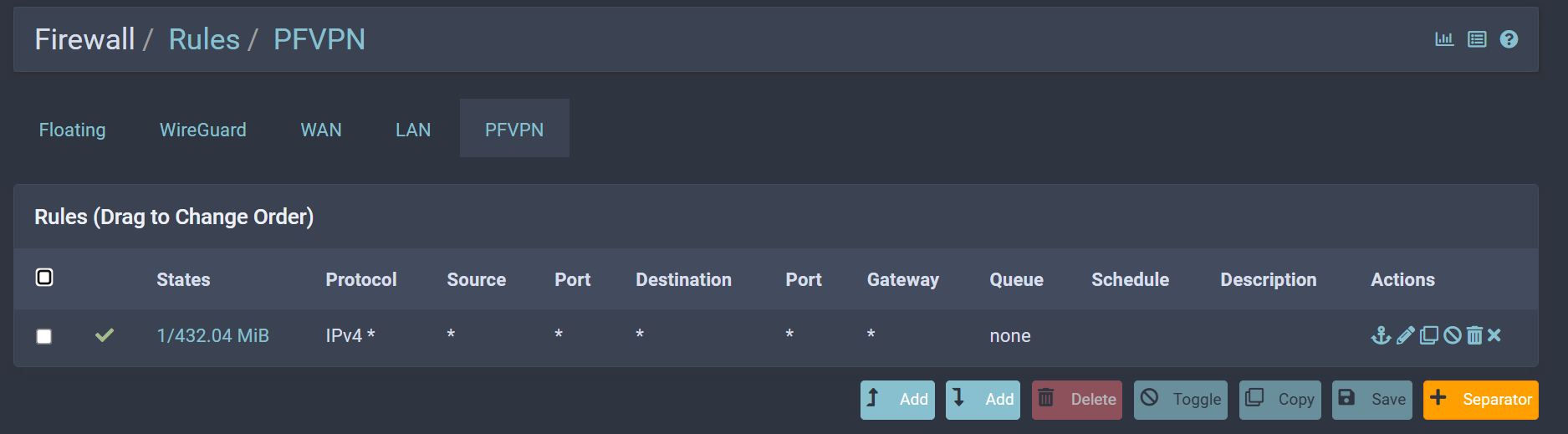
This is how I have it configured on the WireGuard app on my phone:
[Interface]
PrivateKey = -removed-
Address = 100.20.0.5/24
DNS = 172.22.1.11
MTU = 1376[Peer]
PublicKey = -removed-
PresharedKey = -removed-
AllowedIPs = 0.0.0.0/0
Endpoint = myDynamicDNSaddress.org:52836
PersistentKeepalive = 24The 172.22.1.11 IP on the DNS is my pfSense address. I don't know if this is what people usually put here but I only want it to query my pfSense (for pfBlockerNG) and haven't had any issues with either my iPhone nor Windows laptop.
I have my own domain and have it to automatically update the Public IP using Dynamic DNS. My ISP sometimes changes the Public IP so this is done so I don't have to continuously keep updating it.
Other than that I didn't add any other rules nor changes. I see you added the Outbound rules, I have this set to Automatic which WireGuard automatically adds the rules for me.
-
@rtorres Here are some of the logs I'm seeing on my end. Tbh it looks like gibberish to me but maybe it makes sense to someone else.
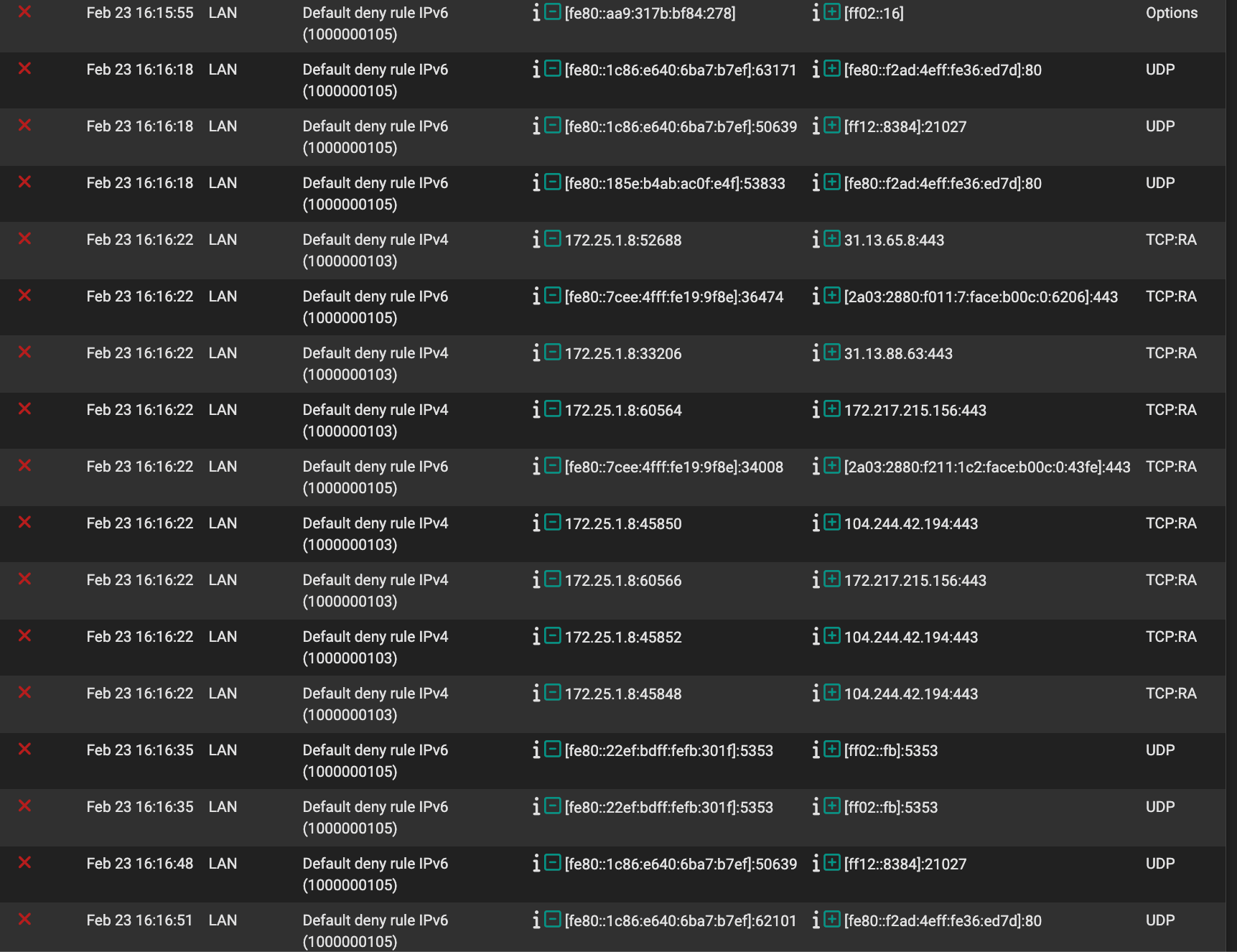
The Default Deny IPv6 (1000000105) is super confusing. System > Advanced > Networking > Allow IPv6 is checked so I have no idea why this rule is enabled nor how to disable since it seems to be an implicit rule
-
@emnul I don’t know if this was a typing mistake but I see form your post that your WG_TEST tunnel is listening to port 52821 and your iOS device is trying to connect to 51821. These should match for both Tunnel and Peer
VPN Wireguard Tunnels:
tun_wg1
Address / Assignment: WG_TEST
Listen port: 52821And your peer is:
[Peer]
pubKey = MY_PUB_KEY (i've confirmed it matches config in pfSense)
Endpoint = MY_IP:51821
AllowedIPs = 0.0.0.0/0You MUST have your WG_TEST (tun_wg1) Interface /24 and your Peers as /32.
Based on the info you provided on your first post, this is how your WireGuard and Peer SHOULD look like:
Tunnel Setup:
VPN > WireGuard > Tunnels > Edit tun_wg1 Description: WG_TEST Listen Port: 51821 Interface Keys: [Auto-generated]Interface Setup:
Interfaces > WG_TEST IPv4 Configuration Type: Static IPv4 IPv4 Address: 172.26.2.1/24 MTU: 1420WAN Firewall Rules:
Firewall > Rules > WAN Action: Pass Protocol: UDP Source: Any Destination: WAN Address Port: 51821Firewall > Rules > WG_TEST Action: Pass Protocol: Any Source: WG_TEST Destination: AnyOutbound (Hybrid Mode) Setup:
Firewall > NAT > Outbound Interface: WAN Source Network: 172.26.2.0/24 Destination: Any Translation: WAN AddressFor Peer Config (in WireGuard):
VPN > WireGuard > Peers Description: iOS Device Tunnel: WG_TEST Allowed IPs: 172.26.2.2/32 Endpoint: DynamicOn your iOS WireGuard App:
[Interface] PrivateKey = [Auto Generated] Address = 172.26.2.2/24 DNS = 9.9.9.9 MTU = 1420 [Peer] PublicKey = [Auto Generated] PresharedKey = [Auto Generated] AllowedIPs = 0.0.0.0/0 Endpoint = WAN IP:51821If you are still having an issue:
This is the YouTube video I used to setup my WireGuard and it's been working flawlessly for 2+ years.
How to Install WireGuard on pfSense (Tutorial)
Follow it from start to finish in its entirety and set up as in the video. Made the mistake of cutting the video short thinking I was done but my WG was refusing to connect.
I suggest you configuring all of the IPs as in the video to get an undertsanding and a working config, then modify as you like (with your desired 172.26.2.0/24 IPs).