[Solved] OpenVPN Connection issues
-
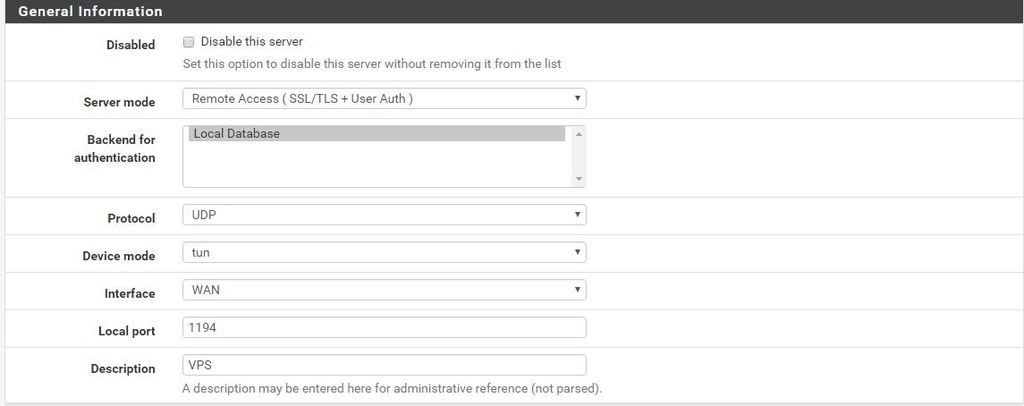
PFSENSE 2.3
Iv been trying to get this thing working for 2 days now. Iv read over everything 100 times and used the wizard. No matter what I do it wont connect to the router. I tried different port numbers UDP/TCP. I did remote port checks on 1194 trying it on UPD and TCP and the port scan always says its closed on either protocol even trying different ports. Its almost like openvpn isn't binding to the port. Iv rebooted the gateway. Rebooted the pf server. Cleared the state table. Removed everything multiple times and started from scratch.. I don't know what i'm missing to make this this work..
OpenVPN server log
May 8 18:02:25 openvpn 79814 event_wait : Interrupted system call (code=4)
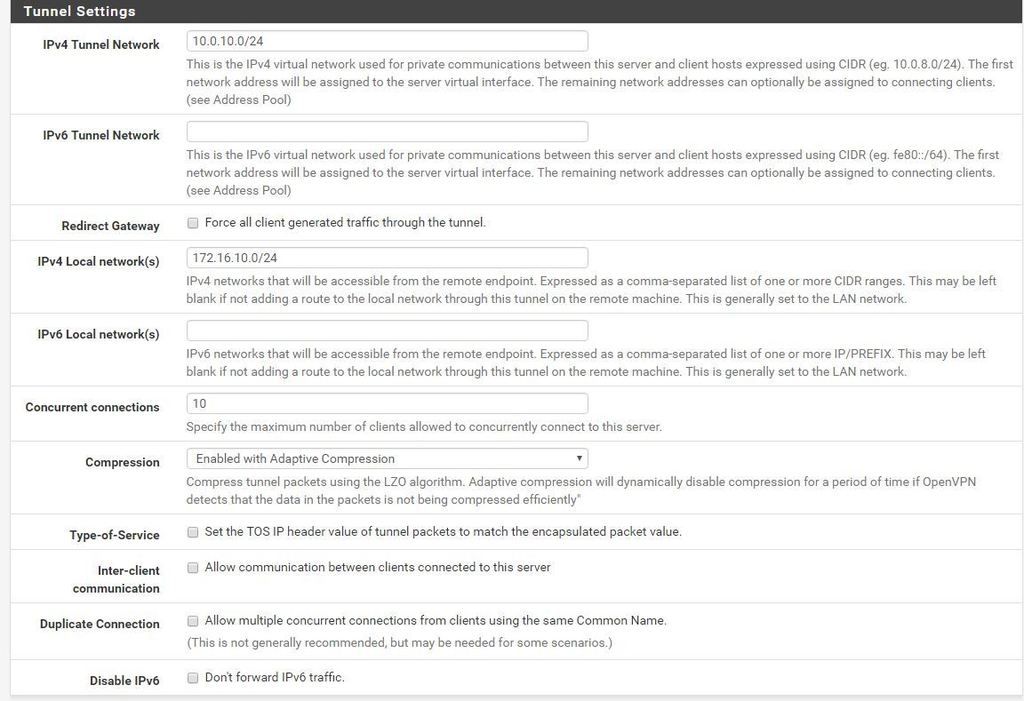
May 8 18:02:25 openvpn 79814 /usr/local/sbin/ovpn-linkdown ovpns1 1500 1558 10.0.10.1 255.255.255.0 init
May 8 18:02:25 openvpn 79814 SIGTERM[hard,] received, process exiting
May 8 18:02:26 openvpn 83741 OpenVPN 2.3.9 amd64-portbld-freebsd10.3 [SSL (OpenSSL)] [LZO] [MH] [IPv6] built on Apr 6 2016
May 8 18:02:26 openvpn 83741 library versions: OpenSSL 1.0.1s-freebsd 1 Mar 2016, LZO 2.09
May 8 18:02:26 openvpn 83787 NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
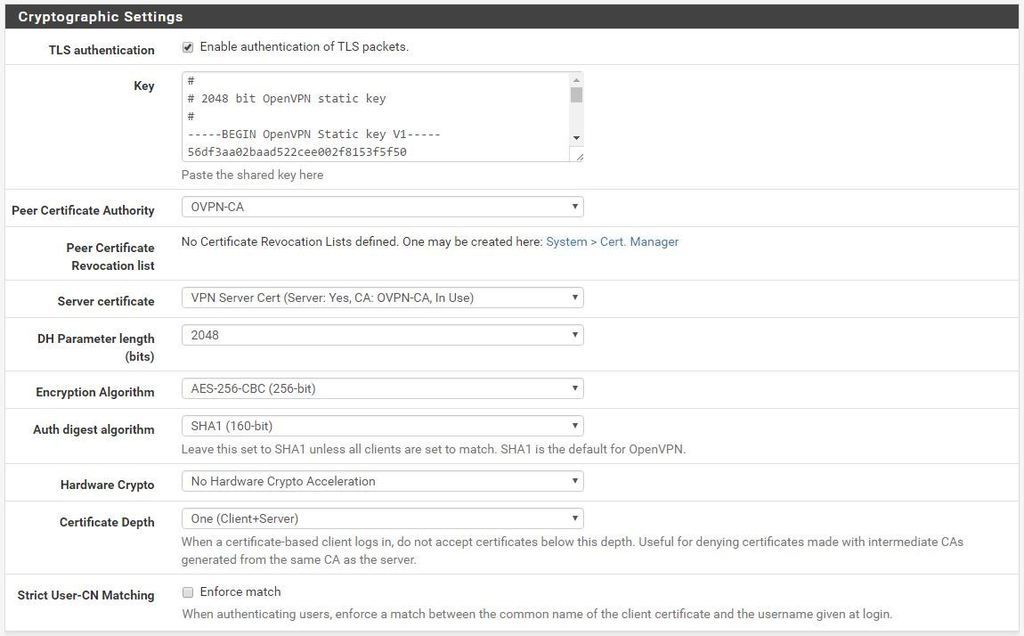
May 8 18:02:26 openvpn 83787 Control Channel Authentication: using '/var/etc/openvpn/server1.tls-auth' as a OpenVPN static key file
May 8 18:02:26 openvpn 83787 TUN/TAP device ovpns1 exists previously, keep at program end
May 8 18:02:26 openvpn 83787 TUN/TAP device /dev/tun1 opened
May 8 18:02:26 openvpn 83787 do_ifconfig, tt->ipv6=1, tt->did_ifconfig_ipv6_setup=0
May 8 18:02:26 openvpn 83787 /sbin/ifconfig ovpns1 10.0.10.1 10.0.10.2 mtu 1500 netmask 255.255.255.0 up
May 8 18:02:26 openvpn 83787 /usr/local/sbin/ovpn-linkup ovpns1 1500 1558 10.0.10.1 255.255.255.0 init
May 8 18:02:26 openvpn 83787 UDPv4 link local (bound): [AF_INET]MY IP REMOVED FOR SECURITY:1194
May 8 18:02:26 openvpn 83787 UDPv4 link remote: [undef]
May 8 18:02:26 openvpn 83787 Initialization Sequence CompletedWindows client log
Sun May 08 18:43:25 2016 OpenVPN 2.3.10 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [PKCS11] [IPv6] built on May 4 2016
Sun May 08 18:43:25 2016 Windows version 6.1 (Windows 7)
Sun May 08 18:43:25 2016 library versions: OpenSSL 1.0.1t 3 May 2016, LZO 2.09
Sun May 08 18:43:36 2016 Control Channel Authentication: using 'firebox-udp-1194-vpnuser-tls.key' as a OpenVPN static key file
Sun May 08 18:43:36 2016 UDPv4 link local (bound): [undef]
Sun May 08 18:43:36 2016 UDPv4 link remote: [AF_INET]IP REMOVED:1194
Sun May 08 18:44:36 2016 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Sun May 08 18:44:36 2016 TLS Error: TLS handshake failed
Sun May 08 18:44:36 2016 SIGUSR1[soft,tls-error] received, process restarting
Sun May 08 18:44:38 2016 UDPv4 link local (bound): [undef]
Sun May 08 18:44:38 2016 UDPv4 link remote: [AF_INET]IP REMOVED:1194
Sun May 08 18:45:38 2016 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Sun May 08 18:45:38 2016 TLS Error: TLS handshake failed
Sun May 08 18:45:38 2016 SIGUSR1[soft,tls-error] received, process restarting
Sun May 08 18:45:40 2016 UDPv4 link local (bound): [undef]
Sun May 08 18:45:40 2016 UDPv4 link remote: [AF_INET]IP REMOVED:1194Ubuntu client log.
Sun May 8 19:54:25 2016 us=999302 pull = ENABLED
Sun May 8 19:54:25 2016 us=999307 auth_user_pass_file = 'stdin'
Sun May 8 19:54:25 2016 us=999314 OpenVPN 2.3.2 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [eurephia] [MH] [IPv6] built on Dec 1 2014
Sun May 8 19:54:36 2016 us=863562 WARNING: file 'firebox-udp-1194-vpnuser.p12' is group or others accessible
Sun May 8 19:54:36 2016 us=863664 WARNING: file 'firebox-udp-1194-vpnuser-tls.key' is group or others accessible
Sun May 8 19:54:36 2016 us=863673 Control Channel Authentication: using 'firebox-udp-1194-vpnuser-tls.key' as a OpenVPN static key file
Sun May 8 19:54:36 2016 us=863682 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun May 8 19:54:36 2016 us=863689 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Sun May 8 19:54:36 2016 us=863706 LZO compression initialized
Sun May 8 19:54:36 2016 us=863756 Control Channel MTU parms [ L:1558 D:166 EF:66 EB:0 ET:0 EL:0 ]
Sun May 8 19:54:36 2016 us=863785 Socket Buffers: R=[133120->131072] S=[133120->131072]
Sun May 8 19:54:36 2016 us=863805 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:135 ET:0 EL:0 AF:3/1 ]
Sun May 8 19:54:36 2016 us=863832 Local Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 1,cipher AES-256-CBC,auth SHA1,keysize 256,tls-auth,key-method 2,tls-client'
Sun May 8 19:54:36 2016 us=863853 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 0,cipher AES-256-CBC,auth SHA1,keysize 256,tls-auth,key-method 2,tls-server'
Sun May 8 19:54:36 2016 us=863874 Local Options hash (VER=V4): '9e7066d2'
Sun May 8 19:54:36 2016 us=863886 Expected Remote Options hash (VER=V4): '162b04de'
Sun May 8 19:54:36 2016 us=864139 UDPv4 link local (bound): [undef]
Sun May 8 19:54:36 2016 us=864178 UDPv4 link remote: [AF_INET]IP REMOVED:1194
pid=0 DATA len=0
pid=0 DATA len=0
pid=0 DATA len=0
pid=0 DATA len=0
pid=0 DATA len=0
Sun May 8 19:55:36 2016 us=39768 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Sun May 8 19:55:36 2016 us=39790 TLS Error: TLS handshake failed
Sun May 8 19:55:36 2016 us=39912 TCP/UDP: Closing socket
Sun May 8 19:55:36 2016 us=39932 SIGUSR1[soft,tls-error] received, process restarting
Sun May 8 19:55:36 2016 us=39944 Restart pause, 2 second(s)
Sun May 8 19:55:38 2016 us=40043 Re-using SSL/TLS context
Sun May 8 19:55:38 2016 us=40125 LZO compression initialized
Sun May 8 19:55:38 2016 us=40168 Control Channel MTU parms [ L:1558 D:166 EF:66 EB:0 ET:0 EL:0 ]
Sun May 8 19:55:38 2016 us=40190 Socket Buffers: R=[133120->131072] S=[133120->131072]
Sun May 8 19:55:38 2016 us=40213 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:135 ET:0 EL:0 AF:3/1 ]
Sun May 8 19:55:38 2016 us=40241 Local Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 1,cipher AES-256-CBC,auth SHA1,keysize 256,tls-auth,key-method 2,tls-client'
Sun May 8 19:55:38 2016 us=40247 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 0,cipher AES-256-CBC,auth SHA1,keysize 256,tls-auth,key-method 2,tls-server'
Sun May 8 19:55:38 2016 us=40261 Local Options hash (VER=V4): '9e7066d2'
Sun May 8 19:55:38 2016 us=40271 Expected Remote Options hash (VER=V4): '162b04de'
Sun May 8 19:55:38 2016 us=40279 UDPv4 link local (bound): [undef]
Sun May 8 19:55:38 2016 us=40288 UDPv4 link remote: [AF_INET]IP REMOVED:1194
pid=0 DATA len=0
pid=0 DATA len=0
pid=0 DATA len=0
pid=0 DATA len=0Open VPN Rule set by wizard
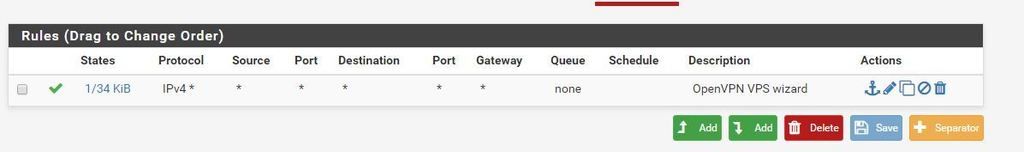
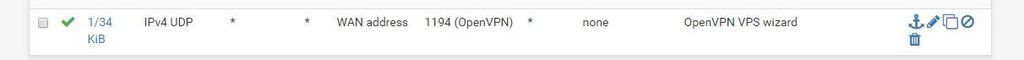
firewall rule set by wizard
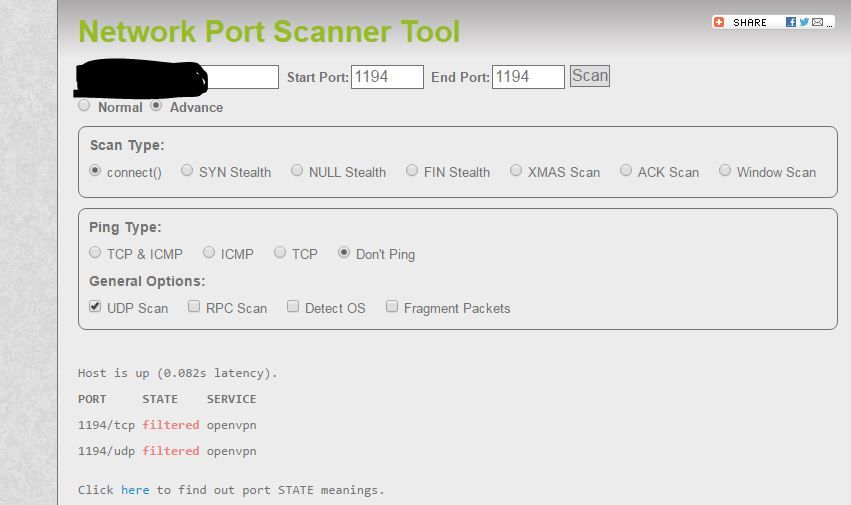
port scan
Interfaces
-
I still cant get it connected. Today I looked at the OpenVPN server log and its full of this. No clients are connecting. is there anyway to uninstall openvpn and reinstall with a fresh copy? I didn't see it listed under installed software packages. Other then that I think I might need to reinstall a fresh copy of pfSense. Maybe something got jacked up when it upgraded to 2.3.
May 9 15:53:24 openvpn 61294 MANAGEMENT: Client connected from /var/etc/openvpn/server1.sock
May 9 15:53:24 openvpn 61294 MANAGEMENT: CMD 'status 2'
May 9 15:53:25 openvpn 61294 MANAGEMENT: CMD 'quit'
May 9 15:53:25 openvpn 61294 MANAGEMENT: Client disconnected
May 9 15:54:26 openvpn 61294 MANAGEMENT: Client connected from /var/etc/openvpn/server1.sock
May 9 15:54:26 openvpn 61294 MANAGEMENT: CMD 'status 2'
May 9 15:54:26 openvpn 61294 MANAGEMENT: CMD 'quit'
May 9 15:54:26 openvpn 61294 MANAGEMENT: Client disconnected
May 9 15:55:27 openvpn 61294 MANAGEMENT: Client connected from /var/etc/openvpn/server1.sock
May 9 15:55:28 openvpn 61294 MANAGEMENT: CMD 'status 2'
May 9 15:55:28 openvpn 61294 MANAGEMENT: CMD 'quit'
May 9 15:55:28 openvpn 61294 MANAGEMENT: Client disconnected
May 9 15:56:29 openvpn 61294 MANAGEMENT: Client connected from /var/etc/openvpn/server1.sock
May 9 15:56:29 openvpn 61294 MANAGEMENT: CMD 'status 2'
May 9 15:56:30 openvpn 61294 MANAGEMENT: CMD 'quit'
May 9 15:56:30 openvpn 61294 MANAGEMENT: Client disconnected
May 9 15:57:31 openvpn 61294 MANAGEMENT: Client connected from /var/etc/openvpn/server1.sock
May 9 15:57:31 openvpn 61294 MANAGEMENT: CMD 'status 2'
May 9 15:57:31 openvpn 61294 MANAGEMENT: CMD 'quit'
May 9 15:57:31 openvpn 61294 MANAGEMENT: Client disconnected
May 9 15:58:32 openvpn 61294 MANAGEMENT: Client connected from /var/etc/openvpn/server1.sock
May 9 15:58:33 openvpn 61294 MANAGEMENT: CMD 'status 2'
May 9 15:58:33 openvpn 61294 MANAGEMENT: CMD 'quit'
May 9 15:58:33 openvpn 61294 MANAGEMENT: Client disconnected -
So your saying this was working before, then you upgraded and not working?
Looks to me here your not even connecting… You sure 1194 is open from where your testing from?
"TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)"
-
I never set it up before I upgraded. I just called and had the gateway re previsioned. New one on the way. Just reinstalled pfsense fresh 2.3 install and restored backup. Fixing to set this up again and see if any of that helped anything.
-
So your saying this was working before, then you upgraded and not working?
Looks to me here your not even connecting… You sure 1194 is open from where your testing from?
"TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)"
Iv tried connecting from my unbuntu client on my VPS and on a windows computer using 4GLTE. Both was giving that same error. Iv tried 1194 on UDP and TCP and i have tried 34447 iv tried 1326 both UPD and TCP. No go same result. I used the rules the wizard auto added. Do I need to add any others?? No NAT because OpenVPN should be listening on the WAN interface.
-
well yes openvpn adds rules on your wan but is pfsense actually got a public? If its behind a nat then traffic would never get to it. What is pfsense wan IP? Is it pubic?
Are there any rules above the openvpn rules that could be blocking?
This really click click and running. Does openvpn show something trying to connect? Doesn't look like it - scans for udp are going difficult to get a good answer from.. Try it on tcp.. then do a scan from outside.. Does it show open?
If I had to guess I would say your pfsense is behind a nat, and never seeing the traffic because your not forwarding on the nat device in front of pfsense to pfsense wan IP for the ports your trying to use for openvpn.
-
well yes openvpn adds rules on your wan but is pfsense actually got a public? If its behind a nat then traffic would never get to it. What is pfsense wan IP? Is it pubic?
Are there any rules above the openvpn rules that could be blocking?
This really click click and running. Does openvpn show something trying to connect? Doesn't look like it - scans for udp are going difficult to get a good answer from.. Try it on tcp.. then do a scan from outside.. Does it show open?
If I had to guess I would say your pfsense is behind a nat, and never seeing the traffic because your not forwarding on the nat device in front of pfsense to pfsense wan IP for the ports your trying to use for openvpn.
Its got a combo gateway in front of it in bridge mode. Some other guys and myself have been figuring its somehow still NATing in bridge mode. I have a new modem on the way that is just a plain jane dumb modem. I'm going to hook that up when it arrives and give it a shot. The funny thing is I opened ports for SMTP and minecraft servers and even open NAT for XBOX One and PS4 on pfSense. They work just fine. Open to the breeze. Only thing I can figure is that combo gateway is doing some kinda trickery to my WAN traffic. I checked with my ISP and some network guys on some other forums and they both confirmed ports are not blocked on the ISP side. So at this point its all pointing to that POS combo gateway.
-
Where this:
OpenVPN server log
May 8 18:02:25 openvpn 79814 event_wait : Interrupted system call (code=4)
May 8 18:02:25 openvpn 79814 /usr/local/sbin/ovpn-linkdown ovpns1 1500 1558 10.0.10.1 255.255.255.0 init
May 8 18:02:25 openvpn 79814 SIGTERM[hard,] received, process exiting
May 8 18:02:26 openvpn 83741 OpenVPN 2.3.9 amd64-portbld-freebsd10.3 [SSL (OpenSSL)] [LZO] [MH] [IPv6] built on Apr 6 2016
May 8 18:02:26 openvpn 83741 library versions: OpenSSL 1.0.1s-freebsd 1 Mar 2016, LZO 2.09
May 8 18:02:26 openvpn 83787 NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
May 8 18:02:26 openvpn 83787 Control Channel Authentication: using '/var/etc/openvpn/server1.tls-auth' as a OpenVPN static key file
May 8 18:02:26 openvpn 83787 TUN/TAP device ovpns1 exists previously, keep at program end
May 8 18:02:26 openvpn 83787 TUN/TAP device /dev/tun1 opened
May 8 18:02:26 openvpn 83787 do_ifconfig, tt->ipv6=1, tt->did_ifconfig_ipv6_setup=0
May 8 18:02:26 openvpn 83787 /sbin/ifconfig ovpns1 10.0.10.1 10.0.10.2 mtu 1500 netmask 255.255.255.0 up
May 8 18:02:26 openvpn 83787 /usr/local/sbin/ovpn-linkup ovpns1 1500 1558 10.0.10.1 255.255.255.0 init
May 8 18:02:26 openvpn 83787 UDPv4 link local (bound): [AF_INET]MY IP REMOVED FOR SECURITY:1194
May 8 18:02:26 openvpn 83787 UDPv4 link remote: [undef]
May 8 18:02:26 openvpn 83787 Initialization Sequence Completedis all you're getting in the logs, no clients are reaching the server to attempt to connect. Assuming you have the wizard-created firewall rule on WAN for UDP 1194, then yeah it sounds like your modem's dropping it. Maybe it's only set to forward all TCP and not UDP.
You can double check by doing a packet capture on WAN, port 1194, rest at defaults. Start. Try to connect from a host on the Internet. Stop the capture. Nothing there? Not reaching you. If you do see UDP 1194 traffic there, then the problem is something else, usually missing WAN rule to allow the traffic to reach the server in that case.
-
well if you say your other port forwards are working.. Then yeah do cmb suggest and sniff.. Do you see the traffic??
-
I found the issue. I had some rules that imported from the upgrade to 2.3. They were all incoming rules. 1194 was at the top of the rule stack, but for some reason the other rules had the firewall jacked up. I deleted all the rules and nat rules. Basically cleared everything out. Cut pure NAT on and re added all the rules to NAT and the firewall and the VPN connected. I did all this after sniffing the WAN traffic that cmb suggested and seen it hitting the firewall. I can ping the server side subnet from the client. All is well now.
Thanks for the input guys. This has been a real headache, but a lesson none the less. I could prolly instruct my grandmaw on how to setup openvpn now.. over the phone and just waking up with a hang over. :)