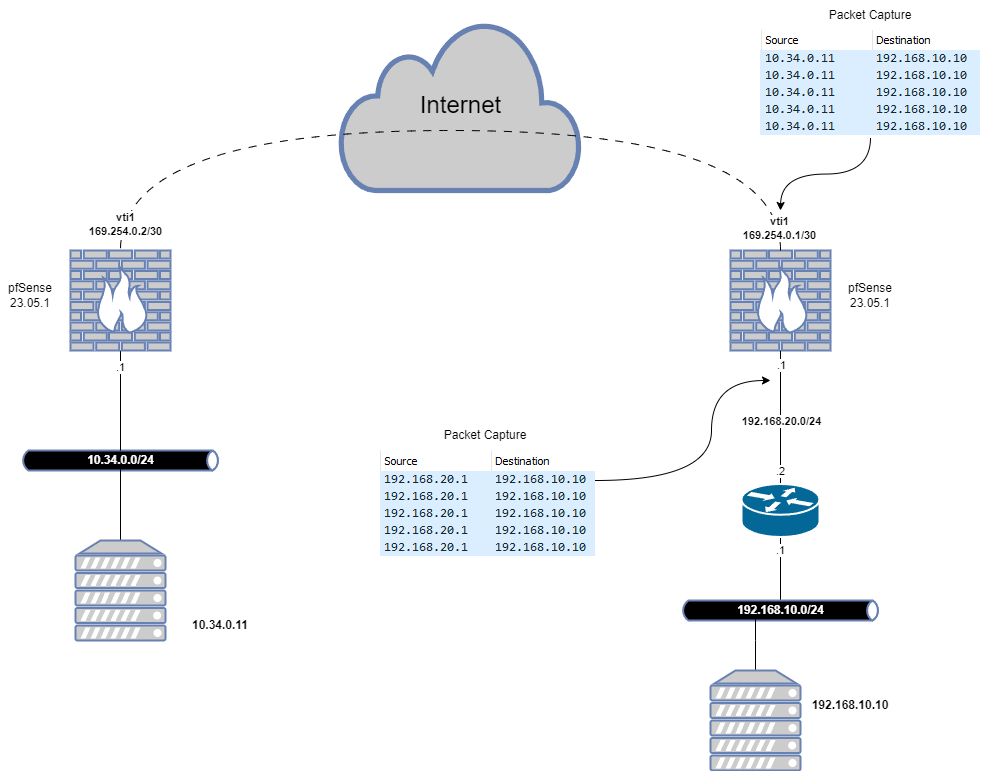
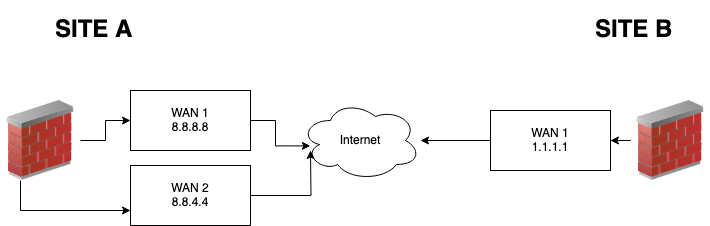
-
0 Votes1 Posts281 Views
-
IPSEC IKEv2 NO_PROP error in Ubuntu 22.04.3 using network-manager-strongswan
0 Votes4 Posts2k Views -
0 Votes8 Posts1k Views
-
0 Votes1 Posts279 Views
-
0 Votes2 Posts455 Views
-
0 Votes4 Posts679 Views
-
0 Votes1 Posts275 Views
-
0 Votes3 Posts841 Views
-
0 Votes12 Posts1k Views
-
0 Votes21 Posts3k Views
-
0 Votes1 Posts248 Views
-
0 Votes7 Posts935 Views
-
0 Votes2 Posts452 Views
-
0 Votes1 Posts193 Views
-
0 Votes5 Posts1k Views
-
0 Votes8 Posts1k Views
-
0 Votes1 Posts278 Views
-
0 Votes1 Posts249 Views
-
0 Votes1 Posts293 Views
-
0 Votes1 Posts230 Views
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.