Seems there are several issues here all getting confused.
Identifier issues with "Distinguished Name" (Which is a bug -- see https://redmine.pfsense.org/issues/11442 -- for a quick workaround, apply the patch there or just set your IDs to KeyID in the meantime)
Identifier issues from incorrect use of Key ID in the past (which fell back to automatic guessing at the type, so may not now match a remote not set specifically to Key ID) -- To fix this, set the right ID type and value on both sides to match
Configuration issues where the configuration is failing to load (with errors)
Tunnels loading but not connecting
Other things that haven't yet been identified
Having one thread for all of this is a giant mess that's hard to follow. It's better for the moment if everyone makes their own thread here in the IPsec category and includes as much detail as possible.
If someone else does have a thread for the exact same root issue then you can combine those threads, but this one is far too generic to be useful.
For those of you who say re-creating the tunnel worked, be sure to grab the config.xml and compare before/after as well as /var/etc/ipsec/swanctl.conf -- something must be different if it suddenly started working, and if it's something done by the upgrade process then we can identify and fix it.
For troubleshooting, first apply patches to fix known issues which have already been resolved:
ead6515637a34ce6e170e2d2b0802e4fa1e63a00 #11435
57beb9ad8ca11703778fc483c7cba0f6770657ac #11435
10eb04259fd139c62e08df8de877b71fdd0eedc8 #11442
ded7970ba57a99767e08243103e55d8a58edfc35 #11486
afffe759c4fd19fe6b8311196f4b6d5e288ea4fb #11487
2fe5cc52bd881ed26723a81e0eed848fd505fba6 #11488
After that, edit/save/apply an IPsec tunnel, then stop and start (not restart) the IPsec daemon, or reboot instead.
If problems persist, do the following:
Edit/save a tunnel
Apply changes
Go to Status > Services and stop, then start the IPsec service (don't click restart)
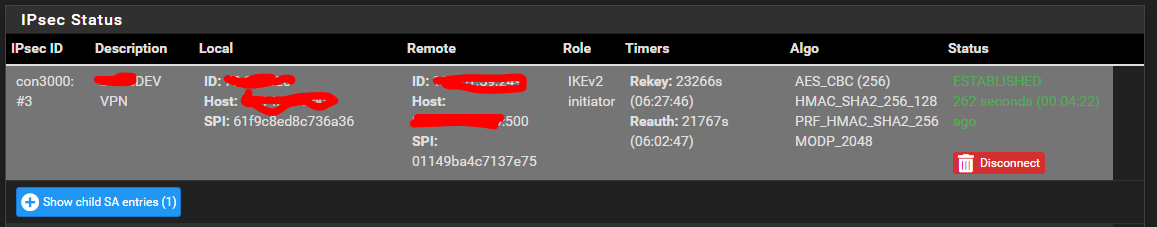
Go to Status > IPsec on one end and attempt to initiate the tunnel if it doesn't come up automatically.
If it works, great. If not:
Run swanctl --list-conns to see what the IPsec daemon loaded for the connections
Run swanctl --load-all --file /var/etc/ipsec/swanctl.conf --debug 1 and see if it reports any problems
Get the config from /var/etc/ipsec/swanctl.conf
Get the most recent logs from both sides
With that in hand, check for an existing thread which matches the symptoms exactly. If one exists, post there. If there isn't one, create one.
Locking this so it doesn't keep growing and making things more confusing.