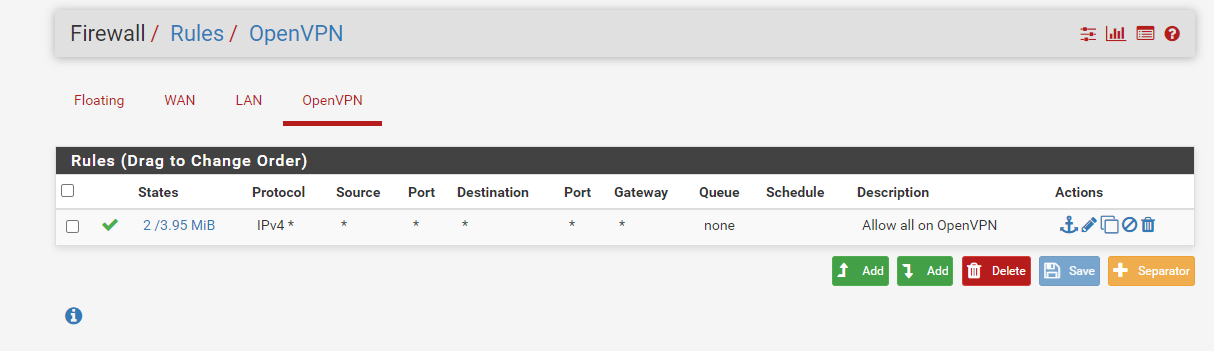
Here is some more information which might help.
My Router is behind my ISP's Router, so I suppose is 'double NATed'?? If that helps.
I have opened The Firewall on the LAN to everything to do with the AirVPN Server address.
This is the config the server is using:
dev ovpnc1
verb 4
dev-type tun
dev-node /dev/tun1
writepid /var/run/openvpn_client1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp4
cipher AES-256-CBC
auth SHA512
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
local 192.168.1.153
engine cryptodev
tls-client
client
lport 0
management /var/etc/openvpn/client1.sock unix
remote xxx.xxx.xxx.xxx 443 udp4
ca /var/etc/openvpn/client1.ca
cert /var/etc/openvpn/client1.cert
key /var/etc/openvpn/client1.key
tls-crypt /var/etc/openvpn/client1.tls-crypt
ncp-ciphers AES-256-GCM:AES-256-CBC
comp-lzo no
resolv-retry infinite
route-noexec
fast-io
explicit-exit-notify 5
sndbuf 262144
rcvbuf 262144
client
persist-key
persist-tun
remote-cert-tls server
prng sha256 64
mlock
auth-nocache
and here is the info from the ovpn file with the keys in:
dev tun
remote xxx.xxx.xxx.xxx 443
resolv-retry infinite
nobind
persist-key
persist-tun
auth-nocache
verb 3
explicit-exit-notify 5
rcvbuf 262144
sndbuf 262144
push-peer-info
setenv UV_IPV6 yes
remote-cert-tls server
cipher AES-256-CBC
comp-lzo no
proto udp
key-direction 1
and the Log Output. The only thing I can spot is this Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key when the Encryption Algorithm is AES-256-CBC (256bit key, 128 bit block)
Also the instructions tell you to use Allowed NCP Encryption Algorithms: AES-256-GCM but the above is using AES-256-CBC, I have tried with both, but no good.
Oct 4 15:34:09 openvpn 41002 MANAGEMENT: Client disconnected
Oct 4 15:34:09 openvpn 41002 MANAGEMENT: CMD 'state 1'
Oct 4 15:34:09 openvpn 41002 MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock
Oct 4 15:34:04 openvpn 41002 UDPv4 link remote: [AF_INET]xxx.xxx.xxx.xxx:443
Oct 4 15:34:04 openvpn 41002 UDPv4 link local (bound): [AF_INET]192.168.1.153:0
Oct 4 15:34:04 openvpn 41002 Socket Buffers: R=[42080->262144] S=[57344->262144]
Oct 4 15:34:04 openvpn 41002 TCP/UDP: Preserving recently used remote address: [AF_INET]185.103.96.130:443
Oct 4 15:34:04 openvpn 41002 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1602,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-256-CBC,auth SHA512,keysize 256,key-method 2,tls-server'
Oct 4 15:34:04 openvpn 41002 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1602,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-256-CBC,auth SHA512,keysize 256,key-method 2,tls-client'
Oct 4 15:34:04 openvpn 41002 Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
Oct 4 15:34:04 openvpn 41002 Control Channel MTU parms [ L:1622 D:1156 EF:94 EB:0 ET:0 EL:3 ]
Oct 4 15:34:04 openvpn 41002 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Oct 4 15:34:04 openvpn 41002 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Oct 4 15:34:04 openvpn 41002 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Oct 4 15:34:04 openvpn 41002 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Oct 4 15:34:04 openvpn 41002 Initializing OpenSSL support for engine 'cryptodev'
Oct 4 15:34:04 openvpn 41002 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Oct 4 15:34:04 openvpn 41002 mlockall call succeeded
Oct 4 15:34:04 openvpn 41002 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client1.sock
Oct 4 15:34:04 openvpn 40744 library versions: OpenSSL 1.0.2u-freebsd 20 Dec 2019, LZO 2.10
Oct 4 15:34:04 openvpn 40744 OpenVPN 2.4.9 armv6-portbld-freebsd11.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 4 2020
Hopefully this additional infomation might jog a memory somewhere.