@jonathan_figueroa said in How serious should I take "invalid chunk size" and "double decoding attack" alerts?:
Hello friend, I am in the same position. I have implemented pfsense in my organization. Snort is giving me the same alerts and blocks with Facebook and Whatsapp. I have disabled those blocks and alerts from the X however hours later it is blocking me again or showing alerts sometimes from the same IP or the IP block corresponding to 157.240.0.0/16.
In my passlist I have put that IP block so that it does not consider it but it keeps giving me the same error.
Did you manage to solve this kind of situations in any way?
Translated with www.DeepL.com/Translator (free version)
When you add addresses to a Pass List you must then do two other things to have the change seen by the running Snort process. First, you must assign the Pass List to the interface by going to the INTERFACE SETTINGS tab, scrolling down to the Pass List drop-down, and selecting the proper list. Then save the change. Second, you must then restart Snort on the interface because the Pass List file is only read and processed once during Snort startup. It is not dynamically processed.
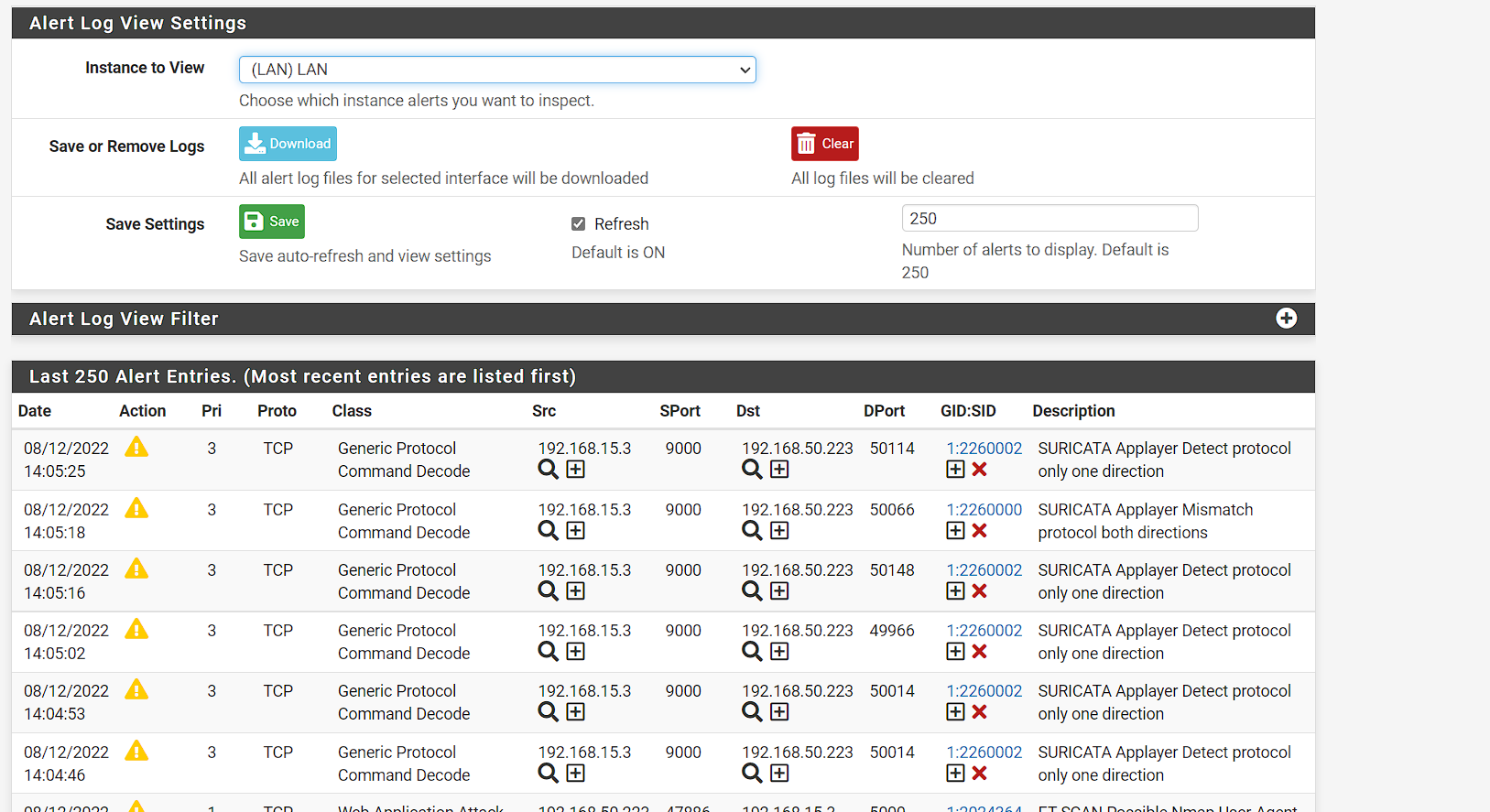
If you disable a rule or suppress an alert using the icons on the ALERTS tab, those changes are dynamic. When you click the icon, Snort is sent a SIGHUP signal that causes it to reload the rules and the assigned suppression list.
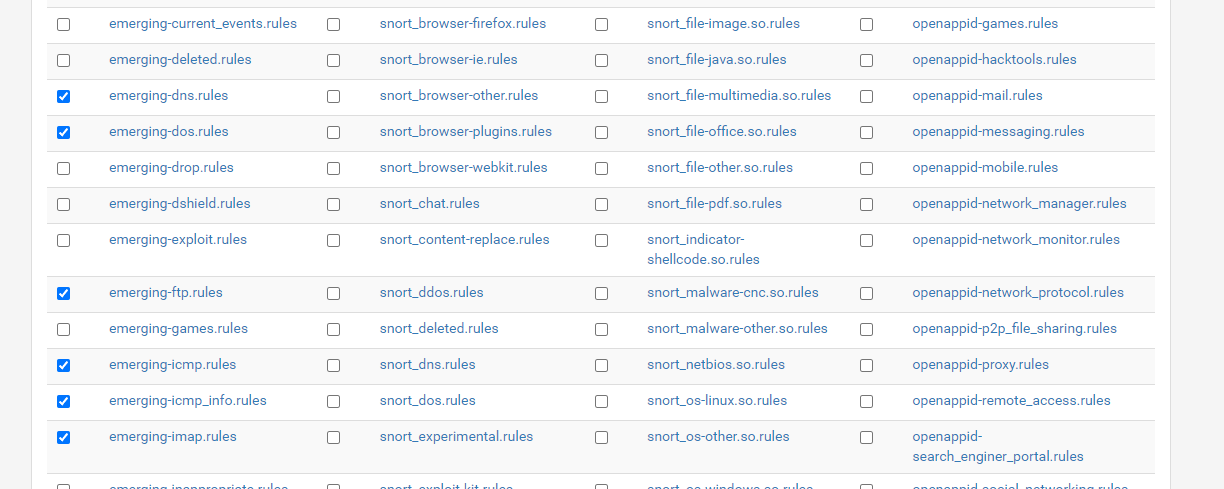
I strongly recommend disabling ALL the HTTP_INSPECT rules as they result in a lot of false positive triggers with modern web traffic. For alerts from other rules, you will need to examine each alerting rule and determine if it represents a false positive or not. That unique skill is what makes one a good IPS/IDS admin. Doing it well requires training and experience.