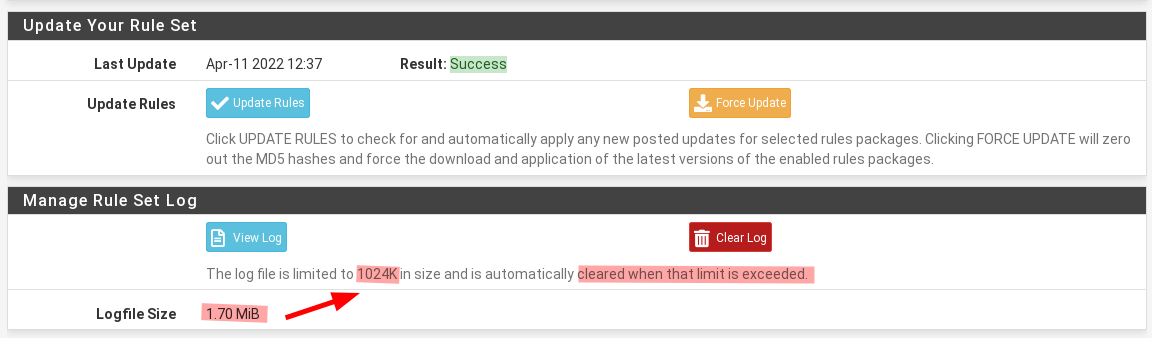
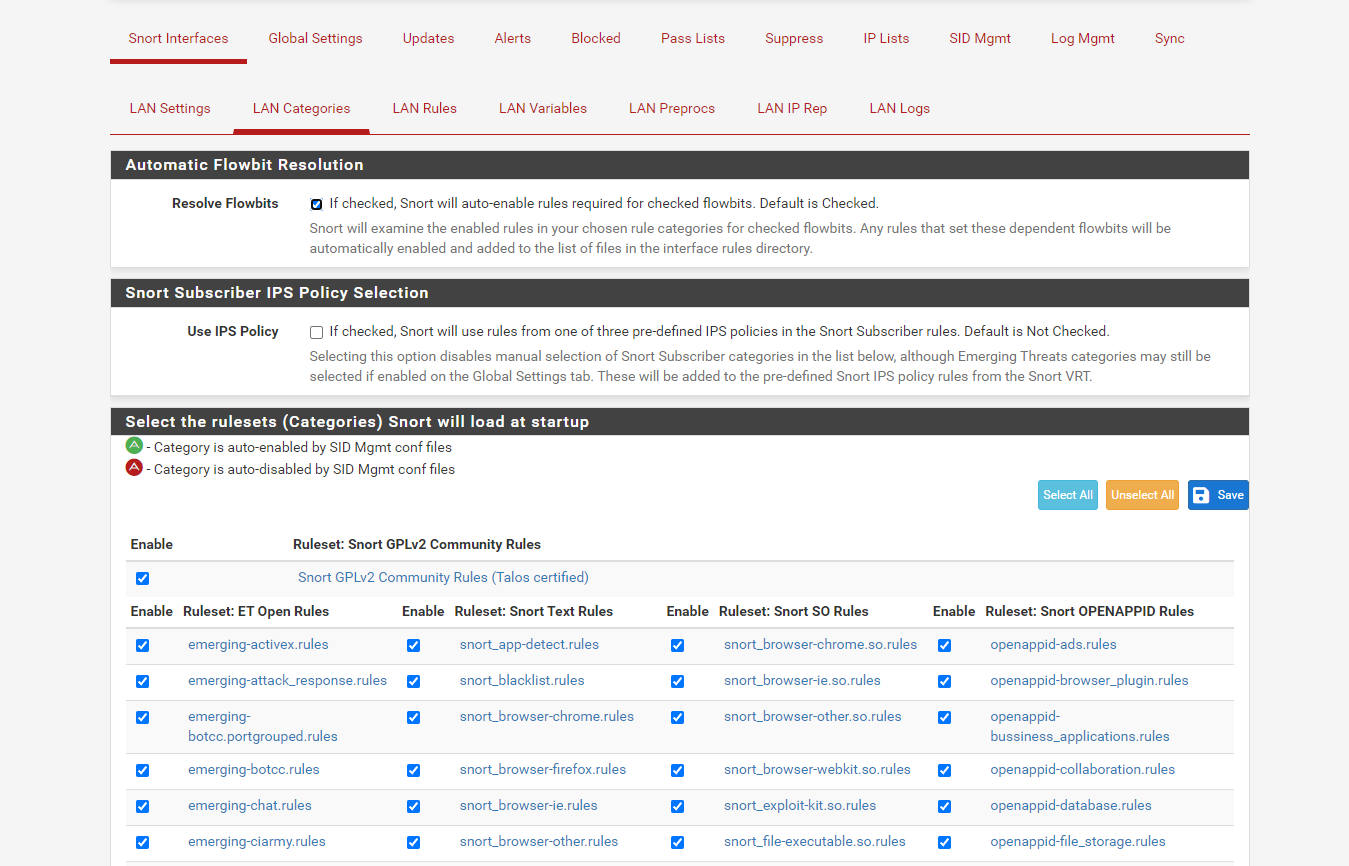
@bmeeks I don't have a proxy set up yet because there's a lot about its configuration that i'm unsure about.
I run suricata in inline mode on the lan interface. I also run unbound with full DoT to cloudflare 1.1.1.2 for dns. i have nat rules and blocks set up so that, unless a client is running a vpn from there device, dns is handled by unbound.
i'm not accessing anything yet from the outside, so.. (still learning this stuff.. babysteps)
My goal is to be able to perform a full-on mitm setup, however i'm still confused with the whole cert thing, wpad, transparent proxy thing.. (the more i read up, the more questions i have).
i thought it was supposed to work as follows: there are basically 2 certs (for simplicity sake i'll refer to the certs as follows):
-A WAN-side cert, so pfsense can de-encrypt/re-encrypt traffic as it receives/sends client data with the outside world,
and
-A LAN-side cert so that it could de-encrypt/re-encrypt traffic as it receives/sends data with the clients on the lan-side for https traffic.
that way, the moment my data hits pfsense on the lan-side, it is decrypted.. pfsense in all it's glory can process all packets to its fullest capability, and then before sending the data out to the internet, re-encrypts it.. and reverse (obviously) when it receives data.
Normally, i'd leave it as is, however as i fill my head with all this 'stuff', i realize that these packages really aren't doing much any more because of the encryption. and since it's just me and my family on my home network, i'd like to be able to use these facets..
also, this stuff is kinda fun! frustrating at times.. but fun..
Also i realize that email is the means of most attack vectors, and it's all basically double-encrypted, such that even with a full-on mitm proxy, email and certain apps can't be de-encrypted, and im fine with that. however regular web traffic i'd like to have scanned and processed. yeah, it's a lot, and those who know would say it's complete overkill and not serving a purpose, however it's all learning to me.. experience that i can take with me where ever i go..
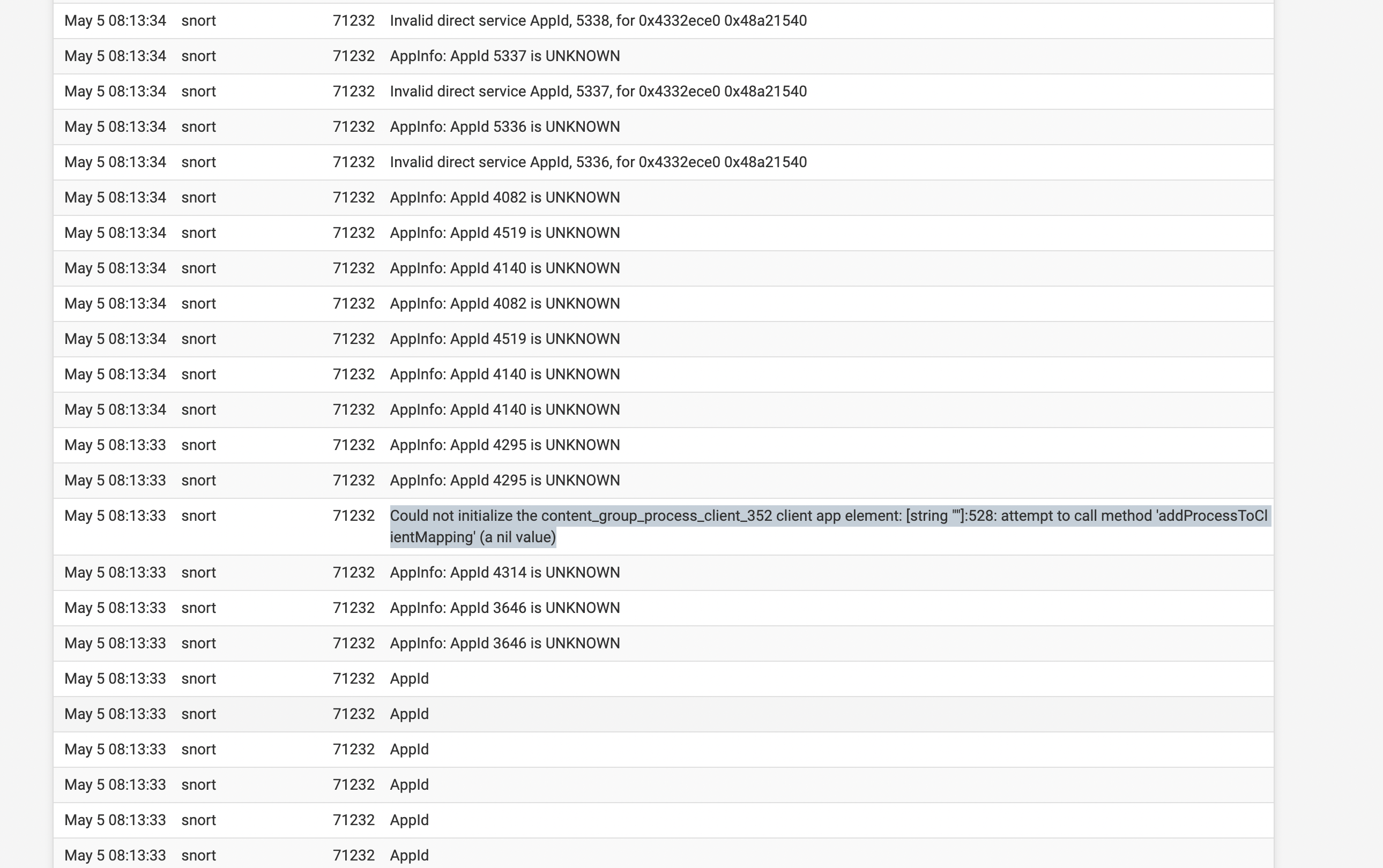 1
0 Votes1 Posts330 Views
1
0 Votes1 Posts330 Views