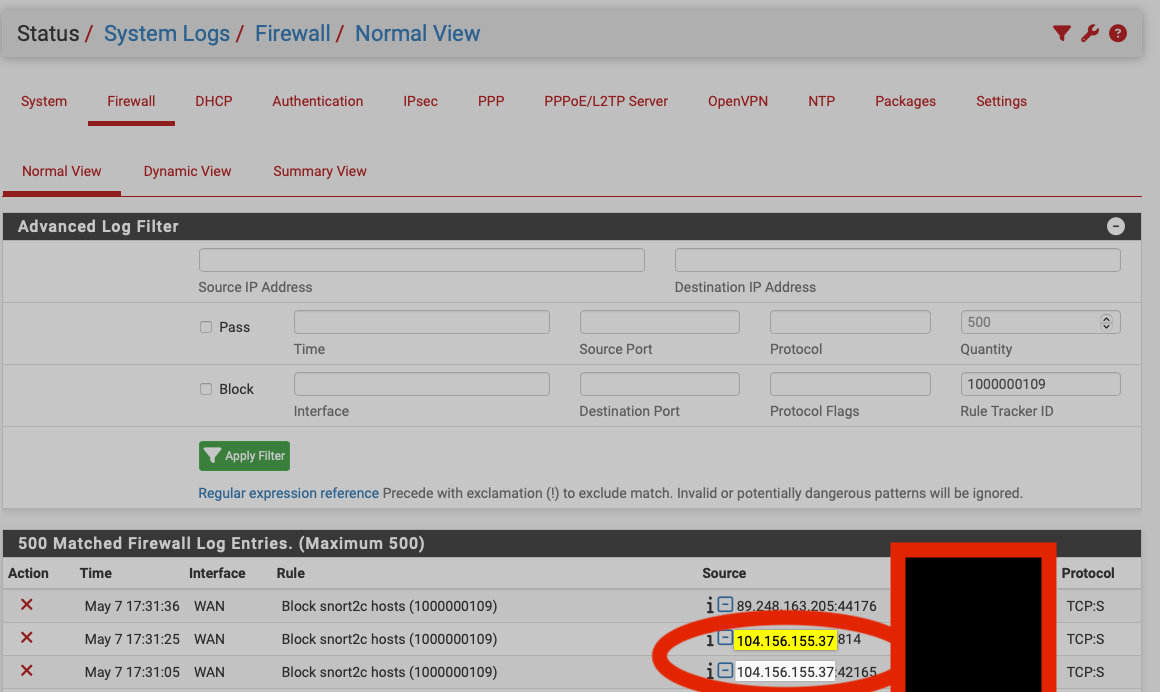
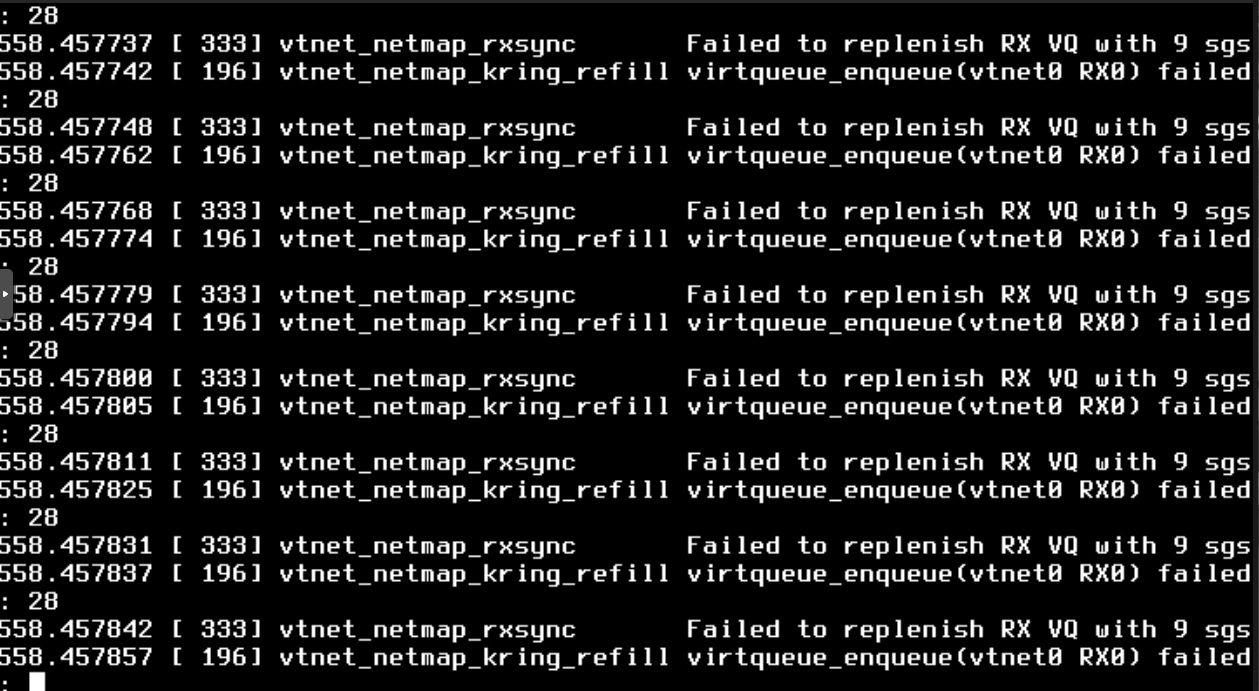
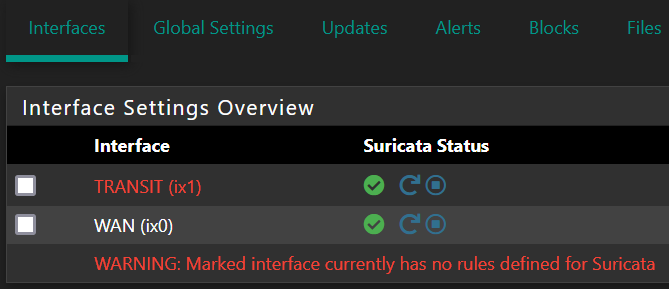
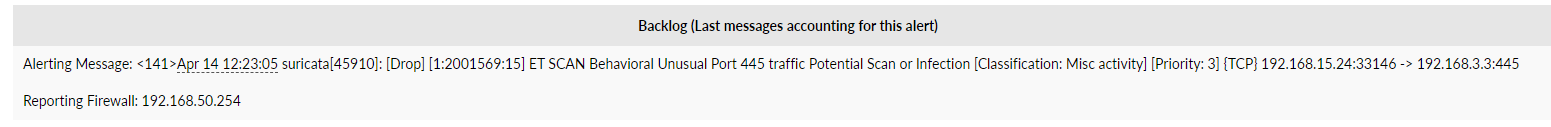
@mcury Obrigado, vou tentar criar apenas para a porta que estou sofrendo mesmo.
Quanto ao DNS, eu realmente tenho um servidor DNS, que responde na porta 53. Quando alguém digita um endereço que esta no meu servidor, é consultado no registroBR que após isso joga para meu servidor certo? Isso nao estabeleceria uma conexão? A pergunta foi meio de curioso haha
Sobre o Synproxy, achei bem interessante, se tiver alguma experiência sobre o uso, lhe agradeço. Vou fazer todos os testes amanhã: Pelo que vi na documentação:
"
Sinproxy
Esta opção faz com que pf faça proxy de conexões TCP de entrada.
As conexões TCP começam com um handshake de três vias. O primeiro pacote de uma conexão TCP é um SYN da origem, que provoca uma resposta SYN ACK do destino e, em seguida, um ACK de retorno da origem para completar o handshake. Normalmente, o host atrás do firewall cuidará disso sozinho, mas o estado synproxy faz com que o firewall conclua esse handshake. Isso ajuda a proteger contra um tipo de ataque de negação de serviço, as inundações SYN. Normalmente, isso só é usado com regras em interfaces WAN.
Atualmente, esse tipo de ataque é melhor tratado no nível do sistema operacional alvo, já que todo sistema operacional moderno inclui recursos para lidar com isso por conta própria. Como o firewall não pode saber quais extensões TCP o host back-end suporta, ao usar o estado synproxy, ele anuncia que não há extensões TCP suportadas. Isso significa que as conexões criadas usando o estado synproxy não usarão dimensionamento de janela, SACK, nem carimbos de data/hora, o que levará a uma redução significativa no desempenho na maioria dos casos.
Esta opção pode ser útil ao abrir portas TCP para hosts que não lidam bem com abusos de rede, onde o desempenho superior não é uma preocupação."