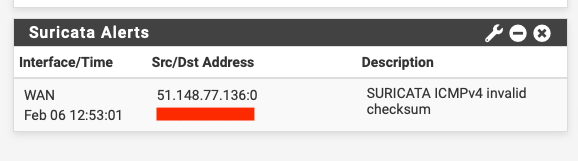
@MaxBishop said in Suricata - bans LAN device -new behavior on new pf install:
@bmeeks
OK, how do I get it.
Here is the link: https://drive.google.com/file/d/1L-rCf8rF-_C93TFISOx4iWPRgW95sFww/view?usp=sharing
This will pull from my Google Drive folder.
Here are the instructions for installing (and then later removing) the test binary.
To begin, download the suricata-7.0.2_7.pkg file from the link above and transfer it to your firewall placing it in the /root directory. IMPORTANT: make sure you transfer the file in binary (unaltered) form! So, if using WinSCP for the transfer from a Windows PC, choose "Binary" for the transfer type.
Stop all running Suricata instances by executing this command from a shell prompt on the firewall:
/usr/local/etc/rc.d/suricata.sh stop
Install the updated version of the Suricata binary using the command below at a shell prompt on the firewall:
pkg-static install -f /root/suricata-7.0.2_7.pkg
That command forcibly updates the binary portion of Suricata with a new package leaving the GUI portion unaltered.
Return to the pfSense GUI and restart Suricata on the interfaces using the icons on the INTERFACES tab.
Report back if there is any change in behavior. I sort of don't really expect a change, but maybe we get lucky. This has proven to be an extraordinarily difficult nut to crack in the past (evidenced by the fact I still have not found a true root cause and thus effective solution). Not being able to reproduce it on my end is what makes finding the bug so hard. I have consulted with the upstream Suricata developers, and they told me the Radix Tree code is thread-safe.
Be sure you leave the passlist-debugging: yes option set in suricata.yaml to give me the maximum level of debugging log messages to work with.
To revert, you will need to first remove the Suricata package, verify the updated binary was also removed, then install the package again from the pfSense menu under SYSTEM > PACKAGE MANAGER.
Remove the package using the SYSTEM > PACKAGE MANAGER menu option.
Next, run this command from a shell prompt:
pkg-static delete suricata-7.0.2_7
That insures the updated test binary is truly removed. If you receive a "not found" or "not installed" error, that simply means the updated binary was removed when the package was removed.
Return to the SYSTEM > PACKAGE MANAGER menu and install Suricata again from the official pfSense repo. This will pull down the current RELEASE package version.