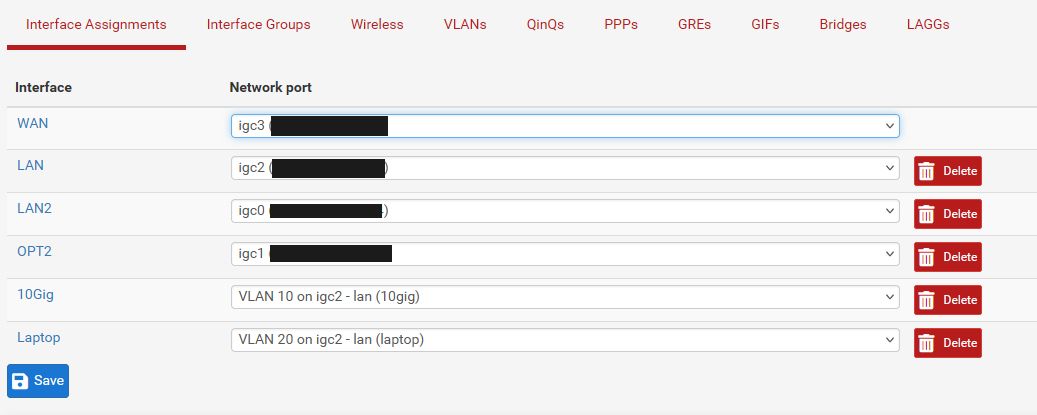
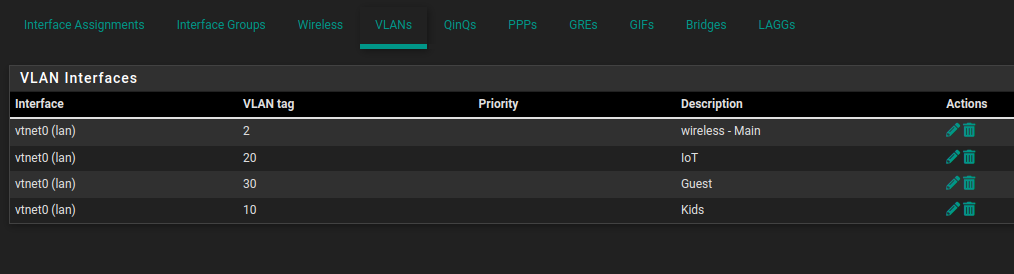
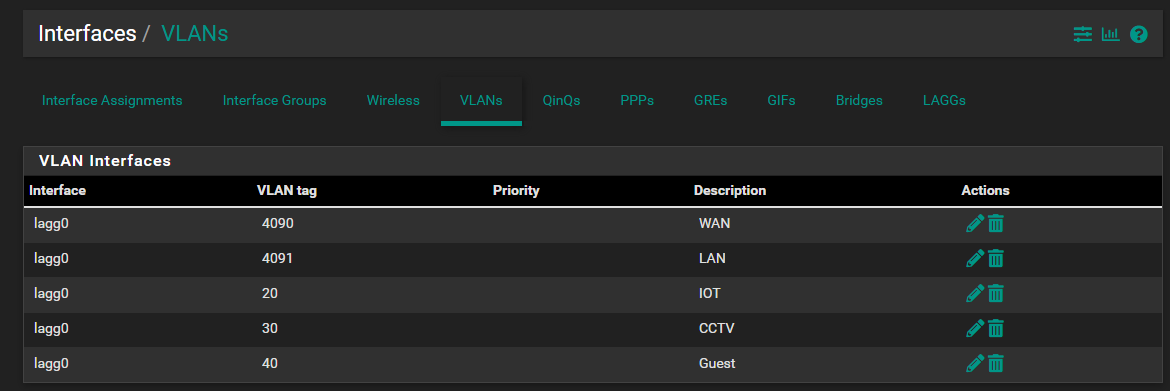
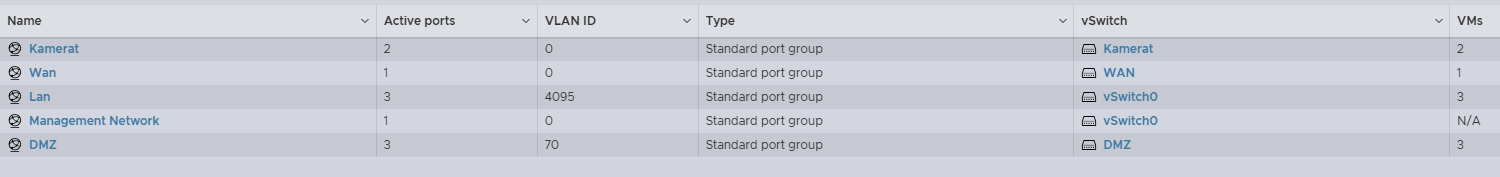
@NGUSER6947
TL DR - Don't use VLANs when a firewall alias is the more appropriate solution.
You don't want to get too granular with your VLANs IMHO. I think most home networks only need 3 VLANs.
1 - a "Secure" VLAN for the router/firewall device itself and other network equipment, as well as all of your personal data. This likely includes most of your personal computers/laptops, network storage devices, etc, but it does NOT include personal mobile devices like phones and tablets. Devices on this VLAN should be able to access any other VLAN.
2 - a "No Internet" VLAN for any device that doesn't need internet access. This might include a lot of the automation devices in your network, CCTV cameras, any network printers, etc etc. Of course the VLAN not having internet doesn't mean you won't be able to access these devices either locally or remotely (over a VPN connection), because you will still be able to do that if setup that way. Devices on this VLAN shouldn't have access to any other VLAN.
3 - an "Everything else" VLAN for........ you guessed it......... everything else (ie your media servers, smart TVs, mobile devices, etc.) Basically anything that needs an internet connection but isn't "secure" enough, or has no reason to be accessing your personal data (which resides on the "Secure" VLAN) needs to go on this VLAN. Not only do your personal mobile devices need to be on this VLAN for security reasons, it's also easier to cast/stream to the media servers when everything is on the same VLAN. Honestly the vast majority of your devices will likely fall onto this VLAN. Devices on this VLAN would have access to the "No Internet" VLAN only.
When you have just a small number of devices that you want to handle differently, this is when you can/should create firewall "aliases" and control groups of devices this way. Most of the time an alias is a better way to manage the devices than a full blown VLAN IMHO. So no, I would not create an "Entertainment VLAN" because that is getting too granular with your VLANs, but I probably would create an "entertainment" firewall alias if I wanted to handle those devices differently when it comes to ad blocking, rules, or other typical firewall activities.
PS - I know a lot of people want to have a "Guest" wireless network/vlan but that isn't actually needed most of the time now that your guests are generally going to have a mobile phone and mobile internet service that works well. Perhaps if your home is located in a cellular "dead spot" this would be helpful to your guests, otherwise it really isn't needed. I know that I initially created a guest network and it was only used perhaps twice over about a 5 year period, so I eventually did away with it. Having a guest network that isn't actually used/needed is nothing but a security risk that should be eliminated.