Get public ip for pcs
-
I bought a pfsense router to get between my isp router and my machines because the operating system of that router is very limited and with little information. My isp router assigns public ips (ipv4) through dhcp to my machines. I wish pfsense could pass these ips to the machines and each machine with a public ip. Is it possible to do that? The machine with pfsense only has 2 rj45 ports. I send the physical link that will be implemented below. Sorry for the translator's English :)
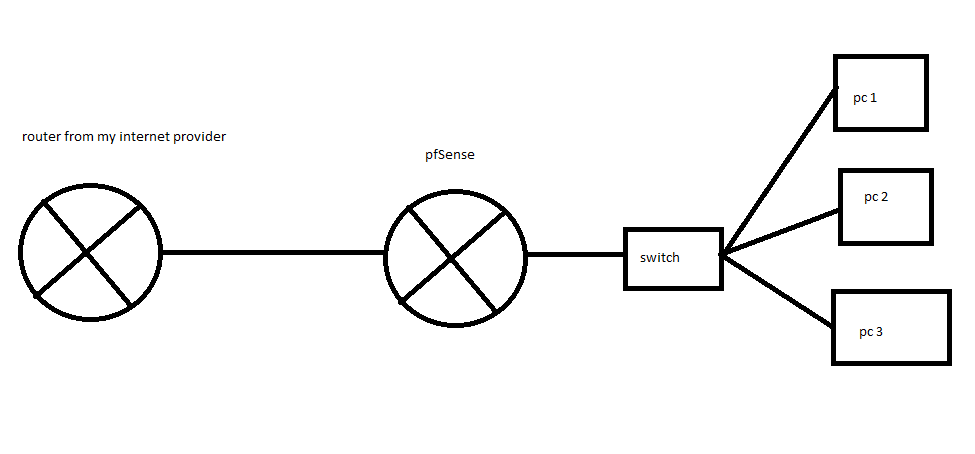
-
You can do that by bridging the ports on pfSense so both interfaces are in the same layer 2 segment.
You may lose some functionality you need by doing that though. What are you using pfSense for in that scenario?Steve
-
@stephenw10 I wanted to use pfsense to detect the source of some ddos attacks. I host game servers.
-
Mmm, Ok you can do that in bridge mode with Snort/Suricata running.
It can be difficult to setup with only two interfaces available as you have no separate management interface. Make sure you have console access as it's very easy top lock yourself out!
https://docs.netgate.com/pfsense/en/latest/bridges/index.html#internal-external-bridges
Steve
-
@stephenw10 Is it possible to bridge only two ports in pfsense?
I have easy access to pfsense console. -
@stephenw10 It is possible to see what IPS my ISP DHCP provided the machines through pfsense.
-
I mean you can 'see' the traffic going to from them and gather the MAC/IP addresses.
pfSense doesn't log that by default though.Steve
-
This post is deleted! -
What I would do here is assign the bridge as an interface and put the management IP on that. Then remove the IP addresses from the interfaces in the bridge.
As I said though it's very easy to lock yourself out when implementing that.Steve
-
@stephenw10 I've already managed to implement. xD I was blocked several times. Hahahaha
-
-
@stephenw10 I'm here with a big problem kkk. The ip addresses do not keep the ports open :( and in the firewall logs nothing appears to block the connection.
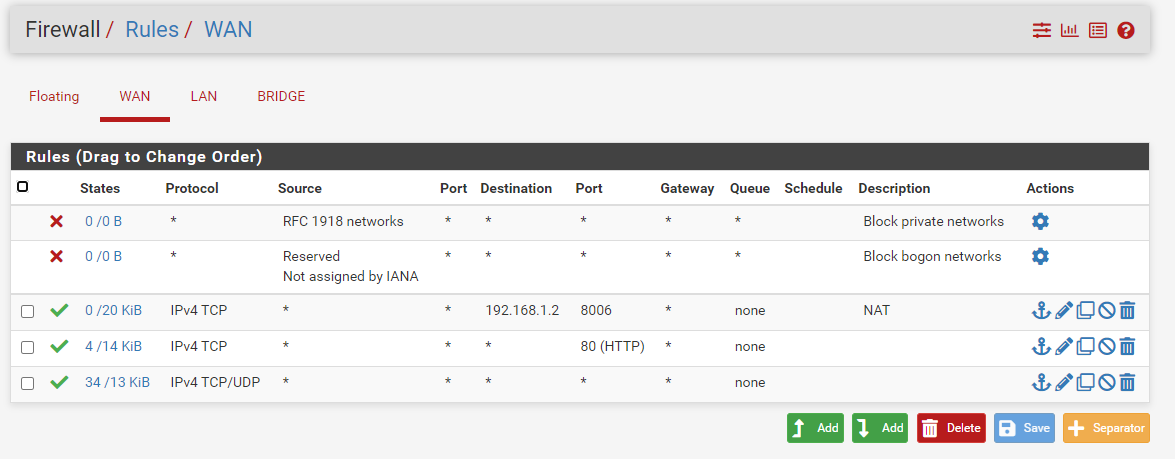
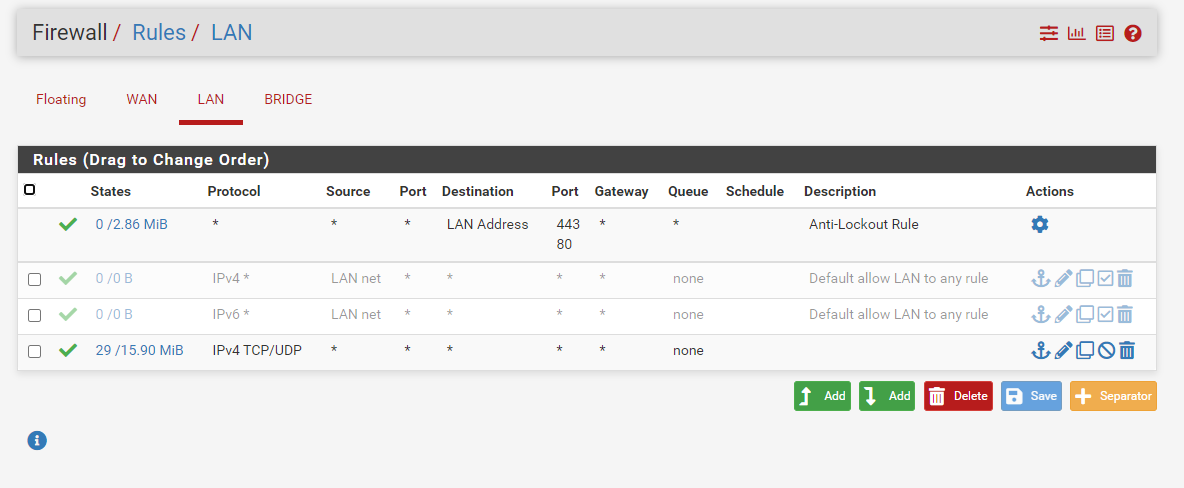
I have an open port 80 on a machine this machine has an apache. I've already tried to get a local ip and do nat routing and it works but with the public ip and with the firewall rules open I can't access it.
-
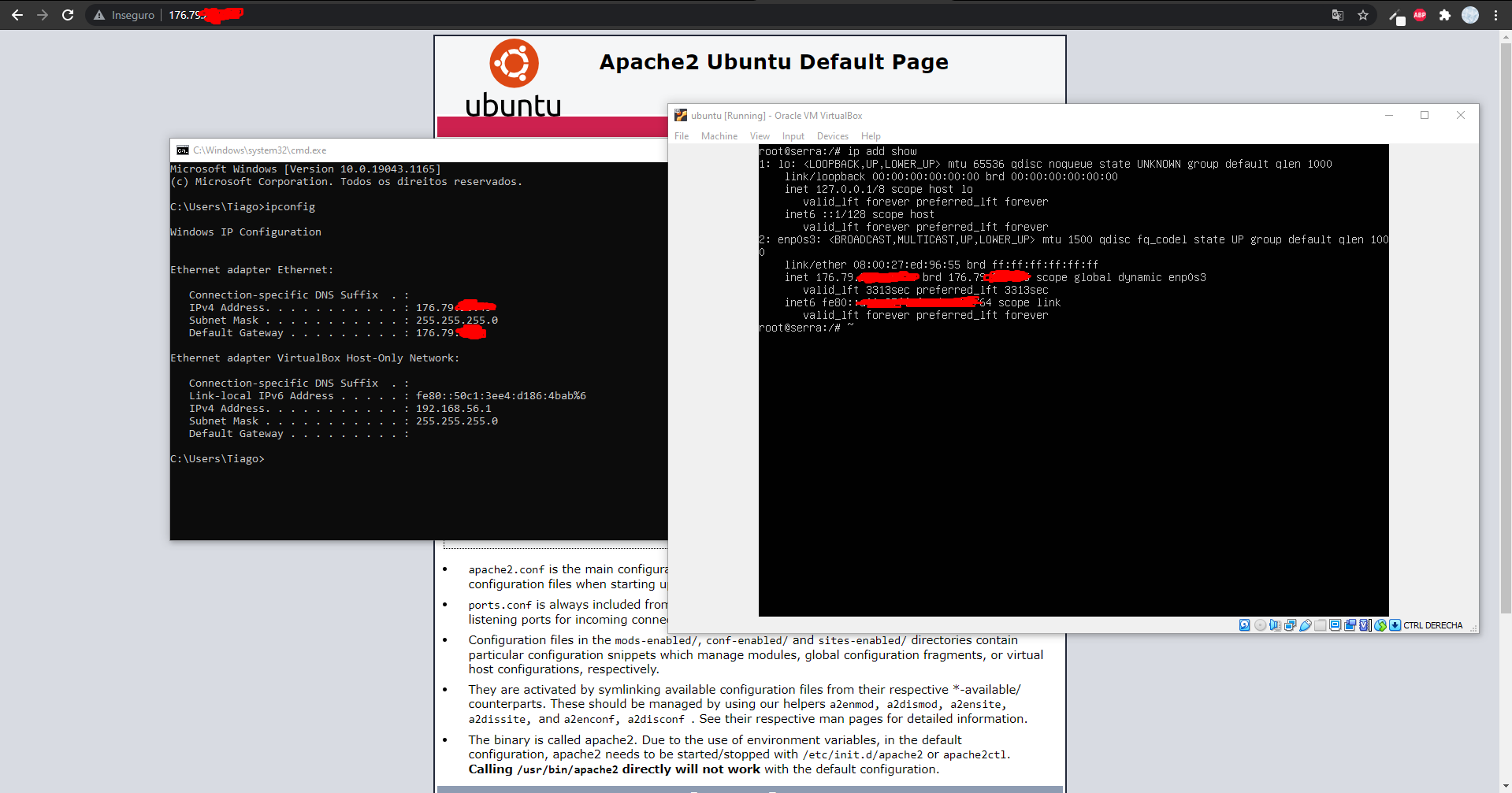
In a virtual machine with public ip it works because the two machines are connected on the same bridge. But if you try to access it from the outside, i can't.
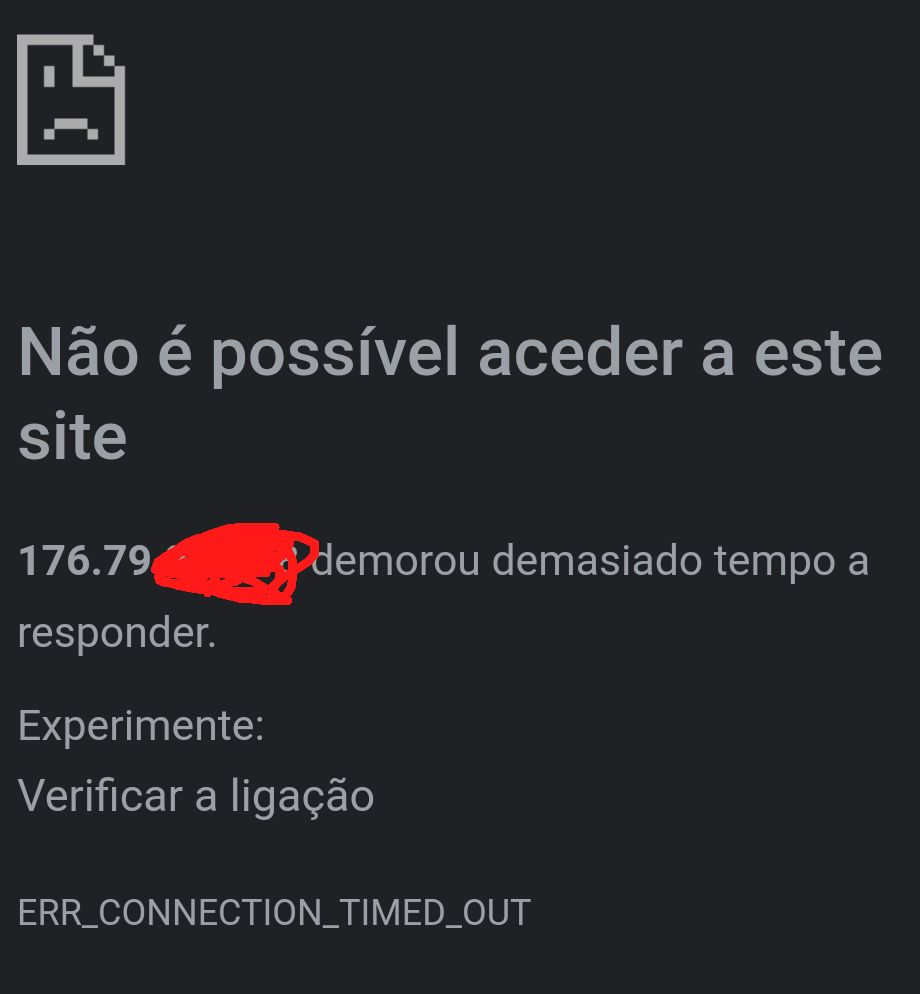
It should probably be something on the pfsense firewall but in the firewall logs nothing is blocked on port 80.
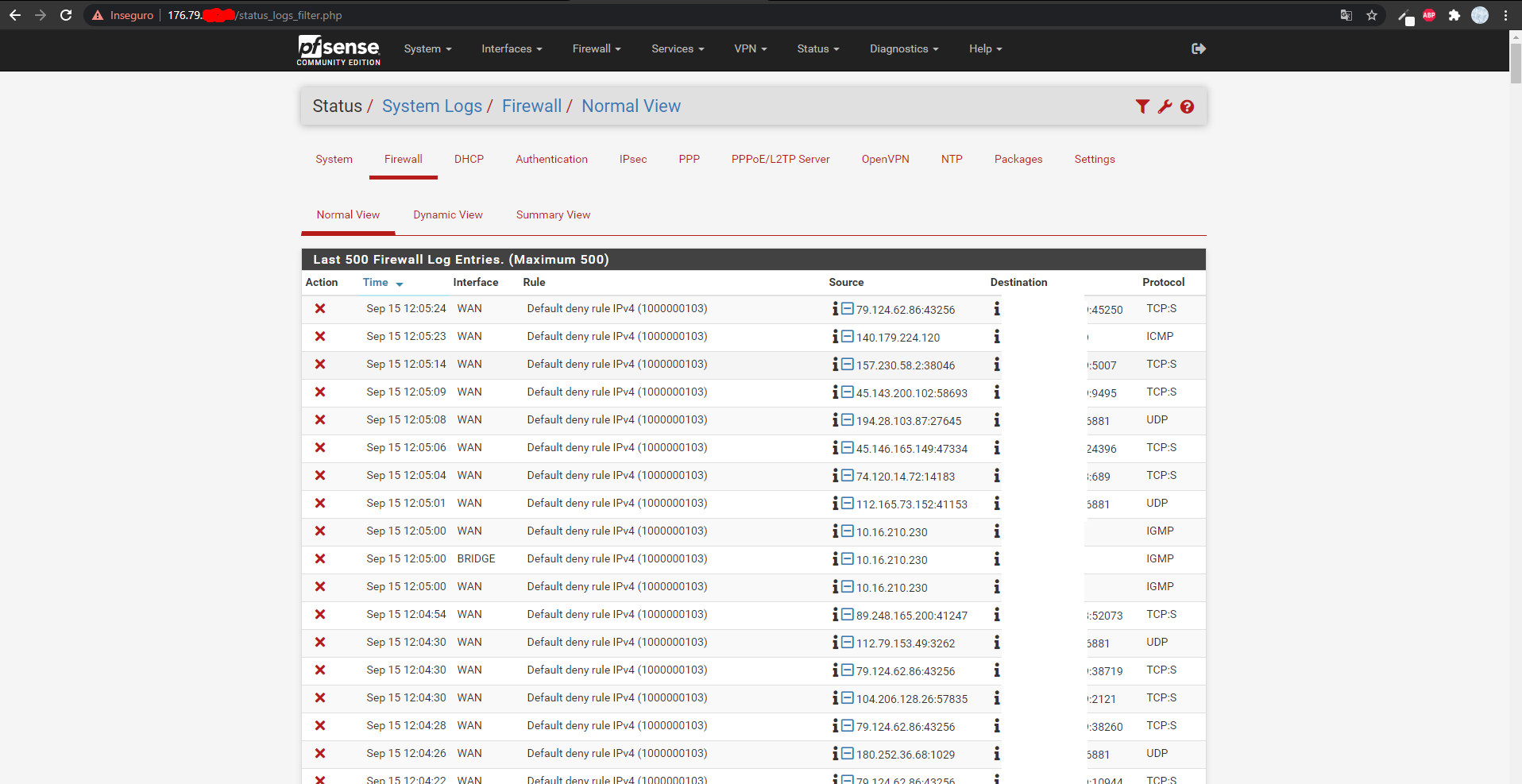
-
How are those servers getting their IP? Statically configured?
If so the ISP is going to be ARPing for those IPs on the WAN and you should see that in a packet capture.
Can the servers connect out?
Steve
-
The servers get the ips through DHCP from my ISP I created a bridge from wan to lan.
pfsense has a public ip public through DHCP and this already works outside the network.The ips that are on the pfsense bridge does not work outside the network, only inside.

-
Ok, if the servers are pulling a DHCP lease correctly then the bridge is working.
Can the servers connect out to public IPs?
Your pass rules are TCP/UDP only so ping will not work.Steve
-
yes the bridge works.
I already added the icmp and the ping works to connect to public servers.
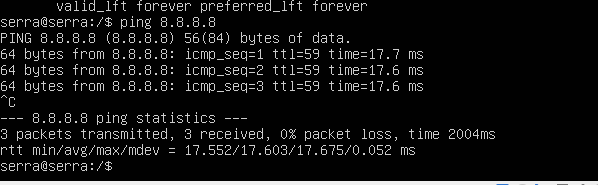
the only problem is that the ports are not open to the outside of these ips on the servers.
but on the firewall they are open and in the logs nothing to block appears. -
Run a packet capture on the WAN for one of the server IPs. Try to connect to it. What do you see?
-
no port
13:32:29.317735 IP 79.124.62.98.8080 > 176.79.22.208.64030: tcp 0
13:32:29.318082 IP 176.79.22.208.64030 > 79.124.62.98.8080: tcp 0
13:32:29.701921 IP 104.211.136.118.42248 > 176.79.22.208.6379: tcp 0
13:32:29.702123 IP 176.79.22.208.6379 > 104.211.136.118.42248: tcp 0
13:32:30.465707 IP 79.124.62.98.8080 > 176.79.22.208.8576: tcp 0
13:32:30.465943 IP 176.79.22.208.8576 > 79.124.62.98.8080: tcp 0
13:32:31.388806 IP 79.124.62.74.8080 > 176.79.22.208.6321: tcp 0
13:32:31.389043 IP 176.79.22.208.6321 > 79.124.62.74.8080: tcp 0
13:32:33.209124 IP 79.124.62.98.8080 > 176.79.22.208.57090: tcp 0
13:32:33.209345 IP 176.79.22.208.57090 > 79.124.62.98.8080: tcp 0
13:32:34.526102 IP 79.124.62.98.8080 > 176.79.22.208.8337: tcp 0
13:32:34.526297 IP 176.79.22.208.8337 > 79.124.62.98.8080: tcp 0
13:32:34.532040 ARP, Request who-has 176.79.22.1 tell 176.79.22.208, length 46
13:32:34.532922 ARP, Reply 176.79.22.1 is-at 00:03:fa:00:00:01, length 46
13:32:36.055518 IP 79.124.62.74.8080 > 176.79.22.208.1340: tcp 0
13:32:36.055728 IP 176.79.22.208.1340 > 79.124.62.74.8080: tcp 0
13:32:37.972712 IP 79.124.62.98.8080 > 176.79.22.208.8009: tcp 0
13:32:37.972919 IP 176.79.22.208.8009 > 79.124.62.98.8080: tcp 0
13:32:40.439980 IP 79.124.62.98.8080 > 176.79.22.208.20049: tcp 0
13:32:40.440203 IP 176.79.22.208.20049 > 79.124.62.98.8080: tcp 0
13:32:43.711008 IP 162.142.125.91.63264 > 176.79.22.208.16061: tcp 0
13:32:43.711217 IP 176.79.22.208.16061 > 162.142.125.91.63264: tcp 0witch port 80
13:34:42.227724 IP 176.79.25.173.53915 > 176.79.22.208.80: tcp 0
13:34:42.227954 IP 176.79.22.208.80 > 176.79.25.173.53915: tcp 0
13:34:42.229700 IP 176.79.25.173.59211 > 176.79.22.208.80: tcp 0
13:34:42.229849 IP 176.79.22.208.80 > 176.79.25.173.59211: tcp 0
13:34:42.540794 IP 176.79.25.173.61377 > 176.79.22.208.80: tcp 0
13:34:42.540998 IP 176.79.22.208.80 > 176.79.25.173.61377: tcp 0
13:34:43.191201 IP 176.79.25.173.59211 > 176.79.22.208.80: tcp 0
13:34:43.191309 IP 176.79.25.173.53915 > 176.79.22.208.80: tcp 0
13:34:43.191405 IP 176.79.22.208.80 > 176.79.25.173.59211: tcp 0
13:34:43.191509 IP 176.79.22.208.80 > 176.79.25.173.53915: tcp 0
13:34:43.447009 IP 176.79.25.173.61377 > 176.79.22.208.80: tcp 0
13:34:43.447285 IP 176.79.22.208.80 > 176.79.25.173.61377: tcp 0
13:34:44.195234 IP 176.79.22.208.80 > 176.79.25.173.53915: tcp 0
13:34:44.195247 IP 176.79.22.208.80 > 176.79.25.173.59211: tcp 0
13:34:44.451104 IP 176.79.22.208.80 > 176.79.25.173.61377: tcp 0
13:34:45.220337 IP 176.79.25.173.59211 > 176.79.22.208.80: tcp 0
13:34:45.220355 IP 176.79.25.173.53915 > 176.79.22.208.80: tcp 0
13:34:45.220578 IP 176.79.22.208.80 > 176.79.25.173.59211: tcp 0
13:34:45.220592 IP 176.79.22.208.80 > 176.79.25.173.53915: tcp 0
13:34:45.463846 IP 176.79.25.173.61377 > 176.79.22.208.80: tcp 0
13:34:45.464016 IP 176.79.22.208.80 > 176.79.25.173.61377: tcp 0
13:34:47.235101 IP 176.79.22.208.80 > 176.79.25.173.53915: tcp 0
13:34:47.235115 IP 176.79.22.208.80 > 176.79.25.173.59211: tcp 0
13:34:47.491289 IP 176.79.22.208.80 > 176.79.25.173.61377: tcp 0
13:34:49.283230 IP 176.79.25.173.59211 > 176.79.22.208.80: tcp 0
13:34:49.283337 IP 176.79.25.173.53915 > 176.79.22.208.80: tcp 0
13:34:49.283432 IP 176.79.22.208.80 > 176.79.25.173.59211: tcp 0
13:34:49.283537 IP 176.79.22.208.80 > 176.79.25.173.53915: tcp 0
13:34:49.527594 IP 176.79.25.173.61377 > 176.79.22.208.80: tcp 0
13:34:49.527794 IP 176.79.22.208.80 > 176.79.25.173.61377: tcp 0 -
Mmm, well it sure looks like two way traffic there.
That's on the pfSense WAN interface?
.208 IP is the server there? What subnet mask does it have?
I assume the .173 IP is not in the same subnet?Steve
