No Internet to LAN Devices
-
So I'm installing a pfSense firewall for the first time and while I have other configurations to compare to, I've had no luck getting this new one to function.
Rough Network "Map":
ISP >pfSense1> switch >pfSense2Devices:
pfSense1is the acting router/firewall for our network. This is where most of the magic happens and it is a fully functional device.pfSense2is the new pfsense device. I'm trying to configure this guy so that it will be 95% plug-and-play when delivered to a new site without an existing hardware firewall.pfSense2 Current Notes/Config:
- NAT is disabled. I don't expect double-NATs to work well...
- WAN is configured for DHCP
- No custom WAN rules. Only the default 2 rules
- No custom LAN rules. Only the default 3 rules
- The internet connects from
pfSense2's configured WAN port, which is our intranet - Can ping the outside WAN and random websites from the diagnostic tool
- I have AD authentication working. It's communicating with
pfSense1's LAN without issue.
All screenshots are from
pfSense2.
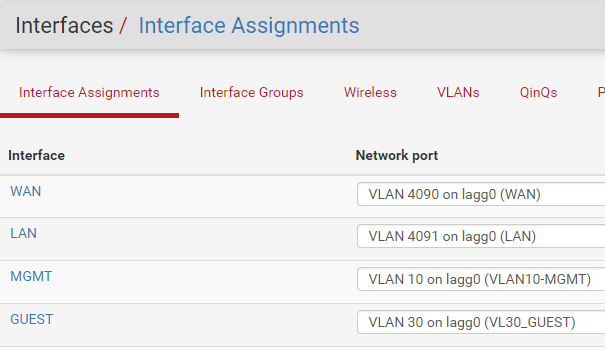
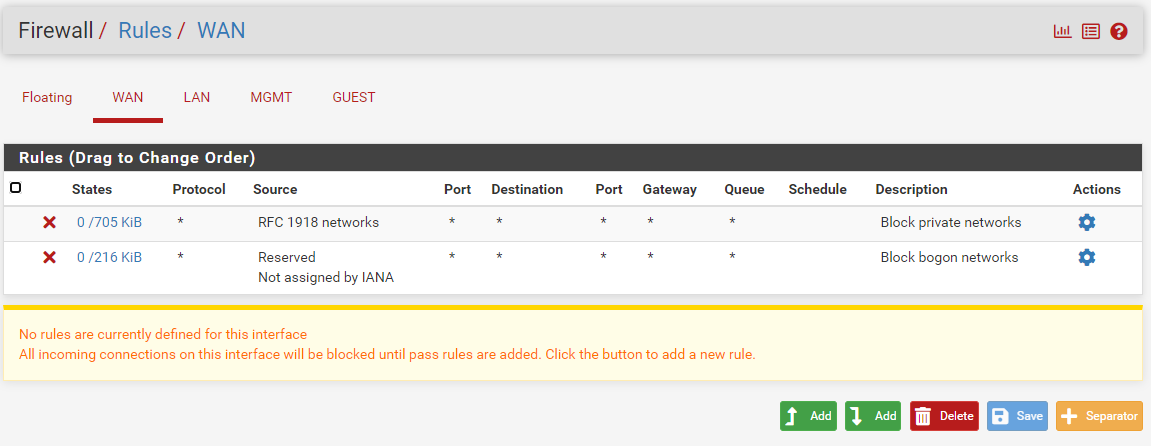
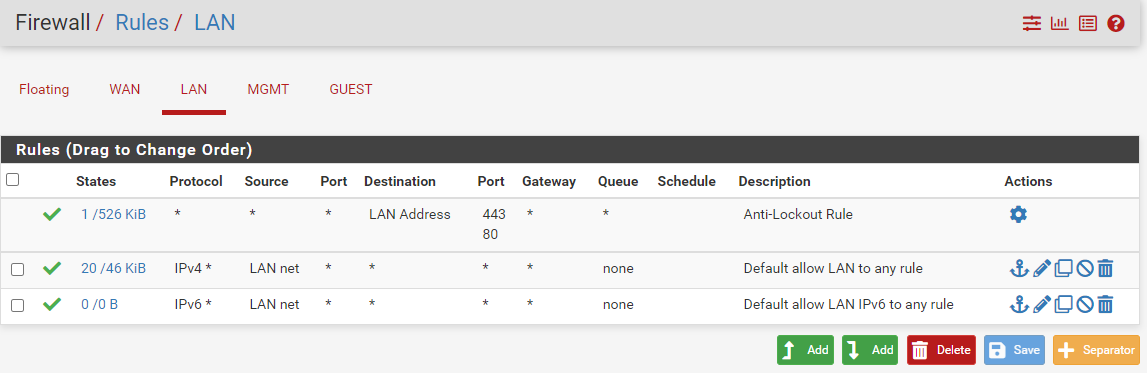
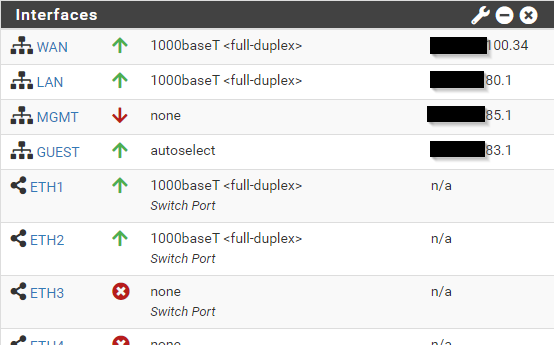
I'm probably missing something stupidly simple, but I truly have no idea what's wrong. Any help is appreciated. Probably need to add a rule to WAN. I don't know at this point. I had thought the firewall knows to let LAN traffic out, and to let responses/connections back in without a WAN rule.
Let me know if you need additional information.
UPDATES:
- Tried to see if disabling "Block Private networks and loopback addresses" and "Block bogon networks" would start letting traffic in, but this also did not fix the issue.
-
Your WAN interface doesn't have any allow rules set in the images above , so defaults to block everything. It also has a block RFC 1918 (private ip ranges) , of which you said that the WAN interface actually connects to a private network.
Try to add some allow rules on both sides... pfsense1 and pfsense2,- since you said you don't have NAT on pfsense2 , add an allow rule on pfsense1 LAN interface to allow traffic from LAN network on pfsense2.
- add an allow rule on pfsense2 WAN to allow outbound from LAN to any or specific dest.
- add NAT on pfsense1 for pfsense2 LAN (not sure this is needed)
- check the gateway configuration and DNS on pfsense2
-
Yeah with NAT disabled you need all that ^ plus you need a static route in pfSense 1 for the pfSense 2 LAN via it's WAN IP.
Just enable NAT again. Almost everything works fine behind double NAT.
If you are planning to send that to some other site it will almost certainly need outbound NAT at that point anyway.
Steve
-
@aduzsardi said in No Internet to LAN Devices:
Your WAN interface doesn't have any allow rules set in the images above , so defaults to block everything. It also has a block RFC 1918 (private ip ranges) , of which you said that the WAN interface actually connects to a private network.
Try to add some allow rules on both sides... pfsense1 and pfsense2,- since you said you don't have NAT on pfsense2 , add an allow rule on pfsense1 LAN interface to allow traffic from LAN network on pfsense2.
- add an allow rule on pfsense2 WAN to allow outbound from LAN to any or specific dest.
- add NAT on pfsense1 for pfsense2 LAN (not sure this is needed)
- check the gateway configuration and DNS on pfsense2
For each of your listed items:
- This is alread done as part of our local subnet alias
- Completed as suggested
- I don't believe this is needed, either, so for now I will skip it. Traffic shouldn't need to be NAT'd here from a downstream device since I have the
pfSense2's subnets added to the allowed traffic - These are all correct as-is
Currently facing the same results. I feel like this should all be working.
-
If you have added a static route on pfSense 1 to the pfSense 2 LAN then outbound rules for it will be added automarically IF OBN is still set to auto.
But you definitely need OBN rules for that subnet.But don't do that. Just enable OBN on pfSense2.
Steve
-
Ok, so I undid the previous changes suggested by @aduzsardi and turned on NAT again, since I truthfully just turned it off without even thinking about it. I've just always had problems with double-NATing and always see people complain about it causing problems.
Nothing changed after this, so I did my "f*** it, let's just reboot and see what happens" dance.
Boom. Working.
There were only two changes that I kept:
- Turning on NAT
- Disabling "Block Private networks and loopback addresses" and "Block bogon networks"
So I did the sensible thing and disabled one item at a time until it broke again.
-
Disabling NAT, then rebooting, did not break it. Turned this back on & rebooted (the FW).
-
Toggling BPNLA and BBN to on and rebooting freaking broke it. Turned these off - still broken - rebooted - boom, working.
So I kinda fixed my own issue without realizing it because it needed to reboot for those itsy-bitsy toggles. Thanks pfSense lol.
aduzsardi & stephenw10 Thanks to you both for your time!
Time for lunch.
-
Hmm, what are you actually testing here?
I thought it was outbound connectivity from the pfSense 2 LAN?
That would require NAT and would be unaffected by those block rule that only apply to inbound traffic. So I assume you were testing something else?Steve
-
I was attempting to get internet passing to a device connected to the LAN on
pfSense2. It just wasn't letting traffic through.This would have probably been a better "map" to present to you:
WAN/ISP >
pfSense1> LAN/intranet > switch >pfSense2 -
Mmm, but you mean connecting out from a client on the pfSense 2 LAN? Like opening an external webpage? Which is what I thought you were doing.
Or connecting to that device from something in the pfSense 1 LAN? Which I would expect to be blocked anyway since there are no WAN rules to allow it.
In the former case you absolutely do need outbound NAT somewhere, but that could be in pfSense 1. And those inbound WAN rules make no difference.
If you have somehow moved the OBN to pfSense 1 it will fail if you send it to another location that isn't configured in the same way.
Steve
-
@stephenw10 said in No Internet to LAN Devices:
Mmm, but you mean connecting out from a client on the pfSense 2 LAN? Like opening an external webpage? Which is what I thought you were doing.
Or connecting to that device from something in the pfSense 1 LAN? Which I would expect to be blocked anyway since there are no WAN rules to allow it.
In the former case you absolutely do need outbound NAT somewhere, but that could be in pfSense 1. And those inbound WAN rules make no difference.
If you have somehow moved the OBN to pfSense 1 it will fail if you send it to another location that isn't configured in the same way.
Steve
The bolded text is exactly what I was trying to do - get to an external page/resource from a client connected to
pfSense2's LAN.I currently have NAT on both
pfSense1andpfSense2, and it's fully functional.I'm not sure what you mean by OBN, should have asked in a previous comment.
-
Sorry, OutBound Nat. Gets tedious typing it every time!