Using a GRE Tunnel to route VMs network and IP to external network.
-
Hey everyone, so, I created a gre tunnel from my local pfsense to an hosting providers' remote pfsense so I can (as told by them) use their IP addresses on my virtual machines.
So, for instance,
I want the IP 192.168.1.139 to have the IP 185.113.141.139. I've been reading some posts here and figure out that I am suppose to be making a 1:1 NAT mapping for each individual IP I have.
I currently don't have an IP block so I gotta do every IP 1 by 1.
The Gre tunnel is already created and both pfsenses communicate to each other. The IP I have on a VM is currently the 192.168.1.139 and when I use
ping 8.8.8.8I get the following states on the local pfsense: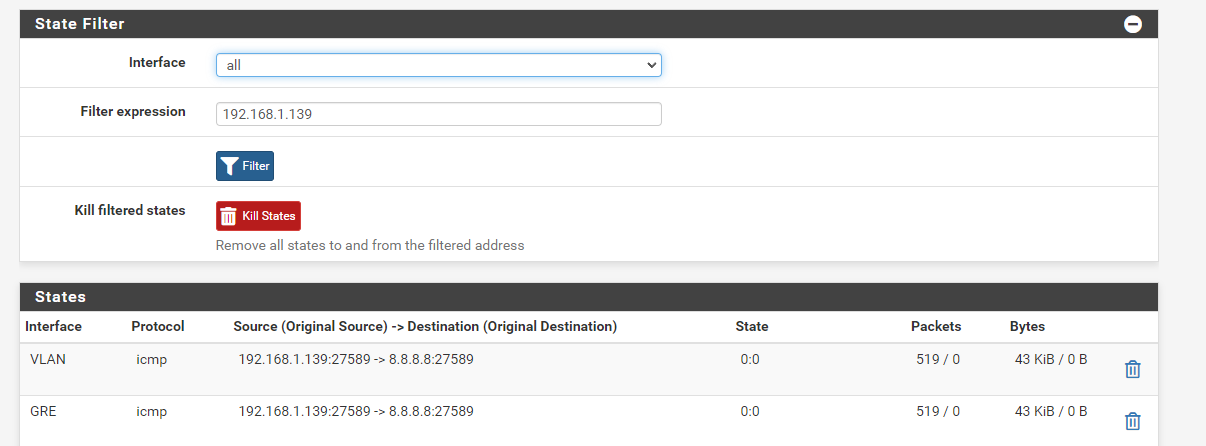
I've also created a gateway for the VMs with the gateway 185.113.141.1 which is the hosting providers' gateway address.
I created a static route from the remote pfsense with the IP I want to use in the VM 192.168.1.139:

which did not do anything..
Some Info:
- Local PFSense address: 192.168.1.10
- Remote PFSense address: 185.113.141.132
- Local GRE Tunnel address: 10.0.2.1
- Remote GRE Tunnel address: 10.0.2.2
- My available remote IP addresses to use on VMs: 185.113.141.139
- Current virtualization system: Proxmox
After following the steps on this post https://forum.pfsense.com/topic/173892/gre-tunnel-to-protect-ip this was all I could achieve, somethings did not work as expected.. If someone could give me a hand I would be very grateful
Best regards,
Xuap -
I assume you are using those IP addresses just as an example? Because those are just copied from the other post, those IPs will not work for you.
That static route makes no sense. You need a static route to 192.168.1.0/24 via 10.0.2.1 on the remote pfSense.
You also need a policy rule on the local pfSense to pass outbound traffic from the local hosts there over the GRE tunnel.
Then add the 1:1 NAT rules on the remote pfSense.
Steve
-
The IP addresses seem to be copied from the other post because they are from the same provider. So in a nutshell, I only need the tunnel created in both ends and add a static route to the 192.168.1.0/24 so that the local IPs on my side can reroute the traffic to the tunnel and so the tunnel can handle that traffic?
The 1:1 NAT rule on the remote (Where the IPs are being routed to) should be something like
- Internal IP: 185.113.141.139
- External IP: 192.168.1.139
And the NAT address should be the interface address (The tunnel one)?
If so, as soon as I get home I'll try to adjust it to these configs and instantly feedback the results.
Thanks in advance.
João Ferreira
-
The static route needs to be on the remote pfSense so that it knows how to reach the 192.168.1.0/24 subnet on the other end of the tunnel. Doing that also adds an outbound NAT rule for that subnet so that traffic arriving over the tunnel can reach the internet. As long as outbound NAT is in automatic mode there still.
You also need a policy routing rule at the local pfSense box if you also want the host in 192.168.1.0/24 to use those public IPs for outbound connections.Steve
-
Everything's done as you said. Now, to use the IPs on the Virtual Machines on Proxmox, I need to create a linux bridge that is associated to the local pfsense (a VLAN was created for that with the remote gateway)
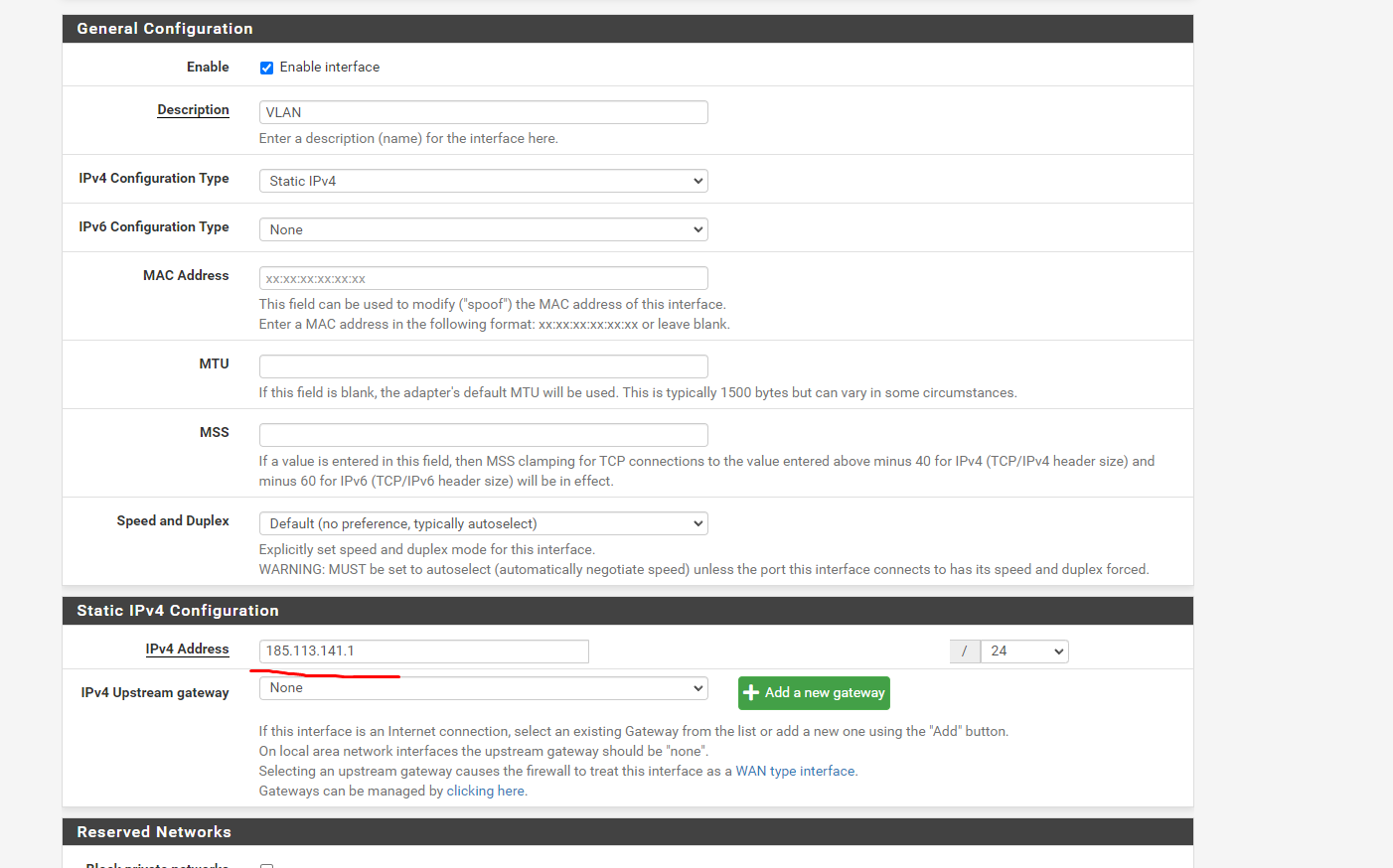
and to get the VM to use the IP I need to put for instance: IP: 185.113.141.139 Netmask: 255.255.255.0 Gateway: 185.113.141.1 or I need to use my normal router gateway (192.168.1.254) and a local ip address like 192.168.1.139?Thanks in advance.
João Ferreira
-
@xuap So, I used the gateway 185.113.141.1 on the VM and the IP 192.168.1.139, on the local pfsense I get this
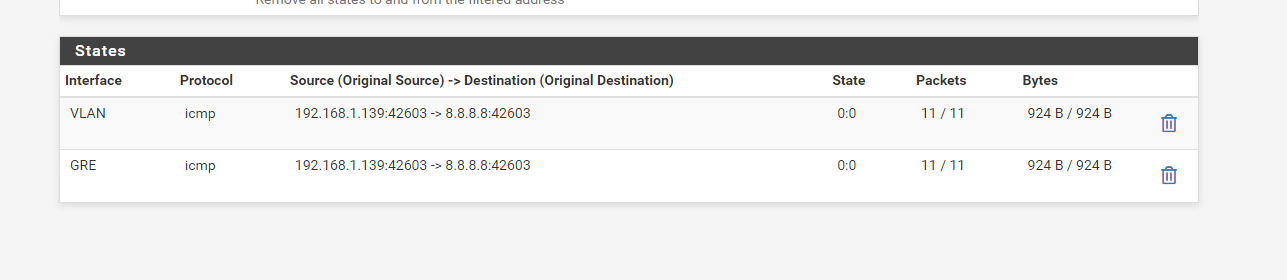
and on the remote I get this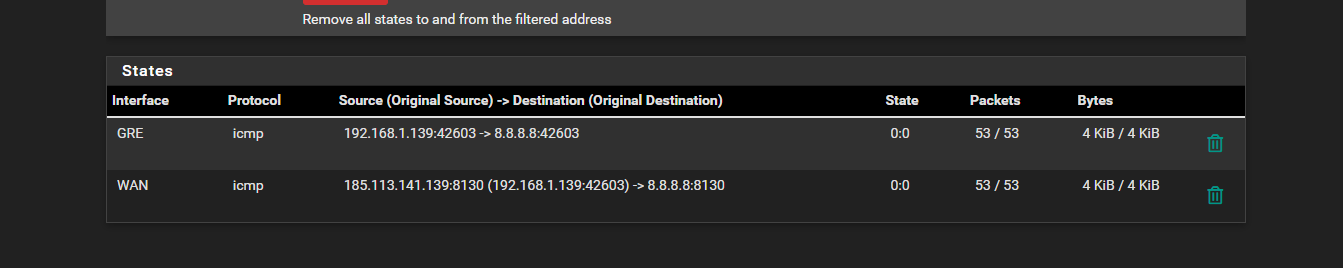
Also, I have this NAT rules

but I don't have internet access on the VM.
-
If you are 1:1 NATing, as you initially said, then you should not have any public IPs at the local site.
The only place the public IPs would be defined would be as VIPs at the remote site.
In the other thread they were given a routed subnet and so could use the public IPs directly on hosts at the local end. In that situation you don't need to NAT anything and instead can route the subnet across the tunnel at the remote site. Then use the subnet directly on an interface at the local end. The pfSense VLAN interface would still not be the .1 address though, that would imply they gave you the full /24 subnet which is very unlikely. It would be the first usable IP in the subnet they routed to you.
Steve
-
@stephenw10 Unfortunately, they didn't allow us to have a routed subnet, so I have to stick with the 1:1.
Virtual IPs on the remote site:

Virtual IPs on the local site:

I only have Virtual IPs on the remote which is one additional IP I got that the hosting provider gave me.
So, in my case do I need to change the gateway 185.113.141.1 to anything else or do I need to make some firewall rules to give the VM internet access or something? Because if I change to my router's gateway and the bridge to the main bridge of pfsense (WAN) the network starts working but I don't get any data on pfsense stats nor the public IP is correct..
-
If I ping something like 1.1.1.1, on the console I get

without any output, but I do get the states on both ends
LOCAL:
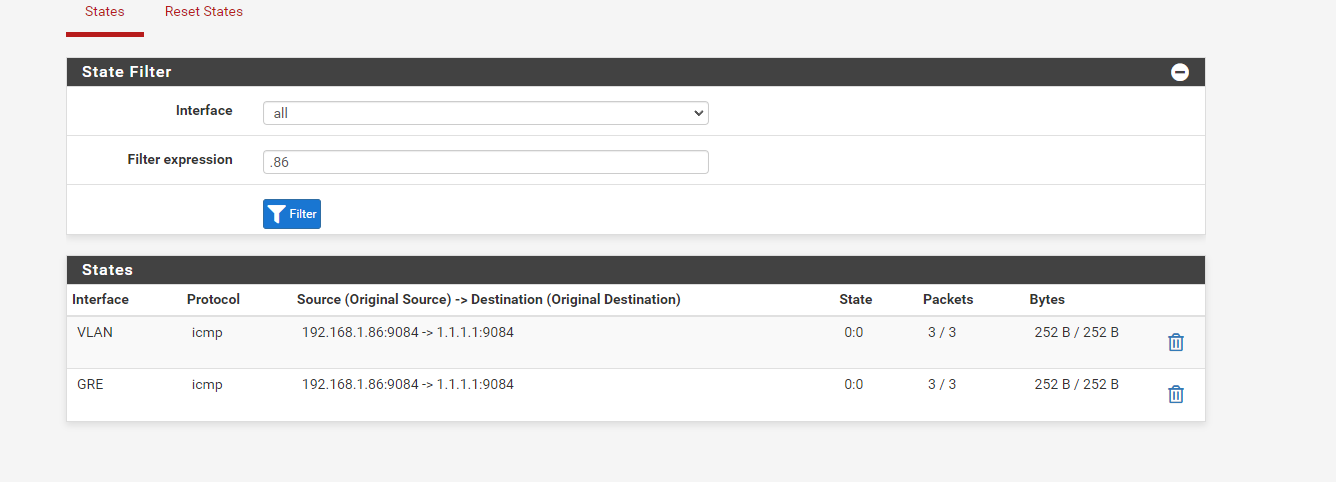
REMOTE:
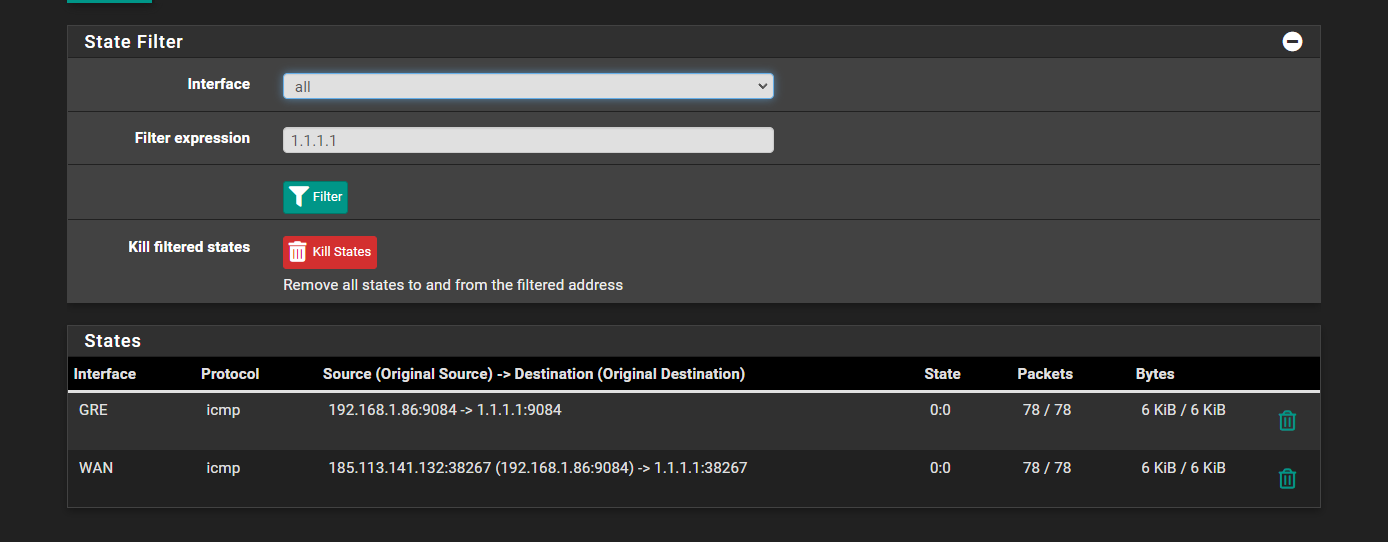
also referring that it's showing the ip 185.113.141.132 when the IP I want to use is the 185.113.141.139.
-
Ok, so what's the 1:1 NAT rule at the remote side? It looks like it's not catching the traffic there on the way out and it's using the auto outbound rule instead.
Also the 1:1 NAT rule would not change the source port (icmp ID here) like is shown there.However it does look to be working as expected apart from that. There is two way traffic shown on all 4 interfaces involved. But the ping fails?
Steve
-
@stephenw10 The NAT rules on the remote site are like this:
1:1
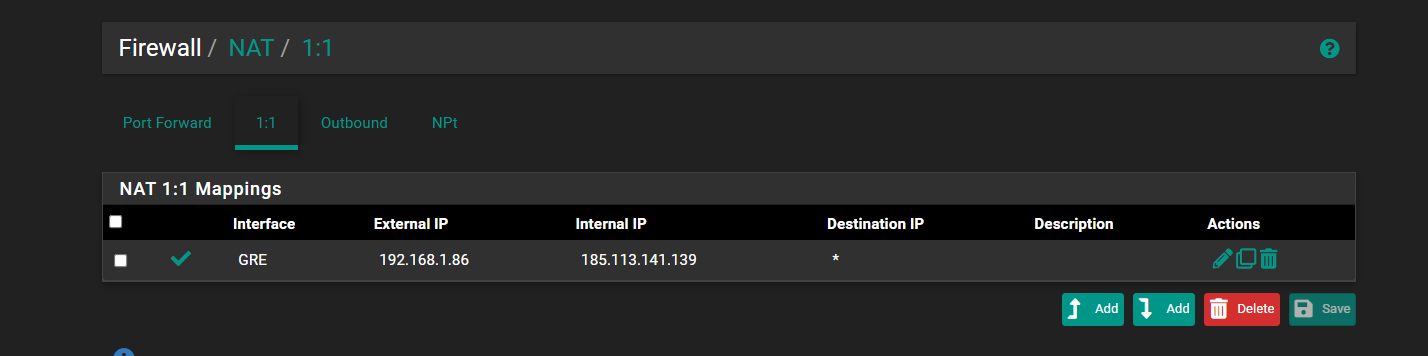
Outbound

Yeah, basically it just doesn't have internet access, nor even access to the pfsense or tunnel ping.. I can't ping the tunnel through the VM even tho the ping arrives there.
-
Ok the 1:1 NAT rule should be on WAN with the external IP being the public IP VIP and the internal IP being the private IP of the server.
-
@stephenw10 So, like this?
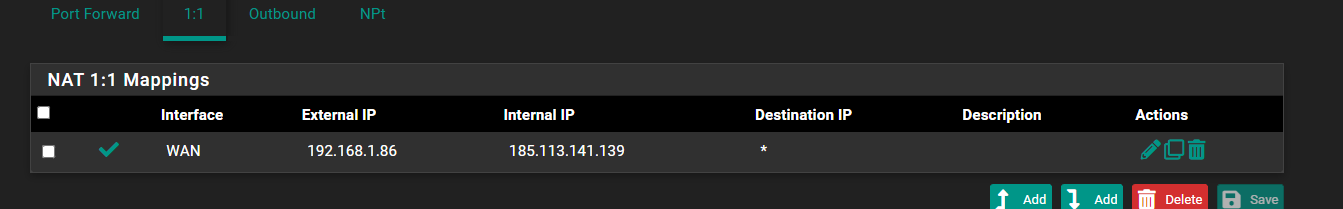
And on the VM, like this?

-
No the external IP should be the public IP. The internal IP should be the server IP in 192.168.1.0/24.
The VM gateway needs to be in the subnet so it should be the local pfSense VLAN interface IP. Probably 192.168.1.1
-
@stephenw10 So, my networks on local pfsense are like this:
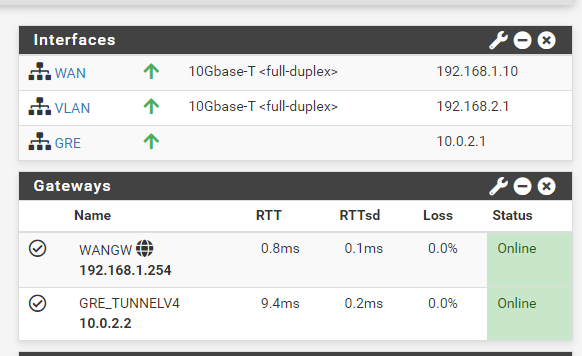
My WAN is the 192.168.1.10 which is on the main gateway of the router 192.168.1.254
I use the VLAN as a bridge for the VMs, but should I use something else both on pfsense or on the VMs?
-
Hmm, where is the VM at 192.168.1.86 then?
I expect all the VMs to be in the VLAN subnet and all the routing the NAT setup to be to and from the VLAN subnet.
Steve
-
I also did a pcap on both the GRE and VLAN of the local pfsense
GRE:

VLAN:

So, as I understood it is sending the ping to the 1.1.1.1 but it is not receiving any traffic..
-
Right, well it won't if traffic from 192.168.1.86 is coming in on the wrong interface!
If you run a pcap on WAN you will see all the replies going back that way because that's where the 192.168.1.0/24 subnet is.
How exactly is the VM connected?
-
@stephenw10 The VM is in the proxmox with the IP on 192.168.1.86 and gateway 192.168.2.1 like I showed above
The VM is with the bridge of the VLAN (192.168.2.1) which is the Linux Bridge 1 on proxmox (vmbr1) that will (supposedly) be attached to all VMs so it can tunnel the traffic to the remote pfsense
-
This is the only 1.1.1.1 ping I have on the WAN of the local pfsense
