Accessing hosted websites from internally
-
Hello everyone
I am looking for help solving the following problem (I think it's NAT related, but I am not totally sure..)
In my network I have different VLANs, one of them is for hosting external services like webservers. The rules for inter VLAN communications are restrictive (f.e. IoT network can not access anything besides WWW).
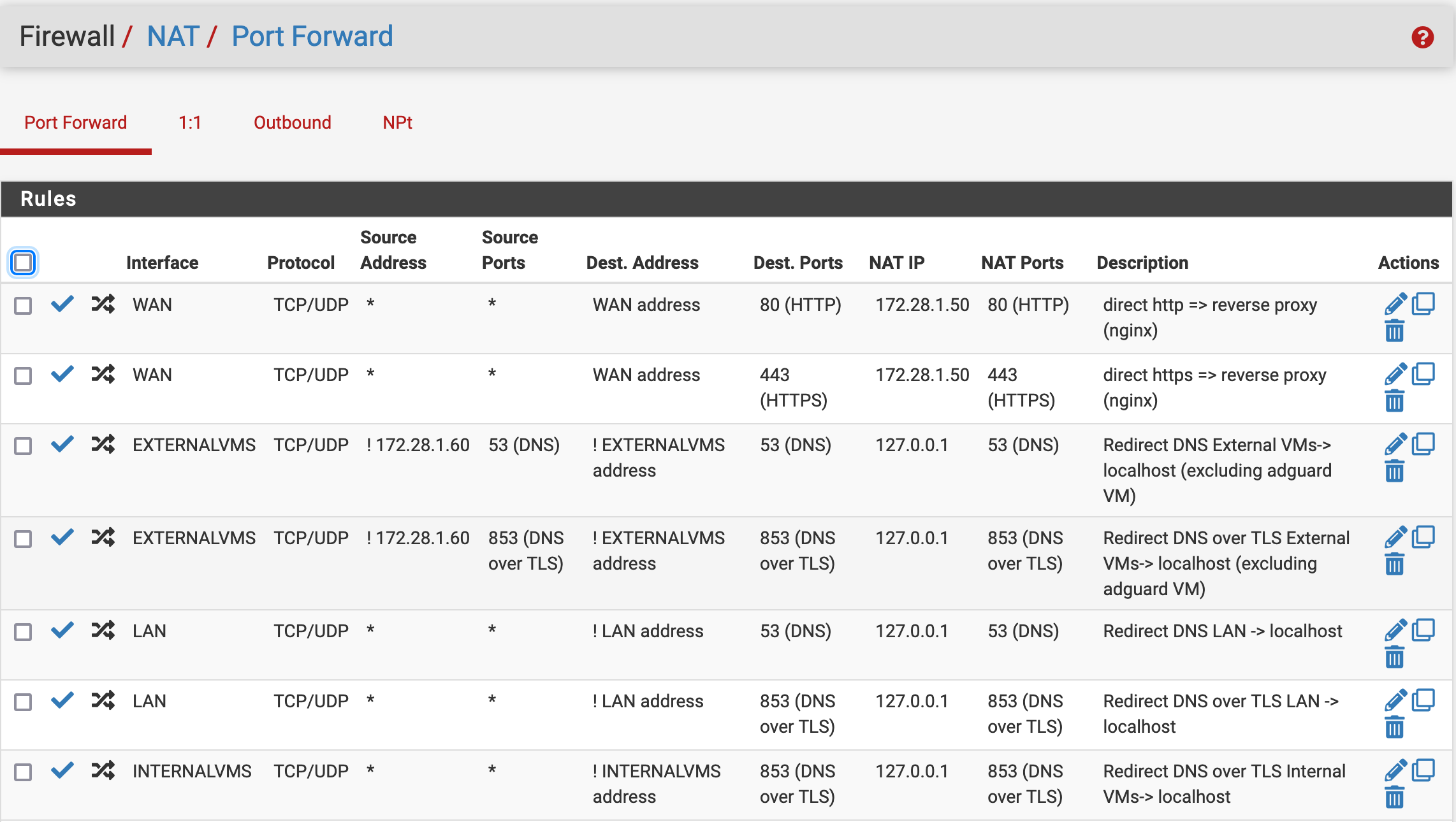
I reroute DNS queries to an AdGuard VM using DNS resolver and the "DNS-Server" Information in "General Setup" Also there are NAT rules forcing every query on port 53 and 853 to localhost (and consequentally to AdGuard). WWW access and DNS works with this setup.
So my understanding is, that I already use Split DNS (correct?). However internally hosted websites are still not available even with NAT Translation enabled. Host overrides in DNS-Resolver does not work for some reason (right now disabled..)
How can I solve this problem? From externally the websites are of course available (sub.domain.ch)
Following a few screenshots of my setup:

I am a little lost and happy for any help!
Best, Alex
-
@unserpablopajero
Redirecting DoT doesn't make sense at all, since the client is awaiting an SSL certificate from the requested DNS server before he start the request. You internal DNS server will not have a matching certificate.Split DNS means that your public host names are resolved to the internal IPs within your network.
So you need to add DNS host overrides to the Resolver pointing to you internal IPs.
So check on your devices with dig or nslookup, what IP you get for your public host name and which DNS server is responding. -
@viragomann Thanks!
I added a host override, the nameservers used are localhost and my AdGuard VM. And it's resolved to the correct internal IP (although on a different VLAN, but that should not be a problem, right?)
However, the webserver is still not accessible..
In regards to DNS over TLS; should I delete those rules then? I wanted to make sure, that every service on every device can only use the DNS server specified in pfSense, but if I understand correctly, DoT redirect rules are not necessary because my server would not provide the certificate needed for those external requests?
-
@unserpablopajero said in Accessing hosted websites from internally:
And it's resolved to the correct internal IP (although on a different VLAN, but that should not be a problem, right?)
However, the webserver is still not accessible..Maybe you need to allow the access.
If the host names resolve properly the client should try to connect to the internal IP.Simply block or reject DoT. So the devices will use unencrypted DNS.
Also consider to block DoH with pfBlocker or alike. -
I did and I can access the website over the internal IP. I had hoped there's a more elegant way of doing it, after all I wanted to separate the VLANs. But thats how I am going to run for now...
Ok, will do :) I used pfBlocker before and wanted to try AdGuard (I like the interface...)..
Thank you, I wish you a pleasant day! :)
-
@unserpablopajero said in Accessing hosted websites from internally:
I used pfBlocker before and wanted to try AdGuard (I like the interface...)..
The one feature of pfBlocker is generating block or reject rules, used by pfSense to block specific IPs or network ranges, the other is DNSBL for filtering DNS requests and responding its own data.
If you want to stay with AdGuard you can disable DNSBL and use only pf rules.
There are lists for blocking DoH available. But maybe you can do that with AdGuard as well. -
@viragomann I changed to pfblockerng. It's easier to use and less complicated with rules. Is it correct though; if I want every DNS query to hit my specified (and filtered) DNS Service, I do need NAT rules? (although no DoT rules..)
-
@unserpablopajero
Not clear, what you're talking about.
DNSBL or redirecting DNS queries in general?For DNSBL, if you enable it it's used automatically with the DNS Resolver. It adds a line in the Resolvers custom options to include it.
Additionally NAT rules for redirecting port 80 and 443 are automatically added.Redirecting all DNS requests to pfSense itself is a good method to catch all DNS request and resolving them on pfSense, even if the client has a static setting. pfSense send responses back using the IP the client requested, so the client doesn't notice that he didn't get to the requested server.
Best practice to configure the DNS Resolver to listen on localhost and redirect any DNS requests to 127.0.0.1.
Regarding DoT, simply reject it on all interfaces. I do this with a floating Quick rule.
-
@viragomann I thought about DNS queries in general, but you already answered :) Will block DoT.
Thank you!