LAN access from VPN
-
I have a Netgate 4100. It’s set up to be a Wireguard VPN server, and that’s working great. Peers connected to the Wireguard VPN can see the Netgate on 192.168.1.1 and 192.168.2.1 (which is in their subnet), but they cannot see other LAN devices (192.168.1.x) other than 192.168.1.1. Is there an easy way to allow bidirectional access between 192.168.1.x (LAN) and 192.168.2.x (WG_VPN)? A bridge seems like overkill, maybe just some sort of routing rules, like whatever permits access to 192.168.1.1 (not actually sure why that works)?
-
@ghazel What did you enter for allowed IP's?
-
@jarhead on which device?
The client (a MacBook Pro) says "AllowedIPs = 0.0.0.0/0,::/0" in the [Peer] section that describes the PublicKey / Endpoint for the pfSense server.
The server (pfSense) says "AllowedIPS = 192.168.2.14/32" for the Peer Address Configuration that describe the client's public key.So, when the client connects it gets an IP address of 192.168.2.14, and can contact 192.168.2.1 and 192.168.1.1 (somehow), but not for example 192.168.1.13.
-
@ghazel did you create rules allowing it?
https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-ra.html#firewall-rules -
@ghazel Did you assign an interface to the tunnel or did you just assign the tunnel address in the wireguard config?
If you assigned an interface you would need to add rules to that interface.
I didn't look at the link Steve posted so that may already be in there, check that link first. -
I assigned the interface (WG_VPN) to the tunnel, so I already have both rules.
-
@ghazel So the outbound NAT should be automatically created then.
Do you see the tunnel network listed? Firewall/NAT/OutboundMake sure the MTU is at 1420 on the wireguard interface.
Diagnostics/Routes, tunnel listed and on correct interface?
-
@jarhead I don't see anything interface specific in Firewall/NAT/Outbound, but I do see the 192.168.2.0/24 range.
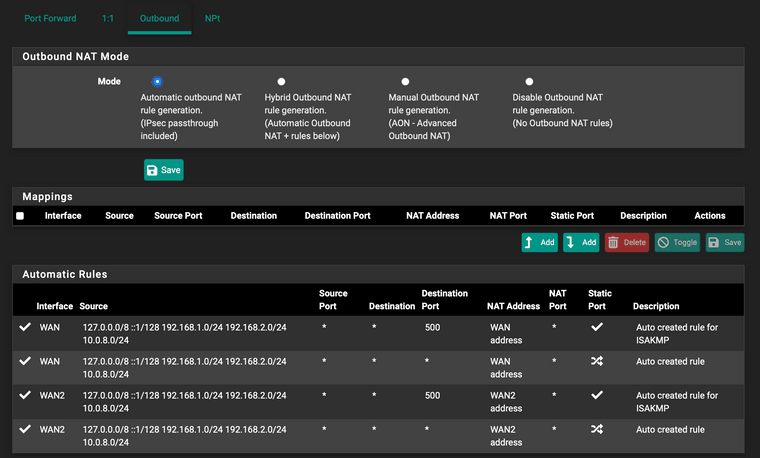
Similarly for Diagnostics/Routes, attached screenshot of what seems relevant:
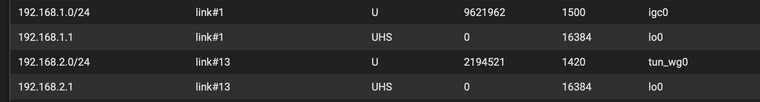
-
@ghazel Post pics of rules and configs from both ends.
-
@jarhead not certain which rules and configs you're talking about. One side is pfSense, which I've shown above, the other end is a macOS machine running wireguard. So no rules there, and only the most basic wireguard config.
-
@ghazel When you say "other" LAN devices, are you actually trying other devices or just one? It might be a software firewall on that device if just one.
-
@jarhead Any other device on 192.168.1.1/24 is unreachable. No firewalls on those devices. I guess I could packet capture to see what happens to those packets..
-
Packet capture on the pfSense LAN interface does show the packets from 192.168.2.14 (WG_VPN subnet) destined for 192.168.1.16 (LAN subnet). However, there is no response. Perhaps tellingly, 192.168.1.16 can reach 192.168.2.14 and it does respond. So for example I can ssh from 192.168.1.16 to 192.168.2.14, but not from 192.168.2.14 to 192.168.1.16.
-
@ghazel but there is a rule on the VPN interface allowing access to lan?
Usually it’s:
Missing fw rule in arriving interface
Device fw doesn’t allow different subnet
Device not using pfSense as gateway -
@ghazel said in LAN access from VPN:
Packet capture on the pfSense LAN interface does show the packets from 192.168.2.14 (WG_VPN subnet) destined for 192.168.1.16 (LAN subnet). However, there is no response. Perhaps tellingly, 192.168.1.16 can reach 192.168.2.14 and it does respond. So for example I can ssh from 192.168.1.16 to 192.168.2.14, but not from 192.168.2.14 to 192.168.1.16.
I agree with Steve and my guess would be the gateway.
You can check by doing the packet capture again but on the WAN instead. You'll probably see the replies being sent out that way. -
I don't see reply packets on WAN. I did uncover more detail that is surprising, though:
Capturing on LAN, I see packets from 192.168.2.14 to 192.168.1.16 as expected. Capturing on the 192.168.1.16 machine, the same packets have the LAN mac address but a source IP of 192.1.68.1.2 -- that's the IP of a Netgear WiFi router running in AP mode (it doesn't run DHCP, and it isn't a gateway), which 192.168.1.16 is connected to. Of course, when 192.168.1.16 responds to 192.168.1.2 it gets ICMP host unreachable responses (with the correct Netgear mac address), and the TCP connection fails.
-
-
@steveits said in LAN access from VPN:
@ghazel but there is a rule on the VPN interface allowing access to lan?
Usually it’s:
Missing fw rule in arriving interfaceArriving interface (WG_VPN) has an 'Allow Any' rule.
Device fw doesn’t allow different subnet
Device fw is not enabled. (behavior is the same even with it enabled, since the source IP of the packets is 192.168.1.2 -- inside the subnet)
Device not using pfSense as gateway
Device is using pfSense 192.168.1.1 as a gateway.
@viragomann said in LAN access from VPN:
@ghazel
Seem a bit mysterious. Can't really believe.Maybe the Netgear is still doing source IP rewriting for sources that are outside the subnet?
I also suspect that the access is blocked by the destination device itself. This is the default behavior of an operating systems firewall.
Operating system firewall is off. Wireshark is seeing the packets and the responses.
-
@ghazel said in LAN access from VPN:
Maybe the Netgear is still doing source IP rewriting for sources that are outside the subnet?
It can do this only on traffic which passes through it.
Operating system firewall is off. Wireshark is seeing the packets and the responses.
Can you post this capture and tell us, on which device and NIC it was taken.
-
@viragomann said in LAN access from VPN:
@ghazel said in LAN access from VPN:
Maybe the Netgear is still doing source IP rewriting for sources that are outside the subnet?
It can do this only on traffic which passes through it.
The traffic is passing through it. Internet > WG_VPN > LAN > Netgear > 192.168.1.16
Operating system firewall is off. Wireshark is seeing the packets and the responses.
Can you post this capture and tell us, on which device and NIC it was taken.
pfSense_LAN.cap
192.168.1.16_en6.pcapngUploaded capture from pfSense on LAN interface 192.168.1.1 90:ec:77:32:cb:ad (which is plugged into the Netgear, 192.168.1.2 3c:37:86
 fc:ae) and capture from target machine en6 192.168.1.16 8c:ae:4c:dd:4a:91 (plugged into that Netgear).
fc:ae) and capture from target machine en6 192.168.1.16 8c:ae:4c:dd:4a:91 (plugged into that Netgear).