Unknown 10.x.x.x address
-
@yorke said in Unknown 10.x.x.x address:
that address its ping and udp 67-68 connections I am asking because I have no
67-68 is dhcp.. where are you seeing that?
Somebody prob connected some wifi router with that IP, and its handing out dhcp.. Maybe your using it for your wan?
Just look at ifconfig on pfsense - what does it show for your IPs, this would show vips as well.. You can also look at your routing table - is that your gateway IP, from your wan connection...
-
I'd guess some client moved onto the network after previously being on that subnet somewhere else and tried to connect to it.
However if that were the case I would not expect a block rule to to make any difference. Assuming the rule was correctly blocking only that destination.
-
Virtual IP Address
10.10.10.1/32 LAN IP Alias pfB DNSBL - DO NOT EDITpfblockerng is at default did not change
seeing it as soon as computers connect pings and udp 68 67 to and from that address.
ifconfig WAN ipaddress starts with 98
LAN ipaddress starts with 172IPv4 Routes default gateway
default 98.X.X.X UGS 15 1500 ixl310.10.10.1 link#10 UH 14 16384 lo0
Alert from Suricata rule I created
06/24/2024
16:58:47 3 UDP Misc activity 10.10.176.1
67 255.255.255.255
68 1:10000151
 Unknown Reserved Internal IP - 10.10.176.1/24
Unknown Reserved Internal IP - 10.10.176.1/24 
Suricata is setup on LAN.
-
Then I'd suspect a client that moved from a different WiFi network where that subnet is used and hasn't updated yet.
-
@yorke yeah as @stephenw10 mentions - destination port 67 to broadcast address would be a request or discovery.. My guess would be request because the client prob asking for renew, ie to keep using its old IP, etc..
What is the mac address - track it down on your network to what it is exactly.
-
ip was from the wan
Exploit UPnP & NAT-PMP
disabled UPnP & NAT-PMP.I would like to thank the maintainer of Suricata
if it was not for Suricata alerts i would not have caught this
thank yougood reason to have backups and extra drives
swap drives and restore backup -
@yorke said in Unknown 10.x.x.x address:
ip was from the wan
Well then who cares its just noise.. Some dhcp from your isp network, or something you have upstream of pfsense - its not going to go anywhere.. Pfsense would just drop that traffic..
edit: I had setup a sniff while back, just looked - what do you know some dhcp traffic on the isp network.. An offer and ack.. the dhcp server in the isp network - giving someone an IP..
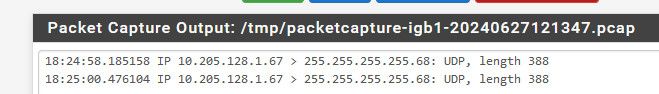
Relay Agent IP Address: 10.205.128.1
Maybe this is news to you - but ISPs use rfc1918 space in their networks ;)
Why anyone would run IPS on their wan anyway - are you hosting services available to the public internet? If not makes zero sense to run IPS on the wan side..
-
Suricata running on the LAN always was
address was hitting lan
block address system on that
LAN no internet (UPnP & NAT-PMP enable).
unblock internet access.disable UPnP & NAT-PMP no address
turn it back on and its back.packet capture on the wan.
who cares I do when powershell scrip
is trying to gain admin access.yes I do know ISPs use rfc1918 space.
Topic Closed Resolve
-
@yorke said in Unknown 10.x.x.x address:
address was hitting lan
Then your not isolated at layer 2 between your wan an your lan.
-
Reads to me like something keeps opening port forwards to non-existent targets using UPnP. That should show in the UPnP status though. And you should be able to see which host keeps opening then and the investigate what it's running that's doing that.
-
@stephenw10 possible I guess - but the traffic is broadcast, what sort of port opening or forward would forward broadcast?f
Who would even have UPnP enabled - if they are concerned that some powershell script is going to own him?
If the traffic was being seen by his lan interface lack of isolation at layer 2 between his wan and lan seems more probable to me.
Does your wan connection run through a switch - or just single cable to your isp device, and no other cables at all connected to the isp device?
-
Mmm, indeed. If you really need UPnP then lock it down to only known devices.