DNS Forwarder Custom Options always gives "Invalid custom options"
-
@stephenw10 nor can I.. And I tried all kinds of weirdness in how I put max-ttl=30 in the box.. blank lines before it, spaces before and after it etc.. It always took it just fine.
-
@stephenw10 Here's the screenshots.
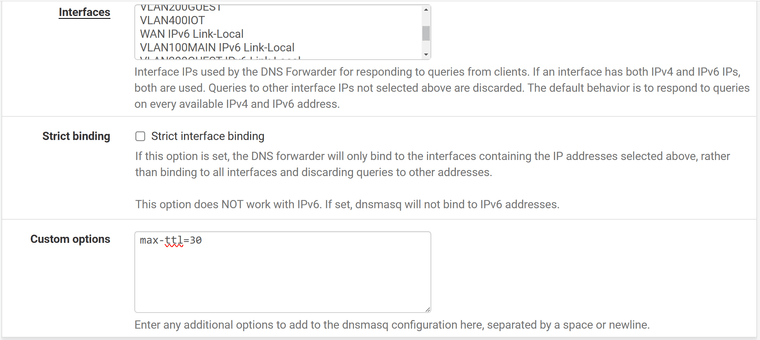
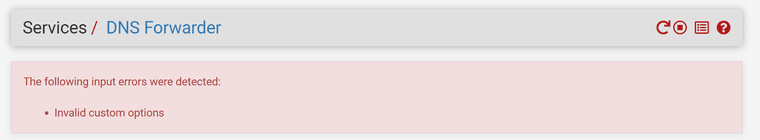
-
Hmm, some rogue character in there?
Some other odd combination of options?
What does it look like in the config:
<dnsmasq> <enable></enable> <port>5353</port> <interface></interface> <custom_options>bWF4LXR0bD0zMA==</custom_options> </dnsmasq>You probably don't have the custom options value as it sees it as invalid when adding it.
-
@stephenw10 It doesn't save it between attempts.
I thought it might be a random character or something like that, which is why I tried other browsers. It doesn't seem to be a browser issue though.
-
Then I can only imagine it's conflicting with some other option you have set.
Is that line you posted above the actual command that's run by your config?
-
This is the generated line:
/usr/local/sbin/dnsmasq -C /dev/null --rebind-localhost-ok --stop-dns-rebind --no-resolv --server=2600:1701:44d:6000::1 --server=192.168.1.254 --all-servers --dns-forward-max=5000 --cache-size=10000 --local-ttl=1
This is the one I created:
/usr/local/sbin/dnsmasq -C /dev/null --rebind-localhost-ok --stop-dns-rebind --no-resolv --server=2600:1701:44d:6000::1 --server=192.168.1.254 --all-servers --dns-forward-max=5000 --cache-size=10000 --local-ttl=1 --max-ttl=30
Both of these work
The only thing difference is max-ttl. I don't think this has anything to do with dnsmasq.
-
@blaize said in DNS Forwarder Custom Options always gives "Invalid custom options":
The only thing difference is max-ttl. I don't think this has anything to do with dnsmasq.
That is a valid dnsmasq option
--max-ttl=<time>
Set a maximum TTL value that will be handed out to clients. The specified maximum TTL will be given to clients instead of the true TTL value if it is lower. The true TTL value is however kept in the cache to avoid flooding the upstream DNS servers.dnsmasq --help | grep max-ttl --max-ttl=<integer> Specify time-to-live in seconds for maximum TTL to send to clients. -
You have the <dnsmasq> config section generating that?
-
It doesn't matter what I put in the text box. It gives me the error. I was using the max-ttl option just to eliminate the variables. I put it on the the command line to make sure it was not a problem with dnsmasq. It really seems like something between validation for the custom options and starting the daemon.
-
@blaize what do you show in the xml for dnsmasq - like @stephenw10 example above.
-
@blaize The corresponding fix seems easy enough for a patch:
https://redmine.pfsense.org/projects/pfsense/repository/2/revisions/aac5bb5d396a1f1b18d59a532ad262a4d1085a40/diff
-
@Antibiotic said in DNS Forwarder Custom Options always gives "Invalid custom options":
ttps://redmine.pfsense.org/projects/pfsense/repository/2/revisions/aac5bb5d396a1f1b18d59a532ad262a4d1085a40/diff
huh - how is that related to reading a custom options entry? That is about domain overrides.
-
@Antibiotic said in DNS Forwarder Custom Options always gives "Invalid custom options":
https://redmine.pfsense.org/projects/pfsense/repository/2/revisions/aac5bb5d396a1f1b18d59a532ad262a4d1085a40/diff
Mmm, seems unrelated.
But I do have all the recommended patches applied on the 2.7.2 box I'm testing on which might be a difference. I don't see anything dnsmasq related there but....
-
@stephenw10 I can't say that I have the latest patches. I run the updates on the UI pretty frequently and it says I'm up to date.
2.7.2-RELEASE (amd64)
built on Mon Mar 4 14:53:00 EST 2024
FreeBSD 14.0-CURRENTThe system is on the latest version.
Version information updated at Thu Dec 19 12:27:08 EST 2024 -
I'm referring to the recommends patches list in the System Patches package. I can't see anything there that should make any difference to dnsmasq but it's worth trying.