Another Netgate with storage failure, 6 in total so far
-
Netgate has finally implemented the fix.
https://redmine.pfsense.org/issues/16210#change-76840
Thank you, @marcosm, @fireodo, @andrew_cb -
Looks like it changes the vfs.zfs.txg.timeout default from
FreeBSD vfs.zfs.txg.timeout = 5
pfsense vfs.zfs.txg.timeout = 30So not as high as 120 suggested but consistent with andrew_cb recommendation
-
That patch code also has this: "zfs set sync=always pfSense/ROOT/default/cf"
Looking at my own system, I don't have that path, as I have only manually named Boot Environments, I have paths like "pfSense/ROOT/24.11_stable/cf ", so that part would fail.Should the command be run manually on the current default/active BE path, "pfSense/ROOT/24.11_stable/cf " in my case?
-
Yup. Fix incoming.
-
@stephenw10 should the timeout be 120 or 30?
-
zfs set sync=always pfSense/ROOT/default/cf
does not work on my 2100 I have a SSD should I run a different command for this?
-
A fix will be provided once it's ready on the following redmine:
https://redmine.pfsense.org/issues/16212 -
A patch is now available for testing on the redmine.
-
@stephenw10 is there a way to stop python pfblocker logging? I’ve tried to shut off all logging in pfblocker but the python module keeps on logging.
I’d prefer to keep using the python module for its benefits but the logging I don’t use often consumes my ssd lifetime at all other times without benefit.
-
@Mission-Ghost What logging are you seeing?
-
@SteveITS dnsbl.log just keeps going and going:
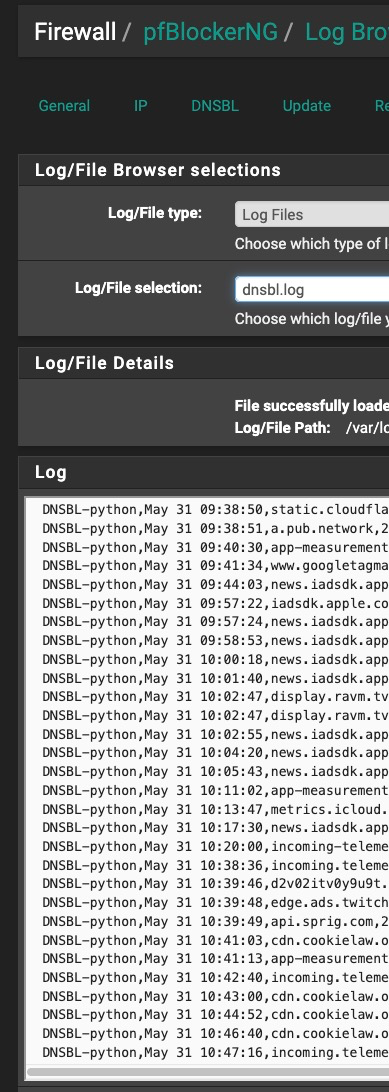
This is useful on rare occasions when I need to find a site to white-list, but I'd like to turn it on only on such occasions and off the rest of the time.
-
@Mission-Ghost That's set for all lists here:

or else on each list, e.g. on Firewall/pfBlockerNG/IP/IPv4.
With the logging off we have:
File successfully loaded: Total Lines: 0 Log/File Path: /var/log/pfblockerng/dnsbl.log -
@SteveITS Thank you!
I found and set it on the master configuration:
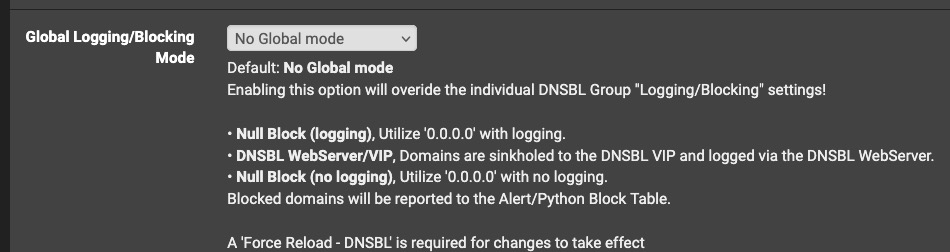
The master setting seems to be working so far.
Why does "Null Block (no logging)" log?
Why does "No Global mode" not log?
Is it just, me, or do the bullet points on the master DNSBL page fail to explain this clearly?
By my way of reading this, "No Global Mode" tells me that the individual settings on each Group will prevail. It doesn't tell me that it is overriding the individual settings on each Group, and sure doesn't tell me that logging is disabled, unlike "no logging" which says it's disabled but it isn't.
I feel like I'm taking crazy pills!
-
@Mission-Ghost No Global should mean it doesn’t override the individual settings. I just set it when creating each list so if the global settings aren’t working I profess ignorance. :)
-
@SteveITS said in Another Netgate with storage failure, 6 in total so far:
@Mission-Ghost No Global should mean it doesn’t override the individual settings. I just set it when creating each list so if the global settings aren’t working I profess ignorance. :)
Well, I guess it should mean it, but in context to some of of us who didn't develop the software, it isn't clear, particularly when adjacent options include "no logging" which apparently could not mean 'no' logging.
Seems like getting an English major (>gasp!<) intern to help redefine the labels to be more meaningful to customers would be a low cost, easy improvement to the usability of the product.
In any case, thank you for your generous help clarifying this. My problem is solved.
-
@andrew_cb said in Another Netgate with storage failure, 6 in total so far:
25% of the blocks are not available for wear leveling
In the same vein, this is a bit of an edge case, but I've strung a few bugs together.
-
there is a bug in Plus 24.03 and 24.11 where /conf/backup is not limited to 30 files (not auto pruned). Fixed in 25.03. https://redmine.pfsense.org/issues/15994, or the release notes. Workaround is to open the /diag_confbak.php config history page in the web GUI, and wait until it either loads or times out.
-
there's a longstanding bug in pfBlocker where if DNSBL is not enabled it will still update the config file at every cron interval, e.g. hourly.
https://forum.netgate.com/topic/174231/pfblockerng-fills-pfsense-config-history
https://redmine.pfsense.org/issues/14409 -
there's another longstanding bug in pfBlocker for HA setups where changes are not synced to the secondary router unless one manually runs a Force Reload (not a force update). Thus if you have, say, disabled a list, at every cron/update it will remove it from the backup and then when the same cron also runs on the secondary pfBlocker will add it again, generating two historical config files on the secondary router.
https://redmine.pfsense.org/issues/15994
https://forum.netgate.com/topic/179060/pfblockerng-sync-not-working/
With these, one poster in my thread https://forum.netgate.com/topic/197685/config-history-not-pruning-on-ha-pair-has-3400-files/ has 20000 config files on disk. At our file sizes of ~300k that is in the 6 GB range, though it should be compressed on disk, if using ZFS.
-
-
@SteveITS FWIW #2 should be fixed with the version in the 2.8.0/25.03 branch. As for #3 that may be fixed with https://redmine.pfsense.org/issues/16231 though the change may only take effect once the cron job runs on the secondary.
-
Wow, I stop checking the forum for a bit and come back to find that the ZFS patch has been released!

Thank you to @marcosm @stephenw10 @cmcdonald @dennypage @arri @w0w @SteveITS @Gertjan @fireodo @chrcoluk and everyone else that has contributed to this discussion and process.
Hopefully, this change will help reduce the change of storage failure for all devices running pfSense, especially those using small-sized and/or eMMC storage.
It is encouraging to see that additional areas have been identified for further improvements to storage wear and space usage.
We have progressed a long way from "you're holding it wrong."

-
I'll add another disk write case, though it's in ISC DHCP which is deprecated. I find "Ignore denied clients rather than reject" sometimes will log the rejection even if the option is checked, which usually results in a log entry every few seconds. Restarting DHCP Server seems to fix it (no log), and at some point later (update? restart? random?) I will find it is logging again.
-
"Thinking out loud here" :
If a (DHCP) client was set to be rejected, it will do the reject (it will answer "no") and normally, the client should take "no" for an answer - the the sofware is RFC compliant (I guess).
Let's consider 'ISC DHCP' as the old generation.
But its 2025, the client is probably a new generation DHCP client and won't take no for an answer, do'nt bother with RFC, so it keeps on insisting.
Now, ISC DHCP start to log.It's in the admin's authority to take things one level up. It was the admin after all who decided who to serve, and who to reject.
Go visit the client, and tell him who is boss in the town.
Next step : MAC black list the guy and call it a day.