What is wrong with this 2100 switch configuration?
-
Elsewhere I have posted about a problem I am having with a Netgate 2100. At least one poster pointed to potential problems with my switch configuration.
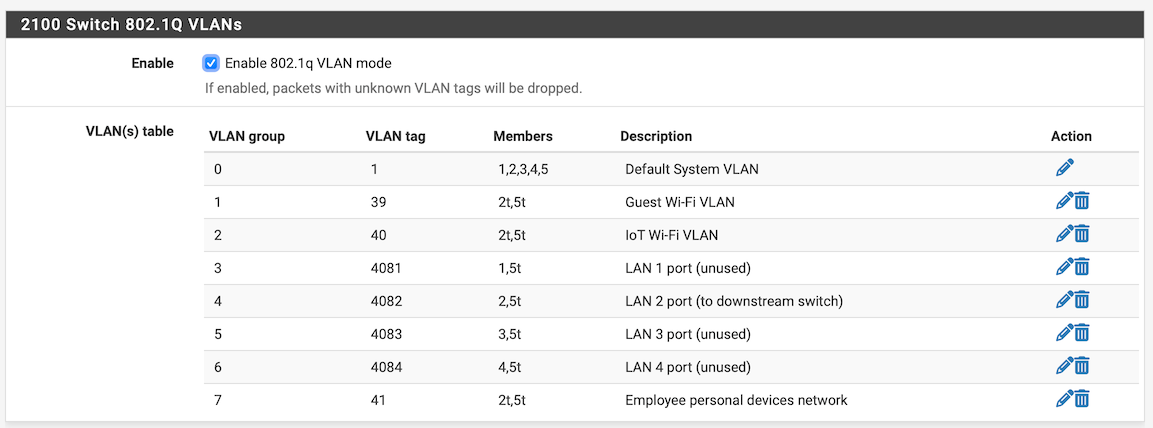
What would be wrong?
I do have to admit that I am not entirely clear on how this is supposed to work. While the 2100 documentation has a section on the internal switch, I can’t quite wrap my head around it, in order to build an adequate model in my mind of how it works.
For added reference, I am including the port configuration:
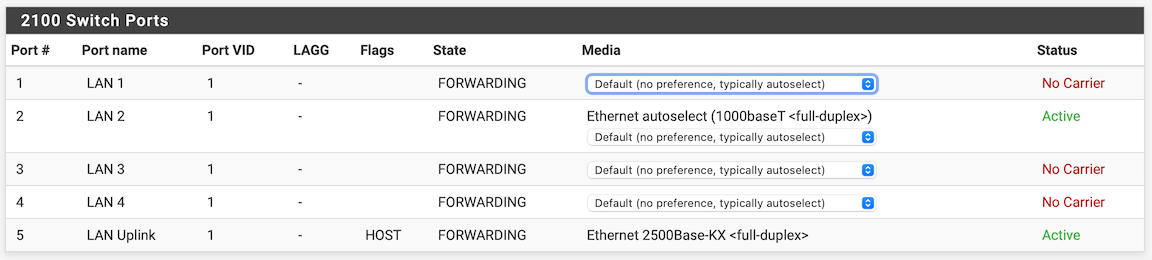
-
@DominikHoffmann I commented on your other question, maybe I'm not the guy to explain it but I'll try:
With VLAN there are a few things to know:
-
Access Port (Cisco) == Native VLAN (Unifi, with 'Block All' set for 'Tagged VLAN Management')
-
Trunk Port : a port carrying multiple tagged VLANs
-
PVID = Port VID = Port VLAN ID: a switch port can only ever have one PVID
-
untagged traffic: traffic from a client connected to a port, with no VLAN tag set on the client, the traffic will get a VLAN tag added on the switch. And every port on the switch does add a VLAN tag to untagged traffic. Which VLAN tag gets added is defined by the PVID. In the other direction, to the client, when tagged traffic leaves a port, the VLAN tag gets removed if VLAN tag == PVID
-
tagged traffic: the client (e.g. pfSense) tags the traffic with an VLAN tag, the switch does not touch that VLAN tag.
-
a port can only ever have one VLAN untagged on it, otherwise the switch doesn't know which PVID to set. In your configuration all ports have two untagged VLANs:
- port 1: VLAN 1 and VLAN 4081 untagged (e.gl VLAN group 0, VLAN tag 1, members 1,2,3,4,5 & VLAN group 3, VLAN tag 4081, members 1,5t)
- port 2: VLAN 1 and VLAN 4082 untagged
- port 3: VLAN 1 and VLAN 4083 untagged
- port 4: VLAN 1 and VLAN 4084 untagged
Of course the internet is full of resources around VLANS and probably explaining it a lot better.
As an example: port 2 in you config is a trunk port for VLANs 39, 40 and 41. It also carries a native VLAN: PVID is set to VLAN 1 (as you set for all other ports) and VLAN 4082. If you set the PVID for port 2 to 4082 and remove port 2 from VLAN group 0, it will then be separate port you will have to setup it in the 2100 (with an IP range, DHCP and firewall rules).
I will have to re-read your other thread to see what you want to achieve, can't remember.
-
-
@DominikHoffmann ^that but step 21/22 here:
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/configuring-the-switch-ports.html -
@DominikHoffmann Having a read-through your other thread Two VLANs set up alike, one does not get Internet: what brand/type of switch is it you have?
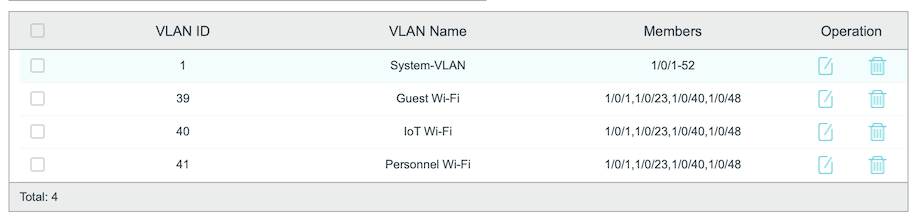
In the screenshot you posted VLAN 1 got port 1 to 52 as members. And the other VLANs are set on ports 1, 23, 40 and 48. How do you set the PVID for ports on this switch, each port can only have one PVID set, too.
My 8 port TP-Link switch for example does allow for multiple PVID set for a port, although the setup will not work correctly by doing so.
-
@patient0: I think, this is the insight I needed! VLAN 4081–4084 were holdovers from the factory-default configuration, and I simply left them in place. I should be able to simply remove those VLAN IDs, shouldn’t I?
-
@patient0 said in What is wrong with this 2100 switch configuration?:
How do you set the PVID for ports on this switch, each port can only have one PVID set, too.
That TP-Link switch is configured to use 802.1q VLANs. VLAN IDs 39–41 are tagged on Ethernet jacks 1, 23, 40, 48.
-
@patient0: Understanding what I am trying to do, what should I do differently?
-
@DominikHoffmann FWIW the factory default config doesn’t have those VLANs…by default ports 1-4 are a plain unmanaged switch. The doc page above is for isolating the ports to be separate networks/interfaces.
-
Yeah you would need the PVID set on the ports to connect untagged traffic to them but that wouldn't affect tagged traffic coming from other switches.
-
@DominikHoffmann said in What is wrong with this 2100 switch configuration?:
@patient0: I think, this is the insight I needed! VLAN 4081–4084 were holdovers from the factory-default configuration, and I simply left them in place. I should be able to simply remove those VLAN IDs, shouldn’t I?
Yes, if you have no interfaces configured for them, you can removed them. Then the ports will again be part of the switch/LAN and have VLAN 1 set for untagged traffic.
That TP-Link switch is configured to use 802.1q VLANs. VLAN IDs 39–41 are tagged on Ethernet jacks 1, 23, 40, 48.
And what is/are the PVIDs for this ports, VLAN 1?
@stephenw10 is right in that the issue with the untagged ports would not affect the tagged traffic. Except if on the TP-Link the PVID is not set to VLAN 1 but VLAN 39 or 41.
Do you have a network defined on LAN and does that work?
-
@patient0: First of all, thank you very much for your willingness to dig into my issue with me!
Yes, all the ports on the switch are set to PVID 1:
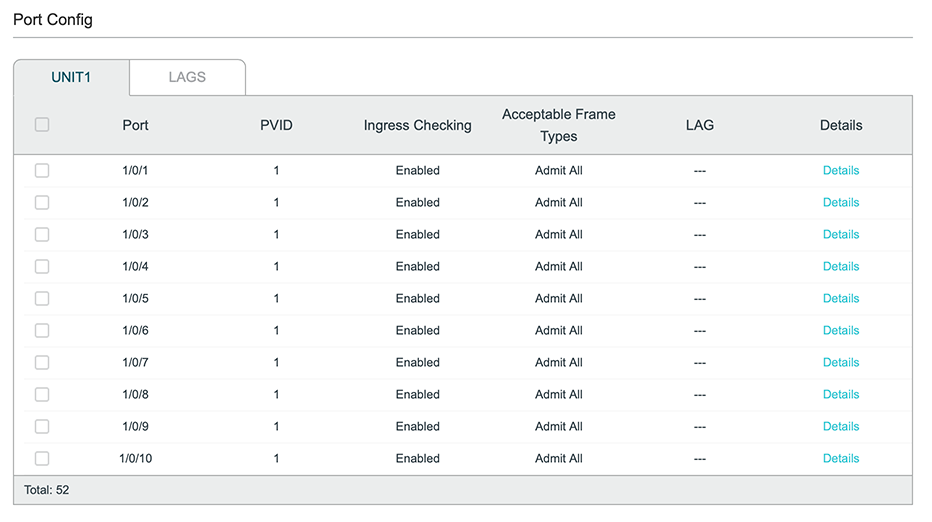
The table is scrollable, and when I scroll down PVID = 1 for all of the switch ports.
This is my new configuration in Interfaces → Switch → VLANs now looks like this:
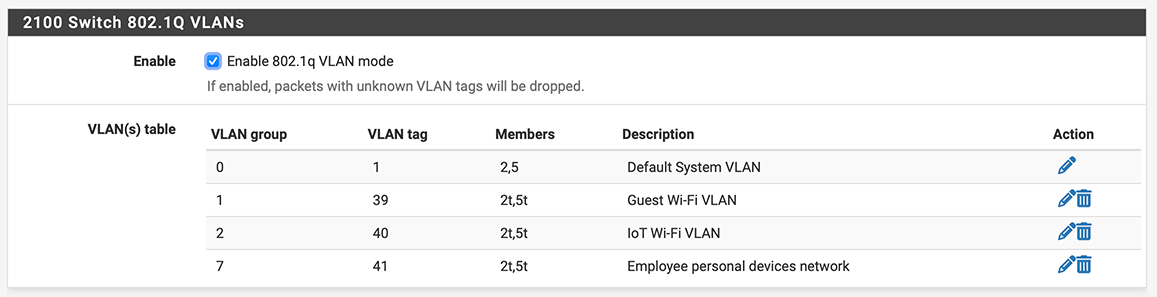
-
Additionally, I just did another test. I configured my MacBook Pro’s Belkin USB-C to Ethernet adapter to untag traffic with VLAN ID 39 and hooked it up to Switch Port 2 on the 2100 directly. This eliminates the TP-Link switch and UniFi Wi-Fi equipment from the equation. With that simplified setup I still cannot get to the internet from my guest network.
-
@DominikHoffmann said in What is wrong with this 2100 switch configuration?:
I configured my MacBook Pro’s Belkin USB-C to Ethernet adapter to untag traffic with VLAN ID 39 and hooked it up to Switch Port 2 on the 2100 directly.
Now the switch config does indeed look good.
Am I right to assume that the normal LAN (untagged VLAN1) does work with the Belkin USB-C ethernet adapter.
Can you access the internet and the router if you set the IP,subnet, router and DNS manually for the VLAN ID 39?
Just to make sure: And you created the VLAN 39 on the macOS by creating a VLAN in System Settings / Network, Manage Virtual Interfaces > New VLAN, set tag and select the Belkin USB-C adapter.
First of all, thank you very much for your willingness to dig into my issue with me!
Same goes for you for keeping on it, it certainly takes a quite a bit time, more then one thinks it should.
-
Ok that 2100 switch config should work for a directly connected connected tagged client like that.
So do you have VLAN 39 defined as an interface? Does it have dhcp running on it? Did your test client pull a lease in the correct subnet?
-
@patient0 said in What is wrong with this 2100 switch configuration?:
Now the switch config does indeed look good.
Thanks very much for confirming!
Am I right to assume that the normal LAN (untagged VLAN1) does work with the Belkin USB-C ethernet adapter.
Yes, it does.
Can you access the internet and the router if you set the IP,subnet, router and DNS manually for the VLAN ID 39?
I don’t think that’s necessary, as my laptop pulls an IP address, router and DNS.
Just to make sure: And you created the VLAN 39 on the macOS by creating a VLAN in System Settings / Network, Manage Virtual Interfaces > New VLAN, set tag and select the Belkin USB-C adapter.
I did.
@stephenw10 said in What is wrong with this 2100 switch configuration?:
So do you have VLAN 39 defined as an interface? Does it have dhcp running on it? Did your test client pull a lease in the correct subnet?
Yes, yes and yes.
Still no cigar!
-
@DominikHoffmann said in What is wrong with this 2100 switch configuration?:
I don’t think that’s necessary, as my laptop pulls an IP address, router and DNS.
Oh, I see, I thought you didn't get an IP.
DHCP is working but you can't get to the internet. Is the captive portal still active (I have no knowledge about that, never used it) and if yes can you authenticate successfully?
And you can ping the pfSense/gateway? Can you ping an external IP address? Does DNS resolution work?
-
@patient0 said in What is wrong with this 2100 switch configuration?:
And you can ping the pfSense/gateway? Can you ping an external IP address? Does DNS resolution work?
I cannot ping it.
I don’t think, I ever checked, whether the captive portal is the culprit. I will do so this afternoon.
-
Yup if it pulls a dhcp lease in the correct subnet but cannot even ping the pfSense interface address then it must be a firewall rule or the captive portal.
-
@stephenw10: Yes, it was the captive portal. Now I have to figure out what’s wrong with the configuration…
-
D DominikHoffmann referenced this topic on
-
Indeed, I have to consult the community on how to configure the captive portal, too.