ICMP Flooding - Need Advice
-
For the past few weeks I have been seeing a large number ICMP request being logged in my firewall. From what I can tell this would be considered a "Ping Flood Attack" but I could be wrong as I have never dealt with something like this. The request are being blocked by pfsense and I am not really seeing a performance hit so I am not sure if I need to worry about it or not.
The problem is more that these request are filling up my logs and I'm not sure but possibly causing my pfSense router to work harder processing the request. After looking around the web, it looks like the only recourse is to have my ISP block the IP's. I did contact my ISP and there tech support told me they don't even know anything about this type of DOS attack. They said the techs that would understand would be their paid support and nothing would be done about this unless I wanted to pay to talk to them. wtf really?
These request are hitting the WAN address about 9 times every second CONSTANTLY ongoing. Here is an example:
Nov 28 14:26:34 WAN WAN: default block IPv4 (1531018817) 64.94.179.80 xx.xxx.xxx.xxx ICMP Nov 28 14:26:34 WAN WAN: default block IPv4 (1531018817) 64.94.179.89 xx.xxx.xxx.xxx ICMP Nov 28 14:26:34 WAN WAN: default block IPv4 (1531018817) 64.94.179.83 xx.xxx.xxx.xxx ICMP Nov 28 14:26:34 WAN WAN: default block IPv4 (1531018817) 64.94.179.88 xx.xxx.xxx.xxx ICMP Nov 28 14:26:34 WAN WAN: default block IPv4 (1531018817) 64.94.179.84 xx.xxx.xxx.xxx ICMP Nov 28 14:26:34 WAN WAN: default block IPv4 (1531018817) 64.94.179.86 xx.xxx.xxx.xxx ICMP Nov 28 14:26:34 WAN WAN: default block IPv4 (1531018817) 64.94.179.87 xx.xxx.xxx.xxx ICMP Nov 28 14:26:34 WAN WAN: default block IPv4 (1531018817) 64.94.179.82 xx.xxx.xxx.xxx ICMP Nov 28 14:26:34 WAN WAN: default block IPv4 (1531018817) 64.94.179.80 xx.xxx.xxx.xxx ICMP(xx.xxx.xxx.xxx) being my WAN address
These are not the only addresses but they all start with 64.94.179. and appear to belong to Internap Network Services Corporation. The IP's all resolve to performance-measurement-6461-1.mse003.pnap.net and "performance-measurement-1299-1.nym.pnap.net" with the only differences being the numbers in the name and a different sub-domain.
I'm already blocking these request so I am good there and the only other option I am aware of is to take a chance on my ISP's paid support which is $15 a call.
So I am wondering, what would you the experts do in this situation?
-
Why not just change your IP? Do you still see this traffic? BTW 9 times a second is a pretty lame attempt at attack ;) 9000, 90000 then yeah be a bit concerned..
You could contact the owners of the netblock to do a whois on the source IP and email / call
I show it as
OrgAbuseHandle: IAC3-ARIN
OrgAbuseName: Internap Abuse Contact
OrgAbusePhone: +1-206-256-9500
OrgAbuseEmail: abuse@internap.com
OrgAbuseRef: https://rdap.arin.net/registry/entity/IAC3-ARINAsk them why that traffic is hitting your IP.
If your biggest concern is filling up your logs.. Just create a rule to drop it but not log it on your wan interface.
Someone prob typo'd the IP they were suppose to monitor ;)
-
@johnpoz said in ICMP Flooding - Need Advice:
Why not just change your IP? Do you still see this traffic?
Yup, forgot to mention that. I get a new IP every time the modem is restarted. I have done several restarts in the last few weeks to get a new IP thinking it would fix the issue. The ICMP request re-start almost immediately, usually anywhere from 5-30 minutes after the restart. That's actually one of the things bothering me about this. Seems like they are targeting the ISP's IP addresses.
BTW 9 times a second is a pretty lame attempt at attack ;) 9000, 90000 then yeah be a bit concerned
Good to know, sounds like its not as bad as what I was assuming it to be. I have considered that maybe its not malicious considering the domain name but then again I've only seen this the past few weeks so it's out-of-the-norm.
You could contact the owners of the netblock to do a whois on the source IP and email / call
I do have this info, I just wasn't sure if they would be safe to call if there intent is malicious in nature.
If your biggest concern is filling up your logs.. Just create a rule to drop it but not log it on your wan interface.
I have considered this option as well but wanted to get advise here first from those that have dealt with similar situations.
Sounds like you are suggesting it's not an attack and not much to worry about. I'll take your advice and contact Intermap and create a rule so its not logged in the router.
While we are on this subject, should I even be blocking ICMP on the WAN? There is alot of info on the web with some saying you should and others saying you shouldn't due to things like MTU discovery.
-
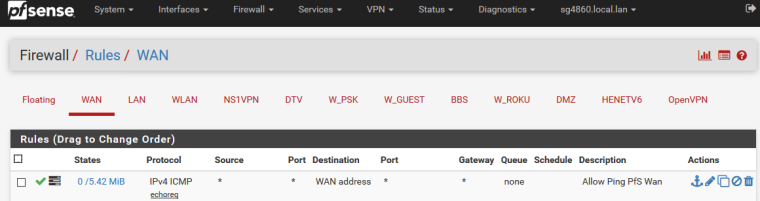
I allow ping to my wan... Its how I can tell if my home internet is up ;)
So I have monitoring setup from outside services that ping my home IP.. And then then it tells me if down.. So yeah its fine to allow ping..
You might even find that once you allow a response that it pinging you 9 times a second drops off.. But sure there is nothing wrong with contacting them to see if they are doing it on purpose you can ask them the purpose, etc.. Maybe they have some deal with your isp? etc..
If you were allowing it - you wouldn't see it in your block log ;)
-
This post is deleted! -
I don't even monitor unsolicited traffic unless the port in question is important. Too much noise from all of the port scanners and what-not. Out of sight and out of mind. pfSense made me paranoid for a while before I had a revelation. This is all normal, I was just never aware of it before.
-
The firewall can only block undesired traffic. It can't stop upstream from sending it to you in the first place.
You can either log it or not log it. Your choice.
Personally, I allow pings to WAN from any.
-
@johnpoz , @Harvy66 , @Derelict Thanks for all of the info and your advise, just what I was looking for. So much info on the web with differing view points and approaches. Makes it hard to digest it all when your trying to learn something new and when it comes to online security and all of its inner workings, well there is a lot to learn.
@harvy66 said in ICMP Flooding - Need Advice:
pfSense made me paranoid for a while before I had a revelation. This is all normal, I was just never aware of it before.
I got a good chuckle out this because (1.) I could see this remark in some meme and (2.) this is what pfSense has done to me as well. I am however starting to come to the same revelation. It's been an eye opener to say the least. I honestly never really messed around with any of my ISP routers aside from opening some ports. Whole different story with pfSense though.
@johnpoz said in ICMP Flooding - Need Advice:
You might even find that once you allow a response that it pinging you 9 times a second drops off..
Maybe they have some deal with your isp? etc..
Funny enough, I was actually thinking about both of these scenarios before you posted.
Given I have no doubts that you all know what you are doing, I'll take your advice and allow ICMP and see how it works out.
Now I just have to figure out what I should log and not log. I have thought about this for a while but still haven't come up with a plan of action so I am still using the defaults. On one hand I am thinking, why log blocked traffic, if its not getting through then the firewall is doing its job and doesn't necessarily need to be seen as it will only add to my paranoia. On the other hand however something on the network might not work as expected or I might not have access to a website and will want to see what is being blocked.
Same kinda goes for allowed traffic, if I log allowed my logs will fill up pretty quick but at the same time it would be good to see just what exactly is getting through and whats talking to what. I've also thought maybe I should not log any traffic at all and only turn on logging if I am having an issue. LOL, what I should probably do is just leave it alone and stop looking! Alot to consider really and no clear examples on the web that I have found so far. Definitely going to require some more thought on my part.
-
I log the interesting traffic... So for starters I want to know what my IOT stuff is doing.. So I log their vlans for outbound traffic.
On the wan - yeah it can be noisy.. But I do like to see directed unsolicited traffic, so I log just that SYN's to my wan IP.. Its more just curiosity sort of thing... Like for example when all those routers got taken offline like a million of them in DE alone shitton of noise being seen on 7547.. Yeah I was seeing that as well ;)
Your typical noise ports are the common 22, 23, 3389, 1433, etc.. All well known script/bot traffic looking for shit to exploit.. Its noise - but it is interesting to see how much of it gets dropped..