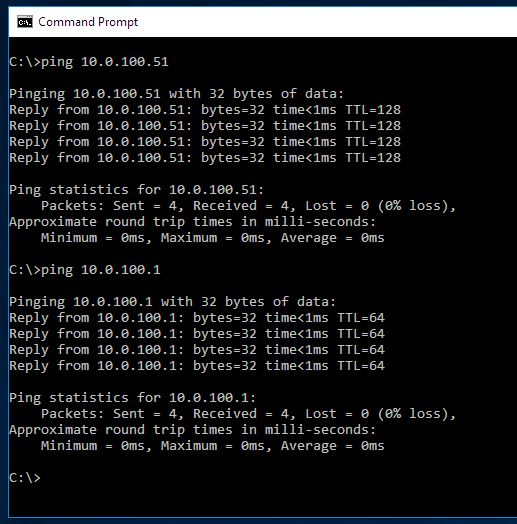
I can ping PFSense but PFSense can't ping back
-
Client firewalls? If you changed anything such as your LAN subnet your desktops will change to "public" and block everything.
Even changing an interface on your router could trigger that.
https://www.netgate.com/docs/pfsense/nat/port-forward-troubleshooting.html
As you eluded to in your first post- once you figure out why your port forward does not work you will most likely also fix the ping.
-
If you can ping one way and not the other it is almost certainly a firewall on the device you cannot ping blocking it. One way ping success proves two-way traffic, routing (for the most part in most cases), and layer 2 are correct.
-
-
I would prefer not to change my link speed. It is currently running at 1000. If I switch it down to 10 or 100, I would be limiting my access to my internet as my internet connection is currently rated for 300. Additionally, this was working previously under the current link state, so I would be surprised if this would resolve anything. What is your rationale for checking this?
-
Tried a different cable, no change in results.
-
Tried connecting a device directly to pfsense. No change in results.
-
Subnet Mask is set to 255.255.255.0 in DHCP and aligns with the client.
-
-
@chpalmer I thought it could be client side firewall too. I normally leave those disabled on my internal LAN as they just cause unnecessary trouble. I have confirmed and they are still off.
-
Then you'll have to packet capture to see the pings going out and nothing coming back, look at the MAC addresses, etc.
-
@striker-0
Reducing the connection speed is just a test
I am very confused by the line in ping test
255.255.255.0 > 10.0.100.51: ICMP echo request, id 16367, seq 0, length 64
( I don't know what's the subnet mask )Should be so
length 98: 192.168.1.1 > 192.168.1.230: ICMP echo request, id 30542, seq 0, length 64
length 98: 192.168.1.230 > 192.168.1.1: ICMP echo reply, id 30542, seq 0, length 64
length 98: 192.168.1.1 > 192.168.1.230: ICMP echo request, id 30542, seq 1, length 64
length 98: 192.168.1.230 > 192.168.1.1: ICMP echo reply, id 30542, seq 1, length 64Can you put the packet capture file here ?
-
@derelict I have confirmed the firewall is off. This issue occurs across all devices on my network, the only constant is pfsense. Additionally, within my network other devices can ping each other and I can connect to the port I am trying to forward. Something is going on with pfsense or the hardware it resides on.
-
@striker-0
And another question - how much do you have active NORDVPN tunnels ?
if you turn them off, will anything change ? -
@striker-0 said in I can ping PFSense but PFSense can't ping back:
255.255.255.0 > 10.0.100.51:
That is NOT right it sould be pinging from pfsense IP on that 10.0.100 network..
re0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=82098<VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,WOL_MAGIC,LINKSTATE> capabilities=18399b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,TSO4,WOL_UCAST,WOL_MCAST,WOL_MAGIC,LINKSTATE,NETMAP> ether 00:11:09:d7:2b:fa hwaddr 00:11:09:d7:2b:fa inet6 fe80::211:9ff:fed7:2bfa%re0 prefixlen 64 scopeid 0x2 inet 10.0.100.1 netmask 0xffffff00 broadcast 10.0.100.255 nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> media: Ethernet autoselect (1000baseT <full-duplex,master>) status: activeThat is the IP it should be pinging from 10.0.100.1
-
@striker-0 Post a packet capture taken on each interface of pings that work and pings that fail.
-
@konstanti at the moment, my NORDVPN tunnel is down. I see no difference in activity when the tunnel is up or down.
-
@johnpoz
All this is very strange, because of the webgui
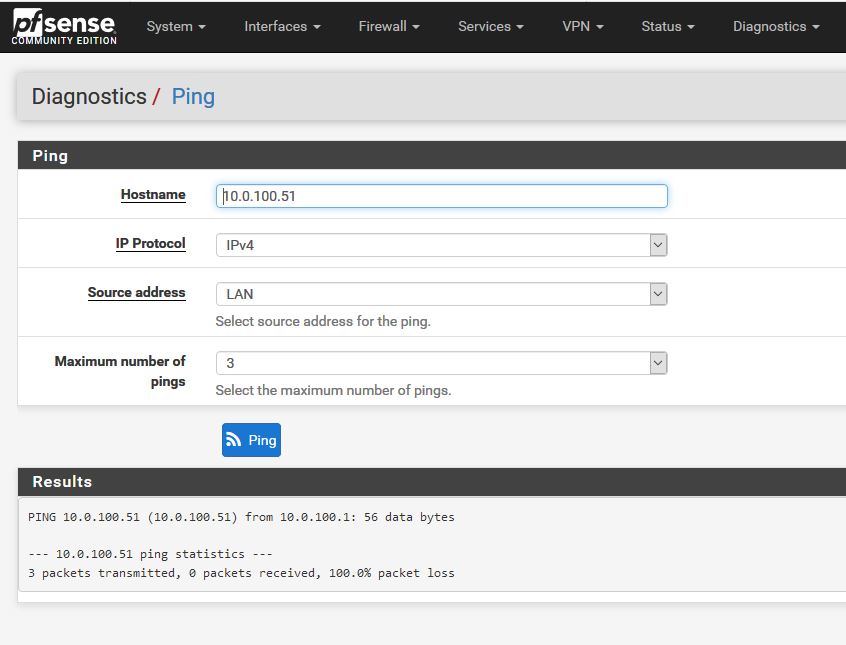
pfsense is also forming a command
/ sbin/ping -S 10.0.100.1 -c 3 10.0.100.51 (as seen in the picture)
and tcpdump shows another -
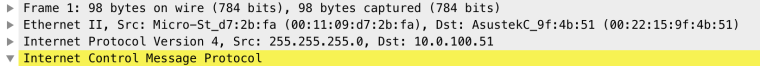
@derelict Here is a packet capture from pfsense where I tried to ping 10.0.100.51 on the LAN interface and it failed.
12:47:22.869939 00:11:09:d7:2b:fa > 00:22:15:9f:4b:51, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 14477, offset 0, flags [none], proto ICMP (1), length 84)
255.255.255.0 > 10.0.100.51: ICMP echo request, id 49230, seq 0, length 64
12:47:23.875326 00:11:09:d7:2b:fa > 00:22:15:9f:4b:51, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 41292, offset 0, flags [none], proto ICMP (1), length 84)
255.255.255.0 > 10.0.100.51: ICMP echo request, id 49230, seq 1, length 64
12:47:24.877890 00:11:09:d7:2b:fa > 00:22:15:9f:4b:51, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 38991, offset 0, flags [none], proto ICMP (1), length 84)
255.255.255.0 > 10.0.100.51: ICMP echo request, id 49230, seq 2, length 64pfsense packet capture doesn't seem to capture any packets when I ping from my workstation to the server even with the use of promiscuous mode. Any suggestions on a tool to capture the information you are looking for?
-
Need a file that you download after clicking " Download capture"
-
@konstanti capture download attached. Forums wouldn't accept a .cap file, so I zipped it.
-
Great. What are we looking at?
-
its pinging from 255.255.255.0 - so no that is never going to work.
-
-
It looks like you have what should be a netmask somewhere that should be an address. As was said earlier, this makes no sense:
Source: 255.255.255.0
What interface is that capture taken on?
The only thing that could do that that I can think of is Outbound NAT on that interface being completely misconfigured. Outbound NAT would also only affect traffic in that direction.
-
@derelict That is a packet capture taken while performing a ping command from the LAN interface to 10.0.100.51.
The packet capture was capturing ICMP IPV4 traffic activity from the LAN interface with the promiscuous setting enabled and set to capture full detail.