SG-1100 Running Real VLANs
-
-
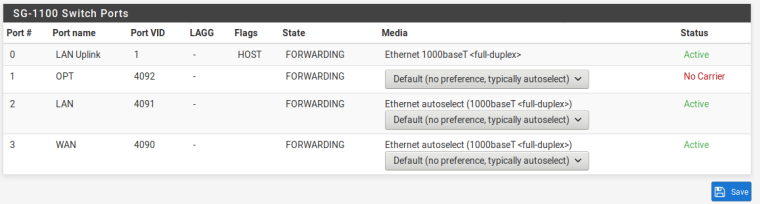
That all looks fine for managing that AP on a LAN address if it is connected to port 2.
Anything in the DHCP logs? DHCP has automatic rules for any interface with a DHCP server enabled.
Based on what you have posted I'd look at the DHCP logs and packet captures on UDP port 67.
Does the smooth network work?
-
Nothing showing up in the DHCP logs then I try to connect to the Work or Guest network. I can connect just fine to the regular Smooth network, clients connect and get a DHCP address. Port two is connected to a switch. I had a similar setup working with untangle, just want to make the jump to pfsense.
-
Well, you have to tag VLANs 10 and 20 through to the AP on the switch on the ports connected to pfSense and the AP.
-
If the L2 is setup correctly check the L3. How are the networks configured, a common beginner mistake is to use the default /32 CIDR for example.
-
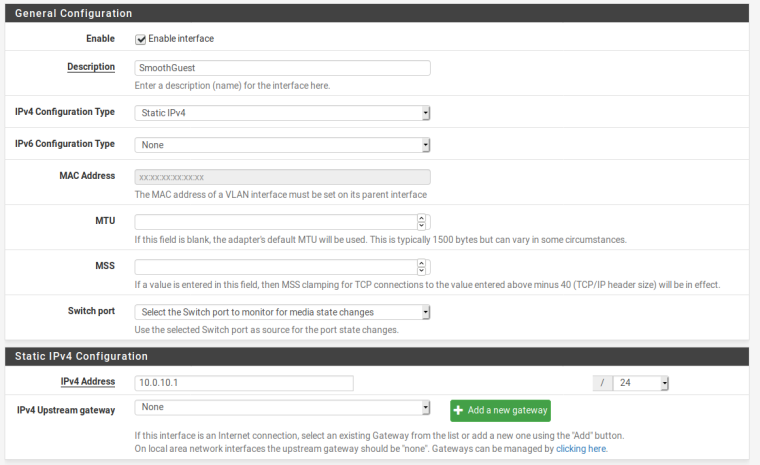 Yep, doublechecked /24
Yep, doublechecked /24and vlan set on the switch port
-
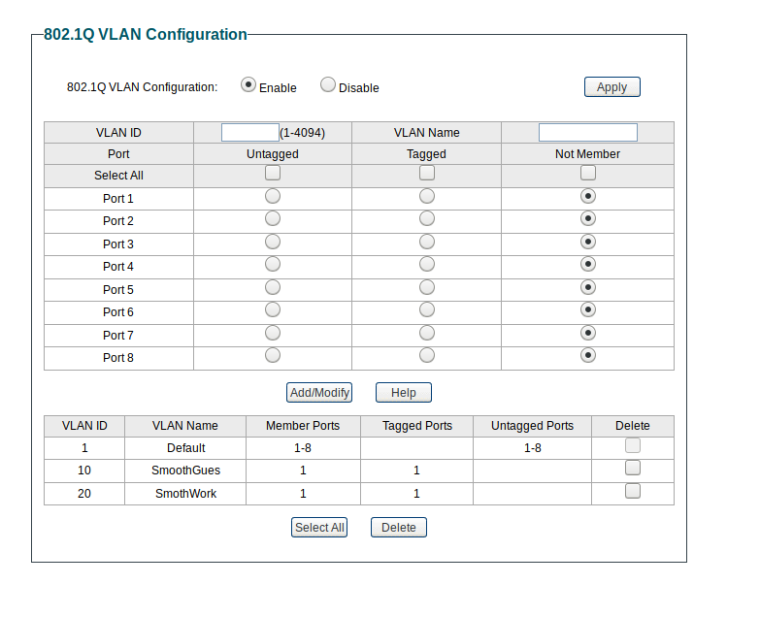
OK. On what switch port are 10 and 20 tagged to the AP?
-
All to port 1
-
OK, on what port are 10 and 20 tagged to pfSense port 2?
-
Not sure I follow, are you talking about the switch on the sg-1100?
-
No. What switch port on your switch is connected to pfSense port 2? That port needs 10 and 20 tagged as well.
-
Brilliant! Ok well that was easy. That worked. Thanks for all your help!
-
@pfsmooth Tag 10 and 20 on switch port 2 and I think you will be pleased with the results.
-
Well all was running smooth for a while, had it all set up and all of a sudden I get flooded with " Default deny rule IPv4 (1000000103) " and things like my plex server wont allow external connections. If I rebuild pfsense from scratch it is fine until i add the vlans. Then boom plex falls off. Any ideas?
-
From that description, no. Not enough information.
-
Not sure if I should start a new thread. But basically the port forwarding is not working directly to 32400. I have set the NAT rule and the FW rule with no luck. A search shows this pops up often but I haven't been able to pin down a solution.
-
That would probably be better in a NAT thread. If pfSense is both receiving the traffic to be forwarded on WAN (verified by Diagnostics > Packet Capture on WAN) and can Diagnostics > Test Port to the address/port it is being forwarded to, then you likely did the port forward incorrectly.
-
your switch only shows port 1 with tagged vlans on it, where is the port connecting to pfsense?
Your vlans will have to be tagged on the port going to pfsense, and the port going to AP.
How is everything connected exactly? What is the point of tagging vlans to your what looks like a sg108e if no other ports are using those vlans, and no other uplink to another device like AP that is tagged?
-
Thanks John, yes. I figured out that the port pfsense was plugged into needed to be tagged to the same vlan as the port the AP was plugged into. All good there.
-
I fell over this as I restored a backup to a new SG-1100 and seem to have "preserve switch config" active.
So I kept the underlying VLANs 4090-4092 as intended but my other VLANs from the backup weren't applied, as far as I understand.Could someone point me to some information what that column "Members" in the VLAN table means exactly?
I'd like to understand that and not only blindly fill in "0t,2t" there, thanks !