I want to block Facebook from certain clients on my network.
-
Also don't forget that when you add a new firewall rule to block something, if that "something" was formerly being allowed (passed), then a state will exist in the firewall's state table. A state table entry for a session means that traffic is allowed so long as the state exists. You need to clear any existing states for that client.
But even doing what I said above is not a sure-fire fix. As @marvosa pointed out, there are thousands of Facebook CDN IP addresses your client may get served up by DNS. You would just have to hope your list of Facebook IP ranges is complete. Just be aware they likely change, though, as deals are made across the web for server space. IPv4 addresses are bought and sold everyday now almost like stocks because the space is officially exhausted and the price for IPv4 addresses has soared. Thus companies that have some extra are frequently willing to sell space to someone else for a nice profit.
-
@bmeeks How up to date would a list be based on a companies BGP data? I have used api.bgpview.io in some simple python scripts to poke around and create network lists for FaceBook and others. That data changes over time. I haven't looked closely enough to say the API provides real-time up to date data.
The OP can use pfblocker (which I think uses the same API) to create an alias off of the 3 facebook ASNs (63293,541115,32934) and then write rules as needed...Edited to add: I just installed pfbocker and gave this a try. I'm not sure what pfblocker is doing but it doesn't give a complete list of networks, not even close. It also throws an error if you try to do more than one ASN at a time in the custom list.
Noticed the OP maybe isn't blocking facebooks ipv6 addresses, can't tell for sure as the list is cut off. The rule is v4+v6 but does the alias contain the v6 addresses? If not, that's your problem.
-
@jwj said in I want to block Facebook from certain clients on my network.:
@bmeeks How up to date would a list be based on a companies BGP data? I have used api.bgpview.io in some simple python scripts to poke around and create network lists for FaceBook and others. That data changes over time. I haven't looked closely enough to say the API provides real-time up to date data.
I think the main issue is just staying current with what is actively in use. Once you get to the "big boys" like the social media sites, there are a lot of CDN things happening. I suspect they have both their own stuff and then perhaps contracts with others as well. It's keeping up with those "others" that gets difficult.
While you can make it aggravating for users to access Facebook and other such large sites, you can't make it 100% unreachable 100% of the time unless you simply pull your connection to the web entirely. Making it aggravating is sometimes enough to discourage them trying. I just point this out in my posts on topics like this so that users realize you can't simply block one or two IP addresses and call it done to block Facebook, YouTube, Twitter, Netflix, etc. There are many newly minted firewall admins that seem to think that is the case based on the posts I've seen here on the forums over the years.
-
@bmeeks said in I want to block Facebook from certain clients on my network.:
unless you simply pull your connection to the web entirely.
That has it's appeal sometimes. ;)
You are, of course, right. It's not practical to 100% de-[facebook|google|amazon|netflix] our online experience.
-
@jwj said in I want to block Facebook from certain clients on my network.:
It's not practical to 100% de-[facebook|google|amazon|netflix] our online experience.
I ran across a firefox addon the other day - one sec let me see if dig it up..
https://addons.mozilla.org/en-US/firefox/addon/cloud-firewall/
Block connections to pages and web resources hosted in major cloud services if the user wishes to do so. Supports blocking Google, Amazon, Facebook, Apple, Microsoft and Cloudflare.Cloud Firewall is a browser extension/addon that allows users to block connections to sites, pages and web resources (images, videos, etc) hosted in major cloud services if the user wishes to do so.
Most of the net becomes useless if you block the major players ;)
-
Yeah, you certainly can block such sites on the browser end, and likely quite reliably. That's because there, the browser can afford to wait a few seconds and do some DNS queries realtime and make a decision on what to show.
Not so easy to be realtime farther down the network pipe at say the firewall end of things. Too much latency if you do realtime lookups on every connection. So the next best thing is falling back to periodic domain lookups and refreshing aliases like pfSense does. But this then leads to the issue of short TTL values on host records and the possibility the firewall's "current" IP address for Facebook differs from what a local client just asked for and received.
-
Yup all true.. My point was more to the fact that blocking such stuff even if easy peasy.. Pretty much renders the internet useless..
So if you could just block anything.facebook.com - when you start blocking CDNs and netblocks, full ASNs - you have no idea what else might be hosted on those IPs, etc.
Now your browsing experience becomes a pile of trash ;)
-
@roy360 said in I want to block Facebook from certain clients on my network.:
I don't need a fool proof block that prevents proxys and stuff from working. I just want to block a list of IPs I know belong to Facebook, and then track traffic that DOES pass through.
I don't know what client devices you are dealing with or what type of environment you have but Screen Time works very well with Apple devices. You can block or limit Facebook access from the app and in safari. This is easy at home, not so much in other situations. I don't know (haven't looked) if there is an android or windows equivalent.Not knowing your situation means this may not be at all useful to you.Actually, as you have figured out that alias and ntopng you know about Screen Time and me pointing it out is simply insulting. Sorry.
-
@marvosa said in I want to block Facebook from certain clients on my network.:
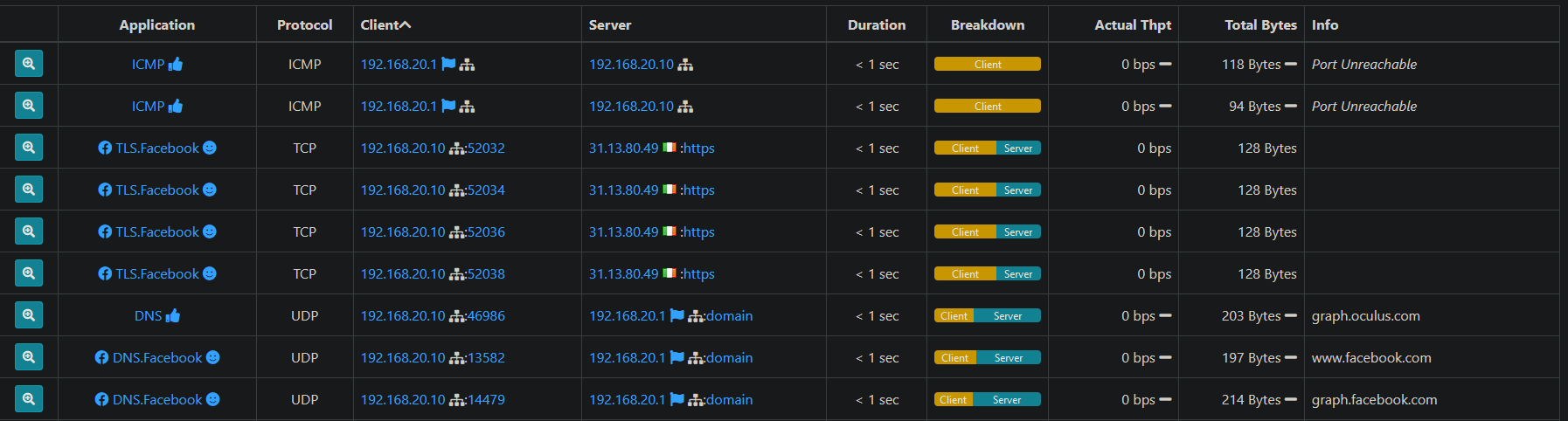
@roy360 Facebook owns 100,000+ IP's. Have you confirmed 31.13.80.0/21 is included in your "BlockFaceBook" alias?
That's whats puzzling me. I definitely have that IP in that alias, so I'm not sure why my rule isn't catching it.
@bmeeks said in I want to block Facebook from certain clients on my network.:
Also don't forget that when you add a new firewall rule to block something, if that "something" was formerly being allowed (passed), then a state will exist in the firewall's state table. A state table entry for a session means that traffic is allowed so long as the state exists. You need to clear any existing states for that client.
But even doing what I said above is not a sure-fire fix. As @marvosa pointed out, there are thousands of Facebook CDN IP addresses your client may get served up by DNS. You would just have to hope your list of Facebook IP ranges is complete. Just be aware they likely change, though, as deals are made across the web for server space. IPv4 addresses are bought and sold everyday now almost like stocks because the space is officially exhausted and the price for IPv4 addresses has soared. Thus companies that have some extra are frequently willing to sell space to someone else for a nice profit.
I do realize that this block will not work completely, which is why I plan on monitoring traffic that does go through and updating my rules periodically.
@jwj said in I want to block Facebook from certain clients on my network.:
@bmeeks How up to date would a list be based on a companies BGP data? I have used api.bgpview.io in some simple python scripts to poke around and create network lists for FaceBook and others. That data changes over time. I haven't looked closely enough to say the API provides real-time up to date data.
The OP can use pfblocker (which I think uses the same API) to create an alias off of the 3 facebook ASNs (63293,541115,32934) and then write rules as needed...Edited to add: I just installed pfbocker and gave this a try. I'm not sure what pfblocker is doing but it doesn't give a complete list of networks, not even close. It also throws an error if you try to do more than one ASN at a time in the custom list.
Noticed the OP maybe isn't blocking facebooks ipv6 addresses, can't tell for sure as the list is cut off. The rule is v4+v6 but does the alias contain the v6 addresses? If not, that's your problem.
My list was creating using this command:
whois -h whois.radb.net -- '-i origin AS32934' | awk '/^route:/ {print $2;}' | sort | uniq===group
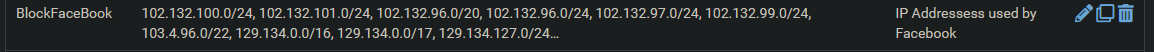
The full list is below:
||102.132.100.0/24
102.132.101.0/24
102.132.96.0/20
102.132.96.0/24
102.132.97.0/24
102.132.99.0/24
103.4.96.0/22
129.134.0.0/16
129.134.0.0/17
129.134.127.0/24
129.134.25.0/24
129.134.26.0/24
129.134.27.0/24
129.134.28.0/24
129.134.29.0/24
129.134.30.0/23
129.134.30.0/24
129.134.31.0/24
129.134.64.0/24
129.134.65.0/24
129.134.66.0/24
129.134.67.0/24
129.134.68.0/24
129.134.69.0/24
129.134.70.0/24
129.134.71.0/24
129.134.72.0/24
129.134.73.0/24
129.134.74.0/24
129.134.75.0/24
129.134.76.0/24
147.75.208.0/20
157.240.0.0/16
157.240.0.0/17
157.240.0.0/24
157.240.1.0/24
157.240.10.0/24
157.240.11.0/24
157.240.12.0/24
157.240.13.0/24
157.240.14.0/24
157.240.15.0/24
157.240.16.0/24
157.240.17.0/24
157.240.18.0/24
157.240.19.0/24
157.240.192.0/18
157.240.192.0/24
157.240.193.0/24
157.240.194.0/24
157.240.195.0/24
157.240.196.0/24
157.240.197.0/24
157.240.198.0/24
157.240.199.0/24
157.240.2.0/24
157.240.20.0/24
157.240.200.0/24
157.240.201.0/24
157.240.203.0/24
157.240.204.0/24
157.240.205.0/24
157.240.206.0/24
157.240.207.0/24
157.240.208.0/24
157.240.209.0/24
157.240.21.0/24
157.240.210.0/24
157.240.211.0/24
157.240.212.0/24
157.240.213.0/24
157.240.214.0/24
157.240.215.0/24
157.240.216.0/24
157.240.217.0/24
157.240.218.0/24
157.240.219.0/24
157.240.22.0/24
157.240.220.0/24
157.240.221.0/24
157.240.222.0/24
157.240.223.0/24
157.240.224.0/24
157.240.225.0/24
157.240.226.0/24
157.240.227.0/24
157.240.228.0/24
157.240.229.0/24
157.240.23.0/24
157.240.239.0/24
157.240.24.0/24
157.240.25.0/24
157.240.26.0/24
157.240.27.0/24
157.240.28.0/24
157.240.29.0/24
157.240.3.0/24
157.240.30.0/24
157.240.31.0/24
157.240.5.0/24
157.240.6.0/24
157.240.7.0/24
157.240.8.0/24
157.240.9.0/24
173.252.64.0/18
173.252.64.0/19
173.252.88.0/21
173.252.96.0/19
179.60.192.0/22
179.60.192.0/24
179.60.193.0/24
179.60.194.0/24
179.60.195.0/24
185.60.216.0/22
185.60.216.0/24
185.60.217.0/24
185.60.218.0/24
185.60.219.0/24
185.89.216.0/22
185.89.218.0/23
185.89.218.0/24
185.89.219.0/24
204.15.20.0/22
31.13.24.0/21
31.13.64.0/18
31.13.64.0/19
31.13.64.0/24
31.13.65.0/24
31.13.66.0/24
31.13.67.0/24
31.13.68.0/24
31.13.69.0/24
31.13.70.0/24
31.13.71.0/24
31.13.72.0/24
31.13.73.0/24
31.13.74.0/24
31.13.75.0/24
31.13.76.0/24
31.13.77.0/24
31.13.78.0/24
31.13.79.0/24
31.13.80.0/24
31.13.81.0/24
31.13.82.0/24
31.13.83.0/24
31.13.84.0/24
31.13.85.0/24
31.13.86.0/24
31.13.87.0/24
31.13.88.0/24
31.13.89.0/24
31.13.91.0/24
31.13.92.0/24
31.13.93.0/24
31.13.94.0/24
31.13.95.0/24
31.13.96.0/19
45.64.40.0/22
66.220.144.0/20
66.220.144.0/21
66.220.152.0/21
69.171.224.0/19
69.171.224.0/20
69.171.239.0/24
69.171.240.0/20
69.171.250.0/24
69.171.255.0/24
69.63.176.0/20
69.63.176.0/21
69.63.178.0/24
69.63.184.0/21
74.119.76.0/22||I did not have any v6 addresses in the alias. For now, I've setup a rule to block all IPv6 traffic for the devices I'm trying to restrict.
-
This grabs the both the ipv4 and ipv6 networks.
whois -h whois.radb.net -- '-i origin AS32934' | awk '/^route6*:/ {print $2;}'
Not sure what's going on with your rule. I'll mess with this this weekend. Would be nice to have something that periodically updates.
Edited 2-27 to add: The web service I want to use (https://api.bgpview.io/asn/asn to look up/prefixes) is 'Service Temporarily Unavailable' so that approach will have to wait for another time. Not a good sign for reliability...
I did write a quick script to drop the ipv4 and ipv6 prefixes for all three facebook ASNs using, whois -h whois.radb.net -- '-i origin ASxxxxx' | awk '/^route6*:/ {print $2;}', into /usr/local/www and then created two URL table aliases from those files (I did one for v4 and another for v6). Ran the script from a cron job and that looks to work OK.
I'll revisit this sometime in the future.