segment wifi traffic (guest, IoT, trusted)
-
@farmerjohn said in segment wifi traffic (guest, IoT, trusted):
According to this video , I don't need a managed switch to have multiple vlans via wireless AP and pfsense.
I haven't watched that video, but you don't need a managed switch to support mulitple SSIDs on an AP. However, if you have wired devices on those VLANs, you will need a managed switch, as many devices can't be configured to use VLANs.
-
I have one of those Netgear GS108Ev3 8 port switches, bought it many years ago, well under 50 bucks if memory isn't way off. Works fine for a home use product. Also have a Netgear GS724Tv4 which is the basically the same thing but with 24 ports. Paid 330 maybe 6 years ago, which again isn't bad if you need that many ports and just need the vlans and aren't looking to study to take Cisco classes. They work just fine in my application, using PFSense to do the routing and firewall between the vlans, with two Unifi WAPs that support multiple SSIDs/VLANs which made the whole setup painless.
-
if you have wired devices on those VLANs, you will need a managed switch, as many devices can't be configured to use VLANs.
If I have a VLAN capable AP connected to an unmanaged switch with 3 other wired devices (don't need these wired devices to be vlan tagged) and this unmanged switch connects to pfsense, will the AP traffic that is tagged match up with the VLAN's I have defined in pfsense and the 3 wired devices work as before, i.e., just LAN members?
-
Yes, I used to do that here. The unmanaged switch will pass the VLAN tagged frames, so that the AP can sort things out. Wired devices that can't be configured to work directly with VLANs will still work on the native LAN and will ignore the tagged frames. Computers can be configured to work directly with VLANs.
-
While you can do that.. Understand that dumb switch doesn't understand vlans.. So there is no isolation. All the broadcast and multicast traffic from all the vlans as soon as hits switch will go to all the other ports.
While your dumb switch will pass the vlan tags.. Since he doesn't understand them doesn't know that broadcast/multicast traffic from vlan X, is not suppose to go to all the ports.
If your doing it that way because you can not afford say $30-50 switch... You shouldn't be running so many freaking devices in the first place. I mean the electric cost alone must eat up your whole budget ;)
Give up couple $10 coffee's at starbucks and get a switch that actually understands vlans.
-
@johnpoz said in segment wifi traffic (guest, IoT, trusted):
So there is no isolation. All the broadcast and multicast traffic from all the vlans as soon as hits switch will go to all the other ports.
There is some isolation in that the devices won't receive the packets for other VLANs. They will appear at the NIC, where they will be promptly ignored.
-
So there is no isolation. All the broadcast and multicast traffic from all the vlans as soon as hits switch will go to all the other ports.
seems not optimal, but what is the downside to this? will this cause a noticeable hit to network performance or other issues?
-
The downside is your sending broadcast/multicast to somewhere it doesn't need to go.
While the nic might drop it. You also can join any vlan you want with any device just be tagging. So no security at all.
If your to the point you wanting to segment your network into different vlans, yet not willing to spend the few bucks required to do it correctly - your doing it F'ing Wrong! ;)
If its a stop gap until your smart switch gets delivered, or you want to do it on purpose as say a easy tap into viewing traffic.. Or your using the dumb switch as sort of relay to extend length of a run or something.. Sure ok..
While there may be some scenarios you need/want to do it - overall its a borked way to do it.
There is one correct answer to want to run vlans on a switch - the switch should understand the tags ;) It doesn't need to be some super managed everything under the sun sort of networking magic that can be done sort of switch.. But it should at least understand what the tag is, and how to process them and isolate them correctly.. So that you actually get the L2 isolation that vlans are meant to do..
-
It will waste some bandwidth on the wire, but devices will not recognize packets on a VLAN they're not configured for. Those packets will be discarded by the NIC.
-
@johnpoz said in segment wifi traffic (guest, IoT, trusted):
You also can join any vlan you want with any device just be tagging. So no security at all.
Assuming:
a) You have admin rights¹ and
b) Know how to do that- Yeah, I know many people run their computers as admin because they don't know better and that's the way it came.
-
@farmerjohn
I totally agree w. @johnpoz here.
Get a cheap managed switch for the job.
As a "bonus" you could use the 6 other ports for other vlans, and treat it as an additional 6 Lan interfaces.@jknott
Just because you could ... Doesn't mean you should.
And certainly not for saving $50/Bingo
-
I suppose you're thinking about dd-wrt
Hw-Rev A1
https://wiki.dd-wrt.com/wiki/index.php/Asus_RT-AC66UHw-Rev B1
https://wiki.dd-wrt.com/wiki/index.php/Asus_RT-AC66U_B1 -
There might be some "Trickery" in connecting the managed switch to the Lan IF , and enable tagging , wo. loosing Lan (that you need for configuring).
I suppose you could keep Lan as untagged.
Maybe one of the others have trued to run untagged & tagged on a pfS IF.
I haven't yet/Bingo
-
@bingo600 said in segment wifi traffic (guest, IoT, trusted):
Maybe one of the others have trued to run untagged & tagged on a pfS IF.
I run one of my interfaces with native (untagged) and then vlans on it.. There really isn't anything tricky about ;)
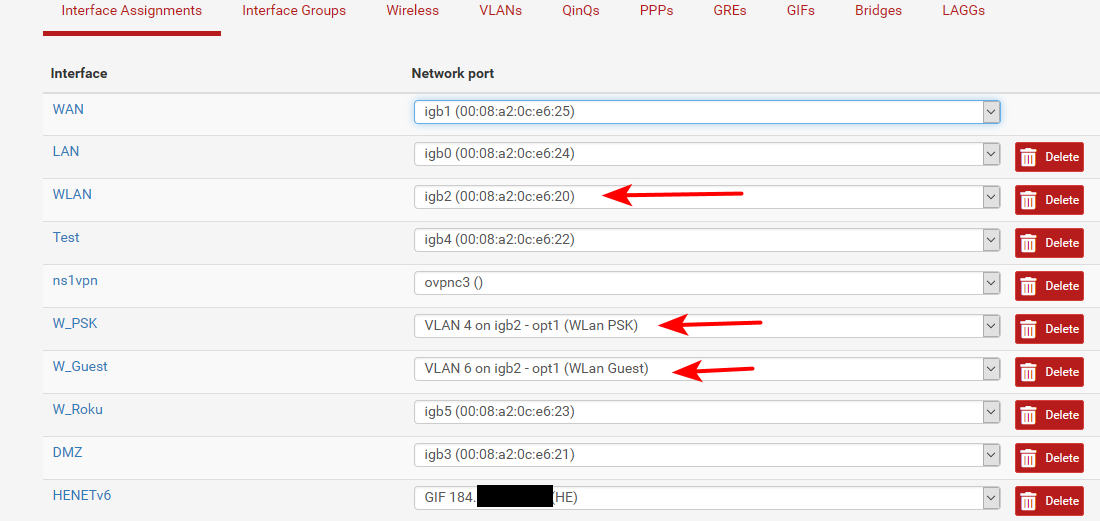
You can see that native network my wlan is untagged and on the igb2 interface. While then 2 other networks (vlans) are on that physical interface igb2
-
@bingo600 said in segment wifi traffic (guest, IoT, trusted):
Maybe one of the others have trued to run untagged & tagged on a pfS IF.
I haven't yetThat's what I have here. My guest Wifi is connected via VLAN3 and the main Wifi is on the native LAN. This is quite common with things like VoIP phones and office computers. On the pfsense end, once the VLANs are enabled, there's no difference with a native LAN when configuring them.
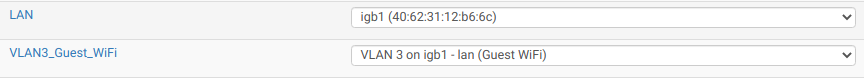
-
I suppose you're thinking about dd-wrt
That was my original plan, but also considering a Ubiquity UAP-AC-PRO - not sure if flashing and configuring the Asus router will be as simple as buying a Ubiquity.
-
I like the UAP AC Pro

I have 5 sites with that model installed.Then i also assume that $50 for a Vlan switch isn't an issue.
/Bingo
-
There is one correct answer to want to run vlans on a switch - the switch should understand the tags ;)
I currently have 3 unmanged switches in the house
one: trendnet TEG-S80G
two: HP procurve 1410-8GI'll be attaching the VLAN capable AP into one of the HP procurve switches - until I save up for a managed switch ;)
Are there advantages of replacing the other two dumb switches if I don't intend to run VLAN tagged traffic through them?
if so, I may go with a 3-pack of these Ubiquiti USW-Flex-Mini for $28 each.
-
@farmerjohn
I'd go for 8-port switches ...
Not that 5 wouldn't do , just that w. a 5 , you only have 4(3) for user ports , as the other 1(2) would be used for uplink(s)The advantage of Vlan enabled switches around your house.
Would be that you could , "pull out" ie. a Guest or "IOT" ethernet port on any switch , if needed. Or you could attach a new "AP AC Pro" on "that" remote switch , if you need better coverage in that area.I'd only buy managed switches today, price diff is too small not to.
You could reuse your old "dumb" switches , if you have the need for many ports of the same type (vlan) - Just make one port on the managed switch a member of vlan xx , and connect the "dumb" switch to that port.
Now every port on the dumb switch will be a member of vlan xx./Bingo
-
You could reuse your old "dumb" switches , if you have the need for many ports of the same type (vlan)
Good to know - I'll probably go with 3 of the 5-port flex mini's and if I need to add more devices (same vlan), I'll attach one of my 8-port dumb switches.
But, found this in the unifi datasheet:
USW-Flex-Mini uses port-based VLANs only and does
not support SSH, STP (forwarding only), 802.1X, DNS
suffix, or experience in the controller.SSH is not an issue for me, but not sure about the other limitations.