Time is not syncing
-
[2.4.3-RELEASE][admin@pfsense]/root: ntpq -pn remote refid st t when poll reach delay offset jitter ============================================================================== 0.pool.ntp.org .POOL. 16 p - 64 0 0.000 0.000 0.000 1.pool.ntp.org .POOL. 16 p - 64 0 0.000 0.000 0.000 2.pool.ntp.org .POOL. 16 p - 64 0 0.000 0.000 0.000 3.pool.ntp.org .POOL. 16 p - 64 0 0.000 0.000 0.000 -2a01:7e00::f03c 85.199.214.98 2 u 334 512 377 10.483 -0.018 0.166 +185.182.62.7 85.199.214.102 2 u 92 512 377 9.679 -0.223 0.409 *87.242.168.84 .UPPS. 1 u 133 512 377 20.003 0.220 0.106 -2001:1b40:5000: 188.39.213.7 2 u 324 512 377 10.234 2.004 0.296 -83.137.225.103 193.190.230.66 2 u 199 512 377 10.425 0.849 0.296 +188.39.213.7 .GPS. 1 u 432 512 377 16.887 0.036 4.039 [2.4.3-RELEASE][admin@pfsense]/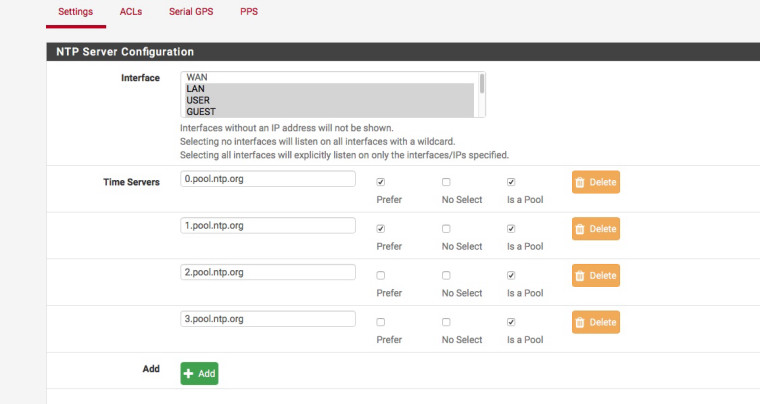
Works fine here, I know thats not of any help.
-
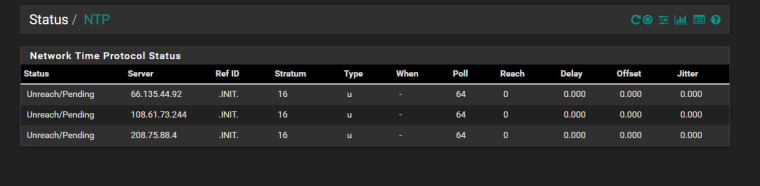
These are the results when I put the IP addresses directly in. Where do I find out what interface NTP is listening on?
-
Here's a link to my thread (that johnpoz mentioned) on the same problem:
https://forum.netgate.com/topic/131506/ntp-not-working-solved-mostly
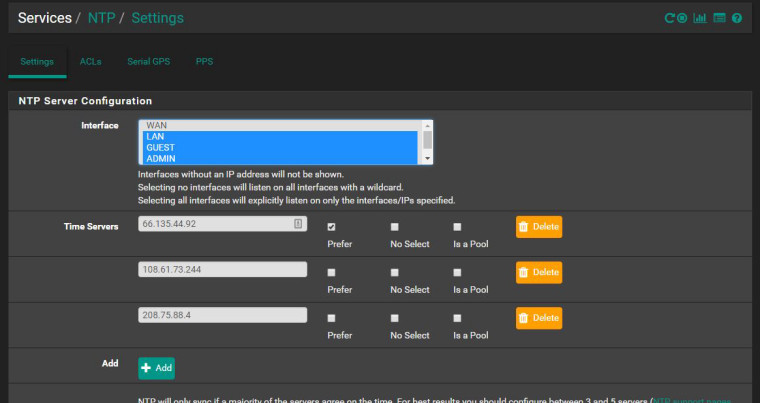
For me, I have to have WAN selected under Services > NTP in the Interfaces section. I've been utterly unable to find any reason for this since it shouldn't be necessary.
-
@beremonavabi said in Time is not syncing:
Here's a link to my thread (that johnpoz mentioned) on the same problem:
https://forum.netgate.com/topic/131506/ntp-not-working-solved-mostly
For me, I have to have WAN selected under Services > NTP in the Interfaces section. I've been utterly unable to find any reason for this since it shouldn't be necessary.
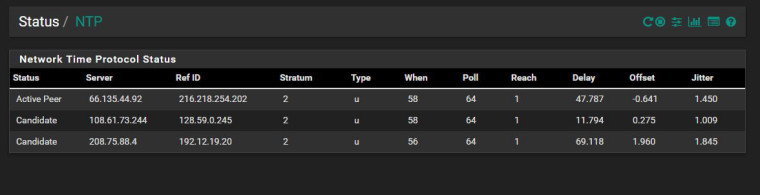
This solution worked for me. Thank you.
-
@brunovic
I don't like having my WAN selected for NTP to listen to. But, since that's the only way I've found to be able to get NTP to run, I guess I have to live with it. -
-
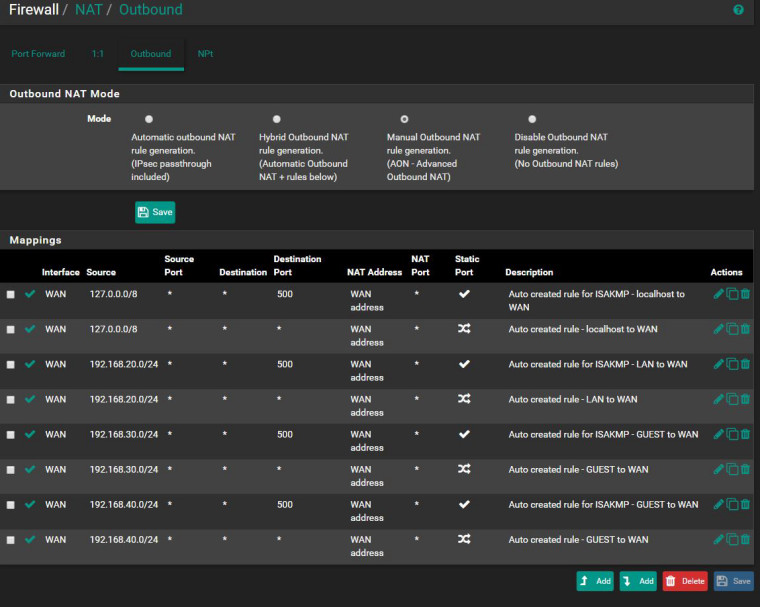
@johnpoz so it looks like my outbound NAT is manually configured. How will this prevent NTP from syncing?
-
@nogbadthebad said in Time is not syncing:
Does it now work ?
You both shouldn't need to have it listening on the WAN interface.
NTP will ONLY run on my SG-4860 if WAN is selected to listen to (the gory details of everything I've tried are in the thread I referenced, above). I agree that the WAN shouldn't be necessary. But, for no reason I can come up with, it turns out to be necessary in my case.
Looking over some of brunovic's other posts, it looks like he's using a VPN. I am, too. It's possible that's a relationship, but I just don't see why using a VPN might interfere with NTP.
-
@beremonavabi I use a VPN for remote access into my network but not for outbound traffic. Is that how you are using it?
-
@beremonavabi said in Time is not syncing:
@nogbadthebad said in Time is not syncing:
Does it now work ?
You both shouldn't need to have it listening on the WAN interface.
NTP will ONLY run on my SG-4860 if WAN is selected to listen to (the gory details of everything I've tried are in the thread I referenced, above). I agree that the WAN shouldn't be necessary. But, for no reason I can come up with, it turns out to be necessary in my case.
Looking over some of brunovic's other posts, it looks like he's using a VPN. I am, too. It's possible that's a relationship, but I just don't see why using a VPN might interfere with NTP.
I run a IKEv2 IPsec VPN ( inbound ) too I've got Automatic outbound NAT rule generation set.
-
@brunovic I've got OpenVPN clients running on my pfSense box to my VPN provider (AirVPN). I've also got a server running on it so our phones can use the VPN.
-
@beremonavabi ah no I am not using the client on my pfsense just the server.
-
@brunovic said in Time is not syncing:
@beremonavabi ah no I am not using the client on my pfsense just the server.
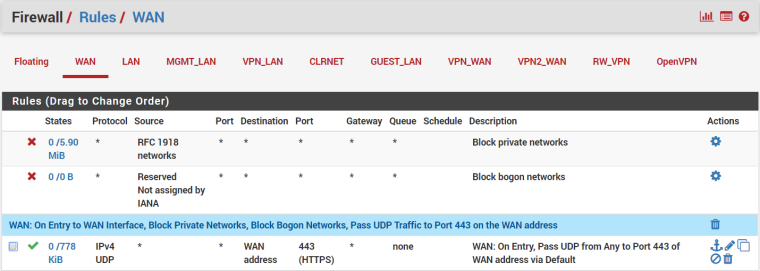
Well, an OpenVPN server commonality might be a start. Mine is listening on port 443. My firewall rules on the WAN look like:
Like you, my NAT rules are Manual. Outside of your specific ports, mine look similar:
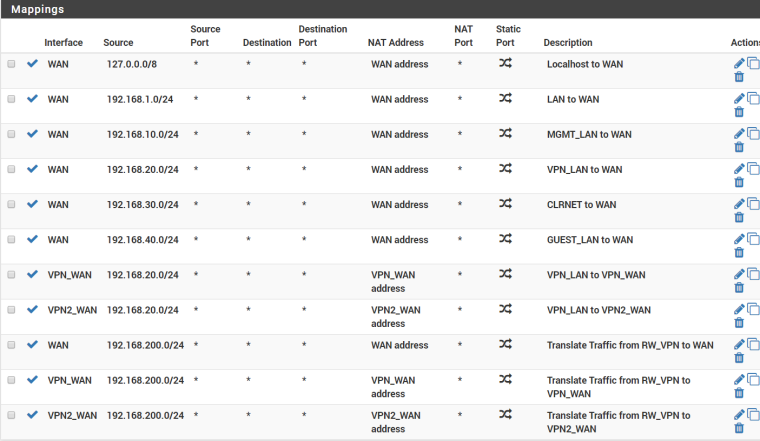
For DNS, I’m using DNS Resolver in NON-Forwarding mode. It’s active for all my local LAN-type interfaces (not WAN). Though, since I've checked with NTP using actual IP addresses instead of pool names (as you did), I can't see how this could be DNS related.
-
@beremonavabi said in Time is not syncing:
NTP will ONLY run on my SG-4860 if WAN is selected to listen
I have sg4860, I run both vpn servers on multiple instances 443 tcp, 1194 udp and also a vpn client connection to a vps out on the net running openvpn-as..
But I am NOT pulling routes from that connection and only policy route out to that vpn if need a client to take that path.. And I am NOT listening on the wan port and have zero issues with ntp talking to outbound ntp per previous screen shots.
So you clearly have something messed up in your configuration causing this problem there is zero reason that ntp should have to listen on wan to talk to ntp servers on the internet.
-
@johnpoz said in Time is not syncing:
@beremonavabi said in Time is not syncing:
NTP will ONLY run on my SG-4860 if WAN is selected to listen
I have sg4860, I run both vpn servers on multiple instances 443 tcp, 1194 udp and also a vpn client connection to a vps out on the net running openvpn-as..
But I am NOT pulling routes from that connection and only policy route out to that vpn if need a client to take that path.. And I am NOT listening on the wan port and have zero issues with ntp talking to outbound ntp per previous screen shots.
So you clearly have something messed up in your configuration causing this problem there is zero reason that ntp should have to listen on wan to talk to ntp servers on the internet.
I'm also not pulling routes. I'm mostly clueless about this, but my routes look fine, to me:
IPv4 Routes Destination Gateway Flags Use Mtu Netif Expire 0.0.0.0/1 10.4.0.1 UGS 16952 1500 ovpnc1 default [my WAN IP] UGS 34 1500 igb1 10.4.0.0/16 10.4.0.1 UGS 0 1500 ovpnc1 10.4.0.1 link#12 UH 371622 1500 ovpnc1 10.4.0.14 link#12 UHS 0 16384 lo0 10.8.0.0/16 10.8.0.1 UGS 0 1500 ovpnc2 10.8.0.1 link#13 UH 371535 1500 ovpnc2 10.8.0.27 link#13 UHS 0 16384 lo0 [my WAN net]/24 link#2 U 371654 1500 igb1 [my WAN IP] link#2 UHS 0 16384 lo0 127.0.0.1 link#7 UH 6821 16384 lo0 128.0.0.0/1 10.4.0.1 UGS 84534 1500 ovpnc1 192.168.1.0/24 link#1 U 0 1500 igb0 192.168.1.1 link#1 UHS 0 16384 lo0 192.168.10.0/24 link#3 U 0 1500 igb2 192.168.10.1 link#3 UHS 0 16384 lo0 192.168.20.0/24 link#4 U 10946342 1500 igb3 192.168.20.1 link#4 UHS 0 16384 lo0 192.168.30.0/24 link#5 U 464495 1500 igb4 192.168.30.1 link#5 UHS 0 16384 lo0 192.168.40.0/24 link#6 U 0 1500 igb5 192.168.40.1 link#6 UHS 0 16384 lo0 192.168.200.0/24 192.168.200.2 UGS 333989 1500 ovpns3 192.168.200.1 link#11 UHS 743340 16384 lo0 192.168.200.2 link#11 UH 33730 1500 ovpns3 [VPN address]/32 [my WAN IP] UGS 456678 1500 igb1 [VPN address]/32 [my WAN IP] UGS 5024988 1500 igb1EDIT: Since only a handful of us have had this issue, I agree that I must have something messed up in my configuration. But I have no idea what it is. And, since nothing in my logs leaps out at me as being a problem, I don't even know where to look. I've pretty much given up on this and am just living with NTP on WAN.
-
@beremonavabi said in Time is not syncing:
0.0.0.0/1 10.4.0.1 UGS 16952 1500 ovpnc1
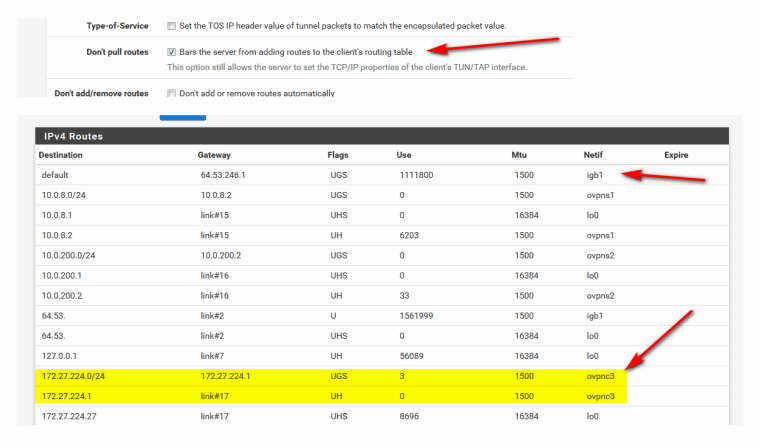
No your pulling routes if you have something like that..
You blocked routes from your client config? See how have only my wan default route and only routes for my client connection are the network its connected too.
-
@johnpoz I've got the same "Don't pull routes" box checked in my VPN clients. The 0.0.0.0/1 (and the 128.0.0.0/1) routes are added with the "redirect-gateway def1" Custom Option I'm using. That redirects all my traffic through the VPN (whereas you are policy routing specific clients), but leaves the default route untouched so the firewall, itself, can get through the WAN:
https://forum.netgate.com/topic/115760/firewall-traffic-needs-redirect-gateway-def1-to-route-thru-vpn
That being said, I had also been wondering if that could be causing the issue. But, since the OP of this thread isn't using a VPN client on pfSense, he shouldn't have those routes set. So, if that were the problem, he shouldn't be seeing it. Also, from my other thread I referenced earlier, I'm pretty sure that's what I tried to work around with a specific Outgoing NAT rule to allow UDP 123 traffic to go through the WAN:
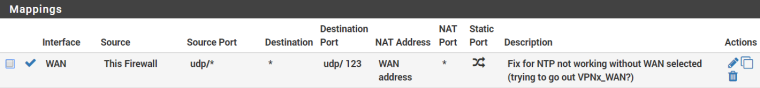
That didn't work. So, obviously it didn't do what I thought it might.
Still, that's all on the routing side. I still don't understand why having NTP listen on the WAN would allow this to work. AFAIK, the NTP client on pfSense sends out traffic asking for the time and gets a response. There shouldn't be anything legitimate arriving unsolicited from the internet. So, the incoming NTP traffic ought to get right through the firewall since it's in response to a legitimate request.
Do you have any blocking rules on your WAN to block incoming private/bogon networks? Or, do you just let the default "block everything" behavior in pfSense handle that? Could the NTP traffic from my setup be somehow avoiding NAT, going out with my private address on it, and getting blocked on the way back in by my rules?
-
@beremonavabi said in Time is not syncing:
Custom Option I’m using.
Same problem then... Why would you be doing that.. Turn that off - does your ntp start working now... Its quite possible your vpn is just blocking ntp. Sniff on your vpn interface do you see the ntp queries go out?
Argghhh I wish people would stop jumping into threads that have NOTHING to do with their problem or their setup is completely different..
-
@johnpoz said in Time is not syncing:
Argghhh I wish people would stop jumping into threads that have NOTHING to do with their problem or their setup is completely different..
What are you talking about? I "jumped" into this thread and gave the OP the solution he needed to get NTP working (select the WAN in Services > NTP). I then noted he was using VPN, as was I. That's a point in common. I was trying to explore that as possibly relating to this issue. In what way did I jump in with something not related to the problem?
But, I guess, just forget it.
-
@beremonavabi said in Time is not syncing:
(select the WAN in Services > NTP)
That is NOT a solution... That is a work around for some other misconfig..
Did you do what I suggested and remove the 0.0.0.0 route you have and see if works then not picking wan.