[SOLVED] How to filter HTTPS for wifi network (guests)
-
@susamlicubuk said in How to filter HTTPS for wifi network (guests):
You can do it with e2Guardian
you still need to install an ssl cert if you don't want your browser to throw warnings:
Disavantages are that in order for MITM to be usable a private root CA
certificate has to be installed on each browser and that more processing power
is needed on the server in order to encrypt and unencrypt the traffic.
(https://github.com/e2guardian/e2guardian/blob/v5.1/notes/ssl_mitm) -
No, there is no such thing as deep packet inspection for HTTPS traffic unless you do MITM set up. HTTPS is designed to resists such snooping and doesn't allow any provisions for the middlemen to even get a slightest hint of the content that is being passed. The best you can do afaik is to filter by URLs that are being used and by inspecting the SNI messages that are passed in the initial phases of a HTTPS connections in clear text. This is the first pfSense specific search hit I found:
https://openschoolsolutions.org/pfsense-web-filter-filter-https-squidguard/
-
When a client is set to use a proxy, explicit not transparent it will send a connect statement to the proxy for the https connection. In this connect statement will be the fqdn of the connection.
So in this case you can filter user from going to say www.p0rn.com without any sort of mitm or interception of ssl traffic.. No certs have to be generated, no ca's have to be trusted by clients.
What what you can not filter in this case is when they go to say www.safedomain.com/p0rn
The only way to filter on such connections is to break the end to end https connection which is the whole heart and purpose of https in the first place.
-
Excellent responses above.
IMNSHO, MITMing HTTPS traffic, except your own for educational or security research purposes, is evil.
 There are reasonably sufficient methods to block/discourage access of inappropriate content for all but the most persistent--the kind you don't want anywhere near your network anyway. But there is no one-size-fits-all filtering/blocking out there. Even if you were to MITM all HTTPS traffic, if you think that would allow you to detect/block 100% of inappropriate content, you're fooling yourself.
There are reasonably sufficient methods to block/discourage access of inappropriate content for all but the most persistent--the kind you don't want anywhere near your network anyway. But there is no one-size-fits-all filtering/blocking out there. Even if you were to MITM all HTTPS traffic, if you think that would allow you to detect/block 100% of inappropriate content, you're fooling yourself.
Depending how important this is to social club organizers/members, you might consider a whitelist approach instead. In other words, all services/protocols/sites are blocked for guests by default, and only specific protocols+ports+sites whitelisted.
Just don't break HTTPS.
FWIW -
Why would you care where guest go? If your going to provide "guests" a connection to use the internet why do you give 2 shits if they are surfing p0rn or not?
Are you trying to protect them from malware? Do that with simple dns filtering you hand out via dhcp - if they don't want to take your "protection" that is on them.. If your "social" club - lets call that pc speak for "church/hate group/same thing" and you don't want your "guests" viewing any inappropriate content like 2 woman "doing" it...
Simple solution is let them just surf the net via their LTE connection on their phone.. You would be doing everyone a favor and just not provide this "free" connection if its not going to be "free"
There is ZERO reason to break the trust that a https connection is there to provide. If you have clients of yours that you do not want going to xyz.. Then you should do such filtering on the client you control and not the connection..
Just my 2 cents after 20 some years of having to deal with corp nonsense and dealing with some companies wanting to be the internet nazi/police... And I have always been on the control side - I just don't get it.. I can understand not wanting your users sucking up all the bandwidth to watch the world cup while they suppose to be working, etc. But that is s different sort of control vs having to do anything with mitm and allowing you to see what is inside their https stream.
What companies don't get is that your not stopping anyone that has a clue.. It takes me 2 seconds to circumvent your "filterng" if you let me out on on port ;)
-
What companies don't get is that your not stopping anyone that has a clue.. It takes me 2 seconds to circumvent your "filterng" if you let me out on on port ;)
Maybe a little longer to circumvent if I only allow to specific sites on port. ;-)
-
No not really ;) Not unless your only allowing whitelist to specific sites..
Here perfect example
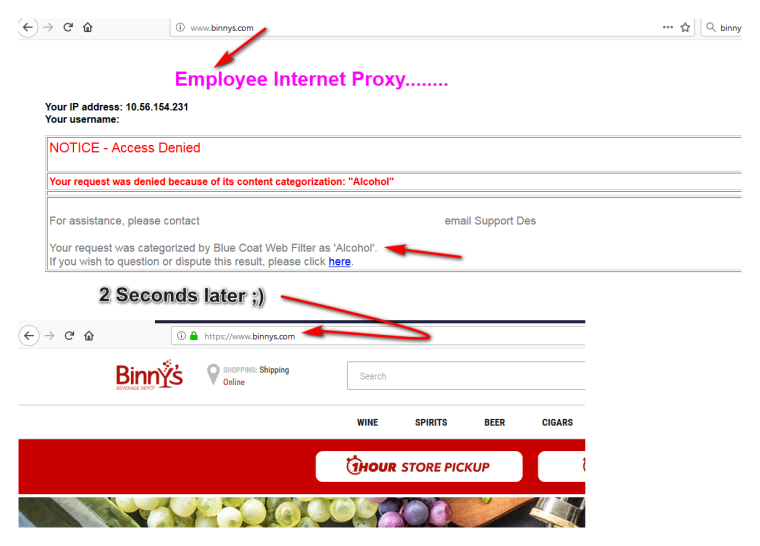
At work now - took me longer to take the pictures and annotate than actual circumvention ;)
-
Ok ok.. i understand all the replys, this was the best part: "internet nazi/police"
 !!
!!My solution was:
NIC LAN (users company): Proxy with SSL Interception, Installing cert via GPO
NIC WIFI (users guest): Not Interception, Not Filtered, Not SSL. Full access but using DHCP with OpenDNS (no porn), ...free as a bird (but without porn )
)Thanks and topic close! :)
-
So what do you have against your guest rubbing one out in the bathroom before the big presentation? ;)
-
You can still do some filtering on HTTPS without the MITM. On E2 Guardian, I have multiple groups setup, some which have MITM enabled and some such as in your case that are for Guest Wi-Fi where I can't properly sneak in the CA. On Squid I believe this is referred to as Bump and Splice all.
For my guest Wi-Fi setups, I just use the non-MITM method. This is where the proxy is able to see the domain name without the resource path at the end in order to decide if a website should be let through or not. MITM would obviously allow the proxy to look at the entire URL with the resource path and make a informed decision as to whether or not to allow a website through. I prefer it way more than DNS level filtering as it's more flexible. You can set it up for specific users while others can browse those sites just fine.
If you've got sometime, I recommend you give E2 Guardian a shot. It worked out a lot better than Squid in my use case and it has the added benefit of actual phrase filtering.