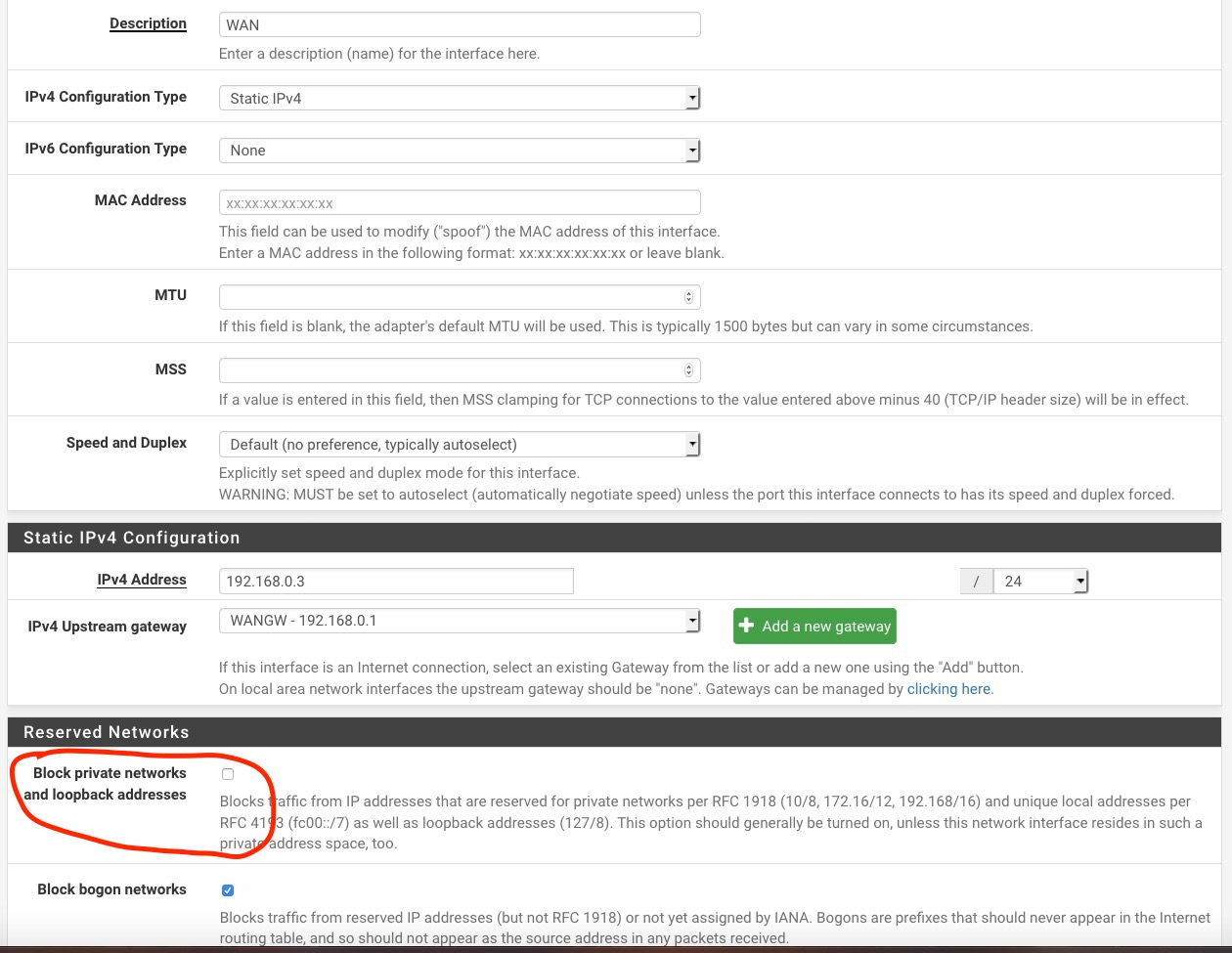
WAN Interface Block private networks and loopback addresses setting correct?
-
In my network I have to run in a double NAT setup as the ISP modem cannot be set to bridge mode. I have setup the ISP router to DMZ the 192.168.0.3 static address I've assigned to my PFSense firewall. My question is with the settings on the WAN interface of PFSense... should the Block private networks and loopback addresses setting be unchecked or checked? Initially I had it checked and all appeared to work fine but with additional reading since 192.168 is a private address the box should be unchecked. Seems to work either way but which is correct??
Running 2.4.4 if it matters.
-
You only have to uncheck it if you want to allow incoming connections and if you have forwarded traffic from your ISP router.
For outbound connections it is irrelevant. -
Even in the case of forwarding traffic from the router, unless it was source natting the traffic the block rfc1918 rule is only on the source IP not the dest IP.. So forwarded traffic from the internet, ie public IPs would not be blocked..
look here post from Derelict
https://forum.netgate.com/topic/119431/block-private-networks-what-does-that-do-what-is-it-used-for/6
These are the rules generated on my WAN interface for the block RFC1918 checkbox:
block anything from private networks on interfaces with the option setblock in log quick on $WAN from 10.0.0.0/8 to any tracker 12000 label "Block private networks from WAN block 10/8"
block in log quick on $WAN from 127.0.0.0/8 to any tracker 12000 label "Block private networks from WAN block 127/8"
block in log quick on $WAN from 172.16.0.0/12 to any tracker 12000 label "Block private networks from WAN block 172.16/12"
block in log quick on $WAN from 192.168.0.0/16 to any tracker 12000 label "Block private networks from WAN block 192.168/16"
block in log quick on $WAN from fc00::/7 to any tracker 12000 label "Block ULA networks from WAN block fc00::/7"They block connections coming INTO WAN sourced from addresses in the RFC1918 list of addresses (and localhost and IPv6 ULA).
They will not block port-forwarded or 1:1 traffic from an upstream router unless that device also NATs the source address to something that matches these rules.
-
Perfect...thanks for the clarification!