100 DNS errors on ipleak.net when upgrading to 2.4.4
-
I’m not really sure what the question i need to ask is in order to solve my problem all i know is that when i upgraded from 2.4.3 to 2.4.4 ipleak.net started giving me 100 dns errors.
Having looked at the release notes for 2.4.4 i’ve noticed that something new was done to the dns resolver feature so my assumption is that this is what’s causing my problem.
What i don’t know though is exactly what the problem is or what to do to fix it.
All i know is that the settings i use for 2.4.3 work and give me no dns errors on the ipleak.net site but don’t work if i upgrade to 2.4.4. I’ve gone back and forth a number of times now making sure it’s pfsense 2.4.4 that’s causing the problem. That much I’m very confident about. I just have no real clue as to why other than the above mentioned change to the dns resolver feature.
As far as i can tell everything else works fine and so does ipleak.net when not using pfsense 2.4.4. Soon as its used however the dns errors appear when running the ipleak.net dns test.
I’ve tried blindly ticking and unticking the new boxes in the dns resolver page but nothing helped.
Does anyone have any idea why this is happening and ideally how i fix it?
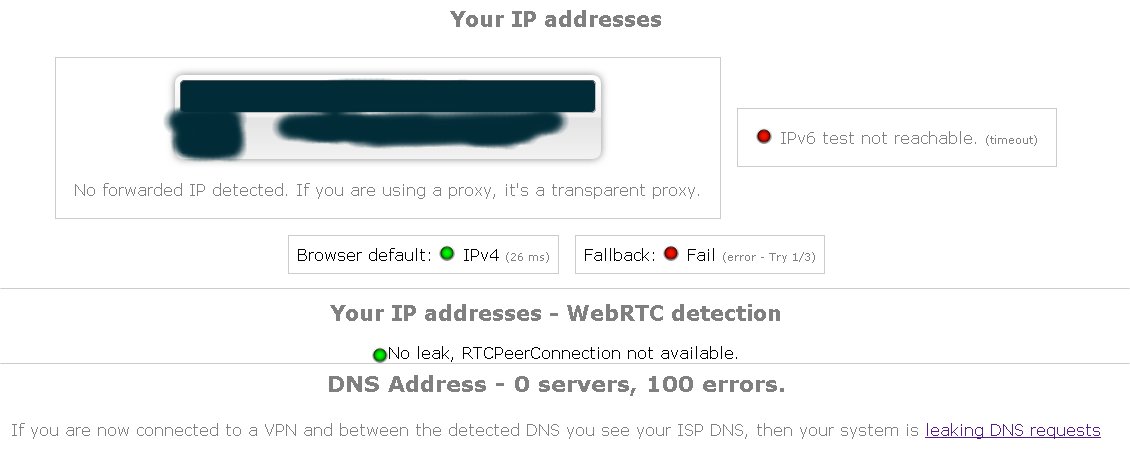
Just for reference this is what i get when running 2.4.3 and is what it should show:
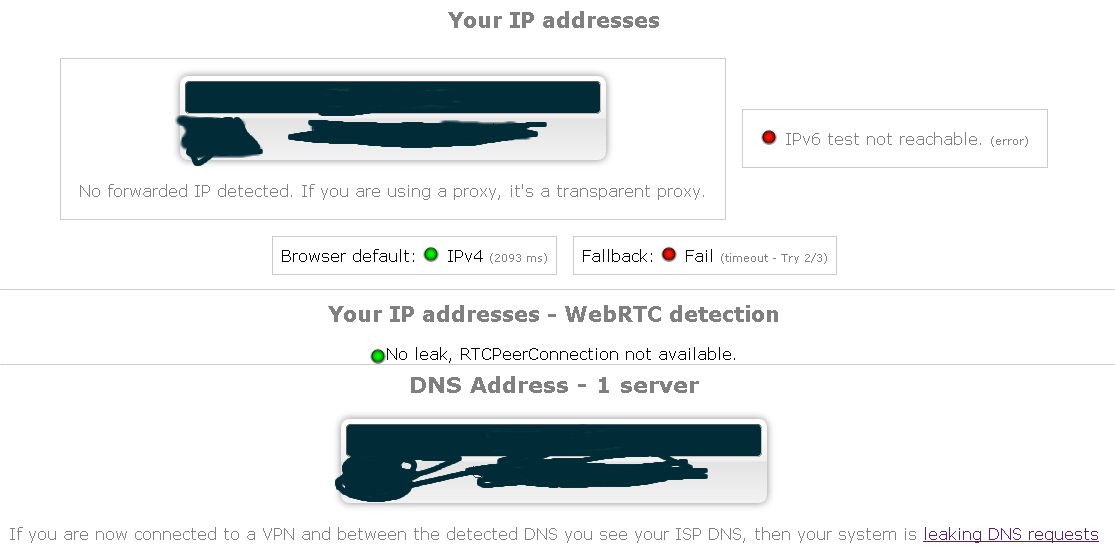
And this is what i get if running 2.4.4 and gives me the errors:
-
Well first you have to find out what they define an "error" as. Saying there are 100 "errors" without saying what they are is useless.
-
"If you are now connected to a VPN and between the detected DNS you see your ISP DNS, then your system is leaking DNS requests"
Isn’t that web site for testing leaks when your connected via VPN?
-
Yeah, I'm getting the same result... also, where the GRC DNS spoofability test used to run (and used to do very well with my DNS settings in Unbound!), it's also returning 0 DNS servers found now. Which is CLEARLY not right, since I certainly browse the internet using domain names and not IP addresses.
Maybe something in the browsers has changed instead of something in pfSense... but something definitely doesn't let these tests work like they should.
Edit to add: Not likely the browsers... tried multiple browsers and all failed the same way for both tests.
-
So this has really been bugging me. I'm guessing that some setting in the version of Unbound that is part of 2.4.4 is enabled that is preventing these different DNS tests from running properly. I don't know what else might have changed in Unbound, but something definitely has. Some searching has returned things that some test sites might have invalid DNSSEC data or other issues, but I've still not been able to get them to work after adjusting various settings in Unbound.
For the moment, I've found a DNS test site that seems to work, and seems to consolidate a number of different DNS tests into one. It tests DNSSEC, port and ID randomization (DNS entropy), and more edge cases like TCP connectivity and IPv6. Unknown if it tests for TLS (I'm not set up for that). And there's a nice list of what IP addresses were observed during testing, so you can see if something's leaking or not (i.e. if you're on a VPN and you see an address not from your VPN provider, you have a DNS leak). Click the word Network to show that list.
This test comes from the DNS Operations, Analysis, and Research Center (DNS-OARC), which may be why it works (since they would certainly have everything configured properly). The link below goes to a DNS-OARC page that links to the test site. Make note that all test data is collected and can be analyzed by the DNS-OARC and its members (though that's not likely to be worse than all the data collection various free test sites do).
https://www.dns-oarc.net/oarc/services/cmdns
-
@smegheed said in 100 DNS errors on ipleak.net when upgrading to 2.4.4:
I’ve tried blindly ticking and unticking the new boxes in the dns resolver page but nothing helped.
Really.. that is strange since blindly clicking shit is such a proven troubleshooting method ;)
There are questions all over their fourms about the 100 errors.. The 30 seconds I was willing to spend looking found nothing but questions with zero answers to what those are suppose to even represent.. So with Derelict if they are not going to state what the 100 errors mean then its useless info.
If I had to guess its sending 100 queries.. And they all fail to find what dns server your using.. While I didn't count them up - there are shit ton of these if you sniff.. Could well be exactly 100 they check for. You can even see their blue bar count down through the hundred - which I assume when its sending the queries.
The test site linked to by @virgiliomi is far better than any of these nonsense "leak" testers the vpn companies put out to try and get you use their vpn services - you know because the man might be sniffing your dns info..
-
Well, maybe it's not pfSense or Unbound... Because I tried the GRC test (which isn't a "nonsense 'leak' test"; it's intended mainly to test port and query ID entropy) on my iPhone, not connected to my WiFi network (just using Verizon LTE) and the test still failed. Maybe there's a larger issue with the means these various DNS tests use to determine their results. Maybe there's something about IPv4 vs IPv6? (GRC's site doesn't support IPv6, not sure about the DNS server(s) his site uses though).
I guess I'll be bookmarking that DNS-OARC test for future use then. :)
-
I've tried asking on the IPLeak forums about what the 100 errors mean and no one has come back to me with an informative reply. Best i can figure out the errors signify that no DNS servers were found or able to be verified as leaking or not.
While i can't rule out the possibility that its more an issue with IPLeak or something else, to me it seems very conclusive that the problem lies with the update to PFsense and its dns resolver feature.
I've checked, double checked and triple checked that the settings I'm using in 4.4 are the same as what i use in 4.3. I've had 2 boxes running side by side, one using 4.3 and the other using 4.4.
In 4.4 it fails to work and i get the 100 errors. In 4.3 it works fine and i get 1 result with no leaking detected and more importantly no errors. It's not the browser or computer i use to access the site that's the problem as they stay they same. The only thing that changes is what version of PFSense I use.
I've even tried setting up PFSense to act as a router to my main internet connection so as to eliminate openvpn being an issue along with the other settings i use to make the openvpn connection work how i need it to.
Putting my ISP's router into modem mode and configuring PFSense in a very basic setup to get the IP from the modem and then accessing IPLeak through this box the problem still occurs. Where as if i access IPLeak through my ISP's router without the PFSense box i get no errors and it all works fine.
I understand what's been said about if it's wise to use a VPN providers testing site but it's what i've used without a problem in the past and can still use perfectly fine in every other scenario besides if PFSense 2.4.4 is used.
This make me believe that the common fault is PFSense regardless of the sites motives and trustfulness.
The only thing i can think of where it's not PFSense that's the problem is that in the update to the dns resolver feature its 'improved' things to the point its now incompatible with an old way of doing the dns checking or something that IPLeak uses.
If this is the cases then that's great. I can accept that. My only issue with this being the case then stems from the question: How do i know for sure and how do i figure out where the fault actually lies?