Using Cisco L3 switch with pfSense - static route needed?
-
Hey guys,
Introducing vlans into our network and will be using a Cisco 3750G to route the vlans inside the LAN. The 3750 will uplink to the pfSense firewall.
My idea is to add a last hop before firewall vlan, so all LAN traffic goes into a single vlan sent to the pfSense.
My question is will I have to add a static route on the pfSense to send the return traffic back to the appropriate vlan?
I'm thinking I won't have to because the 3750 can do that. pfSense would send traffic back to the last hop vlan and then the 3750 will route appropriately.
I just wanted to make sure I didn't have to configure any routes for this on the pfSense.
-
Put a static route on the firewall pointing the internal subnet to the L3 switch. The default route on the firewall should be the WAN gateway. Adding a dedicated transit vlan is a good idea, it avoids asymmetric routing.
-
Thanks, I was a little confused on how that would work.
Just to make sure, on the route, it would be from WAN to the internal (last hop) subnet 192.168.120.0/24?
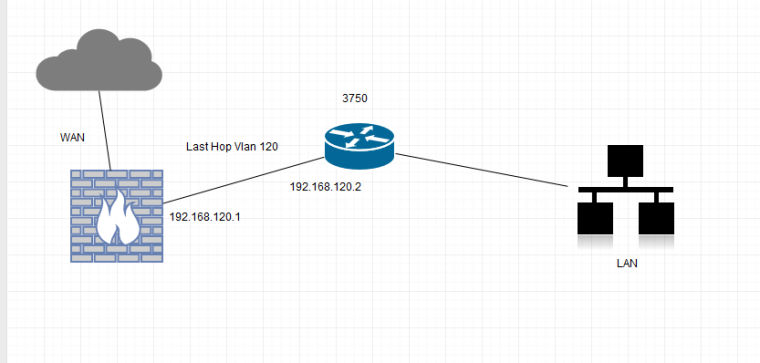
-
Let's say your LAN is 192.168.1.0/24 and the 3750 is 192.168.1.1. The 3750 is directly connected to 192.168.1 and 192.168.120 and has a default route to 192.168.120.1. The firewall has a (lan) route to 192.168.1.0/24 via 192.168.120.2 and a default route of the WAN gateway. Remember to allow traffic from 192.168.1.0 out the LAN and NAT it outbound.
-
So basically I would need to add the static (lan) route on the pfSense. The route would be for traffic seeking 192.168.1.0/24 to go through 192.168.120.2?
I could see that working for a single LAN, but what about the case of multiple vlans on the 3750? Meaning-- not all return traffic would be destined for 192.168.1.0/24.
Or could I choose an arbitrary vlan on the 3750 and then let it do the routing on the LAN?
Sorry, I'm a bit inexperienced on the routing side.
-
If you've enabled ip routing on the 3750 and defined an ip for your vlan interfaces, it will see all of your vlans as directly connected and will not need any static routing. If you define multiple vlans, you will need routes on the firewall for each subnet. You can consolidate the route if you put them in the same private supernet- e.g. you could have a route that pointed 192.168.0.0/16 to the 3750 and use any 192.16.x.x subnet you wanted on the Cisco.
-
Fortunately, at this point there are only 3 vlans on the LAN side.
My original thinking was that static routes for these 3 vlans would have to be entered on pfSense.
So my static routes (on pfSense) would be from 192.168.120.0 to each individual vlan right?
So for example...
Destination Next Hop
192.168.90.0/24 > 192.168.1.2
192.168.1.0/24 > 192.168.1.2
192.168.60.0/24 > 192.168.1.2 -
Based on your diagram, the routes would go to 192.168.120.2
You could consolidate them with 192.168.0.0/17 192.168.120.2 -
Ahh, okay.
So one static route in the pfSense:
192.168.0.0/17 via 192.168.120.2
Thanks so much for your help dotdash!