Force DNS Resolver to Query OpenDNS for content filtering?
-
Can I force PfSense to use the DNS resolver for local hosts, then forward any external query to OpenDNS?
Current Setup:
PfSense (192.168.100.1) DHCP Server points DHCP clients to raspberry-pi PiHole DNS server (192.168.100.2).
PiHole Up-Stream DNS points to OpenDNS server IPs
Whats Working: Content filtering (kiddos cannot access porn sites)
Whats not working: Local hostname DNS registration / lookup / PTR records, core DNS functionality IMODesired Setup:
PiHole Up-Stream DNS points to PfSense DNS Resolver. DNS Resolver "Enable Forwarding Mode" ticked. Everything ticked on DNS Resolver Options page. In System > General Setup > I have each WAN (dual WANs) Gateway pointed to a OpenDNS server. Disable DNS Forwarder and DNS Server Override are not ticked.Whats Not Working: OpenDNS Content filtering no longer works with the "Desired Setup", I'm guessing the DNS Resolver is resolving the fqdn itself instead of forwarding requests to OpenDNS.
Here's an imgur gallery of the "desired setup" and pihole if anyone can spot any obvious config issues. DNS Forwarder is not enabled. I tried using that instead of the resolver but it didn't make a difference. I've rebooted the PfSense box and Pihole multiple times.
https://imgur.com/a/8KFPgiv
Thanks everyone
-
Here's how I just got it to work.
Disable DNS Resolver
Enable DNS Bind Server, set forwarder IPs - 208.67.222.222; 208.67.220.220;
(the last ";" is important or you have to edit /cf/named/etc/namedb/named.conf manually to get service to start-- pfSense front end web devs need to regex the input field and people wont make this mistake)Something about DNS Resolver just wasn't working....
Am I losing any important features going with the Bind flavor? -
Hi,
No need to get bind involved to have what you want.
You could ask OpenDNS how to setup your pfSense https://support.opendns.com/hc/en-us/community/posts/220008547-How-to-configure-my-pfsense-firewall-with-OpenDNS-for-my-network ( the first link supplied is extraordinary !)
Or, the even better : consult the pfSense documentation (which is this forum in this case, not the doc).Anyway. I have an account with OpenDNS, so I :
- Stopped using the Resolver which I use normally (for DNSSEC etc).
- Entered these on the System => General Set up page :
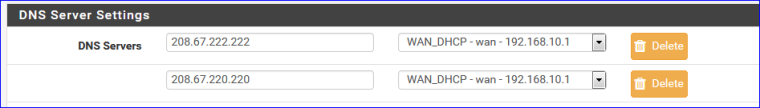
- Activated the Forwarder.
And done. This URL https://support.opendns.com/hc/en-us/articles/227986567-How-to-test-for-successful-OpenDNS-configuration- confimed that my request went through OpenDNS.
Pffff. Took me 60 seconds flat.
Btw : Keep in mind that OpenDNS should know what your WAN is, because that's the way they know that your DNS requests came from you. If your IP-WAN isn't a static one (always the same) you should setup a Dynamic DNS : see their instructions.
@ccnewb said in Force DNS Resolver to Query OpenDNS for content filtering?:
Am I losing any important features going with the Bind flavor?
Dono.
Working with bind has a big advantage : you're working with the real thing that can handle all DNS related things. You name it, bind does it (as long as you are able to set it up). It's huge, you'll be studying for hours.
I guess using bind just to instruct pfSense that it should OpenDNS as it's upstream DNS seems overkill to me.
Keep in mind : keep it simple.Edit :
Another proof that it works :
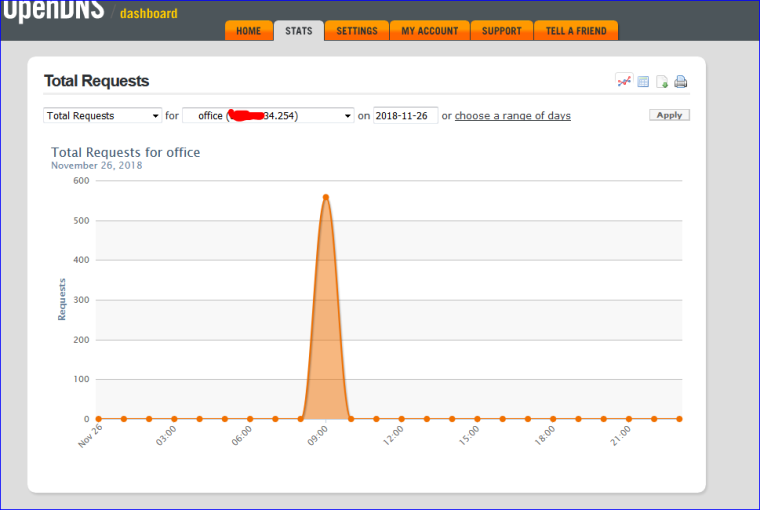
edit 2 : another proof : it's 09h00, monday morning. My colleges are showing up.
Took them less then a minute to find out that their favorite p0rn sites are not reachable anymore ..... I promised that I 'have a look at the situation" ^^edit again : I have somewhat this feeling that the Resolver (unbound) can also be used. remove all dnssec thingies, and activate the Forwarder mode - should do it. I'll try that later on.
-
Thanks for your reply.
I'm not sure what's different today, but I disabled BIND server (I agree with you, sounds like overkill for what I'm doing) and I enabled DNS Forwarder with the settings below, and content filtering seems to work just fine. Strange as I remember trying this multiple times before and the porn sites would be accessible.

-
You can test OpenDNS right away : just visit http://welcome.opendns.com and the page that shows up will confirm you're using OpenDSN services.
A typical p0rn site can be tested with http://www.exampleadultsite.com
A pishing site http://www.internetbadguys.com
-
@gertjan Thanks good to know about the example sites. Bookmarked. I loaded the real deal a good 50 times during testing. Content filtering working great now. Added a firewall rule to only allow port 53 DNS traffic through Pi-Hole. My Roku TVs decided to hardcode their own own 8.8.8.8 DNS setting , which now redirects to Pi-Hole. Too cool. I blackhole a ton of call home traffic across the network and it causes some devices to freak out with log writing.