Routing between interfaces (LAN, VLAN)
-
VLANs wouldn't matter. If, as you say, Internet access works from these networks then you have a couple possibilities:
- Firewall rules are incorrect in some way (e.g. policy routed directly out WAN, maybe blocked by some other floating or group rule)
- Incorrect subnet mask on a device causing it to reply the wrong way
- Missing gateway on the target device causing it to not reply at all
- Local firewall on the target preventing communication outside its own subnet
My money is on #4.
-
Thanks for the answer.
In my case:- Firewall rules on LAN interface: IPv4 Allow from any to any, VLAN IPv4 Allow from any to any, no floating or group rules.
- The mask is /24 on all the interfaces for PFsense and VLAN client.
- The Gateway for clients in VLAN is 192.168.172.1/24 (PFSense interface), LAN: 192.168.1.1/24(PFSense interface).
- The local firewall is OFF.
I've checked everything and I'm stuck here. As I remember it worked fine before updates.
Maybe something wrong with network cards?igb0@pci0:0:20:0: class=0x020000 card=0x1f4115d9 chip=0x1f418086 rev=0x03 hdr=0x00
vendor = 'Intel Corporation'
device = 'Ethernet Connection I354'
class = network
subclass = ethernet
cap 01[40] = powerspec 3 supports D0 D3 current D0
cap 05[50] = MSI supports 1 message, 64 bit, vector masks
cap 11[70] = MSI-X supports 10 messages, enabled
Table in map 0x20[0x0], PBA in map 0x20[0x2000]
cap 10[a0] = PCI-Express 2 root endpoint max data 512(512) FLR NS
ecap 0001[100] = AER 2 0 fatal 0 non-fatal 0 corrected
ecap 0003[140] = Serial 1 ac1f6bffff485a98
ecap 0017[1a0] = TPH Requester 1
ecap 000d[1d0] = ACS 1 -
And you not shoving it out a gateway on your rules - post them!!
JimP's 1st thing listed..
If your vlan client can use pfsense to get to the internet, then it can use it to get to lan.. As long as the rules allow it.
How could something with the nic allow for internet access but not access to lan/vlan
Can vlan client ping lan IP of pfsense?
192.168.1.1 and any LAN hosts.
Take .1 is pfsense - then that SCREAMS forcing out gateway, or just say wrong rules - only tcp or only tcp/udp trying to ping which is icmp..
Post up your rules.. So we can all be clear on what they are vs you saying they are X.. When they for sure might be Y..
-
A client from VLAN can't ping 192.168.1.1
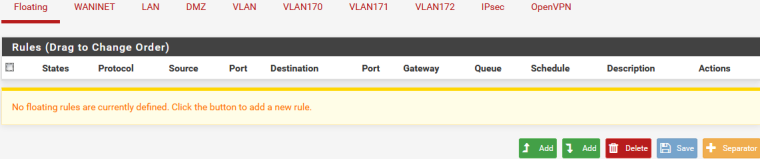
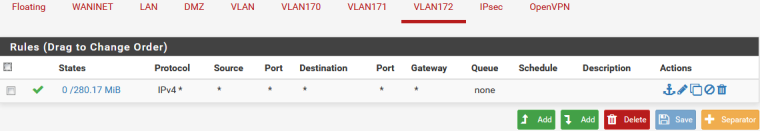
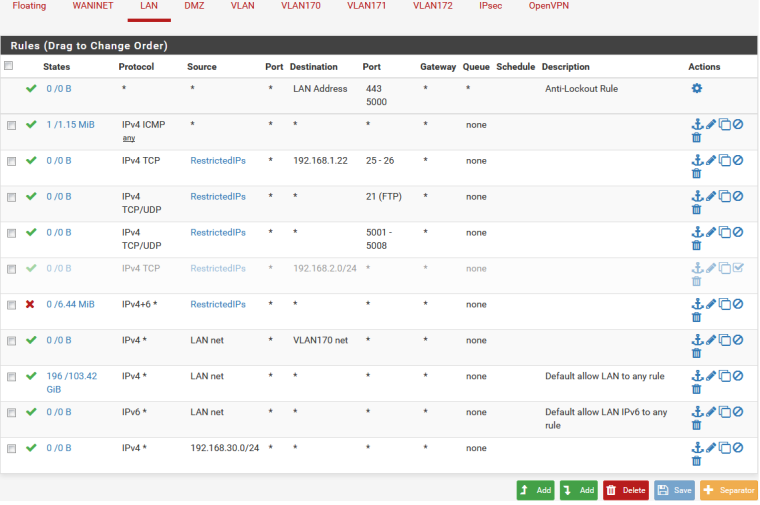
-
You do understand that lan net to vlan170 net is pretty pointless right.. Since below it you have a any any rule..
So you lan has downstream networks on it? With that allow 192.168.30/24 rule?
What about your other vlans - they are all having this problem?
You sure lan trying to talk to vlan172 is just not an IP listed in restricted?
Your saying that client on vlan172, has internet but can not ping pfsense Lan IP 192.168.1.1?
-
Routes:
default MyISPAddress
192.168.1.0/24 link#4 U igb3
192.168.1.1 link#4 UHS lo0
192.168.172.0/24 link#13 U igb3.172
192.168.172.1 link#13 UHS lo0 -
Yes, I understand that there some useless rules for now but there were some blocking rules which I deleted for testing purposes.
RestrictedIPs list contains only 2 hosts .1.31 and .1.87.
All the VLANs have the same problem. -
maybe play with offloading?
<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,VLAN_HWTSO> -
These are all vlans on the same parent interface?
What is your esxi switch settings? Did you set the vlan id to 4095 so it doesn't strip tags? Why do you not just create new vnics for your pfsense vm so there are no tags in pfsense and do the tags on esxi via port groups on your vswitch?
What version of esxi are you running?
-
ESXi 5.5.
It has vlan id 172 currently. Before I set 4096 but I need to set vlan id inside a VM to 172.
The behaviour is the same. -
4096? For the vswitch to not strip tags its 4095.. Not sure where you got that?
Does 5.5 list support for freebsd 11? You should really be running current 6.7
I ran pfsense on esxi for many many years.. I have since moved away from it when I updated the old hardware I was running 6.5 on to just a synology nas and using their VM manager for my VM needs..
If your going to set vlans in pfsense then the vswitch should be 4095.. Then connection on your phy switch vlans would be tagged.. Except for your native vlan if using that - looks like igb3 is your lan.. which is untagged (native).
Then in your switch your devices ports would be untagged in the vlan you want those devices in..
You need to decide if you want pfsense to handle the tags or esxi.. If pfsense then vswitch would be 4095 and pfsense would see the tags..
If want to let esxi to do the vlans then you would create port groups with the tags and connect new vmnics in pfsense to these different port groups.
If internet is working, and your not sending out a gateway something is very strange.. why internet would work but not other networks directly attached to pfsense.. Are you using a proxy on pfsense?
I would sniff on pfsense to validate that your tagged traffic gets there still tagged.. And then reply is sent with tag as well to your switch.. A correct setup with vlans being done on pfsense your vswitch vlan ID would need to be set to 4095.
-
My PFSense is on the Supermicro platform.
VM is on the ESXi. -
So your pfsense is physical... Then what are you trying to do with esxi put vms on different vlans?
Please draw up how you have everything connected... Do a simple sniff of traffic... If you client can get to pfsense and to the internet then it can get to pfsense IPs on its other interfaces. Unless you block it with a rule..
-
I found the cause :).
It was IPSEC. I took wide network range 192.168.0.0/16 so all the traffic goes there.
Thanks for your help. -
Zero mention of IPsec in your OP.. Just saying..
-
C cpohle referenced this topic on