Active Active Load Balancing
-
Hi to all,
I need your advice on a configuration I plan to deploy.
Before going "live" I prefer to ask your opinion.The question is about a pfsense firewall and an active/active load balancer cluster(nginx) that I have setup.
Basically PFsense connects LAN1 to LAN2.-
LAN1 is the client networks
-
LAN2 is the server network
The load balancers have two VIP:
-
test1 primarily on LB1
-
test2 primarily on LB2
There is no problem between LoadBalancers and the server farm: the farm exposes an http service
I also defined on my dns the test.intranet name that points to both IP and answers like this (from the client): in a round robin fashion
dig test.intranet
; <<>> DiG 9.10.6 <<>> test.intranet
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 62823
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;test.intranet. IN A;; ANSWER SECTION:
test.intranet. 3600 IN A 192.168.250.101
test.intranet. 3600 IN A 192.168.250.100dig test.intranet
; <<>> DiG 9.10.6 <<>> test.intranet
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 62823
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;test.intranet. IN A;; ANSWER SECTION:
test.intranet. 3600 IN A 192.168.250.100
test.intranet. 3600 IN A 192.168.250.101PFsense dns point to the same internal DNS and resolve like
drill test.intranet.dynameeting.it @127.0.0.1
;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 4768
;; flags: qr rd ra ; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;; test.intranet. IN A;; ANSWER SECTION:
test.intranet. 3578 IN A 192.168.250.100
test.intranet. 3578 IN A 192.168.250.101I've put an alias in PFSense
TEST test.intranetThe question: is ok if I set my PFSense rules like
allow http LAN1_network -> TEST
deny LAN1_network -> LAN2_networkor I will get some drop or problem?
(feel free to move my answer on another section if this is not the good one!)![alt text]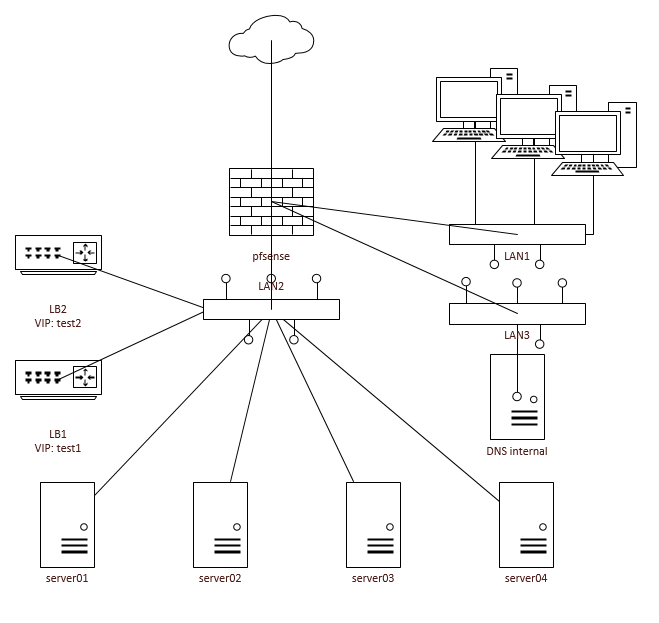
-
-
I would expect that to be OK as long as the load balancers are acting as true proxies rather then forwarders. If all traffic to/from the servers goes via the load-balancer that is all the rules you will need.
Steve