NetGear(s) in AP Mode will not communicate on different LANs (Resolved)
-
Yeah if the device doesn't have a gateway then no you wouldn't be able to talk to from another network... Without source natting the traffic to look like its on the same lan as the device without a gateway.
-
Both routers are setup in default AP mode. The gateways are in the pictures below, looks like gateway received from each LAN on pfsense.
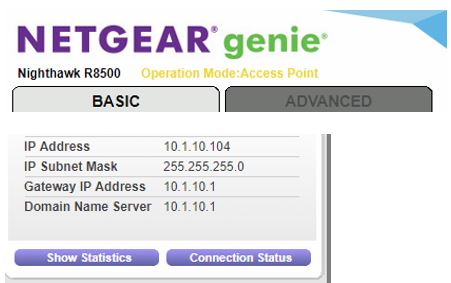
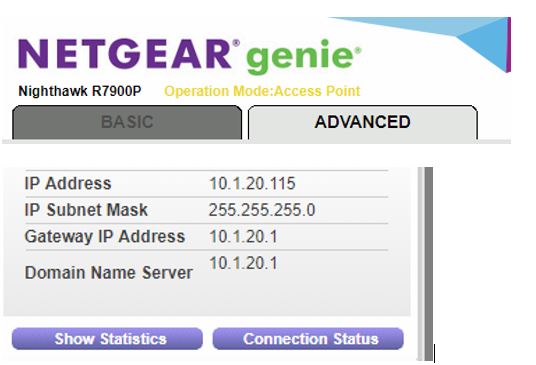
-
Then it could be issue with the netgear just not wanting to allow remote access to its gui... Look to see if you can enable remote admin.
If not since you say it works when you access it from device on that network.. Source nat it so traffic from your remote IP looks like its on that vlan... This is done in the outbound nat tab picking the interface the AP is on, vs the WAN interface.
-
Hello John,
Remote on the routers are unavailable.
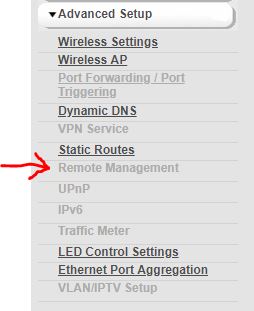
I went to NAT Outbound and changed below to LAN1 and LAN2 is this what you were referring too? If so still no communication to the router APs?
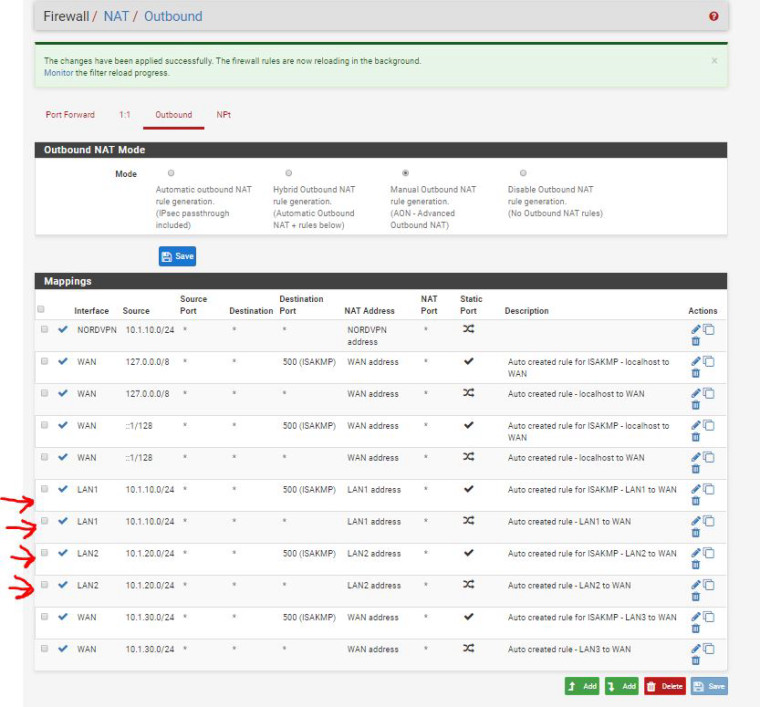
-
Dude your natting everything your VPN.. That is most likely where your problem is!!
Why would you not be in hybrid mode if your using a vpn?
And you would want to setup destination on when to source nat the traffic.
-
John,
I followed instructions from someone that setup NordVPN, based on that are where these settings came from. LOL
I want every device on LAN1 to go through VPN. LAN2 I want every device to go though WAN
Does this look correct now based on what I described above? If so still not working.
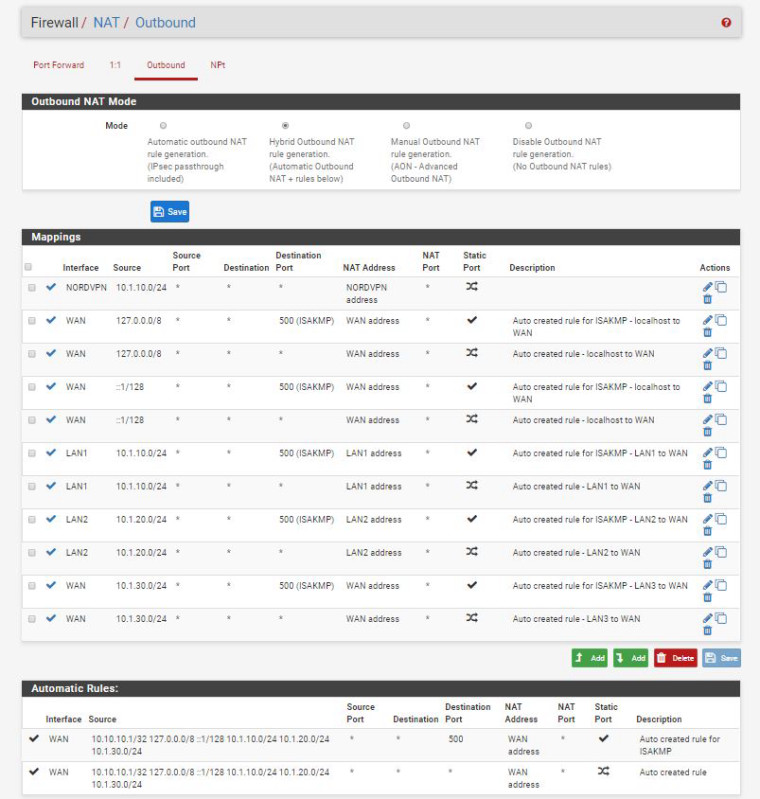
-
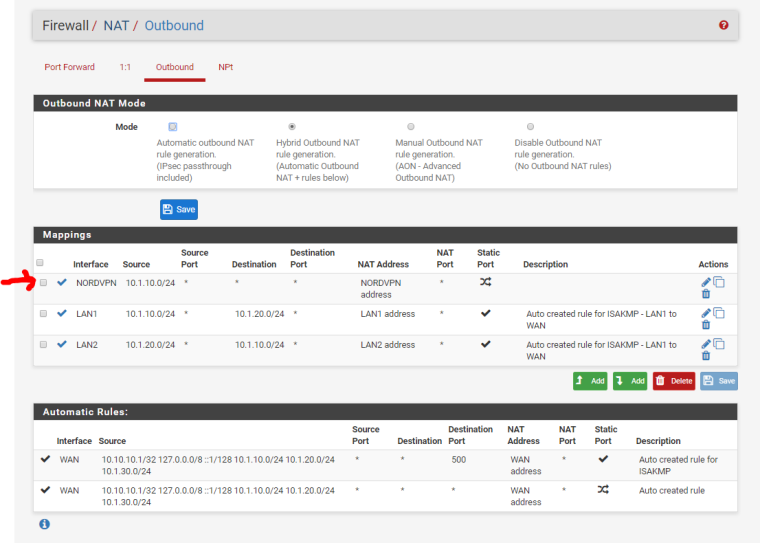
You would probably want to NAT source any or source from an alias with RFC1918. At a minimum you want to NAT from LAN1 sources outbound on LAN2 and LAN2 sources out of LAN1. You also probably want to limit the NAT to just the destination of the APs.
And, yes, you probably want to use Hybrid NAT mode and let it do the heavy lifting with you only adding the LAN1 and LAN2 rules. (Yeah, that's better in Hybrid mode.)
-
I cleaned up NAT and using Hybrid
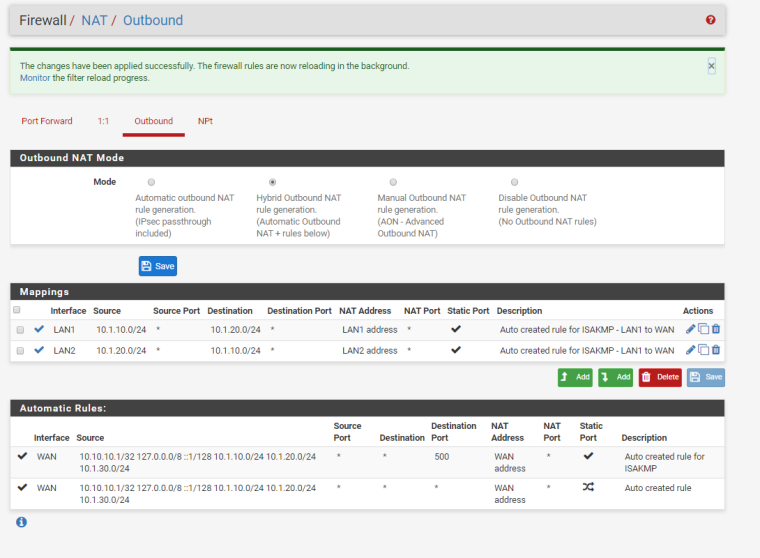
No VPN internet now on LAN1?
LAN2 internet from WAN is ok.
LAN1 Rules
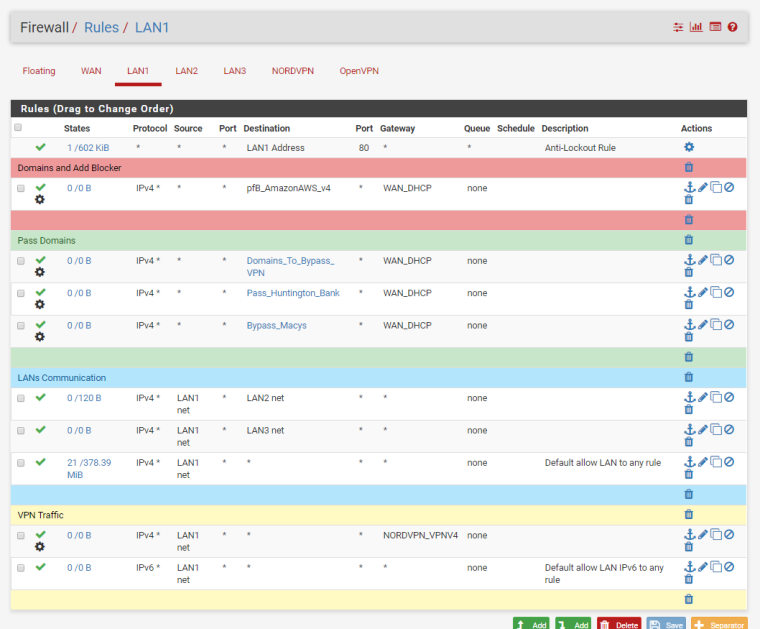
I'm not sure how to setup an alisas for RFC1918, can you provide guidance? I'm so confused now.
-
Navigate to Firewall > Aliases:
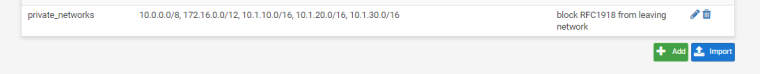
Create an alias for the RFC1918 network ranges. Call it private_networks and include the following ranges:- 10.0.0.0/8
- 172.16.0.0/12
- 192.168.0.0/16
-Rico
-
Hello Rico,
Thank you for the instructions, I did make a small change due to my LANs IP addresses. correct?
Internet works on LAN2 however still not working on LAN1 VPN internet?
-
Got the VPN internet back on LAN1 by adding to NAT? Does this look correct?
-
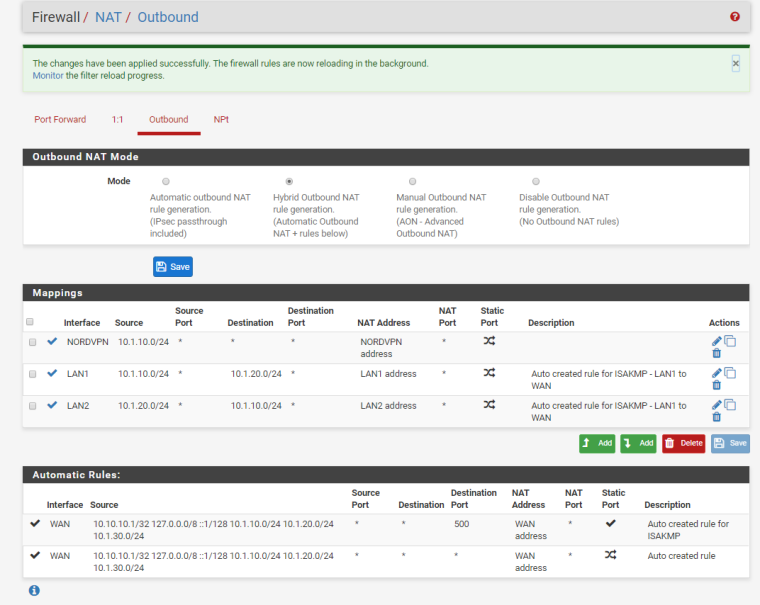
Why did you check static port on the LAN1 and LAN2 NAT rules. Nobody told you to do that.
-
Hello Derelict,
pfsense defaulted to static. LOL now it's corrected.
-
And does it work? Sniff on lan2 interface when trying to talk to lan2 AP from lan 1... Is the source IP your Lan2 interface IP.. Does the AP answer?
If works really no reason to sniff - but if not working they validate that pfsense is sending with source IP changed..
And NO pfsense does not default to static
-
The only way I can see it behaving like you thought static port was the default is if you used the copy icon on one of the existing static port NAT rules for ISAKMP. Which looks to be the case baseed on the rule description. :)
-
John,
Still not working? What do you mean to sniff?
Correct, I copied the rule and it was checked. Sorry for the false information, thanks for the correction.
-
@z71prix So you are trying to connect from a host on LAN2 to an AP on LAN1 (10.1.10.104).
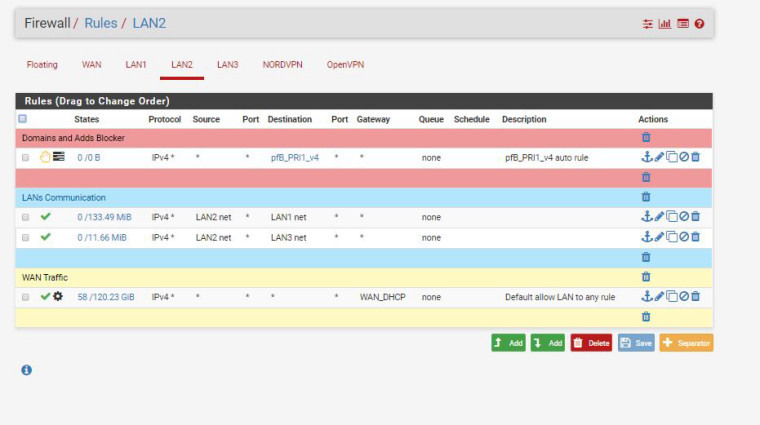
What are the firewall rules on the LAN2 interface?
Can you ping the AP instead of trying to connect to it?
-
Derelict,
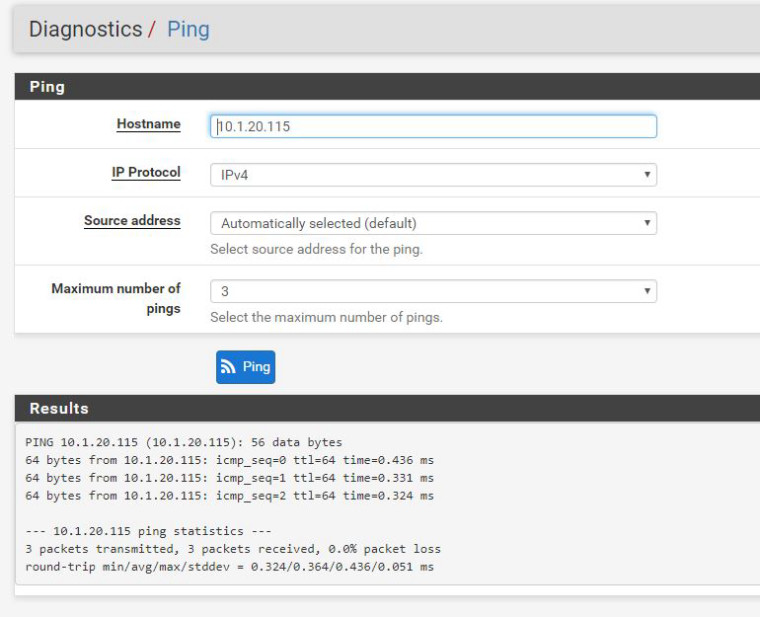
I'm on LAN1 now and pinged router AP on LAN2 ok, however cannot connect on web interface still.
Rules on LAN2
Rules on LAN1
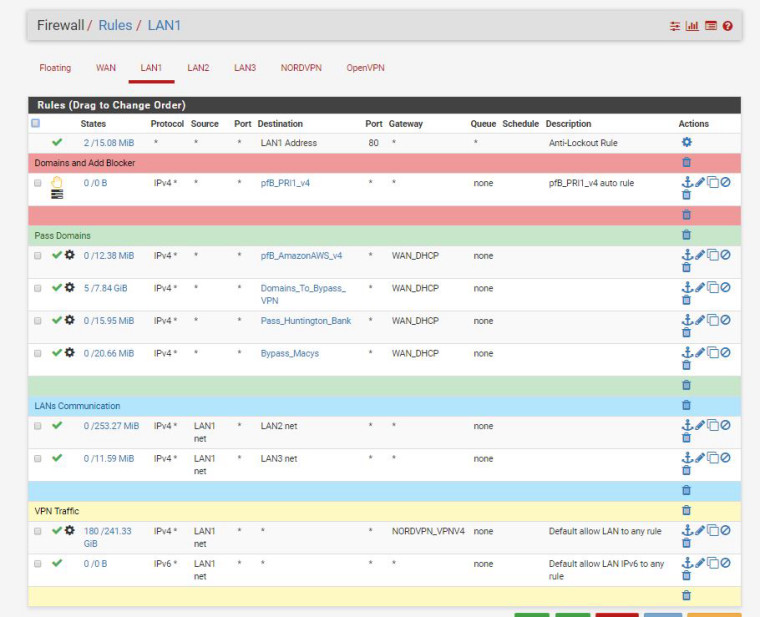
thank you -
Don't ping from the firewall, ping from the same host you are trying to connect from.
Please stick with ONE and ONLY ONE test scenario. Bouncing between connecting to 10.1.10.104 then 10.1.20.115 only confuses the troubleshooting steps. Fix the first and you'll probably fix both.
Diagnostics > Packet Capture
Interface: LAN2
Host: 10.1.10.104
Packets: 10000
Level of Detail: Full
Start
ping from the host you are trying to connect from. Windows default of a 4 count should be fine.
Try to connect to the web interface. Let if fail.
Stop the Capture
Copy/paste what is there here.Then:
Diagnostics > Packet Capture
Interface: LAN1
Host: 10.1.10.104
Packets: 10000
Level of Detail: Full
Start
ping from the host you are trying to connect from. Windows default of a 4 count should be fine.
Try to connect to the web interface Let it fail.
Stop the Capture
Copy/paste what is there here. -
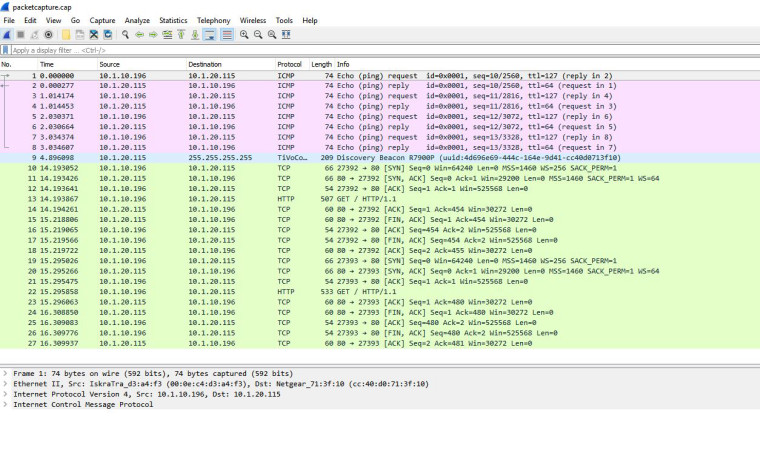
Ok, I'm currently on LAN1 trying to connect to AP on LAN2 IP 10.1.20.115
Here's the results: