NTP not running on backup FW?
-
I have a problem setting up NTP with two pfsense in HA.
I think both server should have their NTP server up and running at all times and using their own IP address to sync to internet peers. That way they both have the right time regardless if they are master or backup and ntpd will have adjusted the clock drift on both.
Right now I only have the NTP server syncing to internet peers on the master and not the backup. Because of this the time on the backup server drifts away and when failover occurs the time is wrong. When the backup servers becomes master it starts to sync though.
Could this be a problem with NAT? Or is pfsense doing something with the ntpd service depending if the machine has the master och backup role?
I couldn't really find anywhere how ntp works in HA but maybe I looked in the wrong place. Any pointers would be much appreciated!
-
OK, with
psI found that the ntpd daemon is actually running on the secondary (backup). But it can't reach any peers on the WAN so it can't sync time.Is this normal behavior?
-
What are your outbound NAT settings?
Can the secondary ping out WAN when it is not CARP MASTER?
-
@Derelict said in NTP not running on backup FW?:
What are your outbound NAT settings?
Can the secondary ping out WAN when it is not CARP MASTER?
I'll test it when I get back into the office in a bit.
I know I have manual outbound NAT with the WAN VIP on everything except from localhost to udp/123. I'll check it.
-
You need to be sure outbound NAT is using the CARP VIP for things that go through the firewall like sessions from inside clients, but that connections from the firewall itself are using the WAN address. If you make connections from the firewall itself use the CARP VIP it won't be able to connect out when it is CARP BACKUP.
-
@Derelict said in NTP not running on backup FW?:
You need to be sure outbound NAT is using the CARP VIP for things that go through the firewall like sessions from inside clients, but that connections from the firewall itself are using the WAN address. If you make connections from the firewall itself use the CARP VIP it won't be able to connect out when it is CARP BACKUP.
OK, that makes sense.
Should I do that by looking at the source address and if it's the WAN address then it's from the firewall itself? In which case I can use the "Do not NAT" option.
-
Just NAT inside subnets to the CARP VIP and NAT connections from Localhost to the WAN address. You do not want to NAT from source any or source This firewall (self).
-
I have it set like this now.
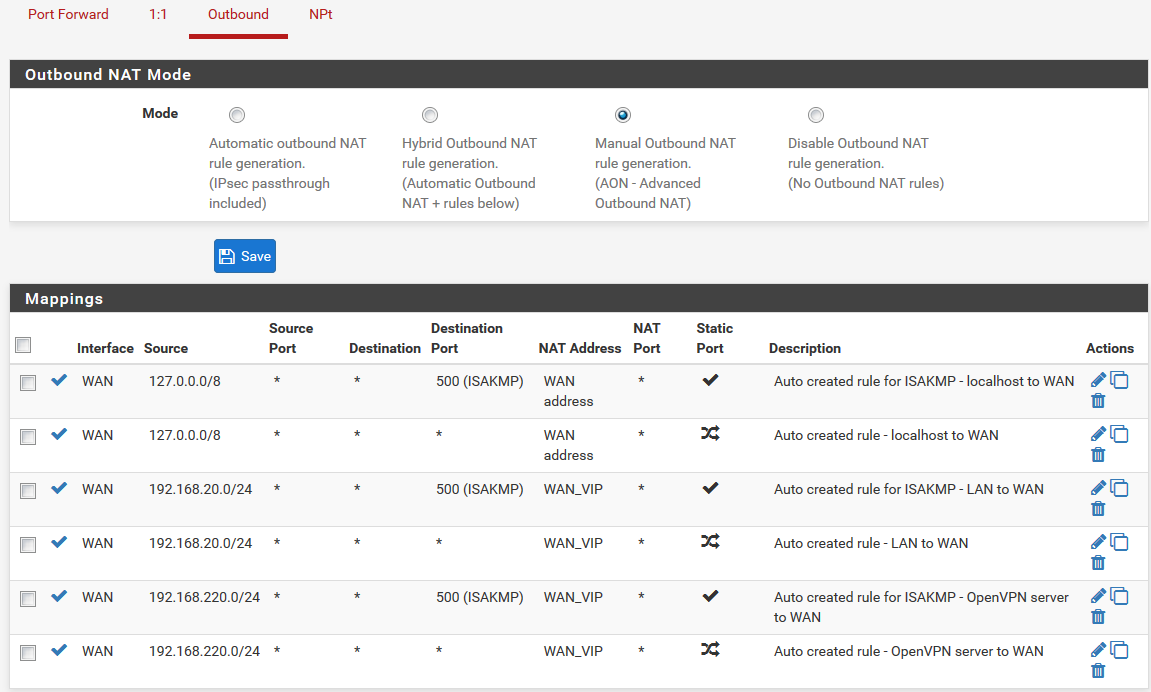
-
I still had problems with NTP though but I think it had to do with IPv6.
It looked like the NTP server got IPv6 addresses from DNS and would try to reach the peers that way.
These settings took care of that problem:
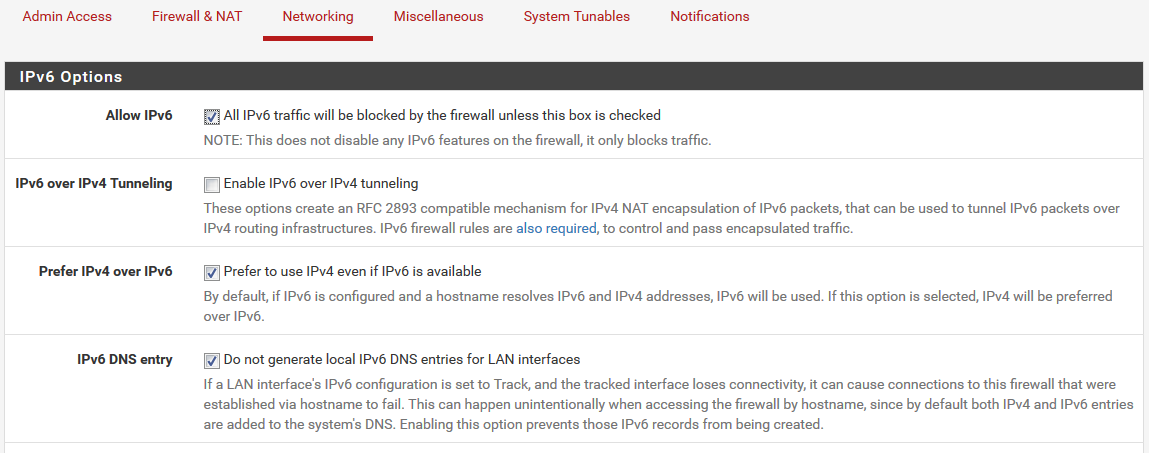
-
I had IPv6 traffic enabled under the Advanced settings not because I wanted it but because I wanted to have it blocked/rejected without logging it.
So I have this floating rule to do that.
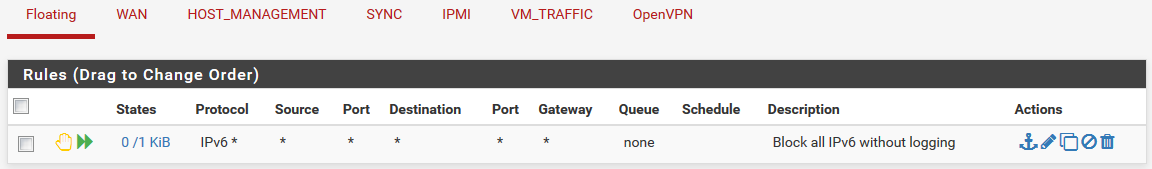
-
So now everything worked fine for a little while.
But then I saw this:
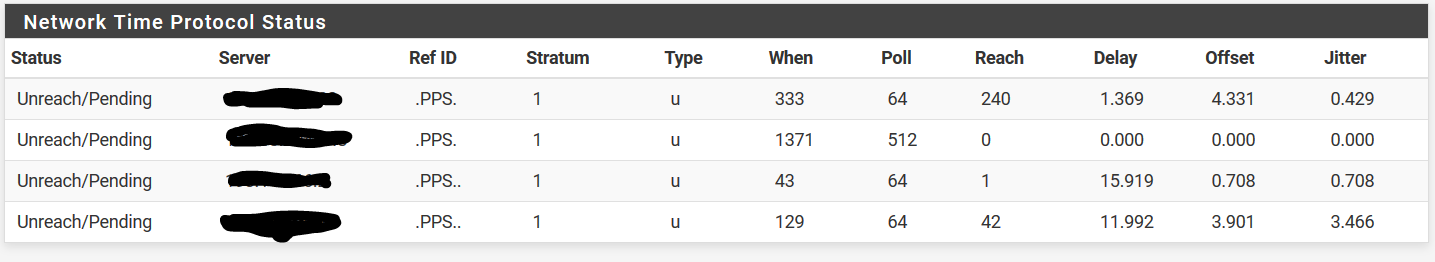
Using a shell on pfsense I can ping each NTP server and I can also use
ntpdateto set the clock. So basically it's not a firewall or routing problem I think.NTP log doesn't show anything unusual or different compared to the master firewall.
I'll keep looking.