Restricting access to GUI from LAN - Still have access?
-
Hi there,
I am trying to lock down the access to our Management GUI to a certain IP Range, i have followed the guide thats on netgate's website: https://docs.netgate.com/pfsense/en/latest/firewall/restrict-access-to-management-interface.html
Everything is identical, but once i turn Disable webConfigurator anti-lockout rule , we are still able to access the management gui from the LAN.
Here is what i have set up:
Aliases
Firewall Aliases IP Range - 10.0.7.0/24
Firewall Aliases Ports - 22, 443Firewall Rules on LAN
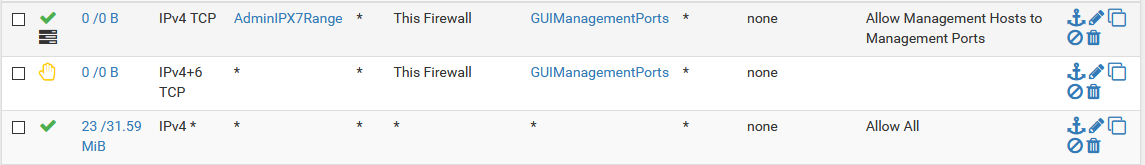
But as i mentioned, even with these rules in place, i am still able to access the management from a different network to whats been defined in the alias that was created.
Any help with this would be much appreciated.
Thanks!
-
Killed the firewall states ?
Bet if you put a log on your last rule it will show up as allowed.
What subnet mask do you have on your LAN interface ?
-
Hi thanks for the reply!
"Killed the firewall states ?" Not sure entirely how you would do this.
Hmm i tried it without that last rule and it was the same with or without that rule in.
With regards to the Subnet mask of the LAN interface its on a /22, and the AdminPIX7Range is on a /24 Subnet. Both are on the 10.0.7 range though would this cause the issue?
Further to this now, i have changed the management to be on /24 also, i will test the Rules again and see if this makes any changeThanks
-
This post is deleted! -
@gethersJ said in Restricting access to GUI from LAN - Still have access?:
Hi thanks for the reply!
"Killed the firewall states ?" Not sure entirely how you would do this.
Hmm i tried it without that last rule and it was the same with or without that rule in.
With regards to the Subnet mask of the LAN interface its on a /22, and the AdminPIX7Range is on a /24 Subnet. Both are on the 10.0.7 range though would this cause the issue?
Its shouldn't if the alias is defined correctly.
Further to this now, i have changed the management to be on /24 also, i will test the Rules again and see if this makes any change
Thanks
Diagnostics -> States -> Reset States
Diagnostics -> States -> States then filter on the IP
-
Cool thanks, ill try this tonight when no one is connected to the firewall.
One thing i notice is, on the State Filter, if i look at the LAN interface i see a Established State there.
The SOURCE is my PC's Default Gateway? , and not the actual IP Address of my PC. This would probably cause the issue as the DG is on the 10.0.7.X Network and my PC is on the 10.0.4.X network.
Any reason why this may be?
Thanks
-
@gethersJ said in Restricting access to GUI from LAN - Still have access?:
The SOURCE is my PC's Default Gateway? , and not the actual IP Address of my PC. This would probably cause the issue as the DG is on the 10.0.7.X Network and my PC is on the 10.0.4.X network.
Any reason why this may be?
Thanks
Err the subnet for your LAN should be 10.0.4.0/22 so your PC and anything in 10.0.7.0/24 are directly attached and the default gatway should be the pfSense LAN interface.
Your not using a managed switch with SVIs and routing 10.0.4.0/24, 10.0.5.0/24, 10.0.6.0/24 & 10.0.7.0/24 are you ?
-
Hi,
Sorry i should have mentioned, yeah my PC is on the 10.0.4.X network (just as a test PC) , the aim here was to loose connectivity to the GUI from my PC, then i have another one on the 10.0.7.X range that "should" get access to the GUI.
After thinking about this last night I think I have sussed it out, we are going through a Proxy and this is the IP Address that accesses the Management GUI, hopefully I should be able to add some rules in our other proxy to avoid this Firewall bypassing it.
Ill let you know if i have any more issues or if i need more help with this.
Thanks for your help!